Xubuntu 24.04 and Kubernetes cluster
 Kev
KevFollow this documentation to set up a highly available Kubernetes cluster using Xubuntu 24.04. You can try this out in VMWare Workstation 17 since it has been free for Personal Use
This documentation guides you in setting up a cluster with a master node and one worker node
Environment
| FQDN | IP | OS | RAM | CPU | |
| Master | kmain1.example.com | 192.168.1.101 | Xubuntu 24.04 | 2G | 2 |
| Worker | knode1.example.com | 192.168.1.110 | Xubuntu 24.04 | 2G | 4 |
On all kubernetes nodes (kmain1, knode1)
- Upgrade your Xubuntu servers
Provision the servers to be used in the deployment of Kubernetes on Xubuntu 24.04. The setup process will vary depending on the virtualization or cloud environment you’re using.
Once the servers are ready, update them.
sudo apt update
sudo apt -y full-upgrade
[ -f /var/run/reboot-required ] && sudo reboot -f
- Install kubelet, kubeadm and kubectl
Once the servers are rebooted, add Kubernetes repository for Xubuntu 24.04 to all the servers.
sudo apt install curl apt-transport-https -y
echo "deb [signed-by=/etc/apt/keyrings/kubernetes-apt-keyring.gpg] https://pkgs.k8s.io/core:/stable:/v1.31/deb/ /" | sudo tee /etc/apt/sources.list.d/kubernetes.list
curl -fsSL https://pkgs.k8s.io/core:/stable:/v1.31/deb/Release.key | sudo gpg --dearmor -o /etc/apt/keyrings/kubernetes-apt-keyring.gpg
Then install required packages.
sudo apt update
sudo apt install wget docker.io curl vim git kubelet kubeadm kubectl -y
sudo apt-mark hold kubelet kubeadm kubectl
- Disable Swap Space
Disable all swaps from /proc/swaps.
sudo swapoff -a
Now disable Linux swap space permanently in /etc/fstab. Search for a swap line and add # (hashtag) sign in front of the line.
$ sudo vim /etc/fstab
#/swap.img none swap sw 0 0
Enable kernel modules and configure sysctl.
# Enable kernel modules
sudo modprobe overlay
sudo modprobe br_netfilter
# Add some settings to sysctl
sudo tee /etc/sysctl.d/kubernetes.conf<<EOF
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
net.ipv4.ip_forward = 1
EOF
# Reload sysctl
sudo sysctl --system
After that configure containerd.
# Configure containerd and start service
sudo su -
mkdir -p /etc/containerd
containerd config default>/etc/containerd/config.toml
In the config.toml
To use the systemd cgroup driver, open vim/etc/containerd/config.toml, change the SystemdCgroup = true
Also change the sandbox image to
sandbox_image = "registry.k8s.io/pause:3.10"
After that perform containerd restart
# restart containerd
sudo systemctl restart containerd
sudo systemctl enable containerd
systemctl status containerd
On kmain1
We now want to initialize the machine that will run the control plane components which includes etcd (the cluster database) and the API Server.
Pull container images:
$ sudo kubeadm config images pull
Initialize Kubernetes Cluster
$ sudo kubeadm init
--pod-network-cidr=10.1.0.0/16
--cri-socket unix://var/run/containerd/containerd.sock
--upload-certs
--control-plane-endpoint=dev-k8s-cluster.example.io
Once you see the initialization has completed, there is a long list of tasks to proceed, to which I touch below
Your Kubernetes control-plane has initialized successfully!
To start using your cluster, you need to run the following as a regular user:
#do this
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
Next download Calico
curl https://raw.githubusercontent.com/projectcalico/calico/v3.28.1/manifests/calico.yaml -O
We need to edit the calico file, since we have specify the ip range to 10.1.0.0/16, so lets make it over to the calico yaml, make the change as below. If you wish to use Calico and your own defined ip range, this should be changed
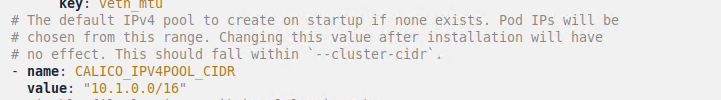
Next apply the yaml file
kubectl apply -f calico.yaml
You are done for KMain1
On knode1
Next lets look into the Worker node, as usual, you can follow the step until the containerd section and lastly perform this to join the cluster
kubeadm join dev-k8s-cluster.example.com:6443 --token sr4l2l.2kvot0pfalh5o4ik \
--discovery-token-ca-cert-hash sha256:c692fb047e15883b575bd6710779dc2c5af8073f7cab460abd181fd3ddb29a18
Subscribe to my newsletter
Read articles from Kev directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
