Mastering SELinux: A Comprehensive Guide to Enhancing Linux Security with Mandatory Access Control
 TATHAGATA ROY
TATHAGATA ROYTable of contents
- 1. Introduction to SELinux
- 2. Understanding Access Control in Linux
- 3. SELinux Architecture and Working Mechanism
- 4. Installing and Verifying SELinux on Your System
- 5. SELinux Modes: Enforcing, Permissive, and Disabled
- 6. Configuring SELinux for Your System
- 7. Troubleshooting SELinux Issues
- 8. Practical Example: Setting Up SELinux with Apache and VSFTPD
- 9. SELinux Policies and Modules
- 10. Advanced SELinux Configurations
- 11. SELinux Best Practices
- 12. Monitoring SELinux Activity
- 13. Disabling SELinux: Pros and Cons
- 14. Common SELinux Use Cases
- 15. Conclusion
- Resources

1. Introduction to SELinux
Overview of SELinux:
Security-Enhanced Linux (SELinux) is an advanced access control mechanism integrated into the Linux kernel. It provides an additional layer of security by enforcing mandatory access control (MAC) policies that restrict users and processes from performing unauthorized actions on a Linux system.
The Origin of SELinux:
SELinux was originally developed by the United States National Security Agency (NSA) to address security concerns in computer systems. The NSA released SELinux to the public domain, allowing various Linux distributions to incorporate it into their security frameworks. Today, SELinux is a standard feature in many popular Linux distributions, such as CentOS, Red Hat Enterprise Linux (RHEL), and Fedora.
Importance of SELinux:
In an era where cybersecurity threats are constantly evolving, SELinux plays a critical role in preventing unauthorized access and system tampering. By confining each process to a specific domain and controlling its interactions with files and other processes, SELinux reduces the risk of exploitation by malicious actors.
2. Understanding Access Control in Linux
What is Access Control?
Access control is a fundamental security concept that governs how users and processes interact with system resources. In Linux, access control is traditionally managed through Discretionary Access Control (DAC), which allows users to set permissions on their files and directories.
Difference Between DAC and MAC:
DAC (Discretionary Access Control): This is the default access control mechanism in Linux, where file and directory owners have the discretion to set permissions. However, DAC has limitations, as users can inadvertently grant excessive permissions, leading to security vulnerabilities.
MAC (Mandatory Access Control): SELinux introduces MAC, a stricter form of access control that operates independently of user discretion. With MAC, access permissions are enforced by the system based on predefined policies, reducing the risk of unauthorized access.
How SELinux Enhances Security with MAC:
SELinux enhances Linux security by implementing MAC policies that restrict the actions of users and processes, regardless of DAC settings. For example, even if a user has permission to execute a file under DAC, SELinux can block the execution if it violates a MAC policy.
3. SELinux Architecture and Working Mechanism
How SELinux Works:
SELinux operates by assigning security contexts to all files, processes, and system objects. These contexts define the security attributes, including the type, role, and user, which SELinux uses to enforce access control policies.
Role of Domains in SELinux:
In SELinux, each process runs within a specific domain, which determines what actions the process can perform. Domains are essential in preventing unauthorized access, as they limit the scope of what processes can do based on the assigned policies.
Example: Restricting Shell Script Execution in Home Directories:
Consider a scenario where you want to prevent users from executing shell scripts in their home directories. Without SELinux, users with execute permissions could run any script. However, with SELinux, you can enforce a policy that restricts script execution to specific directories, ensuring that only trusted scripts are executed.
Here is a diagram of the architecture:
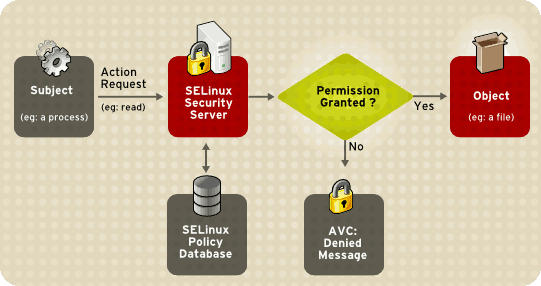
4. Installing and Verifying SELinux on Your System
Prerequisites for SELinux Installation:
Before installing SELinux, ensure that your system is up to date. You can do this by running the following command:
sudo yum update
Step-by-Step Guide to Installing SELinux Packages:
To install SELinux on a CentOS or RHEL system, follow these steps:
Install Apache (
httpd) and VSFTPD:sudo yum install httpd sudo service httpd start sudo service httpd status sudo yum install vsftpd sudo service vsftpd startCheck if SELinux Packages are Installed: Use the following command to verify if SELinux packages are installed:
rpm -qa | grep selinuxExpected Output:
libselinux-utils-2.2.2-6.el7.x86_64 libselinux-2.2.2-6.el7.x86_64 selinux-policy-targeted-3.12.1-153.el7.noarch selinux-policy-3.12.1-153.el7.noarch libselinux-python-2.2.2-6.el7.x86_64Install Missing SELinux Packages: If SELinux packages are missing, install them using the following command:
sudo yum install policycoreutils policycoreutils-python selinux-policy selinux-policy-targeted libselinux-utils setroubleshoot-server setools setools-console mcstrans
Verifying SELinux Installation with Commands:
After installation, verify that SELinux is properly installed and configured by running:
sestatus
This command will display the current status of SELinux, including whether it is enabled and the current mode (e.g., enforcing, permissive, or disabled).
5. SELinux Modes: Enforcing, Permissive, and Disabled
Explanation of SELinux Modes:
Enforcing: In this mode, SELinux enforces its security policies, denying any unauthorized actions. This is the recommended mode for production environments.
Permissive: SELinux policies are not enforced in this mode, but all violations are logged. This mode is useful for troubleshooting and testing.
Disabled: SELinux is completely turned off, and no policies are enforced or logged. Disabling SELinux can expose your system to security risks.
How to Check the Current Mode with getenforce: You can check the current SELinux mode using the following command:
getenforce
Configuring SELinux Modes in the SELinux Configuration File: To change the SELinux mode, you need to edit the SELinux configuration file located at /etc/selinux/config. Here’s how:
sudo vi /etc/selinux/config
Inside the configuration file, set the SELINUX variable to one of the following:
SELINUX=enforcing # For Enforcing mode
SELINUX=permissive # For Permissive mode
SELINUX=disabled # For Disabled mode
6. Configuring SELinux for Your System
Editing the SELinux Configuration File:
The SELinux configuration file /etc/selinux/config allows you to configure SELinux settings. To edit the file, use a text editor like vi:
sudo vi /etc/selinux/config
Switching SELinux Modes: Enforcing, Permissive, and Disabled:
As previously mentioned, you can switch between SELinux modes by setting the SELINUX variable in the configuration file to enforcing, permissive, or disabled.
The Importance of Rebooting the System After Configuration Changes:
After making changes to the SELinux configuration, you must reboot your system for the changes to take effect. Use the following command to reboot:
sudo reboot
7. Troubleshooting SELinux Issues
Common SELinux Errors and How to Identify Them:
SELinux can block actions that would otherwise be allowed under DAC. Common errors include denied access to files or services, which are logged in the system's audit logs.
Using Logs to Troubleshoot SELinux Issues:
To troubleshoot SELinux issues, you can check the system logs for any SELinux-related messages. Use the following command to search for SELinux entries in the logs:
sudo cat /var/log/messages | grep "SELinux"
Commands to Check for SELinux Errors in System Logs: To specifically check for errors where SELinux is preventing an action, use:
sudo cat /var/log/messages | grep "SELinux is preventing"
8. Practical Example: Setting Up SELinux with Apache and VSFTPD
Installing Apache (httpd) and VSFTPD on a CentOS System:
As previously demonstrated, install Apache and VSFTPD.
sudo yum install httpd vsftpd
Configuring SELinux to Allow Web and FTP Services:
By default, SELinux has policies that control web and FTP services. You may need to adjust these policies if you encounter issues. For example, to allow Apache to connect to the network, use this-
sudo setsebool -P httpd_can_network_connect on
Testing the Setup to Ensure SELinux Does Not Interfere:
After configuring SELinux, restart the services and verify that they work without SELinux blocking them.
sudo service httpd restart
sudo service vsftpd restart
9. SELinux Policies and Modules
What are SELinux Policies?
SELinux policies define the rules that control the access permissions for users, files, and processes. These policies determine what actions are allowed or denied.
Understanding SELinux Modules:
SELinux modules are components of SELinux policies that can be loaded or unloaded to change the security behavior of the system. They allow for modular management of SELinux policies.
How to Manage and Customize SELinux Policies:
You can manage SELinux policies using tools like semodule. For example, to list all loaded modules:
sudo semodule -l
To install a custom module:
sudo semodule -i mymodule.pp
10. Advanced SELinux Configurations
Fine-Tuning SELinux for Specific Applications:
Advanced SELinux configurations allow you to fine-tune policies for specific applications. For example, you can create custom policies to allow or deny specific actions for an application.
Managing User Roles and Access with SELinux:
SELinux allows you to define user roles, each with different levels of access. This helps in managing user permissions in a more granular way.
Practical Examples of Advanced SELinux Configurations:
One advanced configuration could involve setting up SELinux to only allow a specific user to run a particular service. Another could involve customizing the SELinux policy to allow a specific application to write to a directory that it normally wouldn’t have access to.
11. SELinux Best Practices
General Best Practices for Managing SELinux:
Always keep SELinux enabled in enforcing mode in production environments.
Regularly update your SELinux policies to ensure they are up to date with the latest security patches.
Use permissive mode for troubleshooting but switch back to enforcing mode once issues are resolved.
Security Tips for Using SELinux in Production Environments:
Avoid disabling SELinux unless absolutely necessary, as this exposes the system to potential security risks.
Monitor SELinux logs regularly to detect and respond to any potential security incidents.
Common Pitfalls to Avoid When Configuring SELinux:
Not rebooting the system after making changes to SELinux configurations.
Ignoring SELinux alerts and errors, which could indicate potential security issues.
12. Monitoring SELinux Activity
Tools and Commands for Monitoring SELinux Activity:
SELinux provides several tools for monitoring its activity, such as audit2allow and setools. These tools help you understand what actions SELinux is taking and why.
How to Use audit2allow to Generate Custom SELinux Policies:audit2allow is a tool that allows you to generate custom SELinux policies based on audit logs. For example, to create a policy for an action that was denied:
sudo cat /var/log/audit/audit.log | grep "denied" | audit2allow -M mycustompolicy
Then, install the generated policy with:
sudo semodule -i mycustompolicy.pp
Analyzing SELinux Logs for Security Insights:
Regularly reviewing SELinux logs can provide valuable insights into potential security threats. Look for patterns of denied actions that could indicate an attempted attack.
13. Disabling SELinux: Pros and Cons
Why Some Users Choose to Disable SELinux:
Some users disable SELinux due to compatibility issues with certain applications or because of the perceived complexity of managing SELinux policies. However, disabling SELinux should be a last resort.
Potential Risks of Disabling SELinux:
Disabling SELinux removes a critical layer of security, making your system more vulnerable to unauthorized access and attacks. Without SELinux, any process with the appropriate DAC permissions can perform potentially harmful actions.
Alternative Security Measures if SELinux is Disabled:
If you must disable SELinux, consider implementing alternative security measures, such as AppArmor, strict firewall rules, and regular system monitoring to mitigate the risks.
14. Common SELinux Use Cases
SELinux in Web Server Security:
SELinux is often used to secure web servers, such as Apache. It ensures that web server processes are confined to their domains and cannot access files or services that they shouldn’t.
Using SELinux in Multi-User Environments:
In environments with multiple users, SELinux can enforce strict access controls, ensuring that each user’s actions are confined to their permitted domains. This helps prevent privilege escalation and unauthorized access.
Examples of SELinux Protecting Against Common Threats:
SELinux has been effective in mitigating the impact of several security vulnerabilities. For example, if a web server is compromised, SELinux can prevent the attacker from gaining full control of the system by restricting the web server process’s capabilities.
15. Conclusion
Summary of Key Points About SELinux:
SELinux is a powerful tool for enhancing the security of Linux systems by implementing mandatory access control policies. It confines processes to specific domains, reducing the risk of unauthorized access and system compromise.
Final Thoughts on the Importance of SELinux in Linux Security:
In today’s threat landscape, SELinux is an essential component of a robust Linux security strategy. By understanding and properly configuring SELinux, administrators can significantly improve the security posture of their systems.
Resources
DigitalOcean : https://www.digitalocean.com/community/tutorials/an-introduction-to-selinux-on-centos-7-part-1-basic-concepts
Red Hat : https://docs.redhat.com/en/documentation/red_hat_enterprise_linux/5/html/deployment_guide/ch-selinux
Subscribe to my newsletter
Read articles from TATHAGATA ROY directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

TATHAGATA ROY
TATHAGATA ROY
Hello! I'm a passionate and dedicated cybersecurity enthusiast with a love for learning and sharing insights, my blog dives deep into cybersecurity threats, technical analysis, and best practices to safeguard digital assets.