OverTheWire Bandit - LVL9 (Documented/Completed)
 Mike Kobbie Tieku TABI
Mike Kobbie Tieku TABI
The goal for → LVL 9::
Level Goal:
→ The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
Commands you may need to solve this level: → grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Explanation:
Password for Bandit9 Access: 4CKMh1JI91bUIZZPXDqGanal4xvAg0JM
First, ssh into Bandit Lvl 9. We can do this by entering the following:
→ ssh bandit9@bandit.labs.overthewire.org -p2220
You’ll then be asked top enter the password for Bandit9. Type it in and press enter (REMEMBER, you wont see the password type out on screen so type it carefully and correctly).
Once this is done you’ll successfully connect.
Both the grep command and the string command will be used to solve this level.
The grep command is a powerful tool for searching text using patterns. It scans input line by line and prints lines that match a specified pattern, which can be a simple string or a more complex regular expression. grep is commonly used for filtering text, searching logs, and finding specific content in files.
Examples of grep usage include:
grep "error" file.txt- Finds lines containing "error" infile.txt.grep -i "warning" logs.txt- Case-insensitive search for "warning" inlogs.txt.grep -r "TODO" src/- Recursively searches for "TODO" in all files within thesrc/directory.grep -v "^#" config.txt- Shows lines not starting with#inconfig.txt.
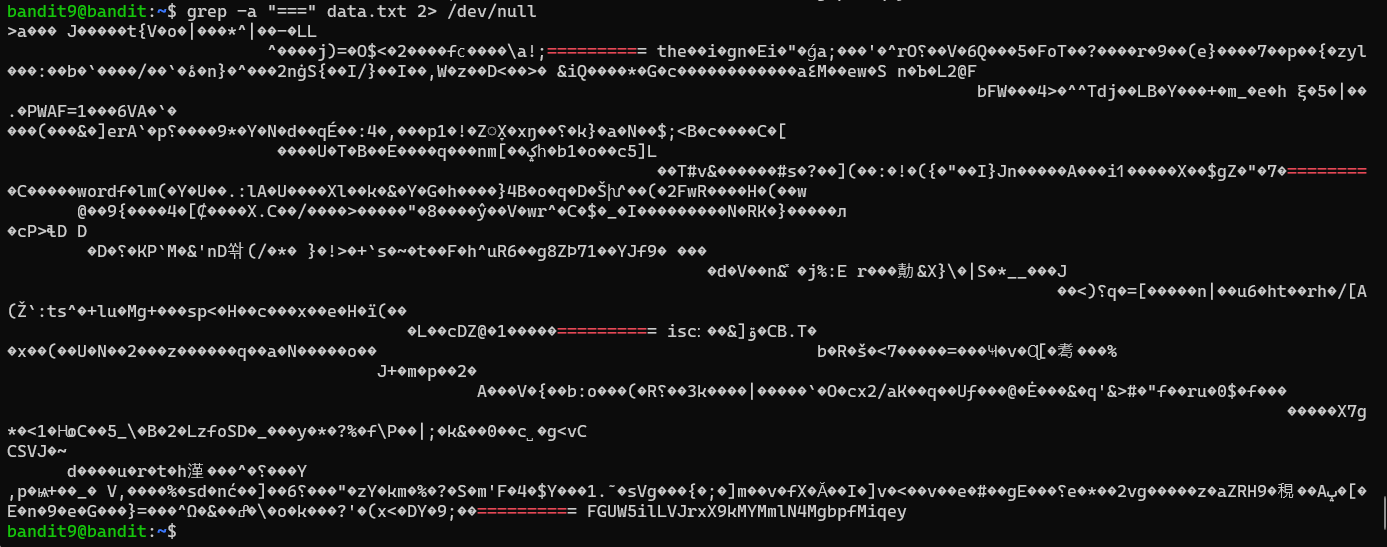
The command used in the image below, grep -a "===" data.txt 2> /dev/null searches for the string === in the file data.txt.
The
aoption treats the file as text, even if it's a binary file. This is useful when searching for patterns in files that might not be plain text.2> /dev/nullredirects any error messages to/dev/null, effectively silencing them. This is useful if the file contains unreadable sections or if you want to suppress error output.
Overall, this command quietly searches for lines containing === in data.txt, even if the file has non-text content, and suppresses any errors. Now in our situation this doesnt exactly help as we are still presented with unreadable text mixed with readable text. Though we see the password at the bottom, lets go a step further and get rid of anything that is unreadable and only show text that might be useful to us. to do this we want to involve the use of the string command.
The strings command is used to extract printable text from a file. It scans the file for sequences of printable characters (typically longer than a certain length) and outputs them. This is particularly useful for analyzing binary files, executables, or any file where readable text might be mixed with non-readable data.
Examples of grep usage include:
strings file.bin- Extracts readable text from the binary filefile.bin.strings -n 8 file.bin- Extracts strings with a minimum length of 8 characters.strings /usr/bin/ls- Displays printable strings from thelsexecutable.strings core.dump | grep "error"- Searches for the word "error" in a core dump file.
When combined, strings and grep allow you to extract readable text from a file and then search for specific patterns within that extracted text. For example, the command strings data.txt | grep "^===" first uses strings to extract all readable text from data.txt. It then pipes this output to grep, which searches for and displays only those lines that begin with ===. As we see below once we run the set of commands we are shown the password.
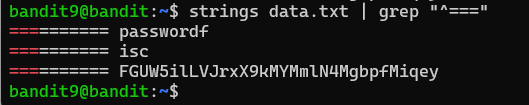
The password for Level 10 access is: FGUW5ilLVJrxX9kMYMmlN4MgbpfMiqey
That is Bandit Level 9 complete, Head over to Bandit Level 10!
Subscribe to my newsletter
Read articles from Mike Kobbie Tieku TABI directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
