AWS Essentials: Setting up a NAT Gateway
 DigiSalt
DigiSalt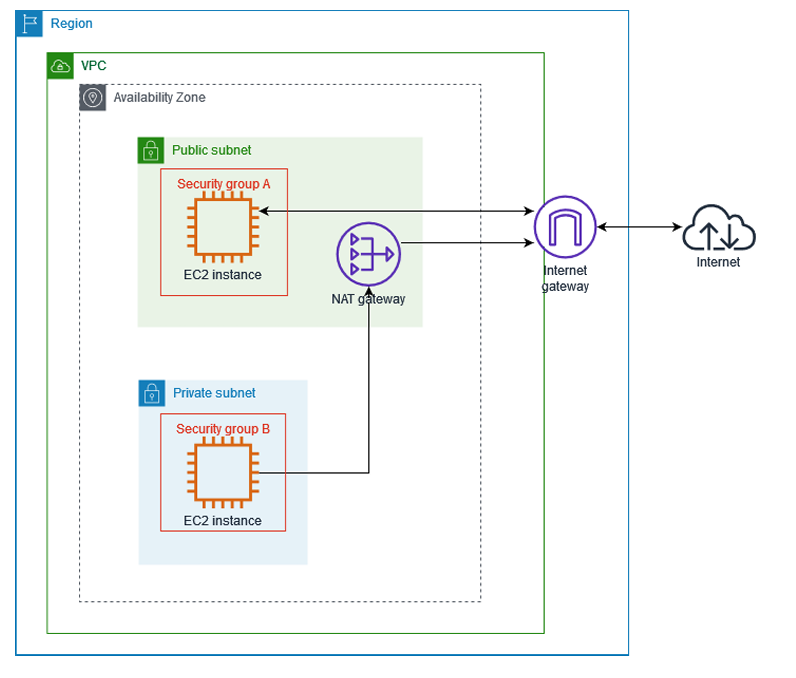
In today's cloud computing landscape, managing secure and efficient internet access within a virtual private network is crucial. The AWS NAT Gateway (Network Address Translation Gateway) is a vital tool in this process, offering a scalable and reliable solution for enabling instances in a private subnet to connect to the internet while keeping the subnet secure.
This article delves into the importance of NAT Gateway in AWS, guiding you through its setup and best practices to ensure a seamless and secure cloud infrastructure.
Importance of NAT Gateway in AWS
The NAT Gateway plays a critical role in AWS networking by allowing resources in a private subnet to access the internet without exposing them to incoming traffic. For example, suppose you have an application server hosted in a private subnet that needs to download software updates from the internet. By using a NAT Gateway, you can route the outbound traffic through a public subnet while keeping your private subnet shielded from direct internet exposure.
Understanding NAT Gateway
What is NAT (Network Address Translation)?
Network Address Translation (NAT) is a method used to modify the IP address information in packet headers while they are in transit across a routing device. In a typical home network, for example, multiple devices might share a single public IP address provided by your ISP. NAT allows these devices to communicate with external networks (like the internet) by translating private IP addresses to a public IP address.
In the context of AWS, NAT is used to enable instances within a private subnet to access the internet while keeping them secure from inbound connections. For instance, a database server in a private subnet can send logs to an external monitoring service via the NAT Gateway without being exposed to the internet.
Difference between NAT Gateway and NAT Instance
AWS offers two primary solutions for implementing NAT: NAT Gateway and NAT Instance. While both serve the same fundamental purpose, they differ in several key aspects:
NAT Gateway: A managed service provided by AWS, offering high availability, scalability, and easier management. For example, if your application traffic suddenly spikes, the NAT Gateway automatically scales to handle the increased load without any manual intervention.
NAT Instance: A self-managed Amazon EC2 instance running NAT software. It offers more control and flexibility but requires manual scaling, maintenance, and management. For example, if you choose a NAT Instance and your traffic increases, you would need to manually adjust the instance size or launch additional instances to handle the load.
Use Cases for NAT Gateway
NAT Gateway is typically used in scenarios where instances in a private subnet need to:
Download Software Updates: For example, your EC2 instances in a private subnet might need to download updates from the internet. NAT Gateway allows this without exposing the instances to incoming internet traffic.
Access External APIs: If your application needs to communicate with third-party APIs over the internet, NAT Gateway can route this traffic securely.
Send Logs to External Services: For instance, you might want to send application logs from a private subnet to a cloud-based logging service. NAT Gateway allows this while maintaining the security of your internal network.
Prerequisites
Before setting up a NAT Gateway, ensure you have the following:
AWS Account Setup
An active AWS account with the necessary permissions to create VPCs, subnets, and NAT Gateways.
Basic Networking Knowledge
Familiarity with basic networking concepts such as IP addressing, routing, and subnetting.
VPC (Virtual Private Cloud) and Subnet Configuration
An existing VPC with at least one public and one private subnet configured. For example, you might have a VPC with a CIDR block of 10.0.0.0/16, a public subnet with 10.0.1.0/24, and a private subnet with 10.0.2.0/24.
Steps to Setup NAT Gateway
Creating a VPC
Define CIDR Block
Start by defining a CIDR block for your VPC. For example, you could choose 10.0.0.0/16, which provides a large range of IP addresses that can be divided into subnets.
Create Subnets (Public and Private)
Create two subnets within your VPC:
Public Subnet: For example, create a public subnet with a CIDR block of
10.0.1.0/24for resources that need internet access.Private Subnet: Create a private subnet with a CIDR block of
10.0.2.0/24for internal resources that should not be directly exposed to the internet.
Configure Route Tables
Public Subnet Route Table
Associate the public subnet with a route table that directs internet traffic to an internet gateway. For example, add a route to 0.0.0.0/0 pointing to the Internet Gateway (igw-1234567890).
Private Subnet Route Table
Associate the private subnet with a route table that directs internet traffic to the NAT Gateway. For instance, add a route to 0.0.0.0/0 pointing to the NAT Gateway (nat-1234567890).
Allocate and Associate Elastic IP
Allocate an Elastic IP address, which will be used by the NAT Gateway for outbound internet traffic. For example, allocate an Elastic IP (54.123.45.67) that your NAT Gateway will use.
Create NAT Gateway
Select Elastic IP
When creating the NAT Gateway, select the allocated Elastic IP (54.123.45.67).
Associate NAT Gateway with Public Subnet
Place the NAT Gateway in the public subnet (10.0.1.0/24) to ensure it can route traffic to the internet.
Update Route Tables
Add Routes for Internet Traffic
Update the private subnet’s route table to direct internet-bound traffic to the NAT Gateway. For example, set a route to 0.0.0.0/0 pointing to the NAT Gateway (nat-1234567890).
Associate Route Table with Private Subnet
Ensure the route table is associated with the private subnet (10.0.2.0/24) so that instances can use the NAT Gateway for internet access.
Testing the NAT Gateway Setup
Launch EC2 Instances
To verify the setup, launch two EC2 instances:
Instance in Public Subnet
Launch an EC2 instance in the public subnet (10.0.1.0/24). This instance should have direct internet access via the internet gateway.
Instance in Private Subnet
Launch an EC2 instance in the private subnet (10.0.2.0/24). This instance should use the NAT Gateway for outbound internet traffic.
Verify Internet Connectivity
Instance in Public Subnet Connection Check
Connect to the public instance and check its connectivity to the internet by pinging a public IP address or running curl http://example.com.
Instance in Private Subnet Connection Check
Connect to the private instance and verify its internet connectivity by pinging a public IP address or running curl http://example.com. If properly configured, this instance will reach the internet through the NAT Gateway.
Best Practices
High Availability
To ensure high availability, deploy NAT Gateways in multiple Availability Zones. For example, if your VPC spans two Availability Zones (us-east-1a and us-east-1b), create a NAT Gateway in each zone and configure your route tables accordingly.
Security Considerations
Restrict access to your NAT Gateway using security groups and network ACLs. For example, create security group rules that only allow outbound traffic to specific IP ranges or ports.
Cost Management
Monitor the use of NAT Gateway to optimize costs, considering the data transfer rates and usage patterns. For example, regularly review your NAT Gateway usage in the AWS Cost Explorer to identify any potential cost savings.
Troubleshooting Common Issues
No Internet Connectivity
Ensure that the route tables are correctly configured and that the NAT Gateway is associated with the correct subnets. For example, check that the private subnet's route table correctly points to the NAT Gateway.
Route Table Misconfigurations
Double-check the route tables for any errors that might prevent proper routing of traffic. For instance, verify that the 0.0.0.0/0 route in the private subnet’s route table points to the correct NAT Gateway.
Elastic IP Issues
Ensure that the Elastic IP is correctly allocated and associated with the NAT Gateway. For example, confirm that the Elastic IP (54.123.45.67) is attached to the NAT Gateway and not to another resource.
Conclusion
Recap of Steps
Setting up a NAT Gateway involves creating a VPC, configuring subnets and route tables, allocating an Elastic IP, and testing connectivity. With these steps, you can ensure that your private instances have secure and controlled internet access.
Benefits of Using NAT Gateway
NAT Gateway offers a managed, scalable, and secure solution for providing internet access to instances in private subnets, making it an essential component in many AWS architectures.
Additional Resources and Reading
For more information, consult the official AWS documentation on NAT Gateway, VPC configurations, and best practices. Additional tutorials and case studies can provide further insights into optimizing your AWS environment.
Subscribe to my newsletter
Read articles from DigiSalt directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

DigiSalt
DigiSalt
🌟 Riding the Digital Wave 🔍 Exploring & Explaining Modern Tech 📱 Programming, Gadgets, Software, Trends, Lifestyle Hacks ✨ Join the Journey at DigiSalt.com