Pyramid of Pain - A Layered Defense System
 Solomon Achugwoh
Solomon Achugwoh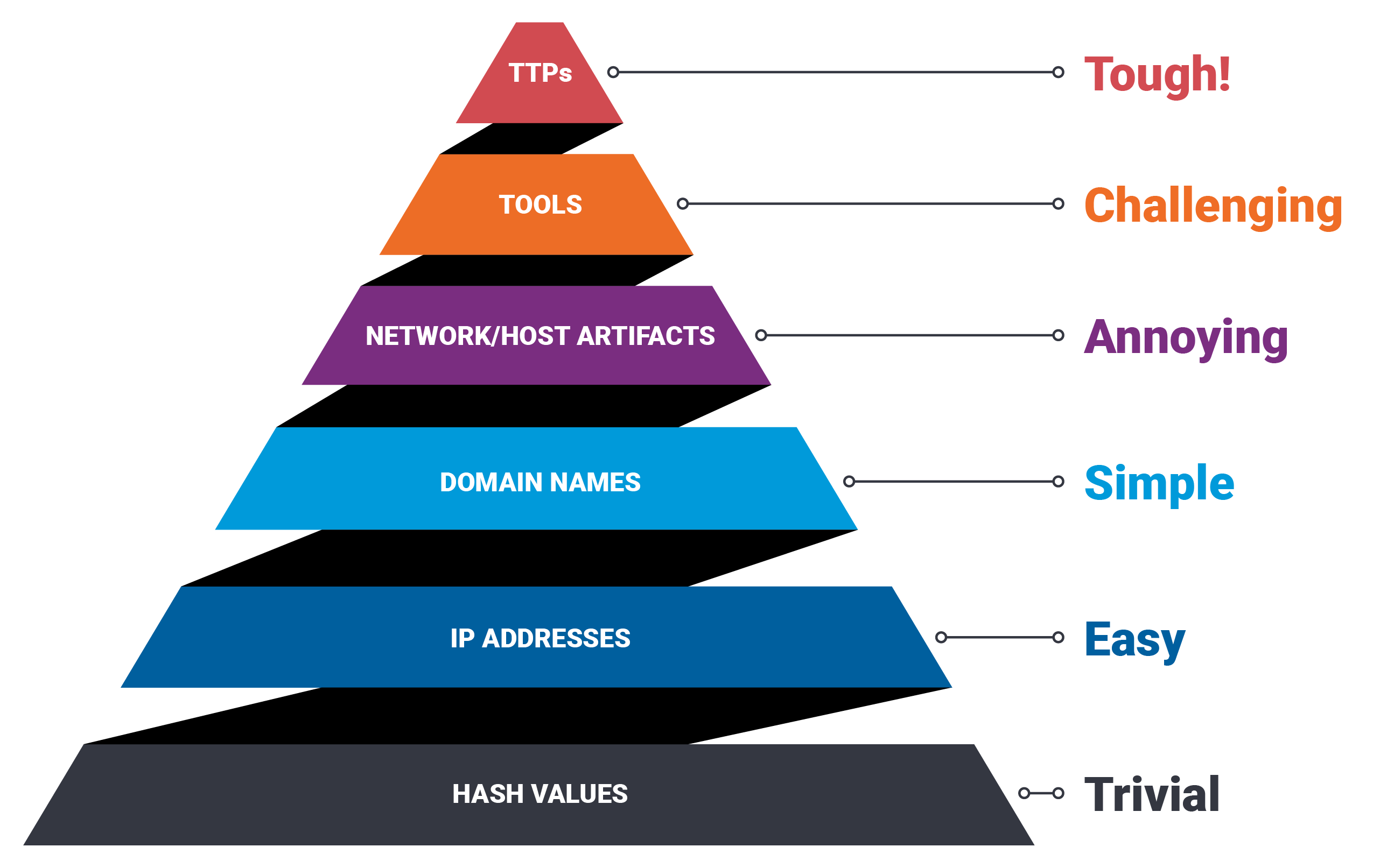
Organizations face ever-growing threat from attackers. One effective way to strengthen defenses against these threats is through the concept known as the Pyramid of Pain. This framework illustrates how various security measures can create layers of difficulty for threat actors attempting to breach an organization's network. The harder the struggle, the more likely they are to give up. The Pyramid of Pain has six layers, each representing different kinds of defenses. The higher you go up the pyramid, the more pain it causes the attacker, making it harder for them to succeed.
Imagine you're a burglar trying to break into a house. You've got your lockpicks and a few tricks up your sleeve. But, as you approach the front door, you notice something's off. The lock is not just any ordinary lock; it's a high-security smart lock with biometric authentication, motion sensors, and a loud alarm system. You realize that breaking in won't be as easy as you thought. The Pyramid of Pain in cybersecurity is a similar scenario to what attackers face when they try to breach an organization's network.
Breakdown of each level of the Pyramid of Pain:
Hash Values: Hash values are like digital fingerprints for files. They’re easy for hackers to use because they can quickly identify known malicious files. However, if you change or block these hash values, hackers need to find a new way to identify their tools. It’s a major setback.
IP Addresses: IP addresses are like home addresses on the internet. If a hacker knows the IP address of a target, they can attack directly. Blocking or changing these addresses forces the hacker to search for the target again, which takes time but is still manageable.
Domain Names: Domain names are the web addresses we use every day, Hackers often use domain names to control their attacks. They have to find or create a new one, which is more effort but still possible.
Network Artifacts: Network artifacts are patterns similar to certain kinds of network activity. If a hacker knows these patterns, they can blend in and avoid detection. By changing or hiding these artifacts, you make it harder for them to operate without being noticed.
Tools: Hackers use specialized tools to break into systems, like how a burglar might use lockpicks. If you block or disrupt these tools, the hacker has to find or develop new ones. This takes significant time and effort, making it much harder for them to carry out their attacks.
TTPs (Tactics, Techniques, and Procedures): TTPs are the strategies hackers use to break into systems. This is the top of the pyramid and the hardest to counter. If you can disrupt or change your defences regularly, it’s like constantly upgrading your security system at home. Hackers need to rethink their entire approach, which is not only difficult but often so frustrating that they’ll move on to an easier target.
Why the Pyramid of Pain important
Increased Complexity: The higher the layer, the more complex and resource-intensive the attack becomes. Hackers must invest more time and effort to find vulnerabilities, making them less likely to target organizations with robust security measures.
Detection and Response: With layers like network traffic and behavioral analysis in place, organizations can detect and respond to threats more effectively. This proactive approach means that even if hackers manage to breach initial defenses, they risk being caught before achieving their objectives.
- It helps organizations defend themselves: By understanding the Pyramid of Pain, organizations can focus on securing the lower levels, which are easier to defend.
Just like how a strong lock and an alarm system can deter a burglar, the right cyber defenses can protect your network from even the most determined attackers. So, when it comes to protecting an organization’s network from hackers, the Pyramid of Pain is a powerful concept. By understanding this framework, organizations can take a more proactive approach to cybersecurity and protect themselves from attacks.
Subscribe to my newsletter
Read articles from Solomon Achugwoh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Solomon Achugwoh
Solomon Achugwoh
I am a cyber security strategist involved in security implementation and cyber awareness across individual and organization level. I am a strong advocate of information security ethics on the part of people using technology. I have strong interest in incident response and vulnerability assessment and passionate about information technology as a whole. I spend my spare time watching football or participating in a sporting activity.