AWS IAM Identity Center: A Beginner’s Overview
 Vallamkondu Sai Varun
Vallamkondu Sai Varun
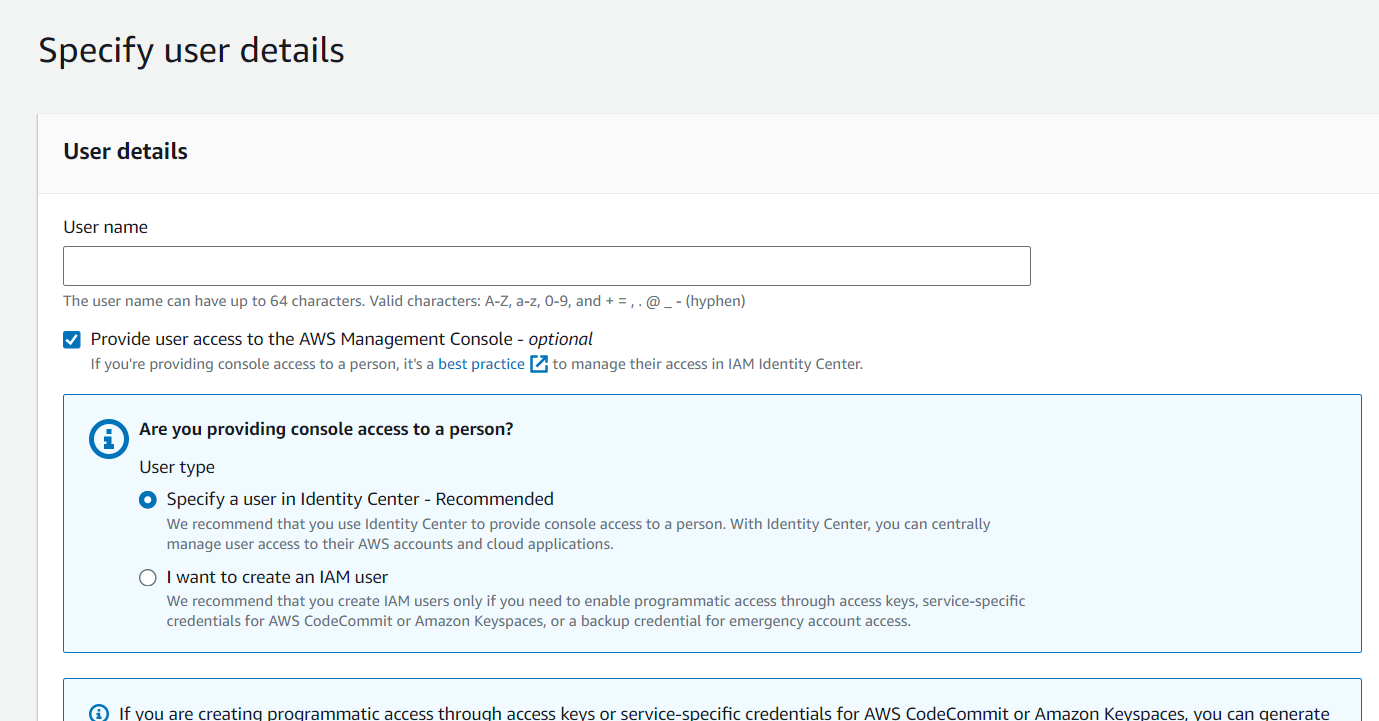
If you are working on AWS, you should be familiar with AWS Identity and Access Management. IAM is where you create and manage users and control their access to various AWS services. When setting up an IAM user, you might notice a message about IAM Identity Center, especially when providing access to the AWS Management Console. So, what exactly is AWS IAM Identity Center?
AWS IAM Identity Center: An Overview
Previously called AWS Single Sign-On (SSO), IAM Identity Center is a central hub for managing user access across multiple AWS accounts and integrated applications. It allows you to create or connect your workforce users in one place, simplifying access management across your AWS environment.
IAM Identity Center enables you to connect your existing workforce directory or create users directly within IAM Identity Center for use across AWS. Whether you're using popular cloud identity providers like Okta, Ping Identity, Azure Active Directory, JumpCloud, CyberArk, or OneLogin, IAM Identity Center can integrate with them seamlessly.
Key Features of IAM Identity Center
Centralized User Management: Manage all your users from one place for multiple AWS accounts and applications.
Single Sign-On (SSO): Users can log in once and access all their AWS accounts and apps.
Integration with AWS Organizations: Manage access across multiple AWS accounts using AWS Organizations.
Support for SAML 2.0: Easily connect with cloud-based apps like Microsoft 365 and Salesforce.
Multi-Factor Authentication (MFA): Add an extra layer of security with MFA for all users.
Customizable User Roles: Create specific roles with different access levels based on user needs.
A Practical Example: Switching Between AWS Accounts
Imagine you have three AWS accounts: Dev Account, Test Account, and Prod Account. If you’re only using traditional AWS IAM, you’ll need to log in separately to each account and manage separate secret access keys and access key IDs. This can become quite painful, especially if you need to switch between these accounts frequently throughout the day.
With IAM Identity Center, once everything is set up, you’ll have a separate login page where you can see a list of all your AWS accounts and other configured applications like Microsoft 365 or Salesforce. This central access point makes managing multiple accounts much easier and more efficient.
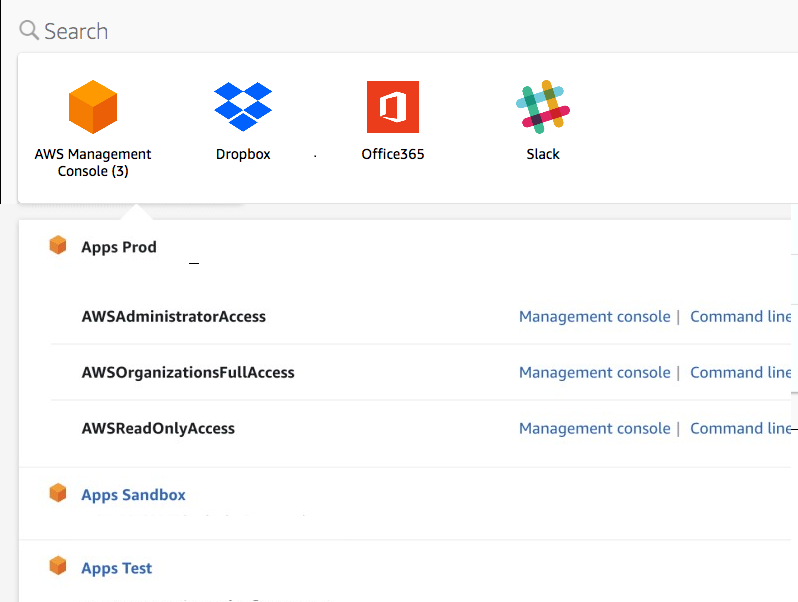
IAM vs IAM Identity Center
| IAM | IAM Identity Center |
| Ideal if you’re not using AWS Organizations. | Works seamlessly with AWS Organizations. |
| Best for managing identities and access within a single AWS account. | Designed for managing access across multiple AWS accounts and applications, though it can also be used for a single account. |
| Recommended for command line and programmatic access, but not for console access. | The recommended approach for managing console access, as well as command line and programmatic access (like access keys and secret keys). |
Enabling AWS IAM Identity Center and Setting Up AWS Account Access for an Administrative User
To get started with AWS IAM Identity Center, you'll first need to enable it. This process involves choosing an identity source, such as connecting to an existing directory or creating users directly in IAM Identity Center. After that, you’ll create an administrative permission set, which defines the permissions your admin user will have. Finally, you'll set up access to your AWS accounts for this admin user, allowing them to manage resources across your environment.
For detailed steps on how to complete this setup, please refer to the official AWS documentation here.
Conclusion
AWS IAM Identity Center simplifies the process of managing user access across multiple AWS accounts and applications, providing a centralized, user-friendly platform. For anyone juggling multiple AWS environments or integrating various cloud-based applications, IAM Identity Center is an invaluable tool.
Subscribe to my newsletter
Read articles from Vallamkondu Sai Varun directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
