Self-Sovereign Identity (SSI) in DevSecOps: Enhancing Security and Privacy in User Authentication
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
Introduction
In today's digital landscape, the need for secure and privacy-preserving user authentication has never been more critical. Traditional identity management systems, often centralized, expose users to risks such as identity theft, data breaches, and privacy invasion. Enter Self-Sovereign Identity (SSI), a revolutionary approach that empowers individuals to take control of their digital identities, eliminating the need for centralized identity providers. In the context of DevSecOps, where security is paramount, integrating SSI can significantly enhance the security and privacy of user authentication processes.
Understanding the Problem: The Risks of Centralized Identity Providers
Traditional identity management systems rely heavily on centralized identity providers (IdPs) like Google, Facebook, or enterprise-specific solutions. While these systems offer convenience, they also create single points of failure. A breach in an IdP can compromise millions of user identities. Moreover, users have little control over their data, leading to privacy concerns and potential misuse.
Real-World Example: The Equifax Breach
One of the most infamous examples is the Equifax breach of 2017, where the personal information of over 147 million individuals was exposed. The breach was possible because a centralized system stored vast amounts of sensitive data. If SSI had been implemented, users would have had control over their own data, and the breach could have been mitigated.
Self-Sovereign Identity (SSI): A Paradigm Shift
SSI shifts the control of digital identities from centralized authorities to individuals themselves. In an SSI model, users manage their credentials in a digital wallet and can share them with service providers as needed, without relying on a central authority. This not only enhances security by reducing the attack surface but also ensures privacy, as users can share only the necessary information without revealing more than required.
Integrating SSI into DevSecOps Workflows
Integrating SSI into DevSecOps pipelines ensures that security and privacy are built into the very fabric of user authentication and authorization. Here's how SSI can be effectively implemented:
1. Digital Identity Wallets: Users store their digital credentials in secure wallets, which can be software-based or hardware-based. These wallets interact with the DevSecOps pipeline to authenticate and authorize users.
2. Decentralized Identifiers (DIDs): Instead of usernames and passwords, SSI uses Decentralized Identifiers (DIDs), which are unique and can be verified across different systems without revealing sensitive information.
3. Verifiable Credentials: When a user needs to access a service, they present verifiable credentials from their wallet. These credentials are cryptographically signed and can be verified by the service without contacting a central authority.
4. Blockchain for Trust: A blockchain or distributed ledger is often used to manage the issuance and verification of DIDs and credentials, ensuring trust without a centralized entity.
Real-World Implementation: A Use Case in Financial Services
Imagine a financial services company that wants to ensure secure and privacy-preserving access to its services for both customers and employees. Instead of using traditional login methods, the company integrates SSI into its DevSecOps pipeline.
Step 1: Issuance of DIDs and Credentials
The company issues DIDs to all users (both customers and employees) and provides them with verifiable credentials for their roles.
Step 2: Integration with the DevSecOps Pipeline
The DevSecOps pipeline is configured to interact with users' digital wallets. For example, when an employee needs to deploy code or a customer needs to access their account, they use their digital wallet to present verifiable credentials.
Step 3: Authentication and Authorization
The pipeline verifies the credentials using the blockchain, ensuring that they are authentic and valid. This process happens without exposing sensitive information like passwords.
Step 4: Continuous Monitoring and Auditing
The system continuously monitors authentication attempts, ensuring that any suspicious activity is flagged and addressed in real-time.
Architecture Diagram
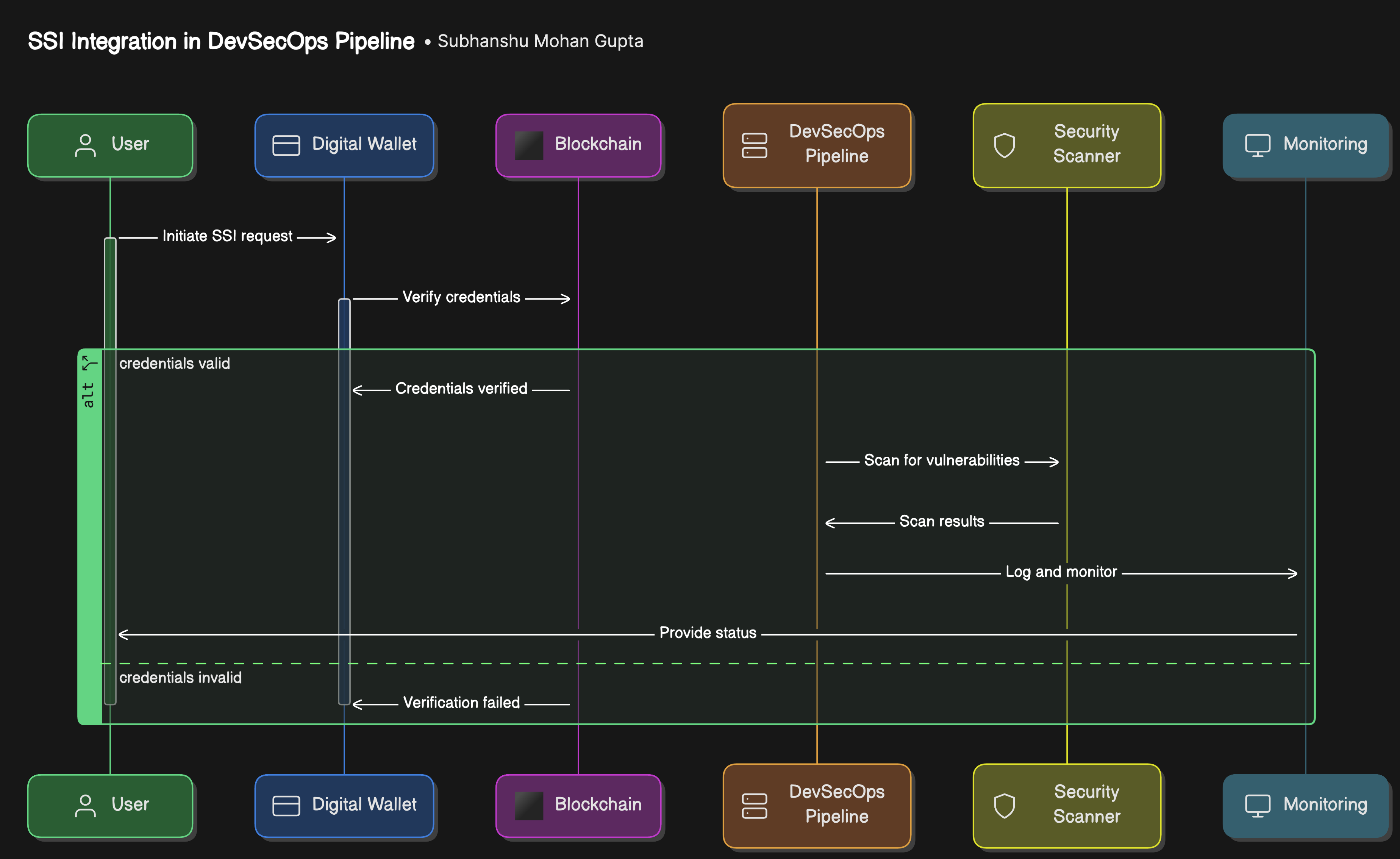
End-to-End Implementation with Testing
1. Setup Digital Identity Wallets: Start by setting up digital wallets for users, ensuring they are secure and easy to use.
2. Configure DevSecOps Pipeline: Integrate SSI protocols into your existing DevSecOps pipeline, focusing on authentication and authorization processes. This might involve using middleware that interacts with digital wallets and verifies credentials.
3. Testing the Implementation:
- Unit Testing: Test individual components, such as credential issuance and verification.
- Integration Testing: Ensure that the SSI components work seamlessly with the existing DevSecOps pipeline.
- User Acceptance Testing: Conduct testing with actual users to ensure that the SSI system is user-friendly and meets security and privacy requirements.
4. Deployment and Monitoring: Once testing is complete, deploy the solution in a production environment. Implement continuous monitoring to detect and respond to any security issues that arise.
Conclusion
By integrating Self-Sovereign Identity (SSI) into DevSecOps workflows, organizations can significantly enhance the security and privacy of user authentication and authorization. SSI not only reduces the risks associated with centralized identity providers but also empowers users to take control of their digital identities. As the digital landscape continues to evolve, SSI represents a crucial step forward in creating a more secure and privacy-focused internet.
Part 2 - The Blueprint | Stay tuned...
This is just the beginning of our journey into integrating Self-Sovereign Identity (SSI) into DevSecOps. In Part 2, we'll dive deeper into the nuts and bolts of the implementation, providing you with a comprehensive blueprint that will guide you through the technical intricacies step by step. Stay tuned for the next installment !!
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.