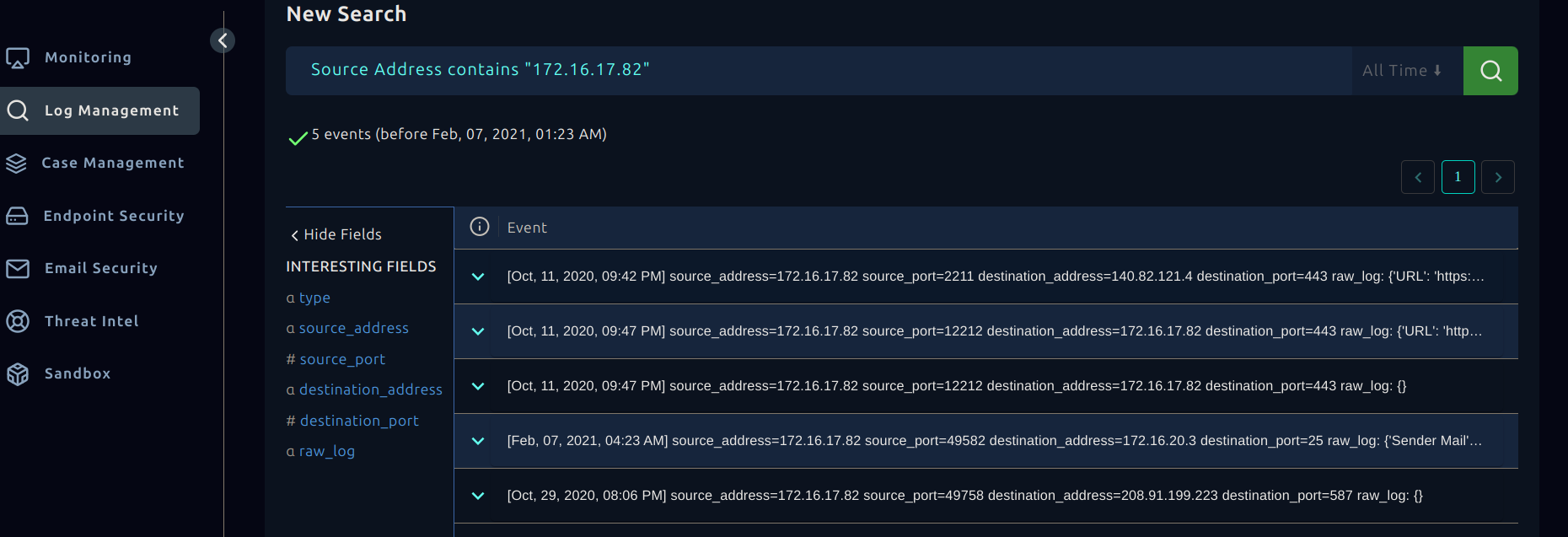
Event ID: 14 [SOC104 - Malware Detected]
 Dru Banks
Dru Banks
In this write-up, I investigate a "Malware Detected" alert from the LetsDefend SOC platform, focusing on SOC 104 Event ID: 14, involving googleupdate.exe. Using tools like VirusTotal and X-Force Threat Intelligence, along with log and process analysis, I determined that the alert was a false positive. The executable was confirmed legitimate, part of Google Chrome's update mechanism, and exhibited no malicious behavior. Recommendations included verifying the update action with the user and potentially whitelisting the executable.
Analysis
The first thing I did was get an overview of the event from the investigation screen and extract key details to help with further analysis, such as the source hostname, source address, and file hash.
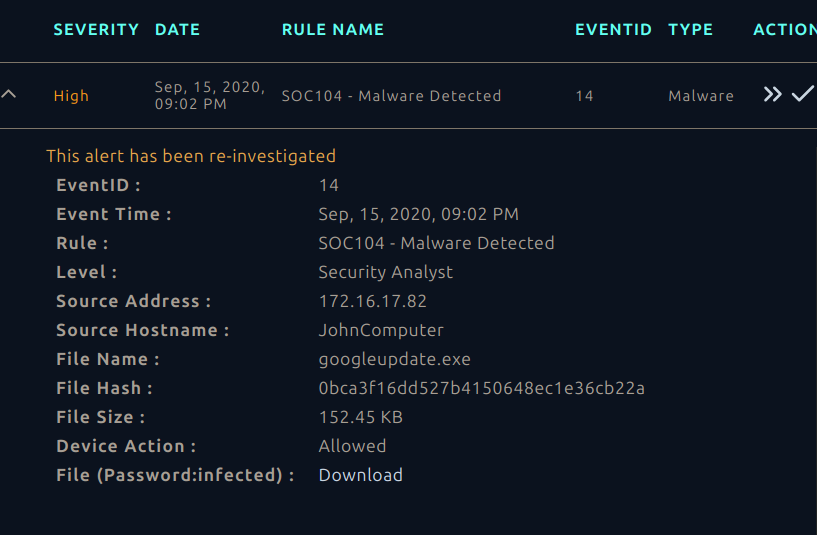
Inputting the MD5 hash into VirusTotal reveals clean results and shows that there is a positive match for the legitimate GoogleUpdate.exe file.
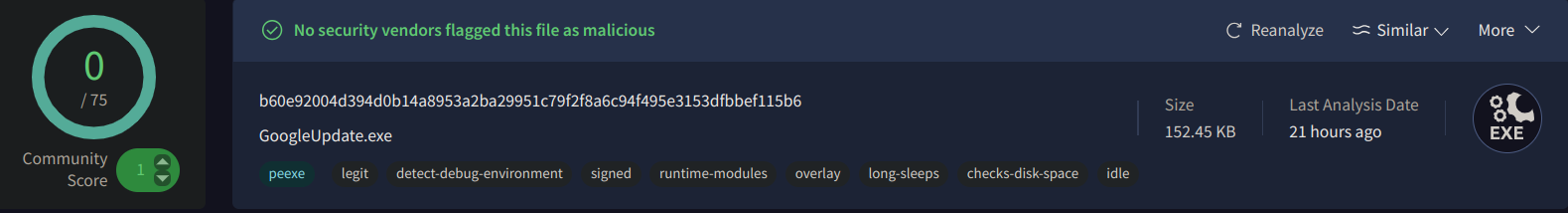
To be thorough, I also entered the hash into the X-Force Threat Intelligence platform. The results from X-Force were consistent with those from VirusTotal, indicating no signs of malicious activity associated with the hash.
I used the Log Management screen to search for any signs of malicious behavior from the endpoint by using its source IP. There were no logs around the time the GoogleUpdate.exe process was executed.
I then investigated the actual host for any suspicious indicators. Checking the process details for GoogleUpdate.exe showed nothing unusual. Interestingly, the file path matched the legitimate location where it would normally be. This strongly suggested it was a false positive.
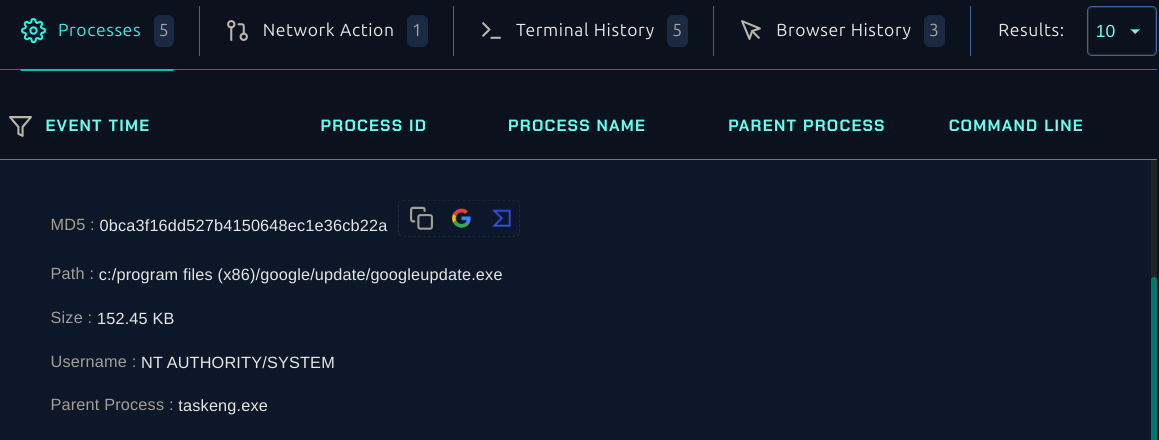
The user's browser history also shows behavior consistent with someone trying to figure out how to update Chrome.
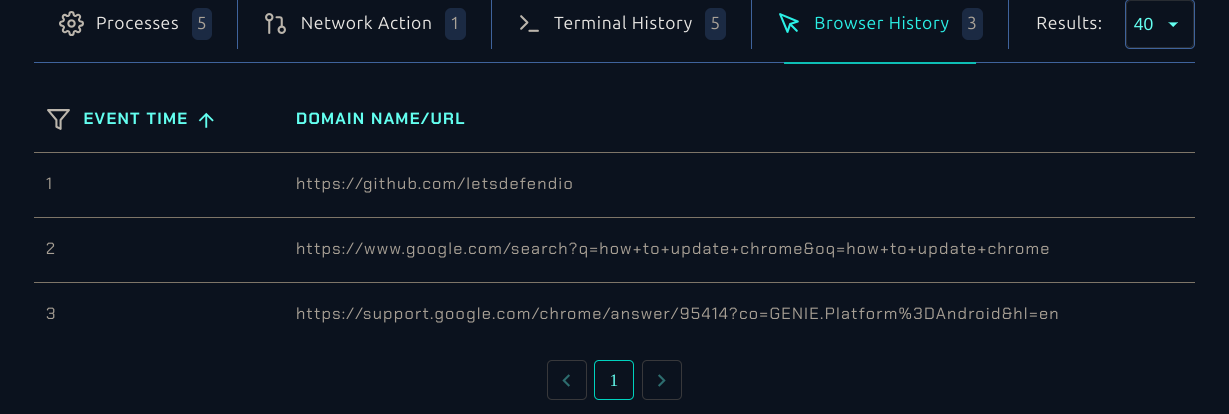
Out of curiosity, I used Urlscan to double-check the URL at the bottom and confirmed it is indeed a legitimate Google subdomain.
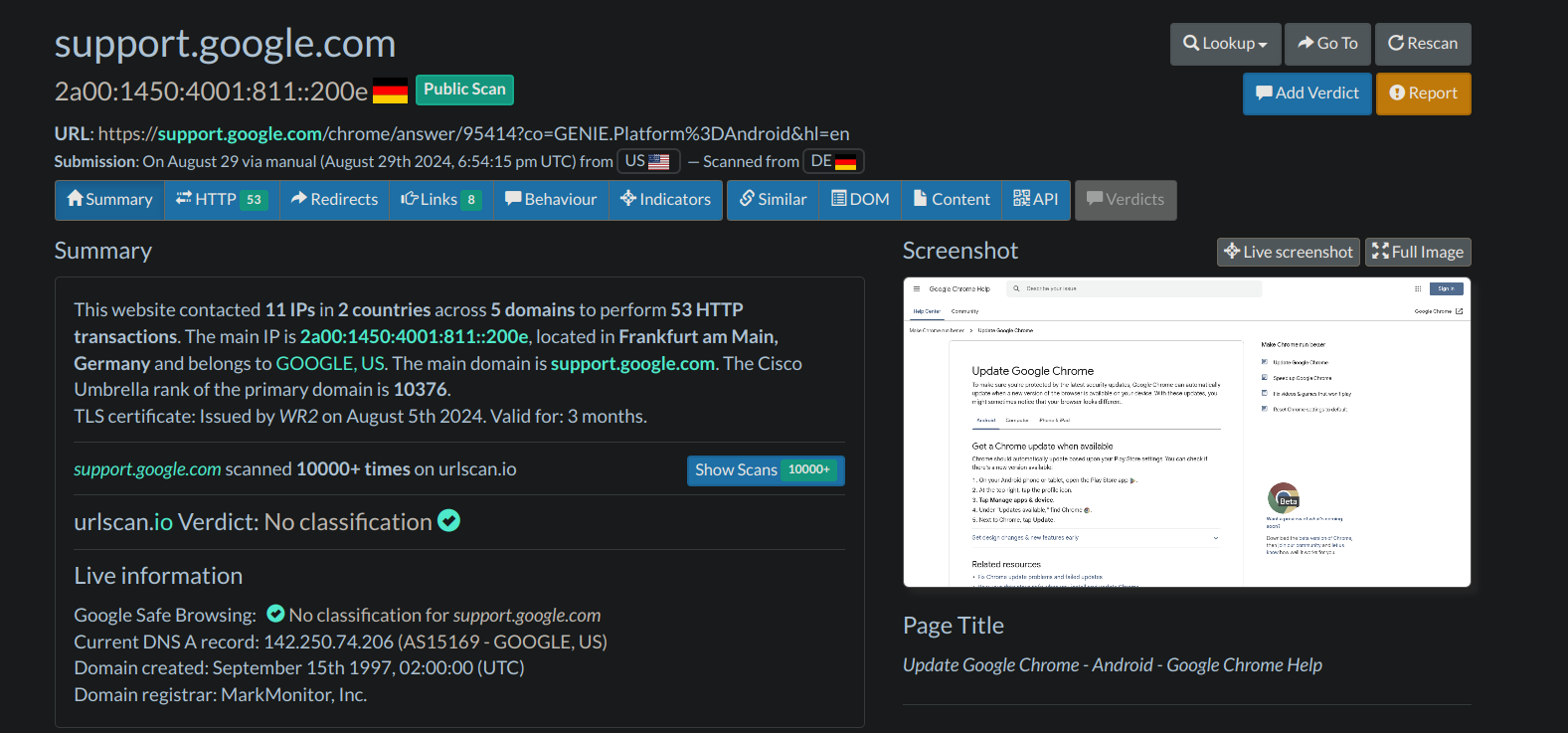
We have gathered a lot of evidence thus far, and all the pieces strongly point to the conclusion that this was a false positive and the user was simply attempting to update their Chrome browser using trusted information.
Closing the Alert
After feeling confident that I had taken the investigation as far as possible, I decided to close the case. LetsDefend has a feature that allows you to close cases by following a playbook. It's recommended that you do this for every alert to receive maximum points and build good habits.
Since the current categories don't really fit, we should mark the threat indicator as "other" because the event was triggered by a malicious process execution. Even though we now know it's a false positive, we should still use the rule name Malware Detected as a guide.
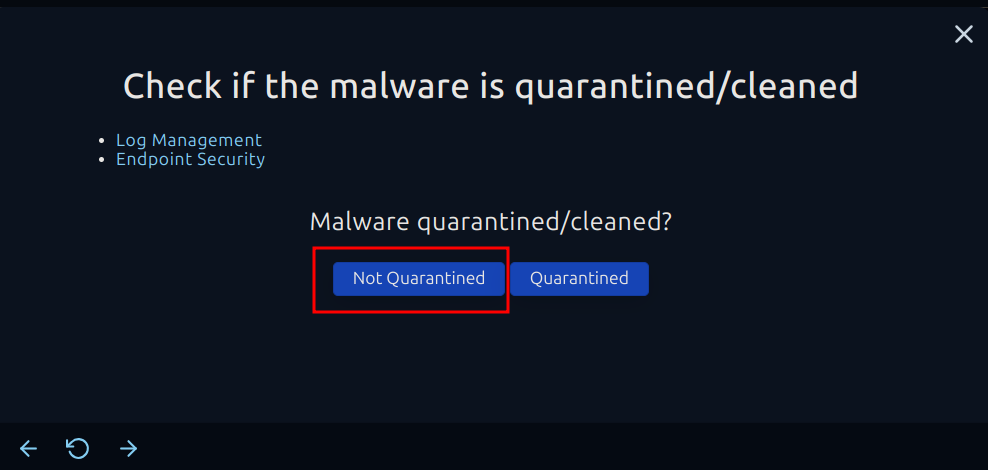
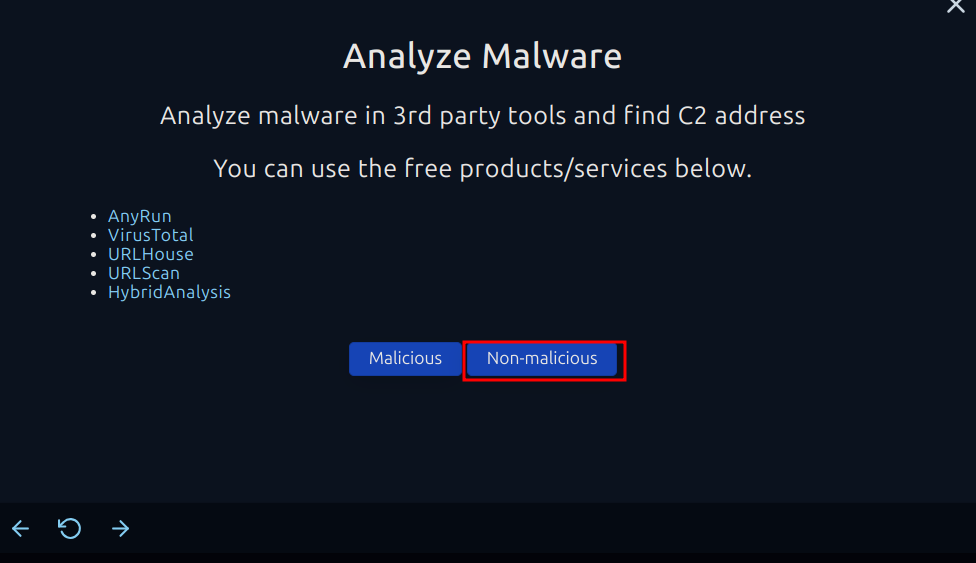
We decided not to quarantine the file and marked the event as non-malicious because it's legitimate. The investigation showed that the file path for GoogleUpdate.exe was exactly where it should be for a real Google update process. Plus, there were no red flags in the process details, logs, or browser history.
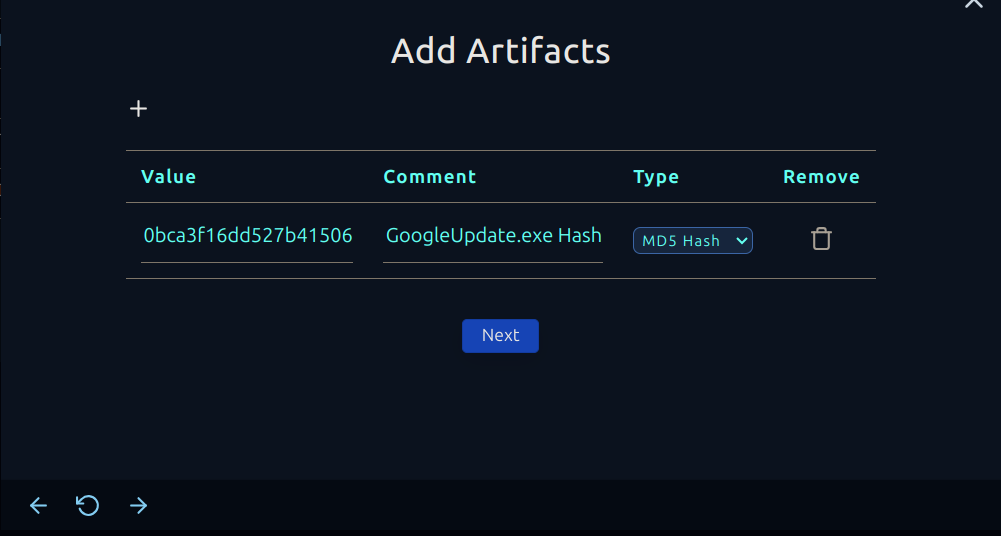
Here's a handy tip: even if it's a false positive, add the file hash for the process that triggered the alert as an artifact. You never know, the client might want to whitelist the executable, and this will make it a lot easier for them.
Summary
This alert was triggered by the suspicious execution of (googleupdate.exe) on the host JohnComputer on September 20th at 21:02 UTC.
After a thorough investigation, we concluded that the process aligns with legitimate Google Chrome update behavior.
Evidence supporting this conclusion includes correct file paths, relevant browsing history to Google support pages, neutral ratings for the process hash on threat intelligence platforms, and benign external connections within the network logs.
To ensure that this behavior is acceptable within the environment, it is recommended to verify with the user if they initiated the update. Confirming that this action was performed by the actual user will help rule out any potential unauthorized activity. If it is acceptable behavior, whitelisting the file will prevent further false alarms.
If you have any further questions or concerns, please contact the LetsDefend SOC.
Subscribe to my newsletter
Read articles from Dru Banks directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Dru Banks
Dru Banks
I am a cybersecurity professional with a deep passion for offensive security, threat intelligence, reverse engineering, and malware analysis. I believe that 'knowledge is power,' and that at every opportunity, knowledge should be shared. My blog serves that purpose and will be a public source for my studies, including write-ups on various topics.