Unlocking SSI: The Ultimate Implementation Blueprint for DevSecOps
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
To implement Self-Sovereign Identity (SSI) in a DevSecOps pipeline, you'll need to follow several steps involving setup, integration, and testing. Below is a detailed technical guide along with a blueprint for the implementation.
Technical Implementation of SSI in DevSecOps
1. Setting Up the SSI Infrastructure
1.1. Digital Identity Wallets
- Tools: Select an SSI wallet provider like Hyperledger Indy, Sovrin, or uPort.
- Setup:
Install the wallet software for users (e.g., developers, admins, customers).
Configure wallets to store and manage Decentralized Identifiers (DIDs) and verifiable credentials.
- Ensure wallets are integrated with a key management system for secure private key storage.
1.2. Decentralized Identifiers (DIDs)
- Tools: Use DID registries such as Ethereum, Hyperledger Indy, or IPFS.
- Setup:
Register DIDs for users within the chosen blockchain or decentralized ledger.
Establish DID documents that include public keys, service endpoints, and other relevant metadata.
1.3. Verifiable Credentials
- Tools: Implement using W3C Verifiable Credential standards.
- Setup:
Define credential schemas based on your organization's needs (e.g., roles, access levels).
Use a credential issuer (e.g., an internal CA) to issue cryptographically signed verifiable credentials to users.
Store issued credentials in users' digital wallets.
1.4. Blockchain or Distributed Ledger
- Tools: Choose a blockchain like Hyperledger Fabric, Ethereum, or Corda.
- Setup:
Deploy a blockchain network or connect to an existing one.
Use the blockchain for registering DIDs and issuing/verifying credentials, ensuring transparency and immutability.
2. Integrating SSI with DevSecOps Pipeline
2.1. Authentication and Authorization Middleware
- Tools: Use middleware like Ory Hydra, Keycloak, or custom-built solutions.
- Setup:
Integrate the middleware with your CI/CD tools (e.g., Jenkins, GitLab CI, Bitbucket Pipelines).
Configure the middleware to interact with users' digital wallets to request and verify credentials during pipeline execution.
Use DIDComm (Decentralized Identity Communication) for secure communication between the pipeline and users' wallets.
2.2. Secure DevOps Tools Integration
- Tools: Modify or configure existing tools to work with SSI.
Jenkins/GitLab CI: Add plugins or webhooks to handle SSI-based authentication.
Ansible/Terraform: Integrate with the SSI middleware to verify credentials before deploying infrastructure.
Docker/Kubernetes: Enhance your container or cluster management with SSI-based access controls.
2.3. Access Management
- Tools: Use access management systems like Vault by HashiCorp or AWS IAM integrated with SSI.
- Setup:
Define access policies based on verifiable credentials.
Use SSI-based authentication to grant or deny access to sensitive resources, such as secrets, configurations, or production environments.
3. Testing and Deployment
3.1. Unit Testing
- Tools: Use testing frameworks like JUnit, PyTest, or Mocha.
- Setup:
Write test cases to ensure proper issuance and verification of DIDs and credentials.
Test the SSI middleware's interaction with the CI/CD pipeline.
3.2. Integration Testing
- Tools: Use integration testing tools like Selenium, Postman, or Robot Framework.
- Setup:
Test the end-to-end process of SSI-based authentication and authorization within the DevSecOps pipeline.
Ensure that the pipeline correctly handles valid and invalid credentials.
3.3. User Acceptance Testing
- Setup:
Conduct UAT with real users to validate the ease of use and reliability of the SSI integration.
Collect feedback and iterate on the implementation based on user experience.
3.4. Continuous Monitoring
- Tools: Use monitoring tools like Prometheus, Grafana, or Splunk.
- Setup:
Implement monitoring for authentication events, credential usage, and DID interactions.
Set up alerts for any suspicious activities, such as multiple failed authentication attempts.
Blueprint of Implementation
Below is a conceptual architecture diagram representing the integration of SSI into a DevSecOps pipeline.
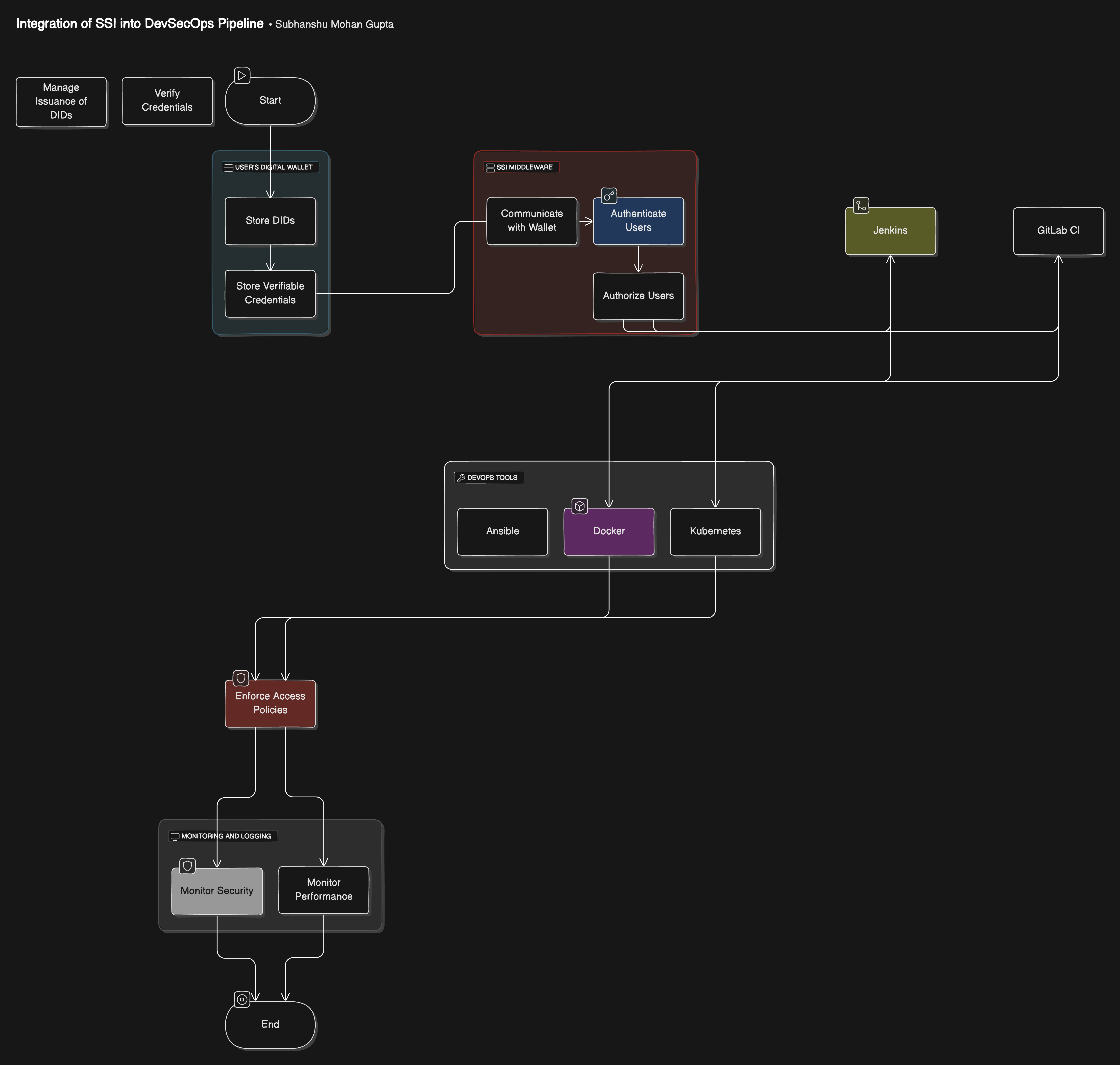
Explanation -
1. User's Digital Wallet: Stores DIDs and verifiable credentials.
2. Blockchain/Distributed Ledger: Manages the issuance and verification of DIDs and credentials.
3. CI/CD Pipeline (e.g., Jenkins, GitLab CI): Integrated with SSI middleware to authenticate and authorize users.
4. SSI Middleware: Manages the communication between the CI/CD pipeline and the user's wallet.
5. DevOps Tools (e.g., Docker, Kubernetes, Ansible): Enforce access policies based on verified credentials.
6. Monitoring and Logging: Continuously monitors the entire system for security and performance.
Conclusion
Implementing Self-Sovereign Identity (SSI) within a DevSecOps pipeline represents a significant leap forward in security and privacy. By decentralizing identity management, organizations can reduce the risks associated with centralized identity providers, empower users with control over their data, and ensure that authentication and authorization processes are both secure and privacy-preserving. The integration process, while technically complex, is well worth the investment for organizations prioritizing security in today's digital age.
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.