🔐 Understanding Refresh and Access Tokens: A Key Component in Modern Development
 Usama Naeem
Usama Naeem
Refresh and Access Tokens are critical for managing user authentication. In today’s digital world, security and seamless user experiences are essential. Whether you're building a web app, a mobile app, or even a complex microservice architecture, Refresh and Access Tokens are critical for managing user authentication. These tokens help keep interactions secure, ensuring that users can access the resources they need without constant re-authentication.
🔑 What Are Refresh and Access Tokens?
Access Tokens and Refresh Tokens are tools used to authenticate users securely and efficiently in modern applications.
Access Token: This is a short-lived token that grants the user access to specific resources or APIs. It typically lasts for a few minutes to a few hours before expiring.
Refresh Token: This is a long-lived token that allows the user to obtain a new Access Token without needing to log in again. Refresh Tokens can last for weeks or even months.
These tokens are often implemented using JWT (JSON Web Tokens) and are vital for maintaining secure user sessions over extended periods.
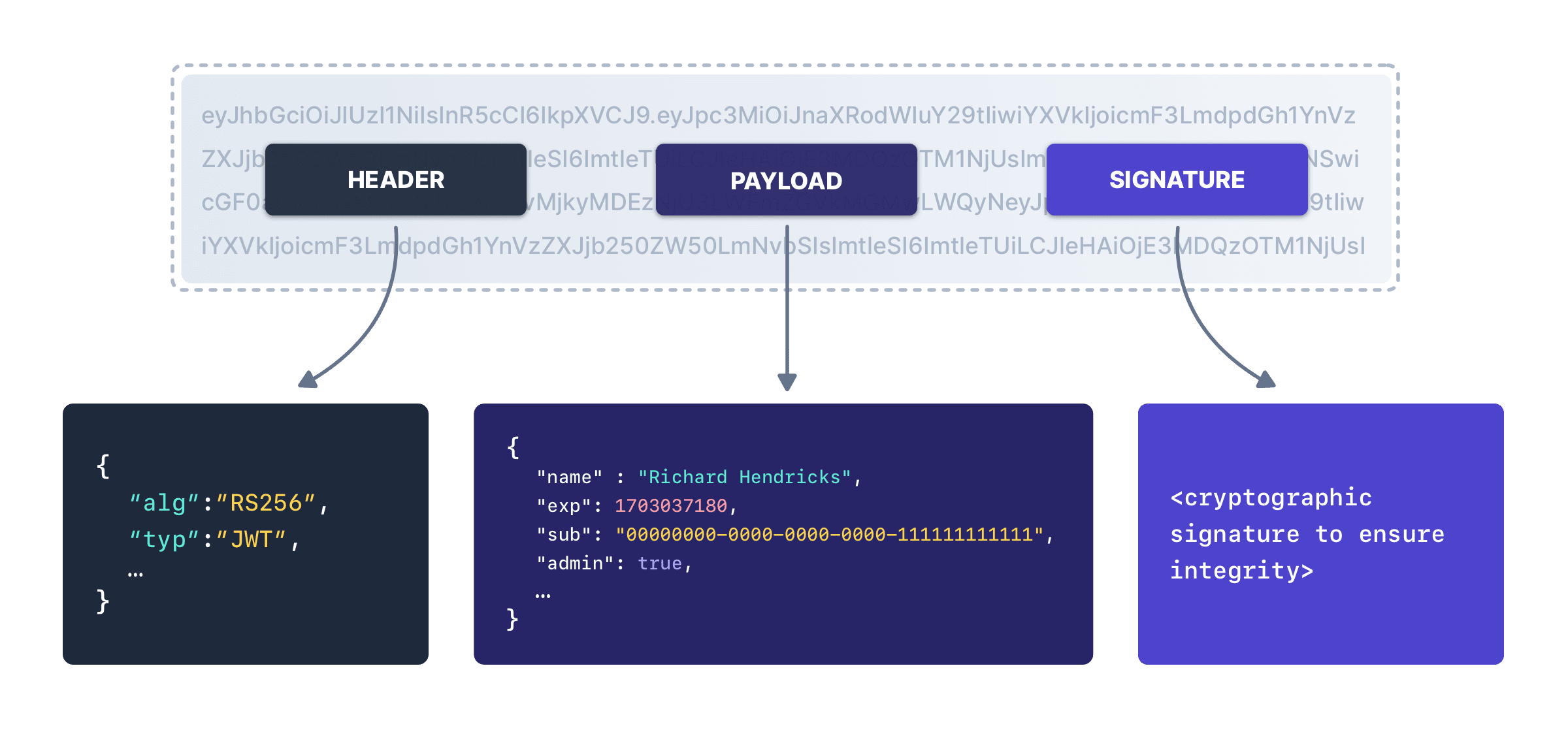
🔎 Example of JWT Structure
💡 Why Do We Use These Tokens?
Using Access and Refresh Tokens offers several key benefits:
🔐 Security: They provide a secure way to authenticate users, ensuring that unauthorized access is prevented.
🌍 Scalability: Tokens enable stateless authentication, which simplifies scaling applications across servers.
🛠️ User Experience: With Refresh Tokens, users don't need to log in repeatedly, making for a smoother, more seamless experience.
🔄 Microservices Compatibility: In architectures like microservices, tokens can be passed between services to authenticate requests effortlessly.
⚙️ How Do Refresh and Access Tokens Work?
Here’s a simplified step-by-step process:
🔓 User Login: The user logs in with their credentials (username, password).
🛡️ Access Token Issuance: Upon successful login, the server issues an Access Token and a Refresh Token.
🎟️ Access Token Usage: The Access Token is used to authenticate the user when accessing protected resources or APIs.
⏳ Token Expiration: When the Access Token expires, the user can use the Refresh Token to request a new Access Token.
🔄 Token Refresh: The server validates the Refresh Token and issues a new Access Token without requiring the user to log in again.
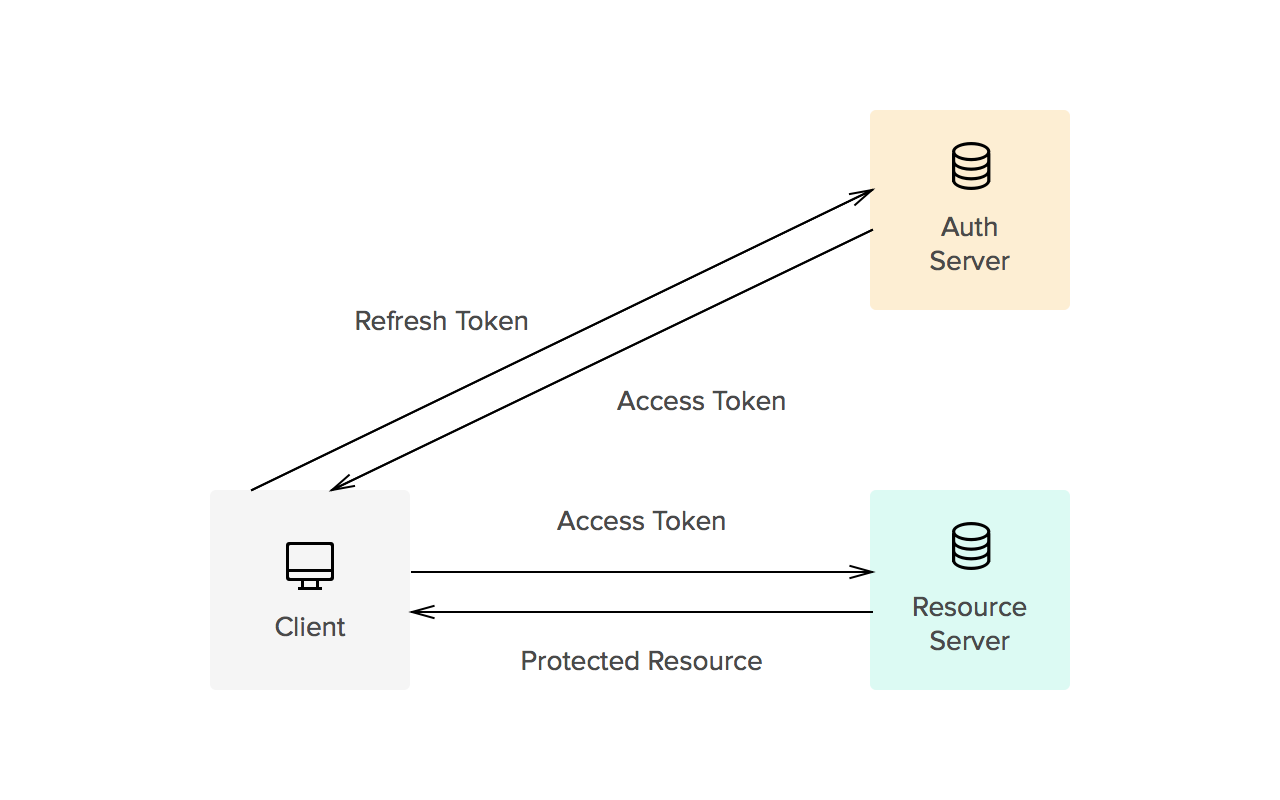

🔄 Lifecycle of Refresh and Access Tokens
🌟 Advantages of Using Refresh and Access Tokens
🔒 Enhanced Security: Short-lived Access Tokens minimize the risk of token theft, keeping your application safer.
✨ Improved User Experience: Users can stay logged in longer without interruption, enhancing their overall experience.
📉 Reduced Server Load: Stateless authentication means no session data is stored on the server, which reduces memory usage and boosts scalability.
⚡ Seamless Integration with Microservices: Tokens can easily be passed between different services, simplifying user authentication in a microservice architecture.
🎛️ Flexibility: Refresh Tokens can be independently revoked, giving developers fine-tuned control over user sessions.
🛠️ Additional Insights
🚫 Token Revocation: Revoking tokens can be tricky, but keeping a list of canceled tokens can help manage this issue.
🔐 Token Storage: It's important to store tokens securely on the client side. Using HttpOnly cookies can help protect against XSS (Cross-Site Scripting) attacks.
⏰ Token Refresh Strategy: Setting up a system to refresh tokens just before they expire can prevent sudden logouts and improve the user experience.
🔑 Multi-Factor Authentication (MFA): Adding MFA to tokens provides an extra layer of security, which is especially useful for sensitive applications.
🛡️ Best Practices for Secure Token Storage
📝 Conclusion
In today's development, Refresh and Access Tokens are essential for keeping user authentication secure and efficient. By understanding how these tokens work and their benefits, developers can build safer and more scalable applications. Using these tokens properly not only boosts security but also makes the user experience smoother, making them a crucial part of any strong authentication system.
Subscribe to my newsletter
Read articles from Usama Naeem directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
