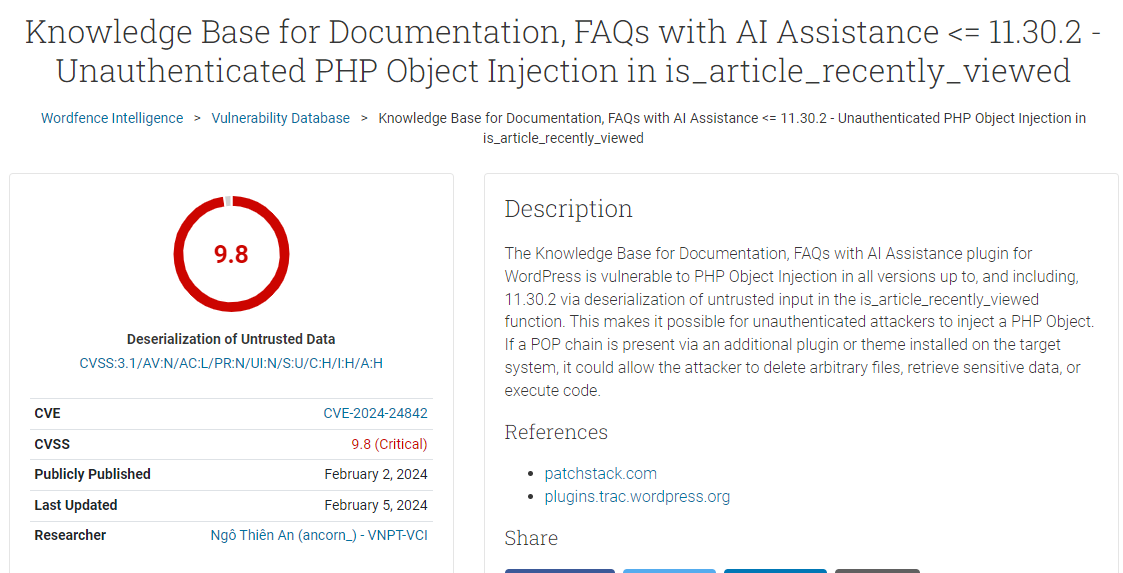
[CVE-2024-24842] Unauthenticated PHP Object Injection in plugin Knowledge Base for Documentation, FAQs with AI Assistance <= 11.30.2
 Ngô Thiên An
Ngô Thiên An
✋ Table of content
About Knowledge Base for Documentation, FAQs with AI Assistance plugin
The security vulnerability
The patch
Conclusion
About Knowledge Base for Documentation, FAQs with AI Assistance plugin
The plugin Knowledge Base for Documentation, FAQs with AI Assistance (versions 11.30.2 and below), which is estimated to have over 10,000 active installations. Comment Suggest edit Edit from here
This Knowledge Base plugin is a powerful documentation tool that helps you create and organize your documentation, FAQs, and articles.
💣 The security vulnerability
The Knowledge Base for Documentation, FAQs with AI Assistance plugin has been identified with an unauthenticated PHP Object Injection vulnerability. This vulnerability arises when user-input data is not adequately sanitized before being transmitted to the maybe_unserialize function, which serves as a wrapper for PHP's unserialize function. Comment Suggest edit Edit from here
Due to PHP's capability to serialize objects, an unauthorized user could supply customized serialized strings to an exploitable unserialize call, leading to the injection of arbitrary PHP object(s) into the application scope. This specific vulnerability was addressed in version 11.31.0 and assigned the identifier CVE-2024-24842.
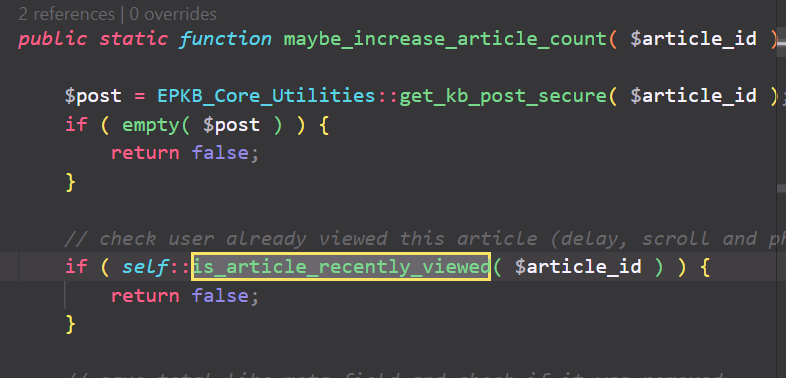
The root cause of the vulnerability lies within the is_article_recently_viewed function:
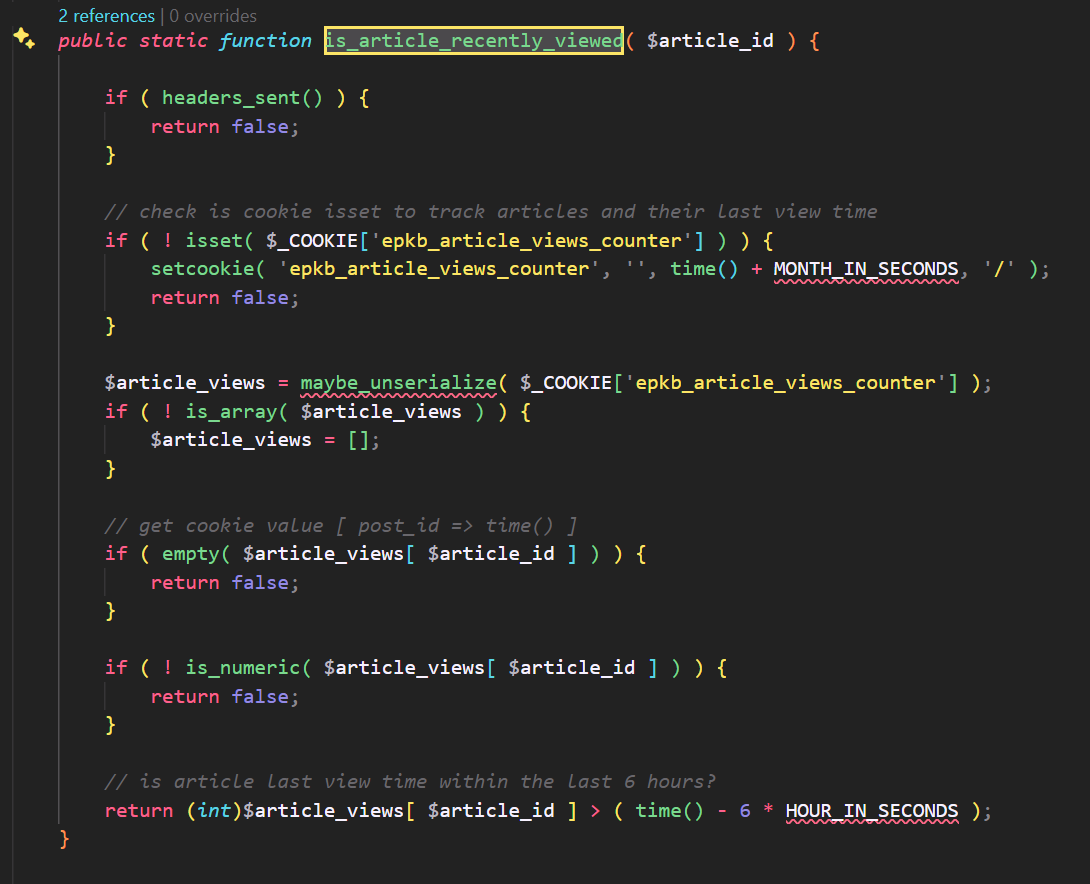
The is_article_recently_viewed function is invoked within the maybe_increase_article_count function to check if a user has recently viewed the article. Simultaneously, the maybe_increase_article_count function is called from the process_article_count function. However, the process_article_count function is invoked through the action epkb_count_article_view.
In the context of WordPress, if the prefixed action wp_ajax_nopriv is declared, this action can be invoked by unauthenticated user.
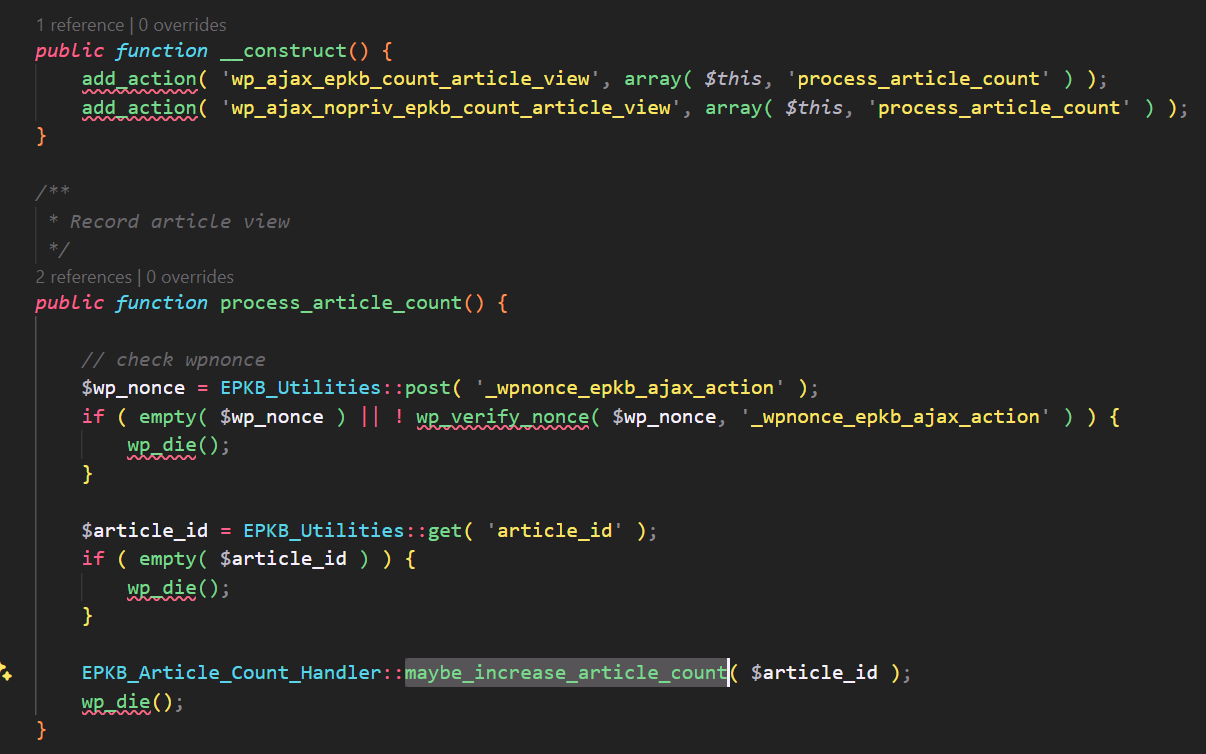
Consequently, this allows an unauthenticated attacker to exploit the PHP Object Injection vulnerability through the following sequence of functions: Comment Suggest edit Edit from here
Invoke the action epkb_count_article_view to trigger the process_article_count function > maybe_increase_article_count \> is_article_recently_viewed \> maybe_unserialize \> trigger chain
By sending a request to trigger the epkb_count_article_view action with the epkb_article_views_counter cookie containing a serialized payload, it becomes possible to inject code effortlessly.
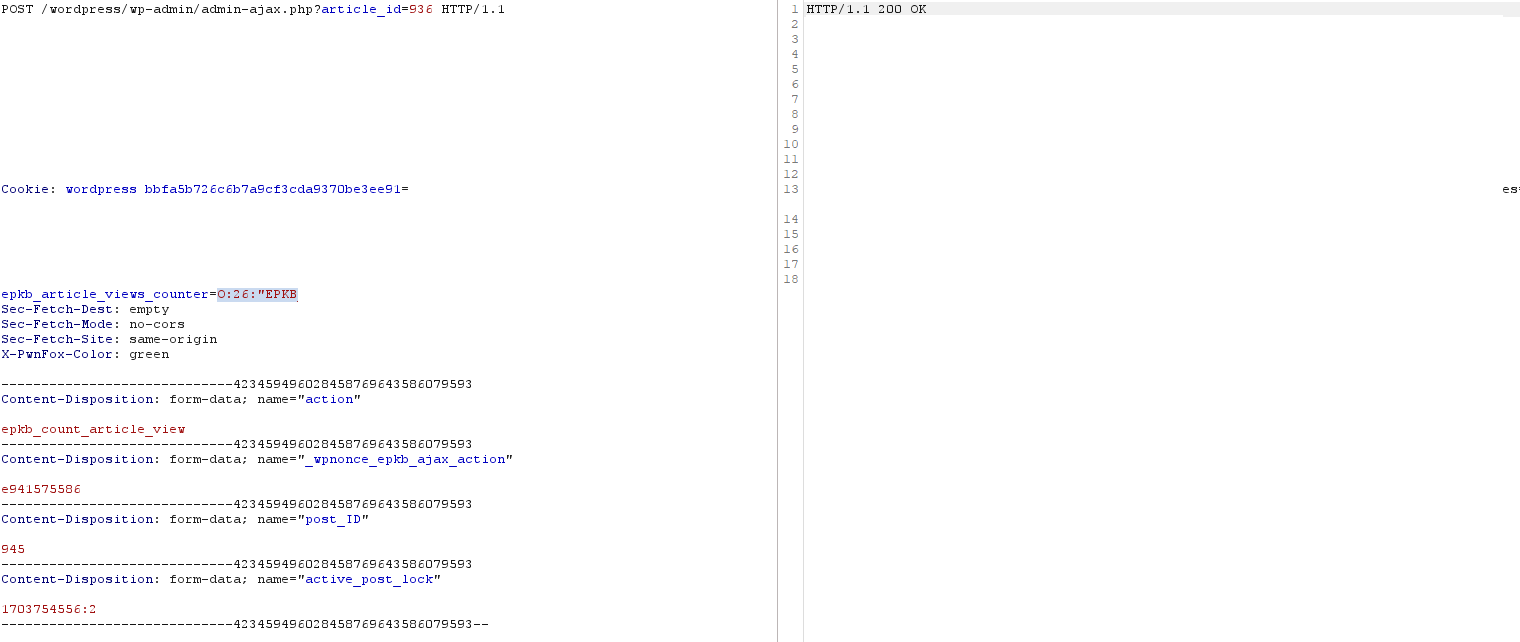
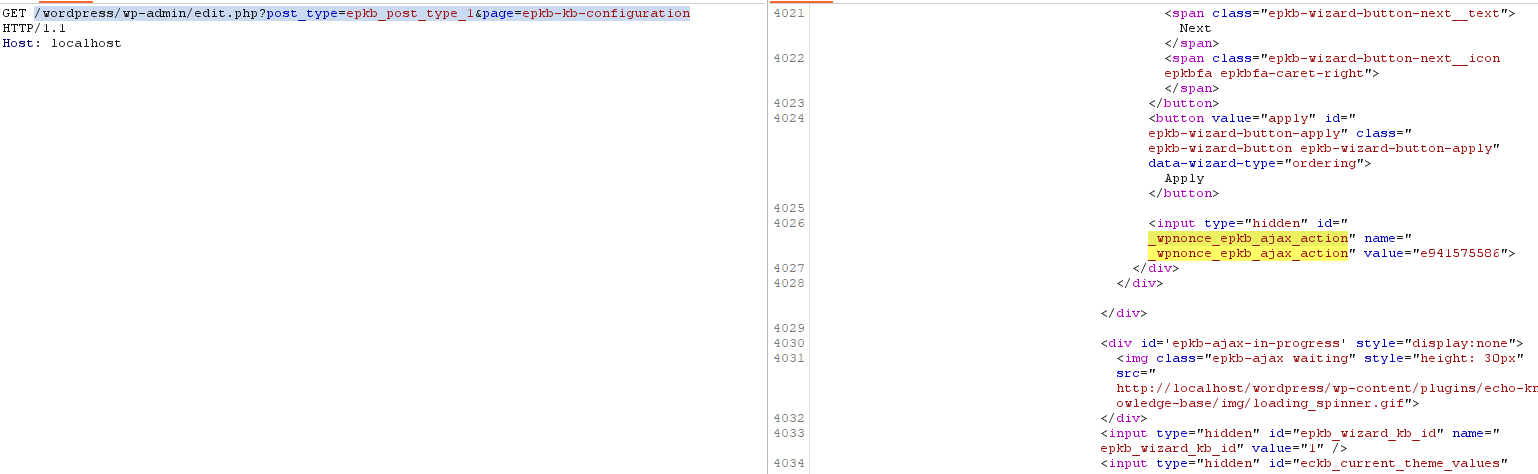
To obtain the nonce value to insert into the request, you can send request like this one:
The patch
Since the issue is mainly because the plugin uses the unsafe maybe_unserialize function, replacing the function should be enough to fix the issue. In this case, the vendor decided to use the JSON format to process the $_COOKIE['epkb_article_views_counter'] data. The patch can be seen below:
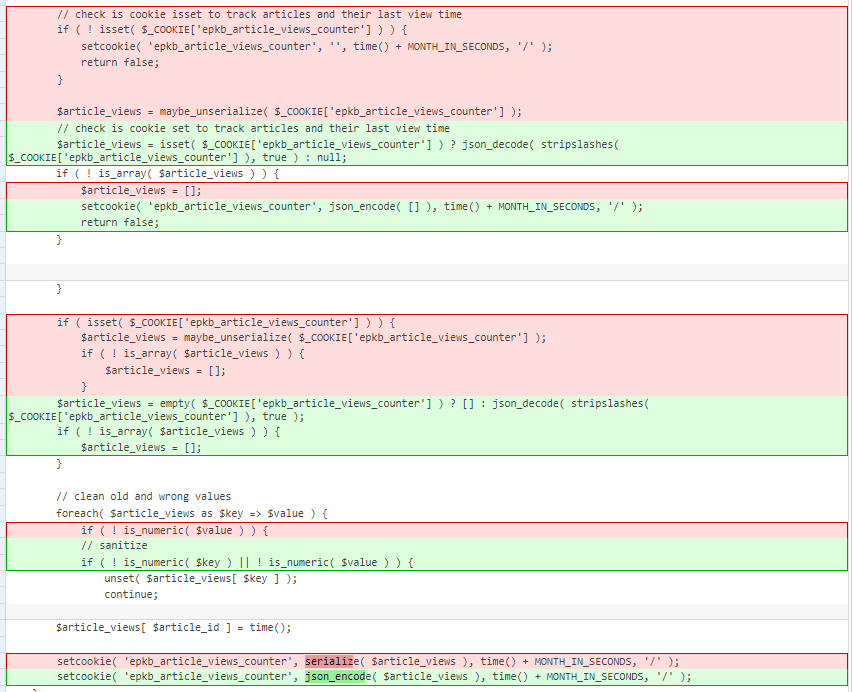
Conclusion
The maybe_unserialize function is a wrapper for PHP unserialize function which is one of the more sensitive processes that could lead to a security issue. In general, I am solely focused on searching for similar functions to identify multiple vulnerabilities like this one.
Subscribe to my newsletter
Read articles from Ngô Thiên An directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ngô Thiên An
Ngô Thiên An
CTFer | Pentester | Reseacher | All my CVE and WU @ancorn_ Mail: nta040702@gmail.com Cheer with me at https://www.buymeacoffee.com/ancorn