KubeLinter: A Comprehensive Guide to Kubernetes Manifest Linting
 D V Shashidhar Reddy
D V Shashidhar ReddyTable of contents
Introduction
This guide provides detailed instructions on using KubeLinter to analyze and improve Kubernetes manifests. Covering everything from installation and basic usage to advanced integrations, this resource is designed to help users at all skill levels master KubeLinter.
Overview
Explore why linting is essential for Kubernetes deployments, how KubeLinter enhances quality checks, and best practices for integrating it into workflows to ensure security, reliability, and compliance.
What is KubeLinter?
KubeLinter is a static analysis tool that scans Kubernetes manifests and Helm charts to identify potential errors, inconsistencies, and security vulnerabilities. It helps ensure that your Kubernetes deployments are compliant, reliable, and secure.
Why Use KubeLinter
Shift-Left Security: Integrate security checks early in the development pipeline with KubeLinter to identify vulnerabilities such as exposed ports or insecure container images before they reach production.
Consistency and Reliability: Enforce standards across Kubernetes manifests to ensure consistent configurations, reducing the risk of deployment failures and downtime.
Automation: Automating linting within CI/CD pipelines for continuous validation of configurations, catching errors and inconsistencies early in the development process.
Compliance: Ensure adherence to security policies, best practices, and regulatory requirements by using KubeLinter to enforce compliance in regular environments.
Getting Started with KubeLinter
Installation
- Using Go
To install by using Go, run the following command:
go install golang.stackrox.io/kube-linter/cmd/kube-linter@latest
- Using Homebrew (macOS):
To install by using Homebrew on macOS, Linux, and WSL, run the following command:
brew install kube-linter
- Using Docker:
- Get the latest KubeLinter Docker image:
docker pull stackrox/kube-linter:latest
- Add path to a directory containing your yaml files:
docker run -v /path/to/files/you/want/to/lint:/dir -v /path/to/config.yaml:/etc/config.yaml stackrox/kube-linter lint /dir --config /etc/config.yaml
- From source: Installing KubeLinter from source is simple:
- Clone the KubeLinter repository, but before cloning the repository install " Go " and then start cloning the repository.
git clone git@github.com:stackrox/kube-linter.git
- Then compile the source code. Where this will create the kube-linter binary files for each platform and place them in the
.gobinfolder.
make build
- Now you can start using KubeLinter, but once verify with the version to ensure you have successfully installed KubeLinter.
.gobin/kube-linter version
Running and Configuring KubeLinter
- Running Your First Lint
kube-linter lint <path-to-yaml-files>
This command checks all Kubernetes YAML files in the specified directory against default checks.
Understanding the Output: When you run the lint command, we might see the following output similar to the following:
Linting <path-to-yaml-files>...
File: deployment.yaml
---------------------------------------
Warning: Exposed port 8080 is not restricted (container-security/exposed-ports)
Error: Privileged container detected (container-security/privileged-containers)
File: service.yaml
---------------------------------------
Checks Passed: All checks passed
Summary:
- Files with Errors: 1
- Files with Warnings: 1
- Files Passed: 1
Errors: Critical issue that need fixing before deployment. In the example the error is "Privileged container detected" meaning that one of the containers is running with elevated privileges, which could pose security risks.
Warnings: Issues to review but not necessarily blocking deployments. Here, "Exposed port is 8080 is not restricted" is a warning that should be reviewed to ensure it meets the security policies.
Checks Passed: Manifests that pass all enabled checks. The service.yaml file passed all checks, including no issues.
- Customizing and Configuring
Lint a Specific Manifest:
kube-linter check --config <path/to/config.yaml> <path/to/manifest.yaml>
This command lints the specified manifest file using the provided configuration.
KubeLinter Rules and Checks: KubeLinter include built-in rules and checks for:
Security: Exposed ports, insecure container images, privileged containers.
Resource Usage: Resource requests and limits, over-provisioning
Best Practices: Consistent naming conventions, proper labels and annotations
Helm Charts: Chart validation, dependencies, and security
Customizing Checks: You can modify KubeLinter's behavior using a configuration file. For example, to disable a specific check:
rules:
- name: "container-security/privileged-containers"
enabled: false
This configuration will turn off the check for privileged containers, meaning that any manifests with privileged containers will no longer trigger an error.
Integrating KubeLinter into Workflows:
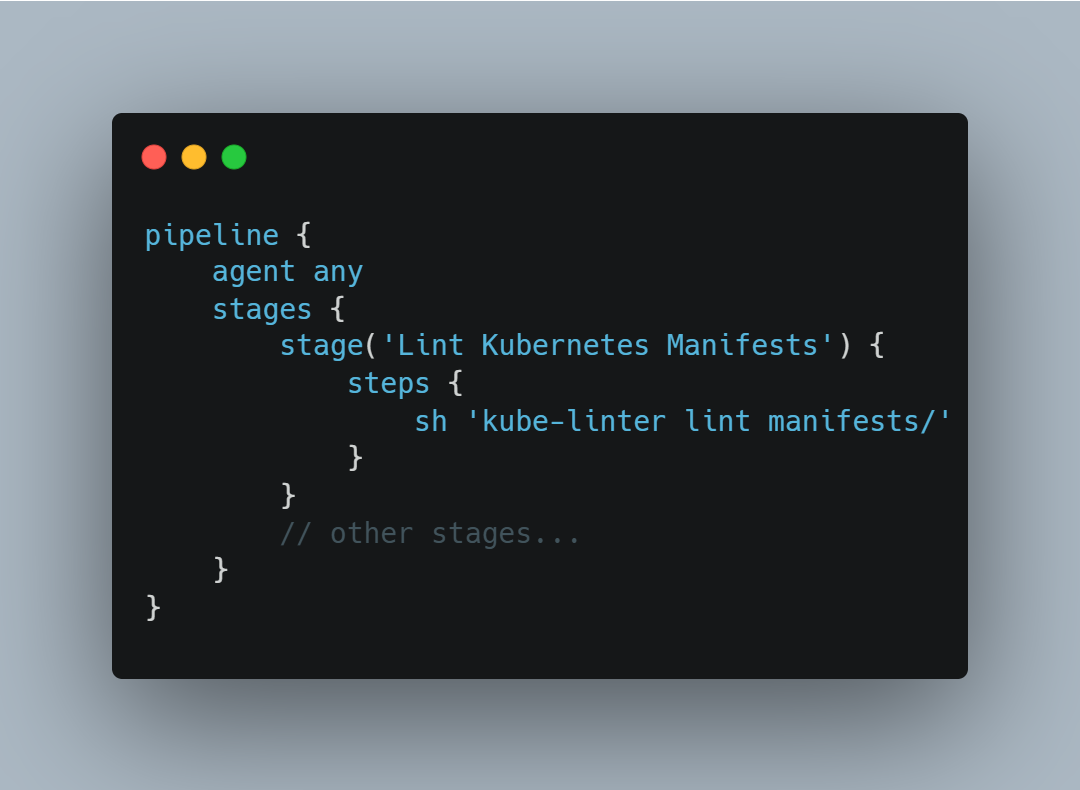
- Pre-Commit Hooks: Use tools like pre-commit to run the KubeLinter before code is committed, ensuring manifets are checked locally.
- repo: local
hooks:
- id: kube-linter
name: Kube-linter
entry: kube-linter lint manifests/
language: system
files: \.(yaml|yml)$
- CI/CD Pipeline Integration: Automate linting in CI/CD pipelines to catch misconfigurations early.
GitHub Actions:
name: Lint Kubernetes Manifests
on: [push, pull_request]
jobs:
lint:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Set up Go
uses: actions/setup-go@v2
with:
go-version: '1.17'
- name: Install Kube-linter
run: go install github.com/stackrox/kube-linter/cmd/kube-linter@latest
- name: Run Kube-linter
run: kube-linter lint ./manifests/
GitLab CI/CD:
stages:
- lint
lint_kubernetes_manifests:
image: golang:1.17
stage: lint
script:
- go install github.com/stackrox/kube-linter/cmd/kube-linter@latest
- kube-linter lint ./manifests/
Advanced Configuration and Usage
Customizing KubeLinter Checks:
- Default Checks:
KubeLinter includes default checks like no-latest-tag, no-privileged-containers, and required-labels. Customize these checks to fit your environment.
- Creating Custom Checks:
- Define a Custom Check:
customChecks:
- name: "check-no-debug-image"
message: "Images should not contain 'debug' in their name."
template: "image"
params:
- name: "notDebug"
value: "^((?!debug).)*$"
- Add to Configuration:
checks:
custom-checks: enable
- Run with Custom Config:
kube-linter lint <path-to-yaml-files> --config kube-linter-config.yaml
- Enabling/Disabling Checks: Customize which checks are enabled or disabled by default with a
.kube-linter.yamlfile.
checks:
disable:
- no-privileged
enable:
- require-run-as-non-root
Helm Chart Analysis
KubeLinter can also analyze Helm charts for potential issues, such as missing vales, invalid dependencies, and security vulnerabilities.
- Analyze Helm charts directly with KubeLinter:
kube-linter lint --helm-chart-dir <path-to-helm-chart-directory>
- Apply custom checks to Helm charts:
kube-linter lint --helm-chart-dir <path-to-helm-chart-directory> --config <path-to-config-file>
Extending KubeLinter with Plugins
Extend KubeLinter's functionality by using or developing plugins that introduce new checks or integrate with other tools. Plugins can help tailor KubeLinter to meet specific needs in complex environments.
Using Third-Part Plugins:
- Discovering Plugins: Explore available plugins in the KubeLinter community or GitHub repositories. Many plugins are designed to address specific compliance needs or integrate with other Kubernetes tools.
- KubeLinter Community:
Official Plugin Repository: Check the official KubeLinter plugin repository for curated list of plugins.
Community Forums: Engage with the KubeLinter community on forums like Slack or GitHub Discussions to get recommendations and learn about new plugins.
- GitHub Repositories: Search GitHub for repositories that contain Kubernetes plugins.
Developing Custom Plugins:
Create a New Plugin: Use the KubeLinter SDK or relevant SDK or relevant APIs to create custom plugins. These plugins can introduce unique checks or automate specific processes that align with the organization's standard.
Testing and Debugging: Test plugins locally with different Kubernetes manifests to ensure they work as expected. Debug any issues by using KubeLinter in verbose mode.
Performance Optimization
Optimizing KubeLinter for Large Scale Environments:
- Caching: Implement caching mechanisms to avoid reprocessing unchanged files during repeated linting sessions. This can significantly reduce linting time, especially in large projects.
Example: Use a caching layer in the CI/CD pipeline to store the result of previous lint runs:
lint-kubernetes-manifests:
cache:
key: lint-cache
paths:
- .lint-cache/
script:
- kube-linter lint ./manifests/ --cache-dir .lint-cache/
- Parallel Processing: Speed by linting by processing multiple files in parallel This will be particularly beneficial in environments with a large number of manifests or Helm charts.
Example: Utilize parallel execution features in CI/CD tools or custom scripts to run KubeLinter on multiple directories simultaneously.
find ./manifests/ -type f -name "*.yaml" | xargs -n 1 -P 4 kube-linter lint
Executing Non-Essential files: Improve performance by excluding directories or files that do not require linting, such as third-party libraries or certain deployment configurations.
Resource Allocation: Allocate sufficient resources like CPU, memory to the CI/CD runners or local machines running KubeLinter to prevent bottlenecks during the linting process.
Monitoring and Tuning: Continuously monitor the performance of KubeLinter especially in production environments, and adjust configurations, resource allocations, or parallelism levels as needed.
Best Practices
- Integrate Early and Often:
Include KubeLinter in development environments, CI/CD pipelines, and pre-commit hooks.
- Customize for Your Environment:
Adjust KubeLinter checks to align with specific security, compliance, and performance requirements.
- Review and Update Regularly:
Keep KubeLinter updated and review custom checks to stay aligned with best practices and policies.
- Automate Feedback:
Setup automated notifications for failed lint checks to provide immediate feedaback to developers.
- Foster a Culture of Compliance:
Promote the use of Kube-linter as a tool for enhancing security and stability rather than as a barrier.
Common Issues and Troubleshooting
Common Issues:
False Positives: Customize or disable checks that might trigger false positives.
Configuration Errors: Validate configurations with small test files before applying them broadly.
Troubleshooting Tips:
- Verbose Mode: Enable verbose mode for detailed output.
kube-linter lint --verbose <path-to-yaml-files>
- Debugging CI Failure: Check pipeline logs and output configurations and results for troubleshooting.
Conclusion
Kube-linter serves as a powerful and essential tool for anyone working with Kubernetes, enabling proactive identification of misconfigurations, enforcing best practices, and enhancing the security and stability of Kubernetes deployments. By incorporating Kube-linter into your development lifecycle whether through pre-commit hooks, CI/CD pipelines, or regular audits you ensure that your Kubernetes manifests adhere to industry standards and organizational policies.
Starting from the basics of installation and configuration, to exploring advanced custom checks and integration with Helm, this guide has demonstrated how Kube-linter can be leveraged to improve both small-scale development projects and large, production-grade environments. Adapting Kube-linter to your specific environment’s needs and automating it within your workflows will lead to consistent and reliable infrastructure, reducing human errors and allowing for smoother deployments.
Whether you're a beginner just getting started or an experienced user looking to implement advanced policies, Kube-linter is a key asset in ensuring high-quality Kubernetes infrastructure. Now, it’s time to integrate Kube-linter into your daily workflow and take full advantage of its capabilities to build secure, scalable, and compliant Kubernetes environments.
Additional Resources
Official Documentation: KubeLinter Documentation
GitHub Repository: KubeLinter
KubeLinter - Red Hat
kube-linter module - GO
🌟 Found value in this post?
Give me a boost by buying me a coffee! ☕
Buy Me a Coffee! It's like adding extra fuel to the content engine!!

Subscribe to my newsletter
Read articles from D V Shashidhar Reddy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

D V Shashidhar Reddy
D V Shashidhar Reddy
I'm a passionate DevOps Engineer with DevSecOps, Cloud, and SDLC expertise. I specialize in CI/CD pipelines, containerization, and infrastructure as code, and love sharing my knowledge.