App Subscription Paywall Bypass via HTTP Hijacking: How and How to Prevent It
 Harsh Vardhan Goswami
Harsh Vardhan Goswami
Attention all passengers! This is your captain speaking! You're about to be hijacked. No no, instead you're gonna be reading an interesting find that i came across this week. So there i was having tea with my favorite person (her), having a conversation about how mobile/desktop apps differentiate between free and paid users with the license, that actually got me thinking why not let's just dissect it. I opened up my toolkit, along with the app i wanted to buy for the longest and entered a random string into the license key and obviously it failed but then i went to my network requests that were being made through my MacBook (for those who don't know you can use http proxy apps for example the infamous BurpSuite or even Proxyman) Yeah you can keep an eye on the Radar! I'll tell you how so buckle up, because we're going off the radar into the dark skies!
Now, I know what you're thinking - "Captain, isn't this illegal?" Rest easy, my fellow sky pirates. We're not here to crash any systems or steal any data. We're simply just gonna learn and see how we can patch these vulnerabilities in our airspace(apps). And don't worry, i’ll be proposing some security measures that you can patch into your existing systems once we land in the legal waters.
So, grab your in-flight beverage and fasten those seatbelts - oh wait, wrong announcement. Grab that mouse and let's scroll through this turbulence!
This vulnerability is common among Apps using REST APIs as their security checkpoint for in-app purchases. Picture this: an app called "TheBoringApp" - it could be lurking on any operating system, be it macOS, Windows, or beyond. This vulnerability is as cross-platform as an international airport! Not the Changai one.
Our Plan of Action : How We're Bypassing Security
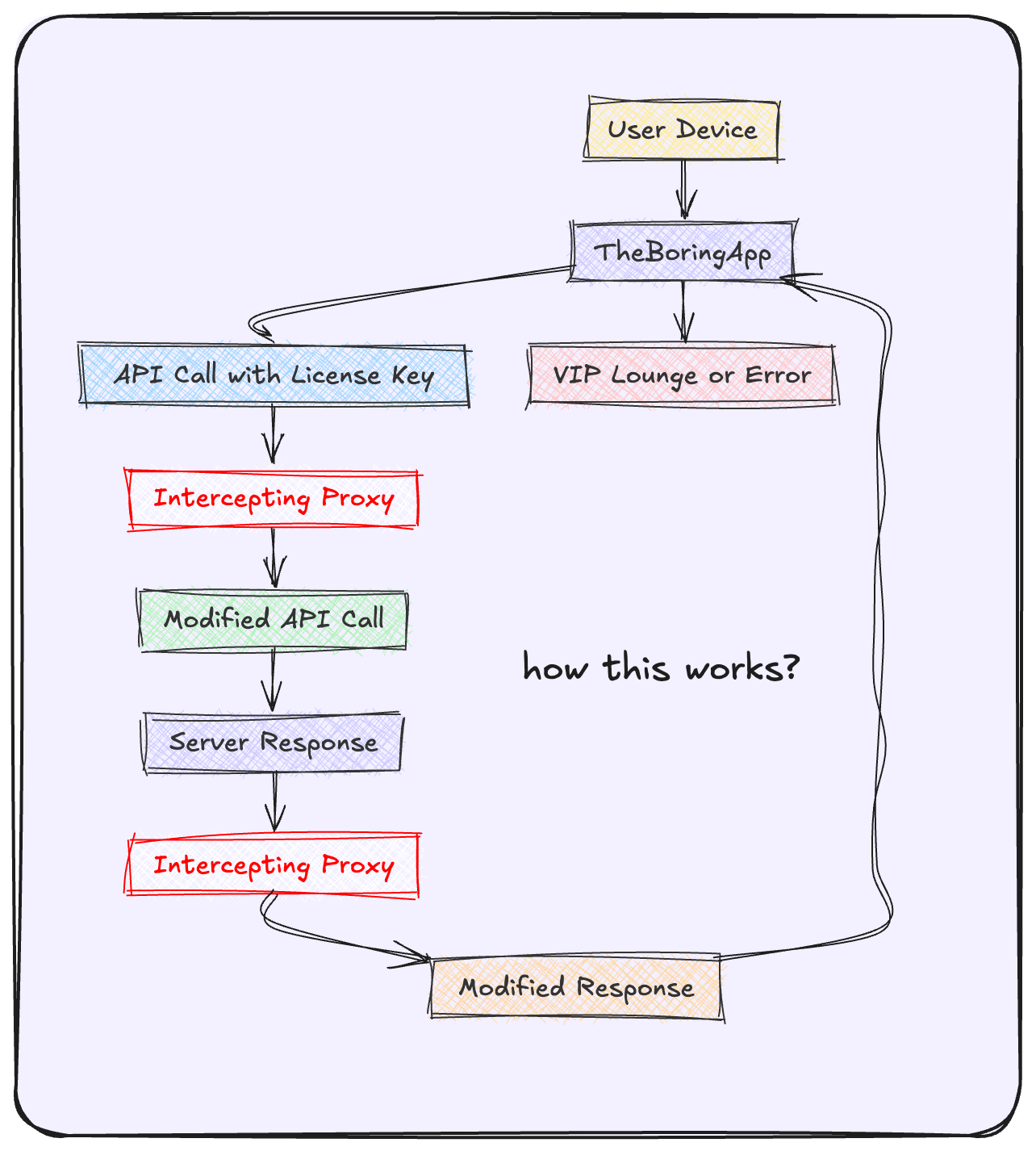
So we're going to use something called as HTTP interception. So in simple terms it's same as hijacking a plane and stealing all the beverages and getting access to first class suite literally for. Free. This process might vary depending on the app's security measures, but many are using the same old predictable patterns.
Here's the drill: The app sends out a signal - I mean, an API call - with your license key. It's expecting a response that'll either grant you access to the VIP lounge or send you packing. We're going to intercept that message and rewrite it mid-flight!
Now, imagine you're a secret agent at a fancy cocktail party. The app is trying to whisper sweet nothings to the server, but you're standing right between them, sipping your martini (shaken, not stirred). You hear everything, and you can even change the message before passing it on. That's HTTP interception in a nutshell, folks! It's like being the ultimate party crasher, but for data!
Prepare for takeoff, because we're about to see this network hijacking in action. Fasten your seatbelts, it might get bumpy!
First things first, we need to infiltrate the cockpit. Our weapon of choice? A proxy app like Proxyman—it's our networking transmission monitoring just like an air traffic controller on the ground.

Now, we're going to pose as a legitimate passenger. Launch the target app and input a fake license key—it's our forged boarding pass. Make sure it passes the basic security check, or we'll never make it past the gate.
Hit that verify button like you're engaging the thrusters. Watch closely as the app sends out a distress signal—I mean, an API request—with your bogus credentials. The response comes back negative, of course. But that's our first piece of intel on how this bird flies. This is the most crucial part. Write this on a paper if you keep forgetting things.
In Proxyman, we'll set up breakpoints and response scripts. These are our tools for rewiring the plane's controls mid-flight. We're looking for two potential weak spots: the request headers or the response body. It's like choosing between cutting the red wire or the blue wire—each app might be wired differently.
I know this sounds more complex than a 747's instrument panel, but stick with me. Soon, you'll be getting everything upto speed.
What the f are Interceptors?
Interceptors are like digital air traffic controllers for your app's communication. They allow you to inspect and modify data as it travels between your app and the server. Here's how they work:
- Outgoing Requests: Before your app's request reaches the server, an interceptor can modify it.
- Incoming Responses: Similarly, when the server sends back data, an interceptor can alter the response before it lands in your app. Think of it as changing the destination towards the trump tower.
These tools are required inorder to perform this VAPD, allowing us to manipulate the app's communication and potentially bypass its security measures. Remember, we're using this knowledge responsibly to improve app security, not to cause turbulence!
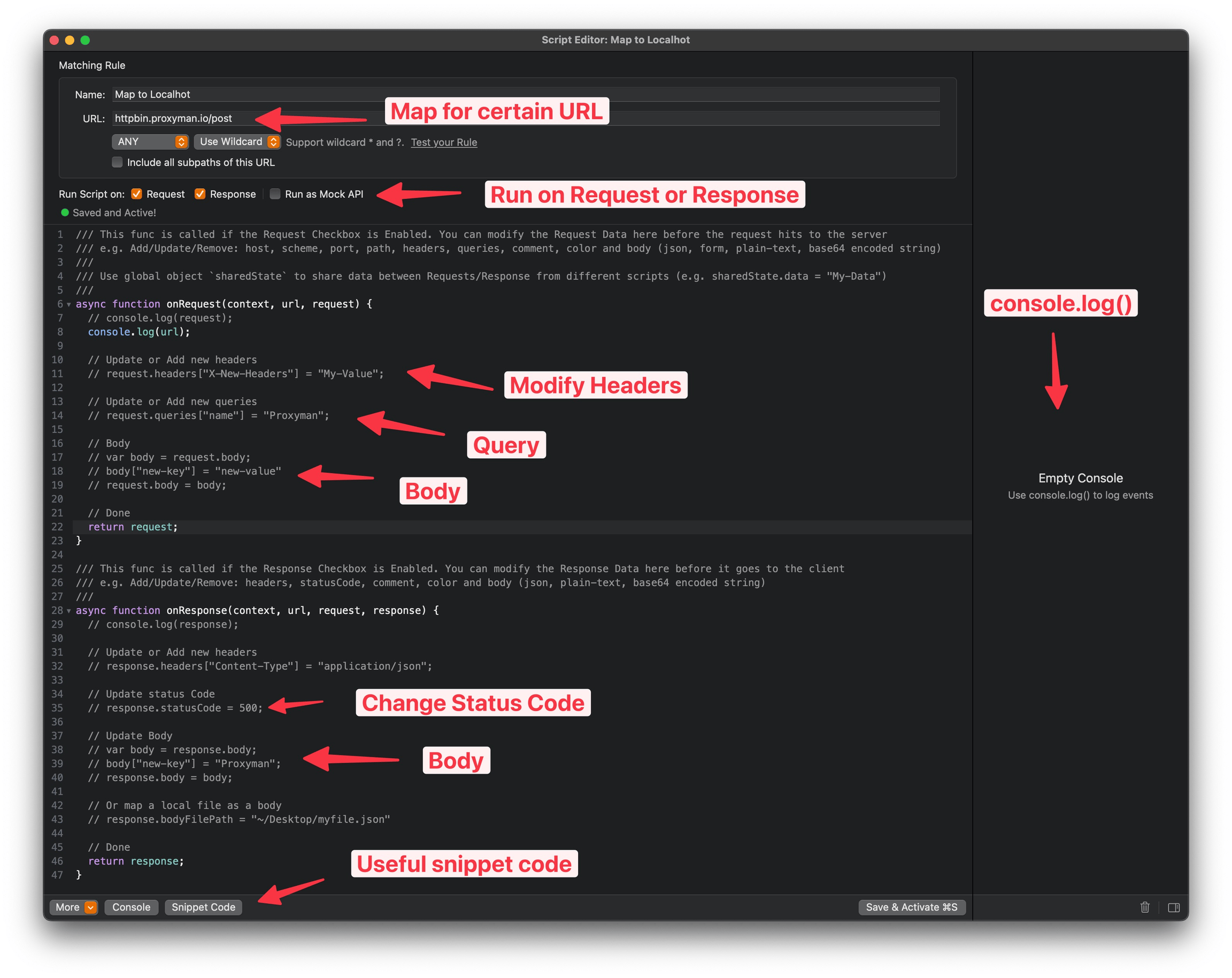
Here's a sample response interceptor:
Read more here: https://docs.proxyman.io/scripting/script
function onResponse(context, url, request, response) {
// Prepare for our daring mid-flight maneuver
response.headers["Content-Type"] = "application/json";
// Intercept the cargo manifest
var jsonBody = JSON.parse(response.body);
// Rewrite the flight plan
jsonBody.status = "cleared for takeoff";
jsonBody.subscription = {
active: true,
expirationDate: "2099-12-31" // We're flying to the future, folks!
};
jsonBody.features = ["first-class", "unlimited-baggage"];
// Seal the new flight plan
response.body = JSON.stringify(jsonBody);
// Clear for landing
return response;
}
It rewrites the response to give us first-class access and unlimited baggage allowance. But remember, this is just a simulated flight! We're exposing vulnerabilities, not actually breaching any systems. Use this knowledge responsibly, or you might find yourself in turbulent legal waters!
And boom! Hit save, jet back to our application, and slam that verify button again. Watch as your subscription status soars to new heights!
Wasn't that too simple? Now let's discuss the fortifications.
What can you do now? For app developers especially.
Use a SaaS-based model, hear me out. Even if your app has a one-time license, keep it valid for limited devices and limited years, maybe 99 years, same as a rental building lease. Isn't this hackable? No, up to almost 100% I've got a better way to do this.
How this works: When a user buys your subscription, you generate a license key which is signed using your RSA private keys. Your app can have a public key which will be a pair to the server-based private key. You can use any algorithm, be it the SHA or ECDSA (Elliptic Curve Digital Signature Algorithm) based keys.
crypto! No, not the kind that makes your wallet cry, but the kind that keeps your data safe and sound.
Imagine you and your best friend have a secret handshake. That's kind of what RSA and ECDSA are, but for computers. They're always coming up with new secret handshakes that are super hard for others to copy.
RSA is like the old-school kid. It uses numbers so big, they'd make your calculator have an existential crisis. ECDSA, on the other hand, is the new kid on the block. It's all about those curves - mathematical curves, that is! It's like doing a complex dance routine that's impossible to fake unless you know the exact steps.
Both these methods make sure that when your app and server are passing notes in class, no one else can read them or pretend to be either of them. It's like having an invisible ink that only you and your server bestie can see!
So this way, we'll have two-way verification of the license key. Before it even reaches your server, you can verify the user input with the public key. Once verified if it's legitimate, encrypt the request body using the public key. When it reaches the server, it can be decoded since we have the salt and everything, or you can just make a search in the DB with the encrypted string. Shouldn't be too heavy for you.
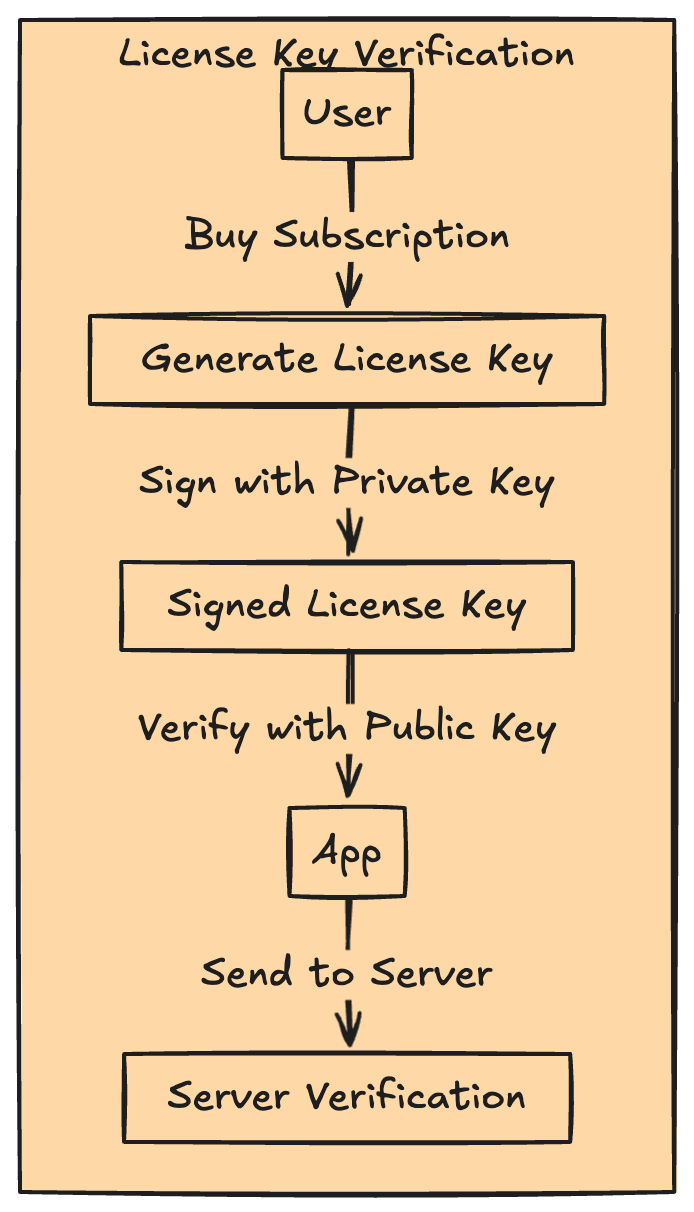
Not only that, with the license key, ask for the device fingerprint too. This way, you can bind the license with the device fingerprint. If next time it mismatches, you know what to do. This can be a many-to-many relation since you want users to have multiple devices attached to a license that you can control. You can give users an option to remove a device from the license which they no longer use.
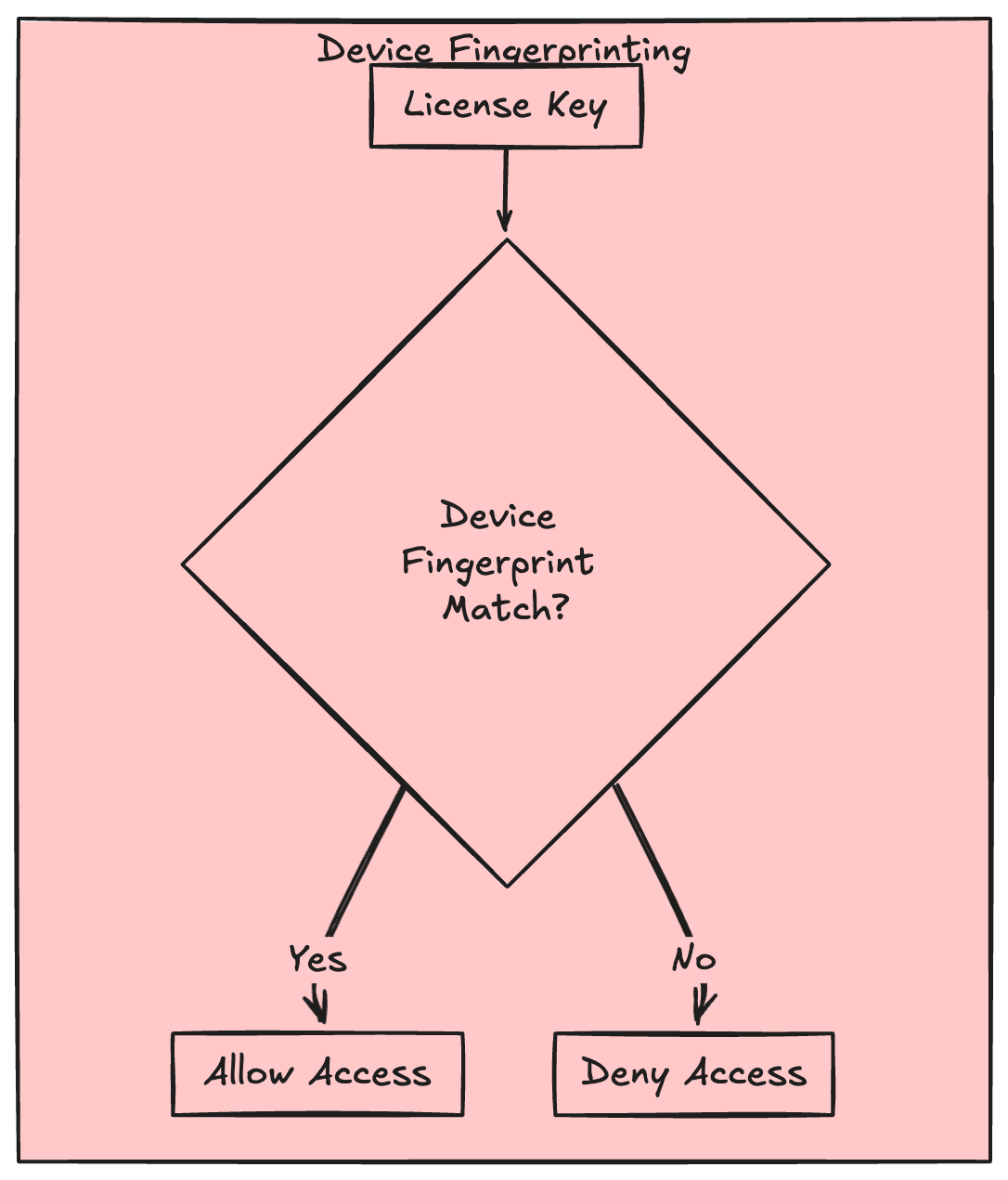
What i;m about to propose is just madness, but in case you have some secret app which is shady, you could use this.
For those who wanna go one level ahead with this, use passkey-based subscriptions, biometrics, or even physical security keys. Here's how this works: the application requests the device keychain to provide public and private keys. The public key is sent to the server, and then the server generates a challenge for the app to solve for registration. If that verifies, the device is registered. When authentication happens again, the same cycle goes, and the challenge is generated by the server since the server knows your public key. Once we have it generated, the application will try to solve the challenge with the private key. If everything goes well, you're safe. I'll put up a diagram for you to understand how it works.
Now, let's talk about passkeys - the superhero of the password less world! Imagine if your favorite superhero could create a unique, unbreakable captain America shield for every battle. That's what passkeys do for your accounts!
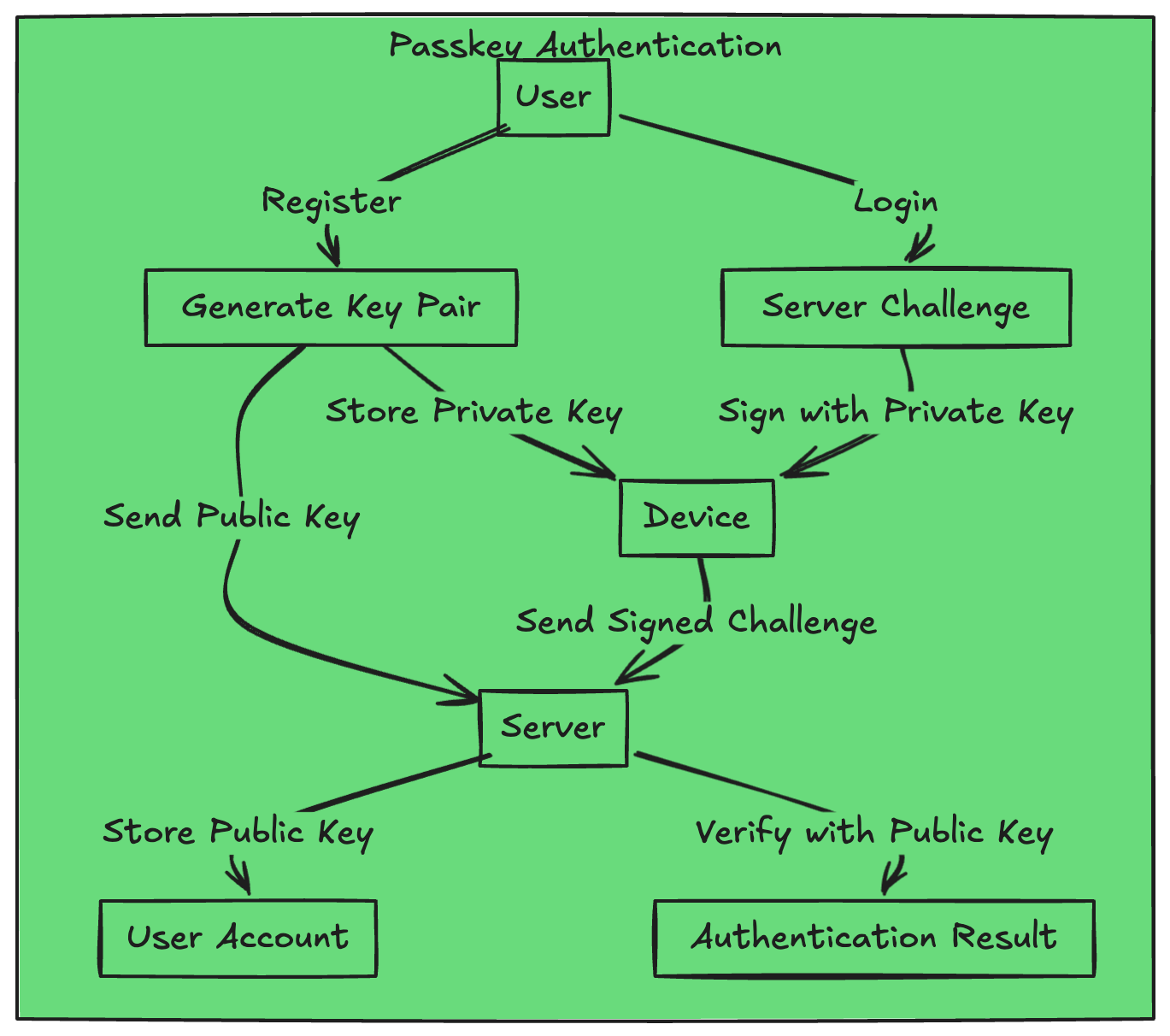
Instead of using the same old boring password for everything (we see you, "password123" users), passkeys create a special key pair for each of your accounts. It's like having a different secret hideout for each of your identities!
The best part? The secret part of this key (the private key) never leaves your device. It's like keeping your superhero costume locked in a vault that only you can access. Meanwhile, the public part (public key) goes to the server. It's like leaving your superhero logo around town so people know you're there to help, but they still can't figure out your secret identity.
This way, even if some sneaky folk tries to trick you into revealing your secret identity (that's phishing, by the way), they can't! Because your secret is locked up tighter than Fort Knox, and you don't even need to remember it. How cool is that? Right. I just love em. It's a hassle for users but it keeps em safe. You could probably use it as your authentication layer. Everyone is using it nowadays. So why don't you join em.
Now speaking of those who don't know how to implement this mechanism or system here is your boy for the rescue thinking of building a service which does all the heavy lifting for your app subscriptions, from Stripe to verification and device management, at a single place with proper SDKs.
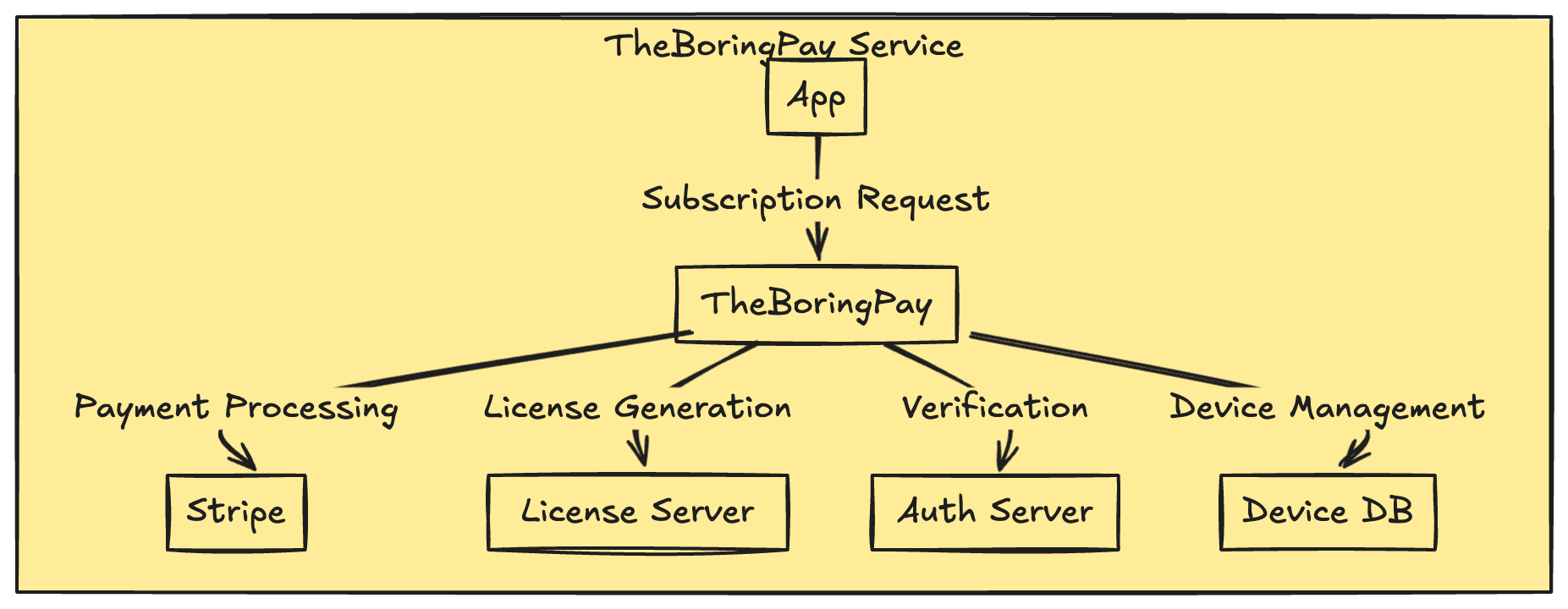
I'll try to keep it open source, but I do want to charge for those who want the cloud version of it. For the nerds, you can buy me a coffee and support my work. I promise I'll keep building awesome stuff for the community. Not a century ago, I started a project called "TheBoringNotch" - it's like an iPhone dynamic island but for macOS and that too open source for now. I'll catch you later, bye bye. I have a dinner date with my girl. The most beautiful girl in the world.
Wait, here's the coming soon landing page for "TheBoringPay".
https://payapp.theboring.name/
Subscribe to my newsletter
Read articles from Harsh Vardhan Goswami directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Harsh Vardhan Goswami
Harsh Vardhan Goswami
Full stack developer with a sense of humor, always striving to turn code into laughs. Building awesome and making people smile, one line at a time.