Building your VoIP system & Call Spoofing
 Sumir Broota
Sumir Broota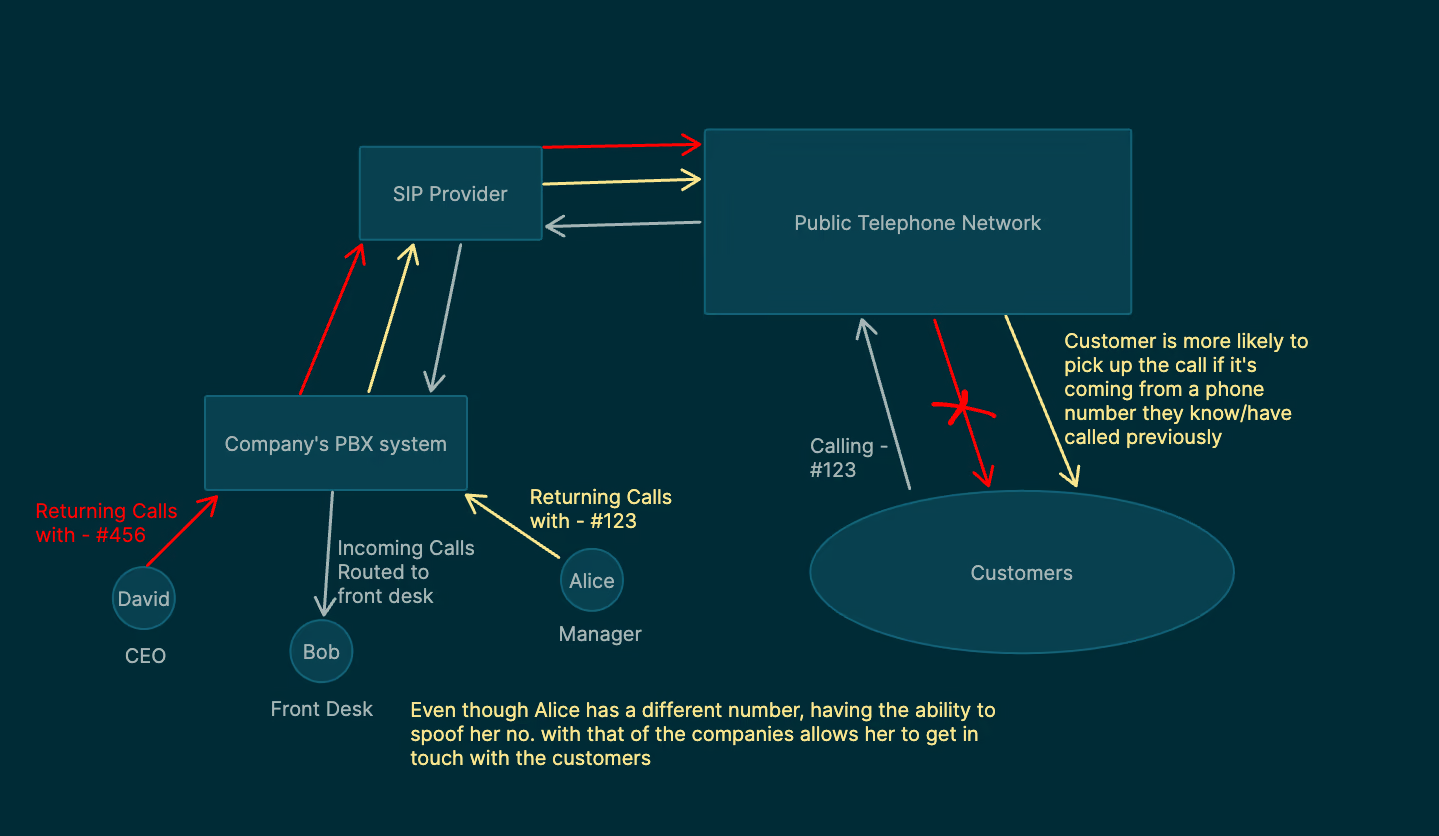
Links
All of the infomation showed here is for educational purposes & to raise awareness about our current systems. Please don’t use this information for anything malicious.
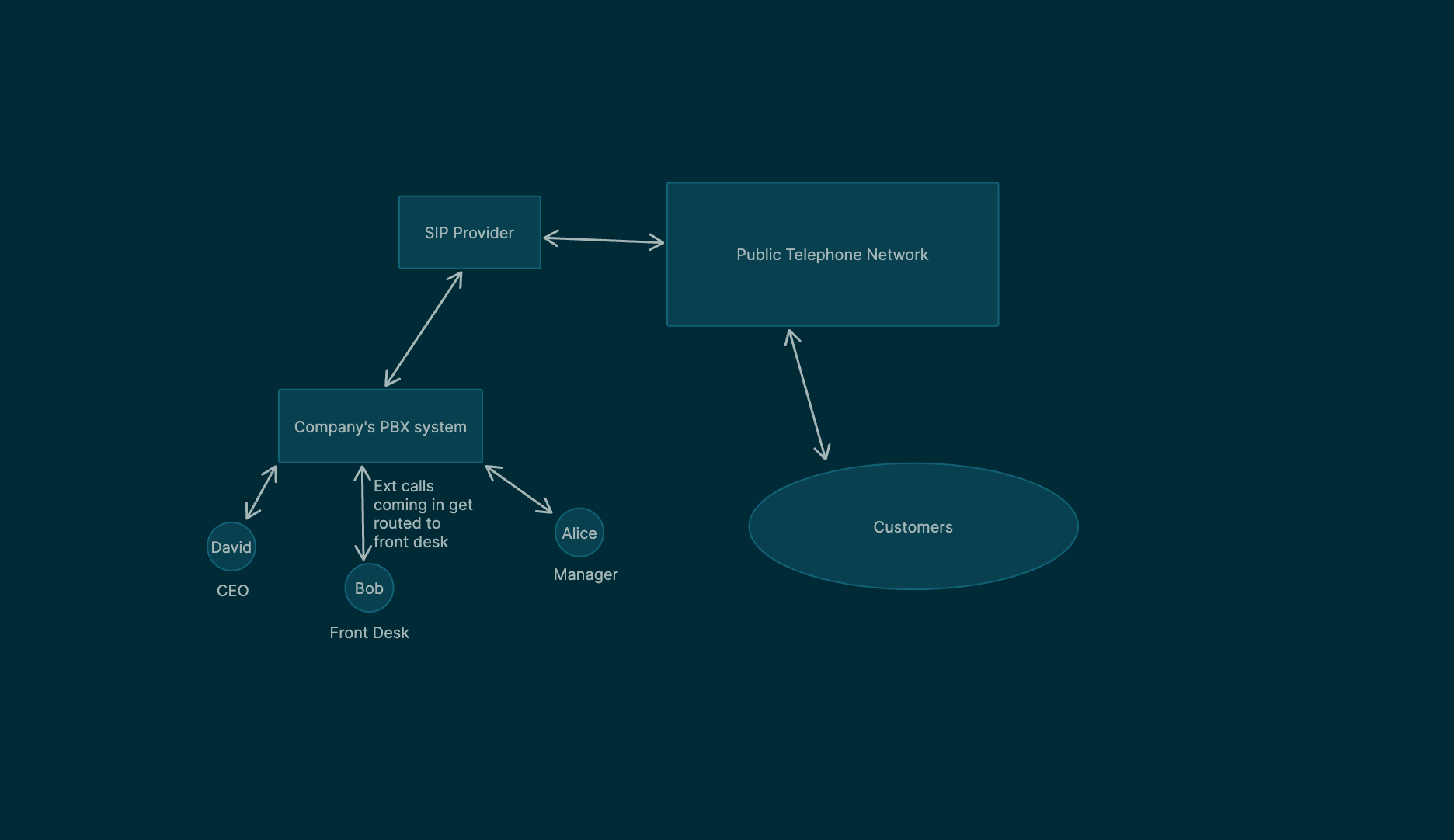
How Do Businesses Setup Their Own Phone System?
- This is where Private Branch Exchange (PBX) systems come in to place
- A PBX system is like a router creating a LAN for your legacy (or modern) internal phone systems
- You can connect your PBX system to the public network using SIP trunk providers (similar to ISP’s)
- Giving a single point of entry/exit to all your local phone systems.
Types of PBX
Analog/Legacy PBX
- traditional onsite hardware PBX working via wired PSTN
- business responsible for install/maintenance/monitoring
- limited features + expensive hardware
- obsolete
On-prem PBX
- hosted & managed on site by end user
- powered by VoIP using IP PBX
- requires purchase of own hardware & in house team to maintain hence still expensive
Hosted/Cloud/Virtual PBX
- VoIP based phone system maintained by 3rd party
- has better savings, mobility, scalability
- has advanced VoIP features
Hybrid PBX
- mix of virtual & hardware PBX
- uses SIP trunking
- end user still needs to maintain the on-prem phone system
Why Businesses need Call Spoofing
 Even though Alice has a different number, having the ability to spoof her no. with that of the companies allows her to get in touch with the customers
Even though Alice has a different number, having the ability to spoof her no. with that of the companies allows her to get in touch with the customers
Modern Phone System Protocols
SIP (Session Initiation Protocol)
- The de facto standard (text-based) for VoIP communication, used for initial authentication and negotiations when making connections.
- SIP is an application layer protocol that uses UDP or TCP for traffic. By default, SIP uses UDP/TCP port 5060.
RTP (Real-Time Transport Protocol)
- The actual voice or video traffic is transmitted via Real-Time Protocol (RTP or SRTP) after authentication and negotiations are done via SIP.
SDP (Session Description Protocol)
- SDP (Session Description Protocol) is a text-based format used to describe the characteristics of multimedia sessions, such as voice, video, or data conferencing, over IP networks.
- SDP does not handle the actual media transmission or session establishment but is used in conjunction with other signaling protocols, like SIP, to negotiate and exchange information about the media streams and their attributes.
SHAKEN/STIR
The current protection mechanism against call spoofing. This requires all SIP trunk providers to sign outgoing calls with their certificate, according to the legitimacy of the outbound caller id.
SHAKENstands forSignature-basedHandling ofAsserted Information using toKENs. It is a specification designed by the Alliance for Telecommunications Industry Solutions (ATIS) to fight caller ID spoofing.STIR (Secure Telephone Identity Revisited)is a protocol developed by the Internet Engineering Task Force (IETF) to enable end-to-end call authentication, but the protocol is very broad and doesn't ensure that different providers will be able to verify each others' calls.- The SIP provider certifies the classes of caller ID’s into the following:
- Class A - (most trusted). The number being dialed from has been authenticated by the service provider, and the caller has been authorized to use that number.
- Class B - The service provider has verified that the call has originated from the customer but not that they are authorized to use it.
- Class C - The service provider does not know the caller’s identity and the source of the call cannot be identified (maybe coming from an international gateway/outside their network).
How STIR/SHAKEN Identity headers are received by end users
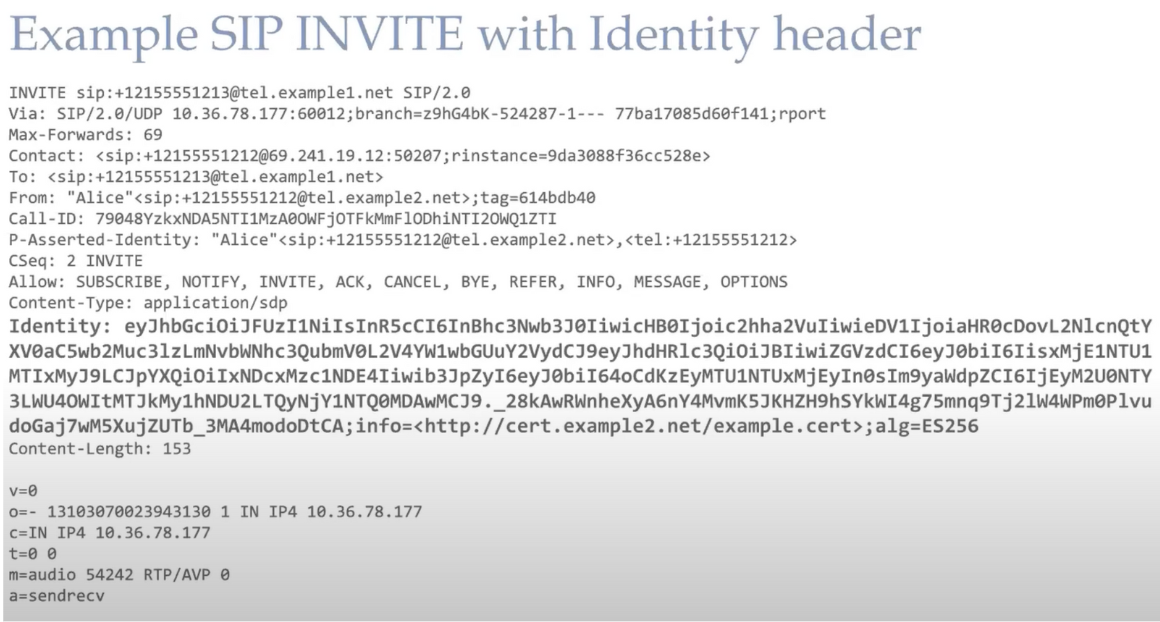
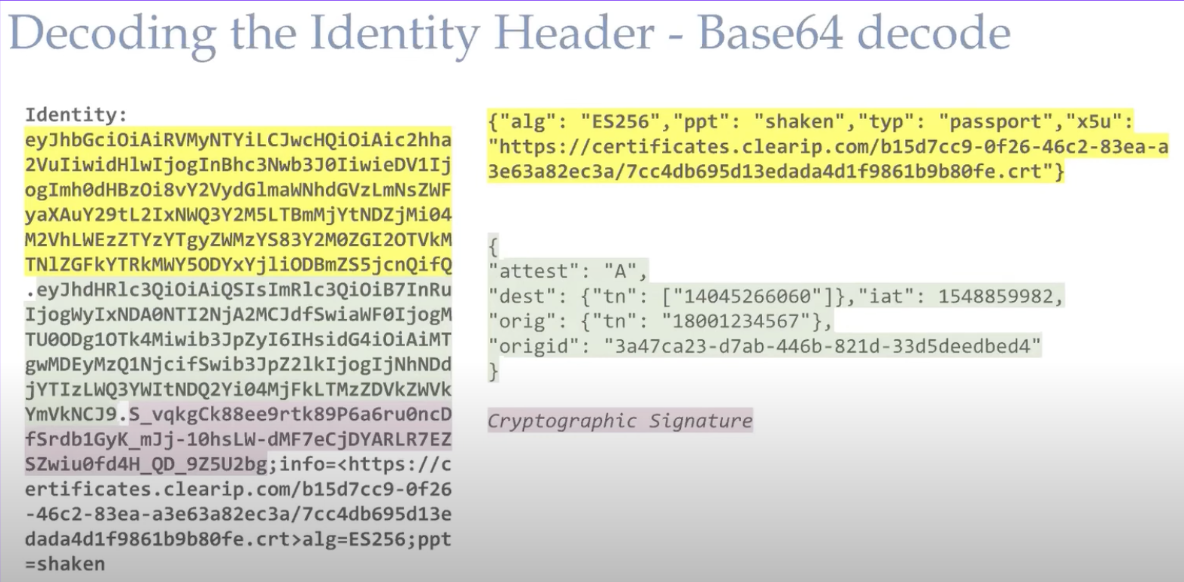
Issues with our current system
- Most providers transmit data over clear text
- Despite the avaliability of TLS encryption with SRTP & SIP-TLS, the lack of industry wide adoption poses a challenge. Anyone with knowledge of the system can capture the data
- Trust on User Defined Outbound Caller ID
- Though most SIP trunking providers have added protections in place, there are plenty of providers willing to skirt the regulation.
- Protection Mechanism in place doesn’t account for legacy systems in the route
- In case the call gets routed/forwarded through a legacy system, the data signed by the SIP trunk gets dropped
- SHAKEN/STIR is expensive to maintain
- SHAKEN/STIR is difficult to maintain, leaving power in the hands of major providers. Also 3rd party SIP trunk resellers can be held liable as service providers despite being dependent on larger providers for their signing method
- Doesn’t factor into the Global context well
- SHAKEN/STIR was originally made for US/Canada to be deployed in their own countries and was later modified to be more global. Due to political relations between nations & lack of accountability in enforcing these protections across countries it can be difficult to ratify as a standard
Ways To Protect Yourself
Report fraudulent calls
For Indian Citizens:
https://sancharsaathi.gov.in/sfc/
Report Incoming International Call With Indian Number (RICWIN)
- https://sancharsaathi.gov.in/InternationalCall/ReportIntCall.jsp
- Alternatively you can report on 1963/1800110420
Scammers often try to rush your decision making
- Before making any major decision based on a possibly fraudulent Call/SMS do the following:
- Take a deep breath and don't rush yourself
- Ask probing questions that only the person you're connecting with would know
- Connect/Communicate with your contact over another medium (email/physically meet)
- Before making any major decision based on a possibly fraudulent Call/SMS do the following:
Know that the Indian Government is taking steps to reduce these threats
- Quickest, simplest way TRAI & telco's have stopped spoofed calls from overseas is to look at the phone numbers for each inbound call and to block them if they pretend to have a domestic origin.
- Note during my testing - it sometimes let the call through but set the caller id as a random number. This behaviour may vary from provider to provider
- Telecom Regulatory Authority of India (TRAI) issued recommendations on leveraging AI-based fraud detection systems to identify and prevent fraudulent activities, such as unauthorized usage of SIM cards, subscription fraud, and billing fraud.
- Quickest, simplest way TRAI & telco's have stopped spoofed calls from overseas is to look at the phone numbers for each inbound call and to block them if they pretend to have a domestic origin.
Raise Awareness of such issues amongst family & friends
- The more people are aware, the less likely they are to fall for such scams
Glossary
VoIP
- is an acronym for Voice Over Internet Protocol, or in more common terms phone service over the Internet.
Private Branch Exchange (PBX)
- It is a private telephone network that is used by an organisation to communicate internally and externally. PBX systems are used to route calls between internal extensions and the public telephone network.
Session Initiation Protocol (SIP)
- The de facto standard for VoIP communication, used for initial authentication and negotiations(terminate, or modify) when making connections. (like metadata for comms).
- SIP is an application layer protocol that uses UDP or TCP for traffic. By default, SIP uses UDP/TCP port 5060.
SIP Trunk
- In order for people to make calls to your internal PBX network (and vice verse)- your network must have an actual exposed number - that is the job of SIP Trunk It connects your PBX network to the Public Switched Telephone Network AKA PSTN
STIR/SHAKEN
- Caller ID authentication confirms the accuracy of the information. It is more difficult for attackers to spoof numbers with this additional degree of security.
References:
- Setup basics playlist
- Rapid 7 Blog on Build your own Caller ID Spoofer Part 1
- Rapid 7 Blog on Build your own Caller ID Spoofer Part 2
- Spoof caller id on the fly from any phone for legal & legitimate puposes
- warvox manual
- Caller ID spoofing
- VoIP Info
- Wardialing Finnish Phones
- Warvox
- PSTN - Public Switched Telephone Network by Sunny Classroom
- Everything SIP - Session Initiation Protocol by Get VoIP
- SIP INDEPTH by VoIP Info
- SCTP - Stream Control Transmission Protocol
- SS7 - Signalling System No.7
- Interesting history of Signaling System
- STIR/SHAKEN and the Death of the Small VoIP Carrier
- Combating Spoofed Robocalls with Caller ID Authentication by US FCC
- SHAKEN/STIR 2/3: SIP Headers, Identity PASSporT, and Call flow through carrier network
- SIP Pentesting - Hacktricks
- Basic VoIP Protocols - Hacktricks
- Global STIR/SHAKEN Is Dead; What Comes Next?
- TRAI Consulation Paper on Leveraging AI for anomaly detection in telecom sector
Subscribe to my newsletter
Read articles from Sumir Broota directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
