Understanding the Basics of ELF Files on Linux
 Sandipan Roy
Sandipan Roy
The Executable and Linkable Format (ELF) is the standard file format for executables, object code, shared libraries, and core dumps on Linux and Unix-like systems. Understanding ELF files is essential for anyone involved in software development, reverse engineering, or security analysis on Linux systems. This blog will walk you through the basics of ELF files, their structure, and how to analyze them.
Introduction to ELF Files
ELF files are central to the functioning of Linux systems. They are used to define how the operating system loads and runs programs, including how they link to shared libraries. The ELF format is flexible, allowing it to be used for different kinds of files, such as executables, object files, and shared libraries.
Key Characteristics of ELF Files:
Portability: ELF is used across various Unix-like systems.
Extensibility: Supports dynamic linking, allowing code to be shared between programs.
Efficiency: Designed to be loaded and executed quickly by the operating system.
Structure of an ELF File
An ELF file is composed of several sections and segments that define the executable's code, data, and other resources. The main components of an ELF file are:
ELF Header: Contains metadata about the file, such as its type, architecture, and entry point.
Program Header Table: Describes segments used at runtime (like code and data).
Section Header Table: Describes sections used for linking and debugging (like symbol tables and relocation information).
Sections and Segments: Contain the actual data, such as code, data, symbols, and debug information.
Here’s a simplified view of an ELF file structure:
+-----------------+
| ELF Header |
+-----------------+
| Program Headers |
+-----------------+
| Sections |
+-----------------+
| Segment Data |
+-----------------+
| Section Headers |
+-----------------+
ELF Header: The File's Metadata
The ELF header is the first part of the ELF file and provides the essential metadata for the operating system to understand how to process the file.
Key fields in the ELF Header:
e_ident: A magic number identifying the file as an ELF file.
e_type: Identifies the file type (e.g., executable, shared object, or relocatable).
e_machine: Specifies the target architecture (e.g., x86_64, ARM).
e_version: The version of the ELF format.
e_entry: The memory address of the entry point, where the process starts executing.
e_phoff: Offset to the program header table.
e_shoff: Offset to the section header table.
Program Header Table: Runtime Segments
The program header table is crucial during the execution of the program. It tells the loader which parts of the file should be loaded into memory and how.
Key fields in a Program Header:
p_type: The type of segment (e.g., LOAD, DYNAMIC).
p_offset: The offset of the segment in the file.
p_vaddr: The virtual address where the segment should be loaded.
p_paddr: The physical address (not always used).
p_filesz: The size of the segment in the file.
p_memsz: The size of the segment in memory.
Common segment types include:
LOAD: Contains code or data that should be loaded into memory.
DYNAMIC: Holds dynamic linking information.
INTERP: Contains the name of the dynamic linker.
Section Header Table: Linking and Debugging Information
The section header table is used primarily for linking and debugging. It contains entries that describe sections of the file, such as the .text section (executable code) or the .data section (initialized data).
Key fields in a Section Header:
sh_name: The name of the section.
sh_type: The type of section (e.g., SHT_PROGBITS for code/data).
sh_flags: Flags indicating the section's attributes (e.g., SHF_EXECINSTR for executable code).
sh_addr: The virtual address where the section should be loaded.
sh_offset: Offset of the section in the file.
sh_size: Size of the section.
Common sections include:
.text: Contains the executable code.
.data: Contains initialized data.
.bss: Contains uninitialized data.
.symtab: Symbol table used by the linker.
.strtab: String table used by the symbol table.
.rel.text: Relocation information for the
.textsection.
Analyzing ELF Files
There are various tools available to analyze ELF files. Here are a few commonly used ones:
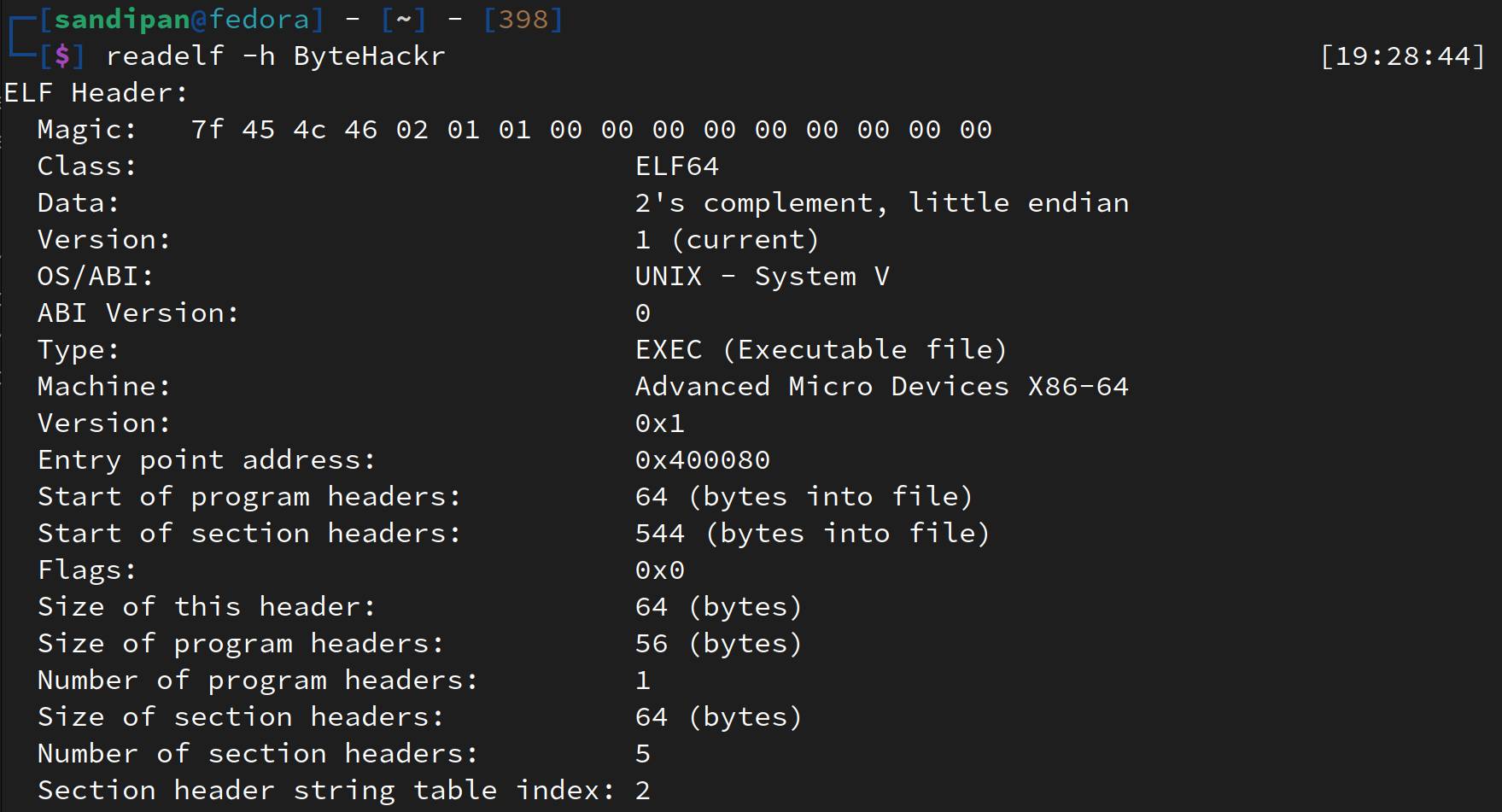
readelf
readelf is a command-line utility that displays information about ELF files. It can show headers, sections, segments, symbols, and more.
Example usage:
readelf -h <file> # Display the ELF header
readelf -l <file> # Display the program header
readelf -S <file> # Display the section header table
Example of a ELF Header:
objdump
objdump is another powerful tool for examining the contents of object files, including ELF files. It can disassemble executables, display symbol tables, and more.
Example usage:
objdump -d <file> # Disassemble the executable code
objdump -t <file> # Display the symbol table
nm
nm is used to list symbols from object files. It’s useful for developers to understand the functions and variables in an ELF file.
Example usage:
nm <file> # List symbols
strace
strace traces system calls and signals, which can be helpful in understanding the runtime behavior of an ELF executable.
Example usage:
strace ./<executable> # Trace the system calls made by the executable
Common ELF File Issues & Malwares
While working with ELF files, you may encounter various issues, such as:
Broken dependencies: Missing shared libraries can cause an executable to fail.
Relocation errors: Errors in the relocation process during dynamic linking.
Corrupted ELF files: Corruption in the ELF file structure can cause the loader to fail.
Sometime malware authors often use file packing techniques to evade detection. Packing involves compressing or encrypting an ELF file, obscuring its contents from traditional inspection methods.
How File Packing Works
File packing compresses or encrypts the ELF file, making it difficult to analyze. When executed, the malware decompresses itself in memory, revealing its true nature. This dynamic unpacking complicates static analysis and requires sophisticated tools and techniques to fully understand the malware's behavior.
The Role of UPX
One popular packing tool is the Ultimate Packer for eXecutables (UPX). UPX is widely used by malware authors to compress ELF files, reducing their size and altering their structure to thwart reverse engineering.
Recognizing and Unpacking Packed ELF Files
To detect packed ELF files, investigators look for anomalies such as irregular section sizes or high entropy levels. Unpacking typically involves dynamic analysis, where the malware is executed in a controlled environment to capture the unpacked code in memory.
Understanding and unpacking these techniques is essential for incident responders to analyze the malware effectively and develop appropriate countermeasures.
Windows vs. Linux: PE vs. ELF
While both Windows and Linux use different executable formats, there are notable differences between the PE (Portable Executable) file format used by Windows and the ELF format used by Linux.
Key Differences:
PE Header: Includes DOS headers, PE signatures, and COFF headers, which are specific to Windows executables.
ELF Header: Contains identification information, file type, and architecture, leading to program and section header tables that facilitate dynamic linking and execution on Unix-like systems.
Understanding these differences is crucial for cross-platform malware analysis and digital investigations.
Conclusion
Understanding ELF files is crucial for anyone working closely with Linux systems. The ELF format’s flexibility and extensibility make it a robust choice for Unix-like systems. Whether you're developing software, performing security analysis, or debugging applications, a solid grasp of ELF files will help you navigate and resolve issues more effectively.
By using tools like readelf, objdump, nm, and strace, you can gain valuable insights into the structure and behavior of ELF files, making you a more effective Linux user and developer.
Subscribe to my newsletter
Read articles from Sandipan Roy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sandipan Roy
Sandipan Roy
Sandipan Roy is a Product Security Engineer working for the Red Hat Product Security Team with a demonstrated history of working in Incident Response, Code Review, and Vulnerability Analysis. Also, he has contributed to many Open Source Projects and also actively maintains a few packages for the Fedora Project. As a Red Hatter applying his technical experience, he guides customers in adopting the best security practices & technologies and helps to raise global awareness about Red Hat Product Security.