Day 1: Mastering Azure Identity Management
 Anurag Raj
Anurag RajTable of contents
- Day 1: Unpacking Azure Identity with Microsoft Entra ID
- What is Administer Identity?
- Objective 1: Configure Microsoft Entra ID
- Introduction to Microsoft Entra ID: The Digital Gatekeeper
- Real-Life Example: Office Building Security
- Deep Dive: Microsoft Entra ID Services in Action
- Delving Deeper: Microsoft Entra ID Concepts
- Tenants and Directories: Your Azure Office Space
- Microsoft Entra ID vs Active Directory: Whats New Here
- Microsoft Entra ID Editions: Tailored Access Levels
- Wrap-Up: Laying the Foundation of Azure Identity Management
Day 1: Unpacking Azure Identity with Microsoft Entra ID
Welcome to Day 1 of our deep dive into Azure's security ecosystem! We’re kicking things off with Managed Identities and Governance, focusing on the building blocks that ensure your Azure environment is as secure as a vault.
In this module, we’ll explore three key sub-topics:
Administer Identity
Administer Governance and Compliance
Administer Azure Resources
But first, a quick heads-up—Microsoft has rebranded Azure Active Directory (AAD) to Microsoft Entra ID. Nothing else has changed, just the name. All services previously under Azure AD are now labeled as Microsoft Entra ID. So, let’s get started!
What is Administer Identity?
Administer Identity is all about managing who has access to what in your Azure environment. Think of it as managing a secure facility—you need to ensure that only the right people can enter and only with the necessary permissions.
Within Microsoft Entra ID, users and groups are the primary entities that represent your organization's identity. Users are individual accounts, each with specific roles, permissions, and profile information. Groups allow you to manage permissions collectively, streamlining access management.
Objective 1: Configure Microsoft Entra ID
Our first objective is to Configure Microsoft Entra ID in which we are going to get an introduction of Microsoft Entra ID and its role in Azure identity services. We’ll cover key concepts such as identity types, authentication methods, and access management. After that, we will be looking at the Microsoft Entra ID Concept followed by its Editions. So, let's get started.
Introduction to Microsoft Entra ID: The Digital Gatekeeper
Formerly known as Azure Active Directory, Microsoft Entra ID is the backbone of identity management in the Azure cloud. It’s like the gatekeeper at the entrance of a high-security facility, ensuring only those with the right credentials get in.
Microsoft Entra ID is a cloud-based identity and directory management service that enables access to Azure services and other SaaS solutions like Microsoft 365, DropBox, Concur, Salesforce, etc.
It offers self-service options including password reset, authentication, device management, hybrid identities, and single sign-on.
In the below picture, as you can see the Microsoft Enter ID is placed at the center of Connections.
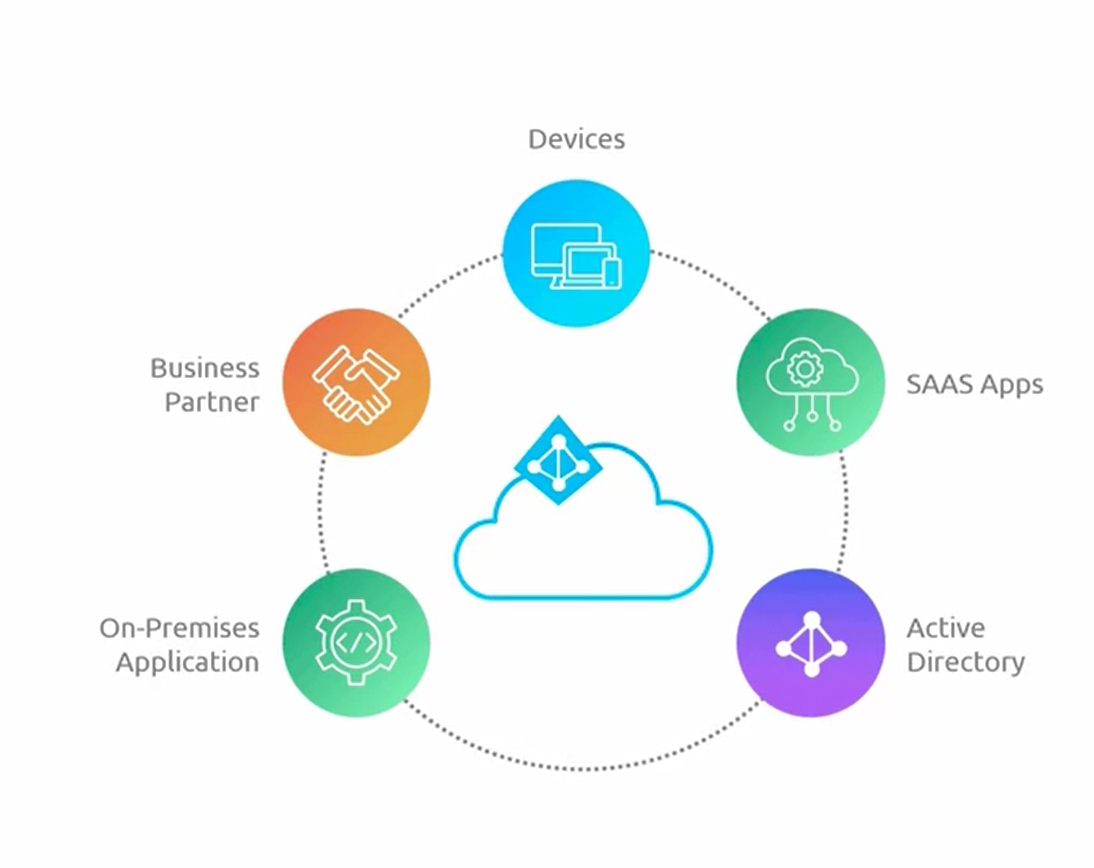
It integrates with our on-premise applications, ensuring that even legacy systems can be part of this secure modern identity framework.
It reaches out to business partners enabling secure collaboration across company boundaries.
It ties into devices highlighting the service's ability to manage and authenticate access regardless of where you are or what device you're using.
It connects to multiple SaaS applications representing its capability to provide unified Access and Security policies across a range of third-party applications.
It integrates with active directory synchronizing with existing on-premise directories for a consistent identity across both local and cloud environments.
Key Concepts:
Identity Types: In Microsoft Entra ID, an identity can be a user, a managed identity for a service, or a service principal. It’s like different types of ID cards—each serving a specific purpose.
Authentication Methods: These are the ways users prove their identity, such as passwords or multi-factor authentication (MFA). Think of this as showing your ID and an additional passcode to get through a checkpoint.
Access Management: Once authenticated, access management determines what resources a user or service can interact with—like granting access to certain floors in a building while restricting others.
Real-Life Example: Office Building Security
Imagine your company’s office building. Each employee has a key card that lets them access only the floors and rooms relevant to their role. The finance team doesn’t need access to the server room, just like the IT team doesn’t need access to the HR files. Administer Identity in Microsoft Entra ID works the same way—it ensures that each user and service only has access to the resources they need.
Deep Dive: Microsoft Entra ID Services in Action
Let’s consider a scenario: You’re the IT admin at a growing startup. With a mix of remote and in-office employees, you need to ensure that everyone can access the tools they need without compromising security.
Microsoft Entra ID steps in as your digital bouncer. It checks IDs (authenticates users), ensures people only enter the rooms (services) they’re supposed to and keeps a log of who went where (audit logs). This way, even if someone’s credentials are compromised, the damage is contained.
Hybrid Identity: A unique feature of Entra ID is its ability to support hybrid identities. Imagine half your employees work from home, and the other half are in the office. Hybrid identity ensures that both groups can securely access the same resources, regardless of where they are.
Self-Service Password Reset: Ever had to wait for IT to reset your password? With Entra ID, users can reset their passwords themselves, saving time and reducing the IT team's workload.
Conditional Access: Security isn’t one-size-fits-all. Conditional access lets you set policies based on risk levels. For example, you might require MFA if someone tries to log in from a new device or location. It’s like having different security levels depending on how risky the situation is.
Delving Deeper: Microsoft Entra ID Concepts
Managed Identity:
This is an identity created for a service, such as a virtual machine or app, allowing it to authenticate and access resources securely. It’s like giving a company car a dedicated parking pass—only it can park in the reserved spot.
In a real-world scenario, imagine you have a virtual machine that needs to access a database. Instead of creating a user account and managing credentials manually, you create a managed identity. This identity is automatically managed by Azure, ensuring secure and seamless access without the headache of managing passwords.
Service Principal:
A Service Principal is an identity created for running automated tasks on behalf of a user. Imagine it as a trusted assistant with the keys to certain parts of the office, allowed to perform specific tasks without needing your direct involvement.
For instance, if you’re automating the deployment of an application, a service principal can be used to give the deployment script the necessary permissions to interact with Azure resources—without needing a human to log in every time.
Account vs. Identity:
An identity becomes an account when specific attributes, like department or location, are attached. It’s similar to adding job-specific information to an employee’s profile, making it clear what resources they should access.
Imagine an identity as a blank ID card. Once you add a name, job title, and access permissions, it becomes an account that can be used within your organization.
Tenants and Directories: Your Azure Office Space
A Tenant or Directory in Microsoft Entra ID is like your organization’s dedicated instance in the cloud. When you sign up for an Azure account, a tenant is created, and all your subscriptions are linked to it. Think of it as leasing office space—everything you do is within your floor of the building.
In practical terms, when your company signs up for Microsoft 365 or Azure, a tenant is created. This tenant acts as a container for all the identities, resources, and subscriptions associated with your organization. It’s like a digital headquarters where all your cloud operations are managed.
Microsoft Entra ID vs Active Directory: Whats New Here
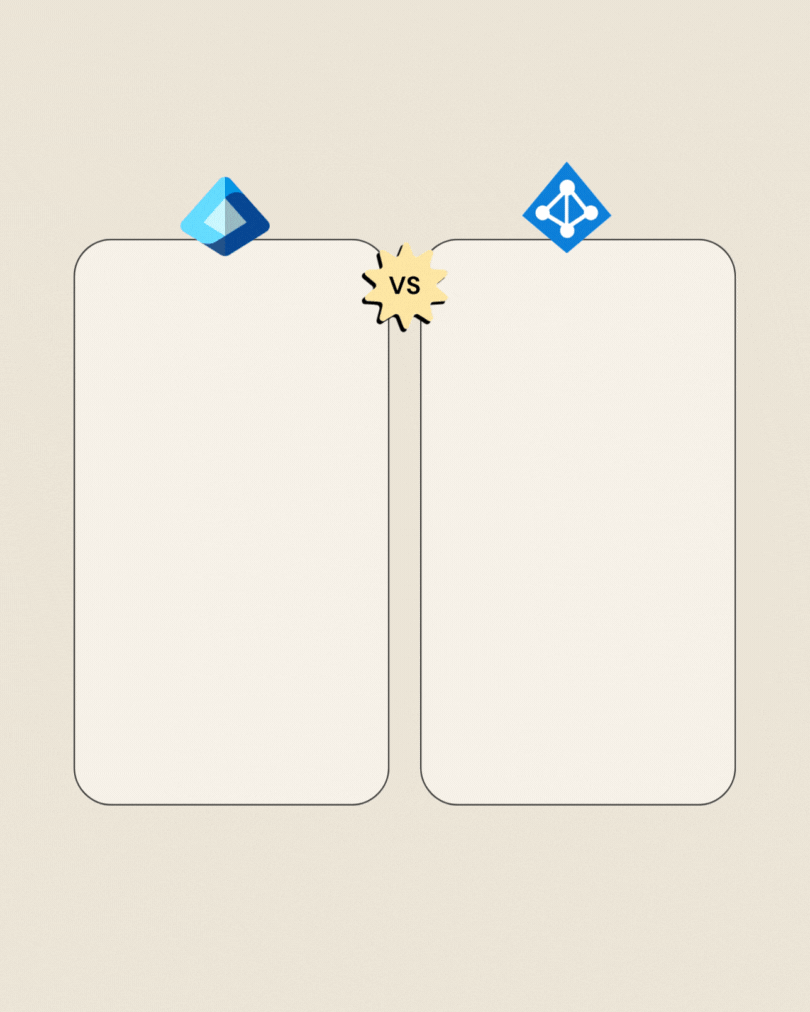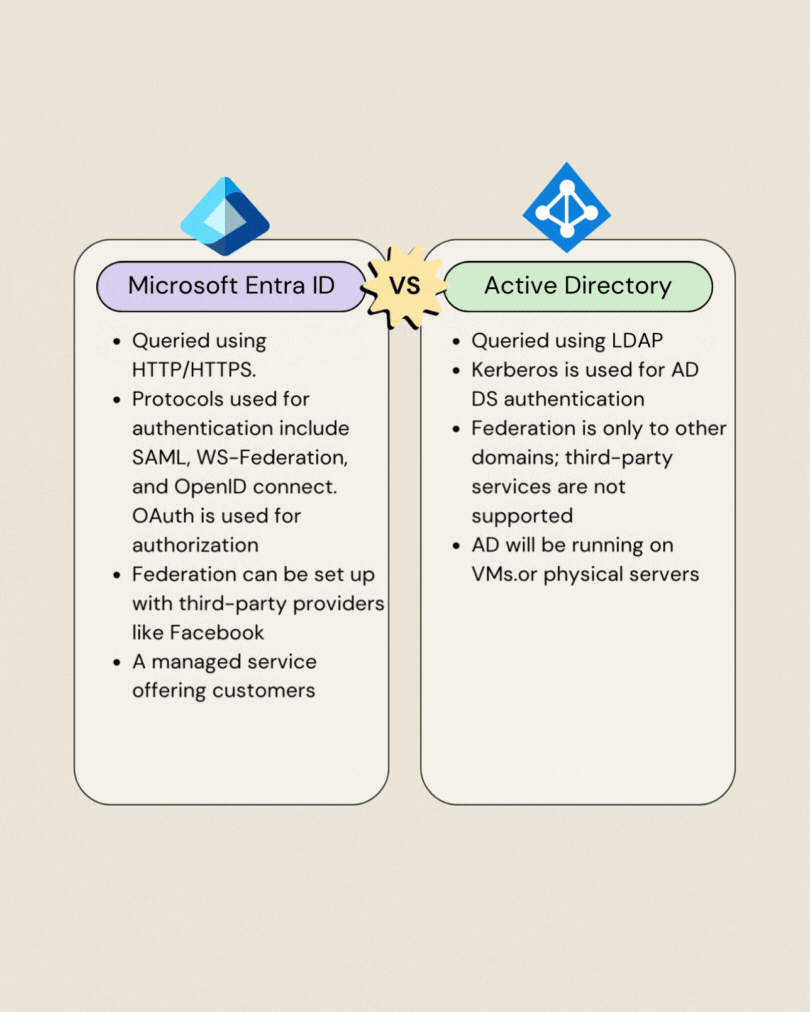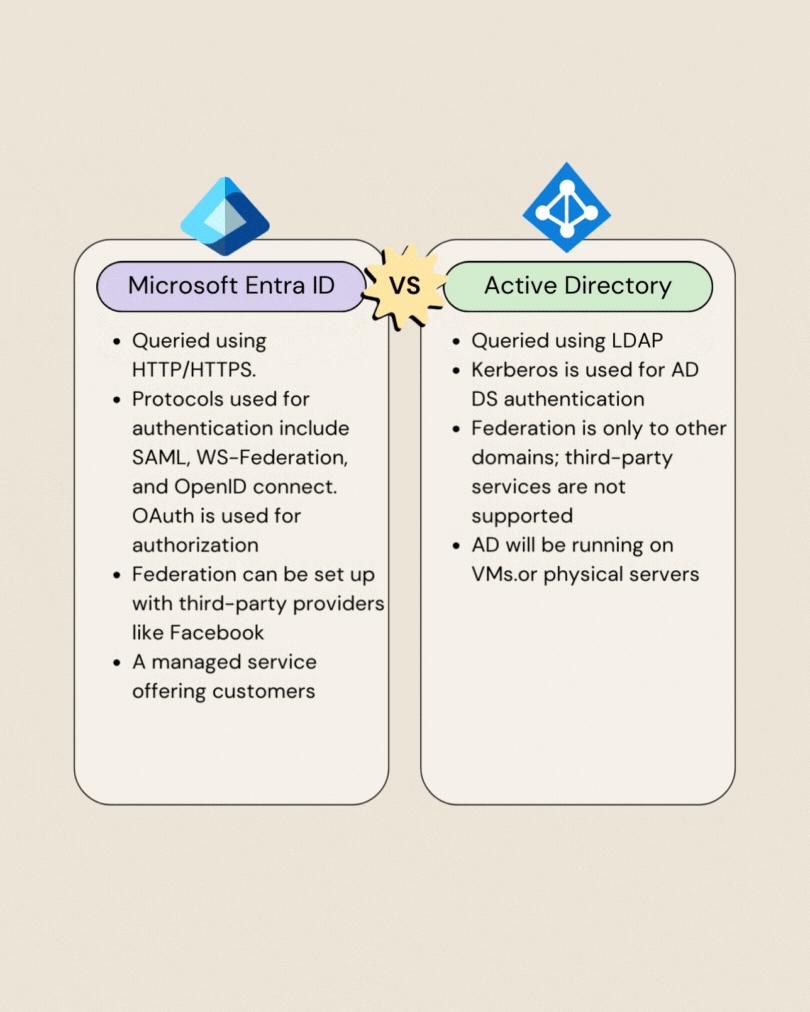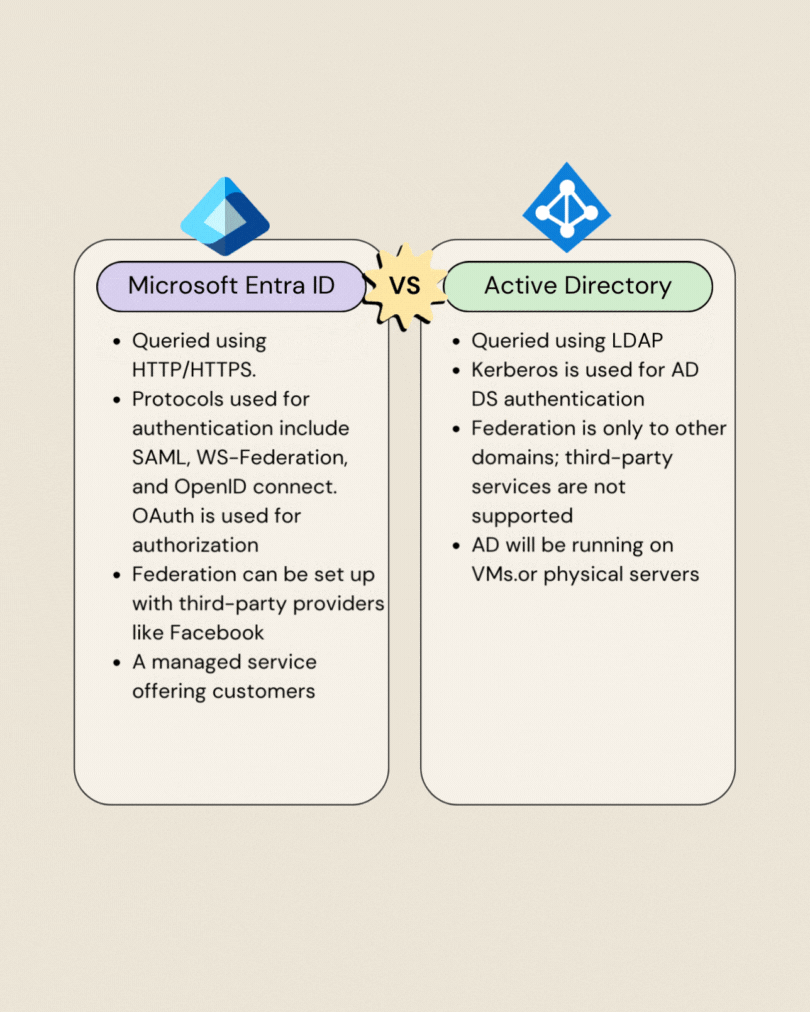
Microsoft Entra ID Editions: Tailored Access Levels
Microsoft Entra ID comes in four editions, each offering different levels of identity management and security features:
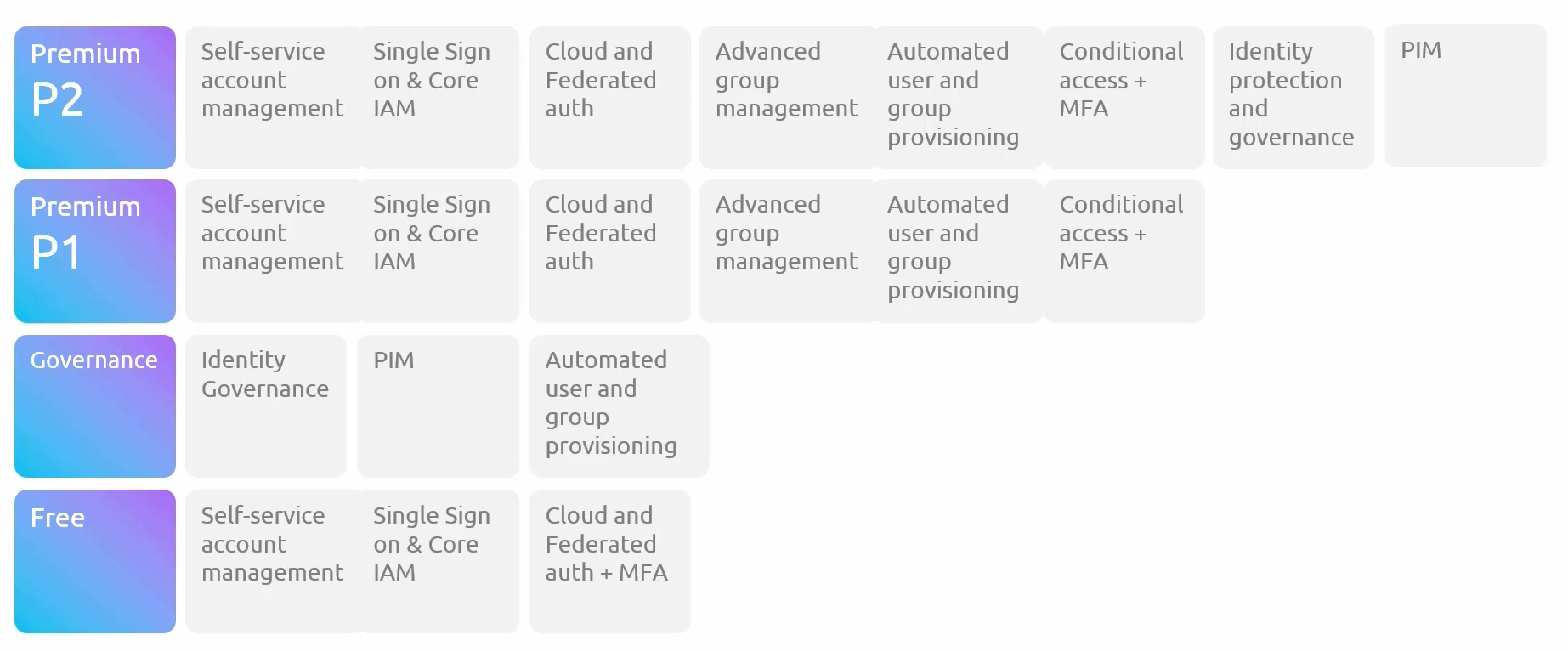
Premium P2: The full package, offering advanced identity protection and governance. It’s like having top-tier security with 24/7 monitoring, identity protection, and compliance checks.
Example: If you’re managing a large enterprise with strict compliance requirements, Premium P2 ensures that your environment is protected against sophisticated threats. It offers tools like identity protection and access reviews, which help you stay compliant and secure.
Premium P1: Provides robust identity management with advanced features like conditional access and MFA. Think of it as a high-security office with access controls that adjust based on threat levels.
Example: A mid-sized company might opt for Premium P1 to secure their environment without the full range of governance tools. Conditional access policies ensure that only trusted users and devices can access critical resources.
Governance: This new edition focuses on identity lifecycle management and governance. It’s like having an office manager who ensures everyone has the right keys and reviews access regularly.
Example: If your organization frequently onboards and offboards employees, the Governance edition streamlines this process, ensuring that access rights are granted according to policies and regularly reviewed. This helps prevent security gaps when roles change.
Free: Offers essential features like self-service account management and basic SSO. This is the entry-level package—enough to get started but with limited perks.
Example: A small business might start with the Free
Wrap-Up: Laying the Foundation of Azure Identity Management
And that's a wrap for Day 1: Administer Identity! Today, we explored the core concepts of Microsoft Entra ID (formerly Azure Active Directory), delving into how it functions as the gatekeeper for Azure identity management. From identity types to authentication methods and access management, we laid the groundwork for understanding how users, services, and devices securely interact within your Azure environment.
Tomorrow, in Day 2, we’ll dive deeper into identity management with Objective 2, where we will cover:
User Accounts: Different types of accounts like Cloud, Guest, and Directory-Synchronized Users.
Bulk Operations: Learn how to manage users at scale using CSV templates for creating, inviting, or deleting users.
Group Accounts: Explore the types of groups—Security and Microsoft 365 groups—and their assignment methods.
Self-Service Password Reset (SSPR): A detailed look at how users can manage their password security on their own.
Keep the momentum going! You're well on your way to mastering Azure identity management. Let’s continue building a secure, scalable, and efficient Azure environment.
Stay tuned for Day 2! 👊
Hey there! I’m Anurag Raj – your go-to DevOps wizard with a knack for transforming complex operations into seamless, magical CI/CD experiences.
With 3 years of hands-on expertise in optimizing workflows and boosting productivity, I’m all about turning the ordinary into the extraordinary. Whether it’s crafting innovative solutions or streamlining processes, I bring a touch of magic to everything I do.
Curious about how we can make DevOps even more awesome together? Click the link and drop me a “Hello Anurag”! Let’s connect and explore the endless possibilities in the world of DevOps.
Excited to chat with you soon!!
Subscribe to my newsletter
Read articles from Anurag Raj directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Anurag Raj
Anurag Raj
As a dedicated and results-driven DevOps Engineer with 3 years of hands-on experience, I am committed to optimizing software development pipelines and infrastructure to accelerate project delivery and enhance overall operational efficiency. My journey in the world of DevOps has equipped me with a diverse skill set that spans across automation, continuous integration, continuous deployment, and cloud technologies. I take pride in my ability to bridge the gap between development and operations teams, fostering collaboration and ensuring seamless workflows. I am eager to leverage my skills and experience to contribute to a dynamic organization, driving innovation and excellence in DevOps practices.