Achieving GDPR and CCPA Compliance with Automation and Encryption: Insights from Real Breach Cases
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
In today’s digital landscape, data breaches like the ones involving Facebook and Marriott have shown us the immense consequences of mishandling sensitive data. The General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) have established clear privacy standards, and non-compliance can result in massive fines and reputational damage. For companies managing sensitive personal data, integrating privacy by design into their DevSecOps pipelines is essential to ensure compliance.
In this article we'll explore:
Automating compliance audits with Open Policy Agent (OPA)
Integrating data encryption into your development and deployment processes using HashiCorp Vault
Implementing privacy risk assessments and continuous monitoring
Lessons from Real-World Data Breaches
Before diving into implementation, let’s reflect on what we can learn from real-world examples:
Facebook-Cambridge Analytica Scandal: Facebook faced a massive backlash after it was revealed that the personal data of millions of users was harvested without consent. It underscored the need for robust consent management, which is central to GDPR.
Marriott Data Breach (2018): One of the largest hotel chains experienced a breach that exposed the personal data of 500 million guests. Marriott’s failure to secure sensitive data resulted in regulatory penalties, proving the need for strong encryption and access controls.
These examples underline the importance of adhering to privacy laws like GDPR and CCPA, which mandate that personal data must be encrypted, users’ consent must be respected, and compliance must be continuously monitored.
GDPR and CCPA in DevSecOps: Key Areas to Focus On
Automating Compliance Audits - Use policy-as-code to automatically check for compliance during the CI/CD process.
Data Encryption - Secure sensitive data both at rest and in transit using encryption mechanisms.
Privacy Risk Assessment - Continuously evaluate risks related to sensitive data using threat modeling and risk assessment tools.
Real-World Problem: The GDPR/CCPA Compliance Gap
Imagine a large-scale organization that manages sensitive customer data in multiple regions. The challenge is ensuring data encryption, consent collection, and continuous monitoring in an agile DevSecOps environment. A slight misstep, like failing to encrypt a user’s data or improperly capturing consent, could lead to significant GDPR fines or a loss of consumer trust.
This architecture will guide you through the solution, where we automate privacy compliance checks, integrate encryption into our development process, and ensure continuous monitoring for risk mitigation.
Step-by-Step Guide to Implementing GDPR and CCPA Compliance in DevSecOps
Here’s a detailed technical guide to implementing the architecture using tools like Open Policy Agent (OPA), HashiCorp Vault, Prometheus, and more.
Step 1: Automating Compliance Audits with Open Policy Agent (OPA)
The first step is to automate compliance checks for policies such as data encryption and access control during the build process.
1.1 Install OPA
Start by installing OPA on your local machine or CI/CD server (e.g., Jenkins).
curl -L -o opa https://openpolicyagent.org/downloads/v0.45.0/opa_linux_amd64
chmod +x opa
1.2 Write Compliance Policies
Define a policy to enforce encryption in a policy.rego file.
package compliance
allow {
input.request.operation == "CREATE"
input.request.resource.encrypted == true
}
deny["Data is not encrypted"] {
input.request.operation == "CREATE"
input.request.resource.encrypted == false
}
1.3 Integrate OPA into CI/CD (Jenkins Example)
Create a Jenkins pipeline file (Jenkinsfile) that invokes OPA to evaluate policies.
pipeline {
agent any
stages {
stage('Checkout') {
steps {
git 'https://github.com/my-org/my-repo'
}
}
stage('Policy Check') {
steps {
sh '''
opa eval -i input.json -d policy.rego "data.compliance.allow"
'''
}
}
stage('Build') {
steps {
sh './build.sh'
}
}
}
}
1.4 Create Input JSON for Compliance Check
The input JSON represents the resource being created, such as an API or a database field.
{
"request": {
"operation": "CREATE",
"resource": {
"encrypted": false
}
}
}
Step 2: Data Encryption with HashiCorp Vault
Next, integrate HashiCorp Vault to encrypt sensitive data both at rest and in transit.
2.1 Install Vault
curl -O https://releases.hashicorp.com/vault/1.9.0/vault_1.9.0_linux_amd64.zip
unzip vault_1.9.0_linux_amd64.zip
2.2 Start Vault Server
vault server -dev
2.3 Enable Encryption as a Service
Configure Vault’s Transit Secrets Engine for encryption.
vault secrets enable transit
vault write -f transit/keys/my-key
2.4 Encrypt Data in Your Application
Encrypt sensitive fields before storing them in the database.
import requests
def encrypt_value(value):
url = "http://127.0.0.1:8200/v1/transit/encrypt/my-key"
headers = {"X-Vault-Token": "root"}
data = {"plaintext": value.encode('base64')}
response = requests.post(url, json=data, headers=headers)
return response.json()['data']['ciphertext']
sensitive_data = "secret_password"
encrypted_data = encrypt_value(sensitive_data)
print("Encrypted:", encrypted_data)
Step 3: Implementing Privacy Risk Assessment
To continuously evaluate privacy risks, you can use OWASP Threat Dragon.
3.1 Install OWASP Threat Dragon
Clone the repository and start the application:
git clone https://github.com/OWASP/threat-dragon.git
cd threat-dragon
npm install
npm start
3.2 Create a Data Flow Diagram (DFD)
Using Threat Dragon, create a diagram to visualize sensitive data flow and identify potential vulnerabilities.
3.3 Automate Privacy Risk Assessment in CI/CD
Integrate threat models into your CI/CD pipeline:
pipeline {
agent any
stages {
stage('Threat Modeling') {
steps {
sh 'threat-dragon-cli check --input threat-model.json --rules rules.json'
}
}
}
}
Step 4: End-to-End Testing for GDPR/CCPA Compliance
Conduct end-to-end testing to ensure encryption and consent mechanisms work as expected.
4.1 Write End-to-End Test Scripts
Verify data encryption using Postman:
{
"request": {
"operation": "CREATE",
"resource": {
"encrypted": true
}
}
}
4.2 Implement User Consent Mechanism Testing
Automate consent validation using Selenium:
from selenium import webdriver
driver = webdriver.Chrome()
driver.get('https://my-website.com')
cookie_banner = driver.find_element_by_id('cookie-consent')
assert cookie_banner.is_displayed(), "Consent banner not displayed"
Step 5: Continuous Monitoring and Remediation
Finally, set up Prometheus for compliance monitoring and AlertManager for triggering alerts.
5.1 Monitor Compliance in Production
Use Prometheus to track compliance metrics:
scrape_configs:
- job_name: 'encryption_monitoring'
metrics_path: /metrics
static_configs:
- targets: ['localhost:8080']
5.2 Set Up Alerts for Non-Compliance
Use AlertManager to trigger alerts for breaches:
groups:
- name: compliance_alerts
rules:
- alert: GDPRViolation
expr: encryption_compliance == 0
for: 5m
labels:
severity: critical
annotations:
summary: "Data Encryption Violation Detected"
Architecture Overview
Here’s the architecture diagram summarizing the implementation -
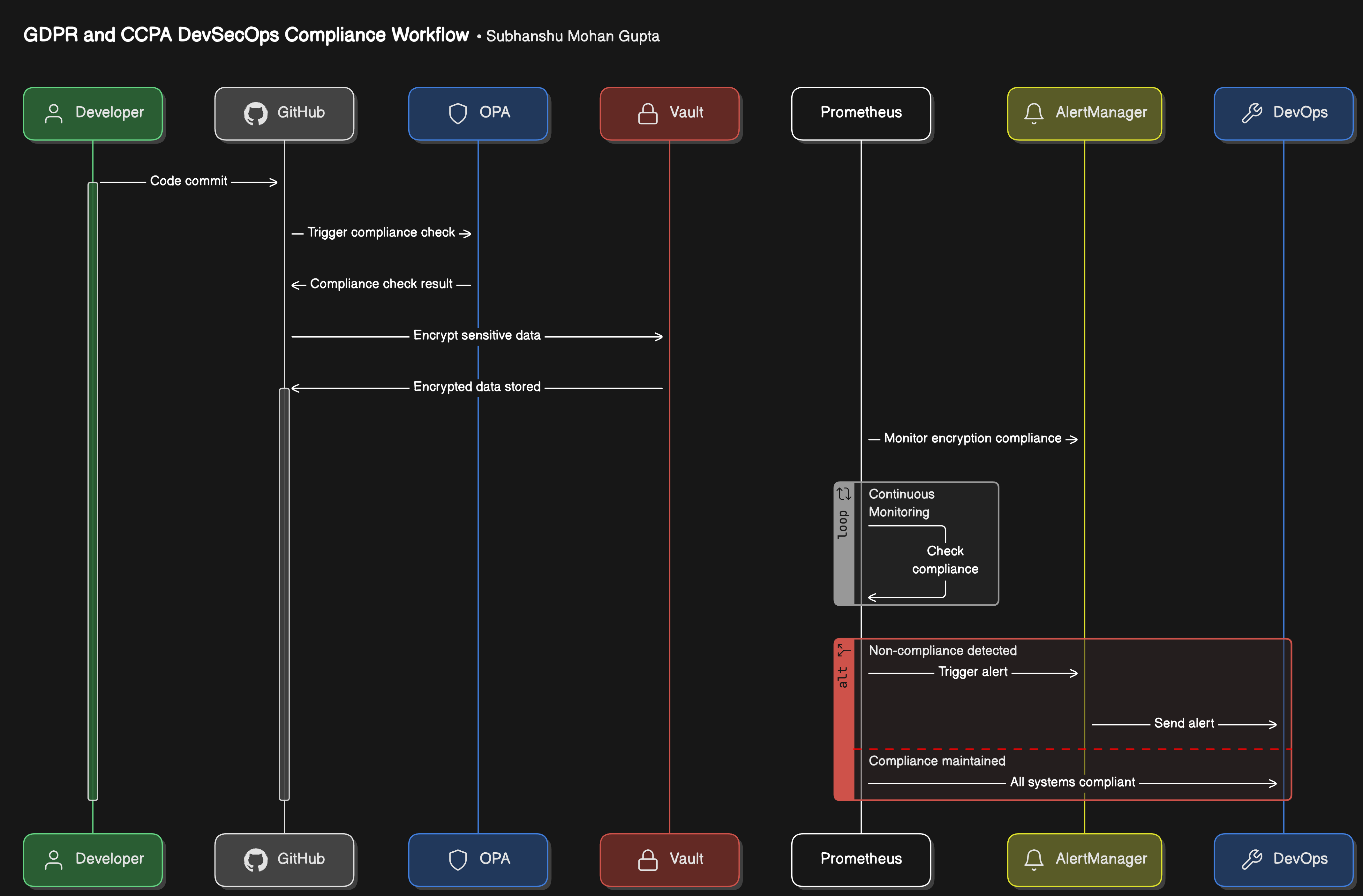
Architecture Components
Development Phase:
Code is committed and scanned for vulnerabilities.
Automated policy checks (via Open Policy Agent) enforce encryption and privacy rules.
Build Phase:
Data encryption libraries (e.g., AWS KMS, HashiCorp Vault) are integrated into the build process.
Privacy risk assessments run as part of the CI/CD pipeline.
Testing Phase:
End-to-end tests validate that consent mechanisms work and data handling complies with GDPR/CCPA.
Vulnerability scans identify potential privacy risks.
Deployment Phase:
Compliance audits are automatically run to ensure no violations.
Threat modeling tools highlight potential security weaknesses.
Monitoring Phase:
Continuous monitoring for compliance violations using logging and alerting tools like ELK Stack and Prometheus.
Any breach of policy is alerted, prompting immediate remediation.
Conclusion
By implementing automated compliance audits, encryption using HashiCorp Vault, privacy risk assessments with OWASP Threat Dragon, and continuous monitoring with Prometheus, you can build a robust DevSecOps pipeline that ensures GDPR and CCPA compliance. This proactive approach not only protects sensitive data but also helps avoid the fines and reputational damage seen in breaches like Marriott and Facebook-Cambridge Analytica.
References
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.