Satoshi Scoop Weekly, 13 Sep 2024
 Cryptape
CryptapeTable of contents
- Crypto Insights
- Same Satoshi, Different Uses
- A Standard for Witnesses-Based Content Storage System: CKBFS Protocol
- Why Be Skeptical of Bitcoin Finance?
- Can Duress Wallets Stop Physical Attacks on Your Bitcoin?
- Nostr Ads on Billarboards
- zkTLS 101: Architecture, Use Cases, and Challenges
- Bitcoin's Corporate Adoption Grows by 30% in One Year
- Top Reads on Blockchain and Beyond
- Overview of Soft Forks and Covenant-Dependent Layer 2 Proposals by Peter Todd
- Thoughts on Blockchain Intellectual Property Inspired by Git
- Core Elements and Various Designs of Multi-Party Shared UTXOs
- Improving the Usability of Recovery Phrases for Decentralized Wallets
- Bitcoin Has Become the World's 5th-Largest Currency by Q2 2024
- Report: Analyzing the Relationship of Bitcoin Price & Hashrate
Crypto Insights
Same Satoshi, Different Uses
Both the BRC20 and RGB++ protocols use Satoshi Dust on the Bitcoin for issuing assets, but they do so in different ways. BRC20 merely uses Satoshis as ledger entries, whereas RGB++ turns them into keys for asset ownership.
This leads to different outcomes. BRC20 results in a large amount of useless Satoshi Dust, putting pressure on node storage, while RGB++ not only avoids this issue but also brings programmable smart contract capabilities to Bitcoin, making it a Bitcoin asset issuance protocol.
A Standard for Witnesses-Based Content Storage System: CKBFS Protocol
Solutions like Ordinals and DOBs on RGB++ inscribe images, text, and other content onto BTC witnesses. However, they share common shortcomings, such as the lack of oracle guarantees, the high costs involved, and the need for cross-chain infrastructure—all of which the CKBFS protocol aims to address.
The proposal is open for discussion on Nervos Talk.
Why Be Skeptical of Bitcoin Finance?
The author argues that, given the current valuation, one should remain skeptical of BTCFi because, philosophically and economically, there is little overlap between BTC holders and yield seekers.
Bitcoin behaves more like gold than a yield-generating asset. Custody isn’t the main focus—BTC is allocated to portfolios as an inflation hedge. Even if only 5% of BTC enters the BTCFi ecosystem, this proportion might still be overly optimistic.
Can Duress Wallets Stop Physical Attacks on Your Bitcoin?
With the increasing number of physical attacks targeting Bitcoin holders, personal security has become a top concern. A common recommendation, especially for travelers, is the use of duress wallets (also known as decoy wallets). The basic idea is to carry a fake hardware wallet or one with only a small amount of assets. In the unfortunate event of coercion, the person can surrender this wallet to protect themselves.
However, Jameson Lopp argues that this method may not be reliable. If the attacker has prior knowledge of the victim, the attacker might not be satisfied with the small amount of payout from a duress wallet, potentially leading to further extortion. Additionally, while some hardware devices (like Coldcard) have a "duress PIN" feature, most holders have never used it, and under stress, they might not remember its existence or how to use it.
Nostr Ads on Billarboards
The Spiral team along with the Bitcoin Design group hosted a "Nostr Ad Hack Week" event, gathering creative advertising slogans.

Check out the full collection.
zkTLS 101: Architecture, Use Cases, and Challenges
Transport Layer Security (TLS) is an encryption protocol that ensures the security of network communications. When visiting a website using HTTPS, data between your browser and the server is encrypted using TLS.
zkTLS (Zero-Knowledge TLS) allows users to prove they received certain data from a website without revealing the full content of the data. In Web3, it's often necessary to connect real-world data (Web2) with decentralized apps (dApps). zkTLS bridges this gap while maintaining privacy and security.
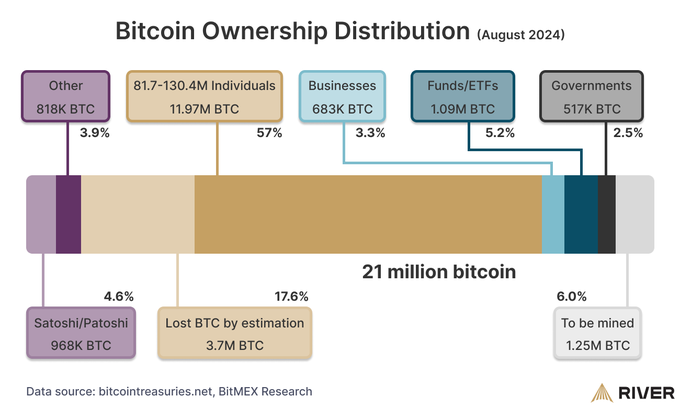
Bitcoin's Corporate Adoption Grows by 30% in One Year
A report from River reveals that as of August 18, 2024, businesses hold 3.3% of Bitcoin’s total supply, or 683,332 BTC. This marks a 587% increase since June 30, 2020, and a 30% growth over the past 12 months.
River estimates that by 2026, corporate Bitcoin holdings will grow at a rate of 204 to 519 BTC per day, equating to $12.2 million to $31.1 million daily at current Bitcoin prices.
Top Reads on Blockchain and Beyond
Overview of Soft Forks and Covenant-Dependent Layer 2 Proposals by Peter Todd
This report provides an overview of various Bitcoin Layer 2 proposals, discussing what technical patterns they share, the new opcodes and other soft fork upgrades they would require to function. It includes a comparison table illustrating how all the components fit together.
The protocols covered include: Ark, LN-Symmetry, Validity Rollups, BitVM, CTV, SIGHASH_ANYPREVOUT, LNHANCE, OP_TXHASH, OP_CAT, Consensus Cleanup, and more.
Thoughts on Blockchain Intellectual Property Inspired by Git
Git can be understood as a distributed version control system. Similarly, intellectual property (IP) represents a collection of various rights, where different people own different subsets of these rights—some hold the rights to create derivatives, others to perform, and some hold multiple rights at once, much like Git's “version”. Applying Git’s logic to IP management system (IP Repo), where each IP regarded as an independent repository and various rights as different branches or versions, could enhance scalability, programmability, and traceability of IPs, while preserving the independence of each sub-version.
Core Elements and Various Designs of Multi-Party Shared UTXOs
This article analyzes the core elements of sharing UTXOs (Unspent Transaction Outputs) and explains the designs of multiple cases based on sharing UTXO, attributing their features to the use of the core elements.
The article is one of the best analyses on multi-party sharing UTXO schemes. By systematically deconstructing the fundamental building blocks of these solutions and providing concise diagrams, making complicated concepts much easier. Once readers grasp these basics, understanding protocols like Ark, channel factories, Statechain, and others becomes much clearer—revealing that these diverse solutions are essentially combinations of the basic modules.
Improving the Usability of Recovery Phrases for Decentralized Wallets
This report details the process of designing and developing prototypes for a decentralized wallet: through research, user review analysis, and the creation of proto-personas, critical points were identified, and solutions are suggested to remove friction and improve the overall experience.
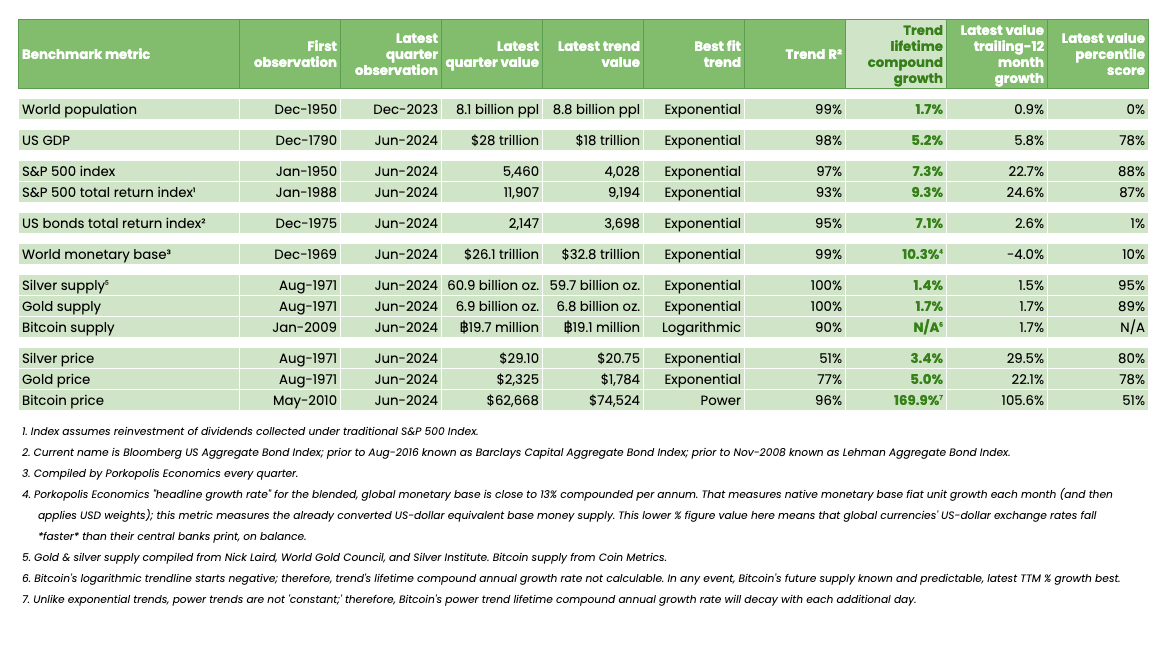
Bitcoin Has Become the World's 5th-Largest Currency by Q2 2024
As of Q2 2024, Bitcoin has become the world's fifth-largest currency, following the Federal Reserve, European Central Bank, People's Bank of China, and the Bank of Japan.
The table below presents various economic indicators, including global population, U.S. GDP, stock indices, bond indices, monetary base, gold/silver supply and prices, and Bitcoin supply and prices, along with historical observations, latest trend values, growth trends, and relevant statistical analyses to assess their evolution over time and future projections.
Report: Analyzing the Relationship of Bitcoin Price & Hashrate
Timing is arguably the most important factor when it comes to success with Bitcoin mining. You can do everything else right - purchase efficient ASICs, source low-cost power, and maintain high uptime - but if you enter the market at the wrong time you will have less success than you otherwise would.
This report examines the quantitative and qualitative relationship between the price of Bitcoin and the network Hashrate to determine when is the most opportune time to start mining Bitcoin. Price and Hashrate are the two most dominant inputs when it comes to Bitcoin mining profitability, mapping out the relationship between the two, what variables impact each, and related trends across Bitcoin cycles will provide key insights into the nature of Bitcoin mining.
Download the PDF here.
Subscribe to my newsletter
Read articles from Cryptape directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
