WordPress Community Plugin PeepSo Vulnerability: CVE-2024-31251
 Abishek Kafle
Abishek Kafle
Introduction
Hey there! I'm Abishek Kafle, a security researcher with the Patchstack Alliance. Today, I want to tell you how I found a big security flaw in a popular WordPress plugin, which got the CVE-2024-31251. This story shows why detailed security research is important and how one person's work can greatly impact the open-source community.
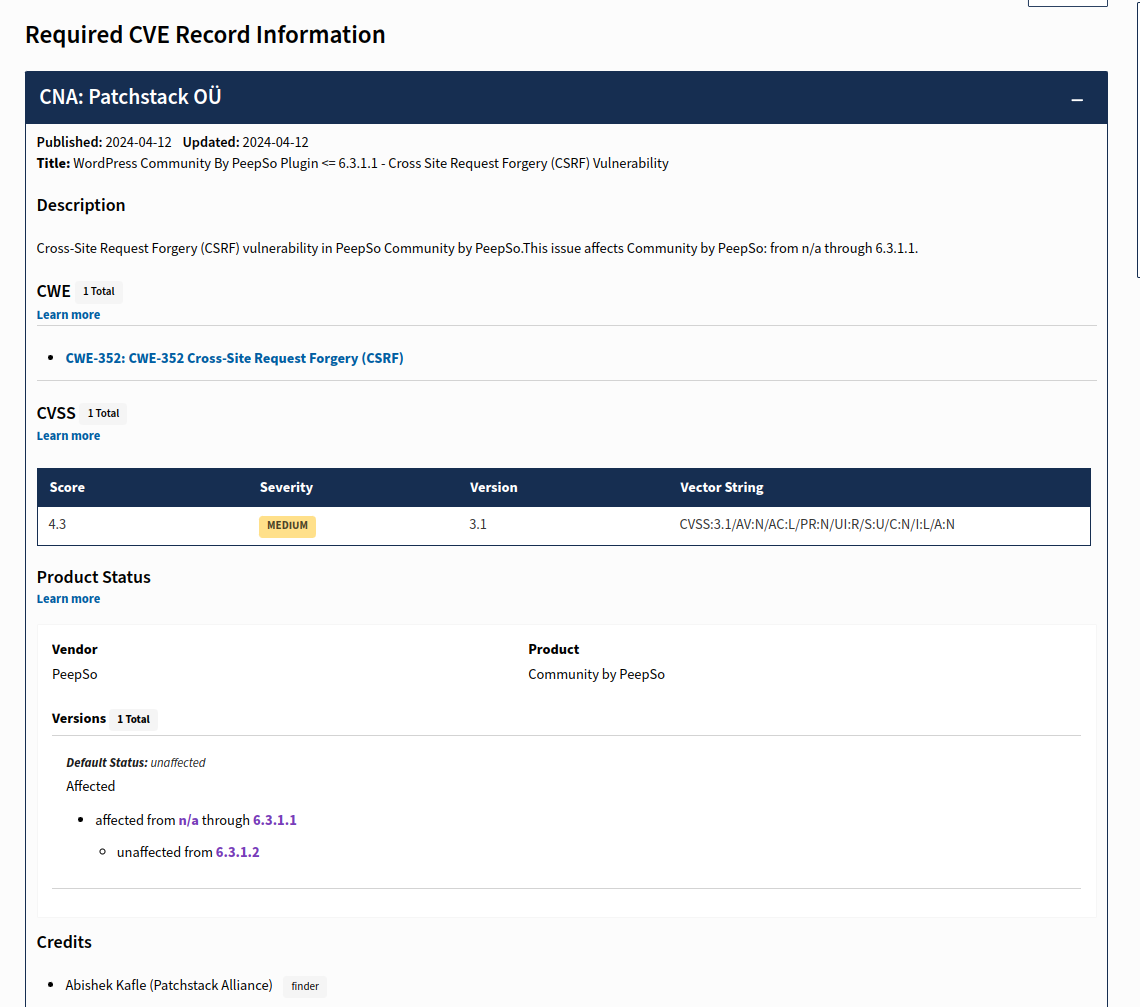
What is CVE-2024-31251?
CVE-2024-31251 is a security vulnerability identified in the WordPress Community by PeepSo plugin. Here are the essential details:
Vulnerability Type: Cross-Site Request Forgery (CSRF)
Affected Versions: All versions up to and including 6.3.1.1
Fixed Version: 6.3.1.2 and later
Severity: Medium (CVSS Score: 4.3)
Understanding the Vulnerability
Cross-Site Request Forgery (CSRF) is a type of attack that tricks a user's browser into performing unwanted actions on a website where the user is authenticated. In the context of the PeepSo plugin, this could potentially allow an attacker to:
Modify user settings without permission
Post content on behalf of logged-in users
Alter community configurations
Technical Details
CWE Classification: CWE-352 (Cross-Site Request Forgery)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N
This vector indicates that the attack:
Requires no special privileges
Can be launched from the network
Needs user interaction
Has a low impact on confidentiality and availability, but some impact on integrity.
Why This Matters?
→ If you're using the Community by PeepSo plugin, update to version 6.3.1.2 or later as soon as possible.
Subscribe to my newsletter
Read articles from Abishek Kafle directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Abishek Kafle
Abishek Kafle
Infosec Poet and CAP-certified DevOps/SecOps Engineer, passionate about security, creativity, and continuous learning.