AI-Driven Infrastructure as Code (IaC) Security: Preventing Misconfigurations in DevSecOps
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
As modern infrastructure becomes more complex, misconfigurations in Infrastructure as Code (IaC) can introduce significant security vulnerabilities. Detecting these issues early is crucial for preventing costly breaches in production. This is where AI-driven security steps in, offering automated solutions to identify and correct misconfigurations before they reach production environments.
In this blog, we explore how AI can be integrated with IaC tools like Terraform and Ansible to automatically detect and fix vulnerabilities, embedding security directly into the infrastructure deployment process.
The Need for AI in IaC Security
Infrastructure as Code allows developers to automate the provisioning and management of cloud infrastructure. However, misconfigurations such as publicly accessible storage, weak firewall rules, or incorrect access control settings are a common challenge.
Without automated checks, these issues often go unnoticed until it’s too late. AI-powered security solutions, like Bridgecrew, allow us to identify these misconfigurations automatically and even apply fixes.
Real-World Example: Publicly Accessible S3 Buckets
One of the most common IaC security issues is the configuration of an S3 bucket in AWS with public access. Suppose a developer sets the bucket’s permissions to public-read, inadvertently exposing sensitive data to anyone with the link.
AI-driven security tools can detect this vulnerability, suggest a fix, or automatically correct it by changing the bucket’s access control to private, ensuring security without manual intervention.
Architecture Overview: AI-Driven IaC Security
Below is the architecture for AI-driven IaC security, focusing on integrating Terraform and Ansible with an AI-powered tool like Bridgecrew.
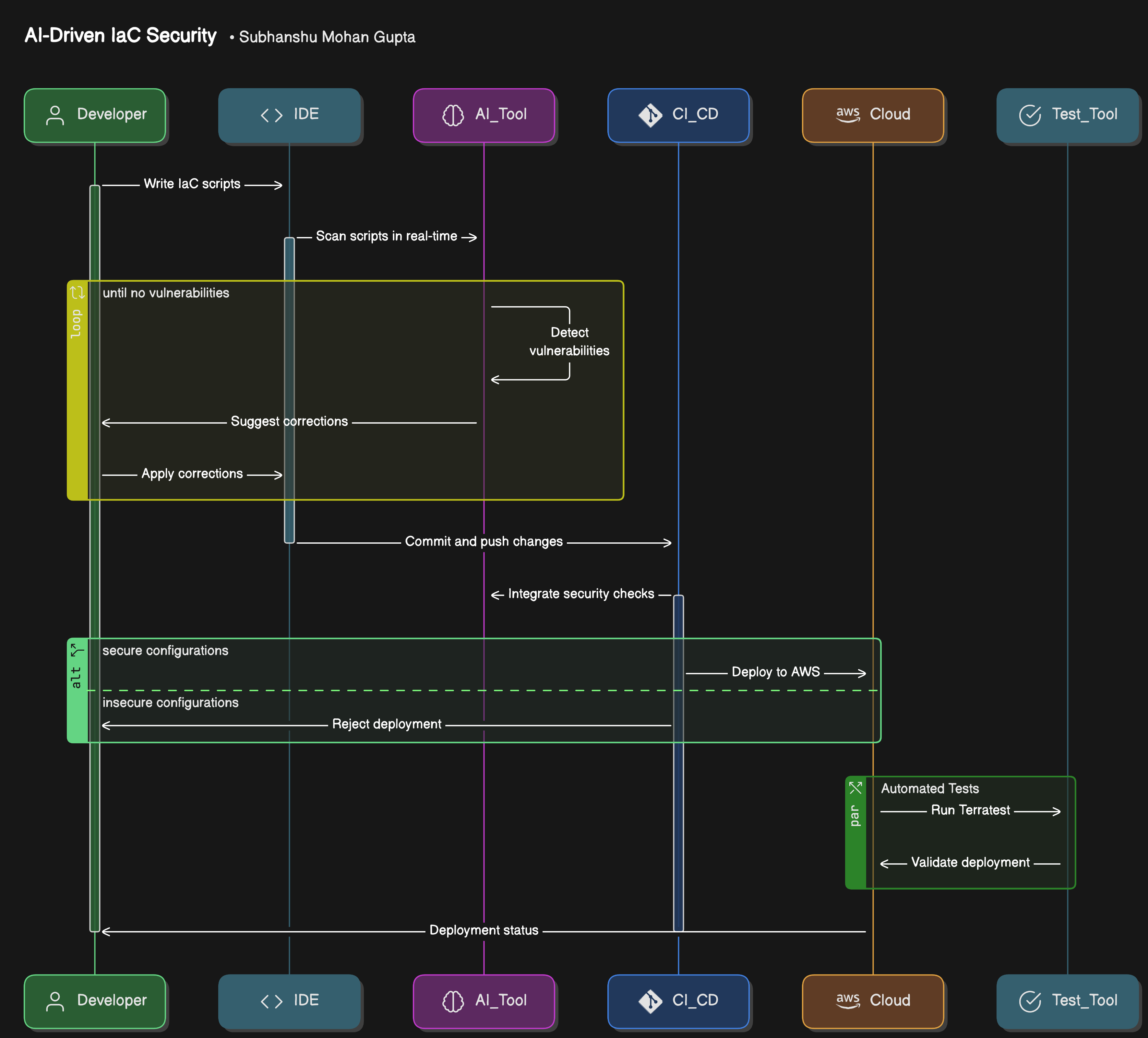
Developer writes IaC scripts using tools like Terraform or Ansible.
AI-powered tool (e.g., Bridgecrew) scans the scripts in real-time, detects vulnerabilities, and suggests or applies corrections.
CI/CD pipeline integrates the security checks, ensuring that only secure configurations reach production.
Cloud infrastructure (AWS in this case) is deployed with AI-validated security settings.
Automated tests like Terratest validate the deployment to ensure the infrastructure is secure and functioning as expected.
Step-by-Step Guide: Implementing AI-Driven IaC Security
Let’s dive into the technical implementation of this architecture using Terraform, Ansible, and Bridgecrew for AI-driven security.
1. Set Up Your Environment
Ensure you have the following tools installed:
Terraform
Ansible
Bridgecrew (or another AI-powered security tool)
AWS CLI (for Terraform to deploy resources to AWS)
Docker (if needed for local Ansible execution)
2. Configure Terraform for Your Infrastructure
Here, we’ll configure a Terraform script that provisions an S3 bucket. This initial script contains a misconfiguration — a public S3 bucket.
main.tf (Terraform file):
provider "aws" {
region = "us-west-2"
}
resource "aws_s3_bucket" "example_bucket" {
bucket = "example-bucket"
acl = "public-read" # Misconfiguration: Public Access
}
resource "aws_s3_bucket_policy" "bucket_policy" {
bucket = aws_s3_bucket.example_bucket.bucket
policy = <<POLICY
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::example-bucket/*"
}
]
}
POLICY
}
3. Install and Configure Bridgecrew
Bridgecrew is an AI-powered security tool that integrates with Terraform and Ansible, scanning IaC for misconfigurations and suggesting fixes.
- Install Bridgecrew:
brew install bridgecrew
Alternatively, install using pip:
pip install bridgecrew
4. Scan Your Terraform Code with Bridgecrew
Scan the Terraform directory for misconfigurations:
bridgecrew -d ./
Bridgecrew will analyze the Terraform script and detect misconfigurations, such as the public S3 bucket.
Example output:
Checkov Report
Passed checks: 1
Failed checks: 1
- S3 bucket should not allow public access [aws_s3_bucket.example_bucket]
5. Automatically Fix Misconfigurations
To fix the detected issues, run:
bridgecrew fix -d ./
Bridgecrew automatically corrects the configuration. For example, it changes the S3 bucket’s ACL from public-read to private:
Modified main.tf after Bridgecrew fix:
resource "aws_s3_bucket" "example_bucket" {
bucket = "example-bucket"
acl = "private" # Corrected ACL to prevent public access
}
6. Integrating AI-Powered Security into CI/CD Pipeline
To ensure ongoing security, integrate Bridgecrew into your CI/CD pipeline. Here’s an example of how to add it to a Bitbucket pipeline:
Bitbucket Pipeline Example:
pipelines:
default:
- step:
name: Run Terraform and Bridgecrew Security Check
script:
- bridgecrew -d ./
- bridgecrew fix -d ./
- terraform init
- terraform apply -auto-approve
This integration ensures security checks and fixes are part of every deployment.
7. Ansible Integration with AI-Powered Security
You can also use Bridgecrew to scan and fix misconfigurations in Ansible playbooks. Here’s an example playbook that creates an S3 bucket:
playbook.yml:
- hosts: localhost
tasks:
- name: Create an S3 bucket with public access
aws_s3:
bucket: mybucket
mode: create
permission: public-read # Misconfiguration
Run Bridgecrew to detect and fix the issue:
bridgecrew -d ./playbook.yml
8. Run Automated Tests (e.g., Terratest)
Testing is critical to ensure your infrastructure is both secure and functional. Tools like Terratest can be used to validate your Terraform configurations.
Terratest example:
package test
import (
"testing"
"github.com/gruntwork-io/terratest/modules/terraform"
)
func TestTerraformAwsS3Bucket(t *testing.T) {
terraformOptions := &terraform.Options{
TerraformDir: "../terraform/aws_s3_bucket",
}
defer terraform.Destroy(t, terraformOptions)
terraform.InitAndApply(t, terraformOptions)
// Add custom logic to validate the S3 bucket's ACL
}
9. Deploy to AWS
Once your Terraform code has been scanned, fixed, and tested, deploy it to AWS:
terraform apply -auto-approve
This ensures that your infrastructure is both secure and ready for production.
Conclusion
By integrating AI-powered security tools like Bridgecrew with Terraform and Ansible, you can automate the detection and correction of misconfigurations. This ensures that your infrastructure is secure from the outset, allowing you to embed security policies directly into the DevSecOps pipeline.
Implementing this architecture allows you to automatically prevent potential vulnerabilities and create a resilient infrastructure without sacrificing agility or speed.
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.