21 Days of Solidity Smart Contract Security Research: Day - 5
 Manojkumar
ManojkumarToday is Day 5, and after crossing Days 1, 2, 3, and 4 you’ll get clarity about What SCSR is, the basics of SCSR, the types of auditors, and finally the terms of DeFi.
Now, we move deeper into Ethereum, the types of layers in Ethereum Blockchain, and the roles of those layers.
The Layers in Ethereum Blockchain: An Overview
Blockchain technology is often described as a stack of layers, each with its specific functions and responsibilities. Let's break down these layers as shown in the diagram:
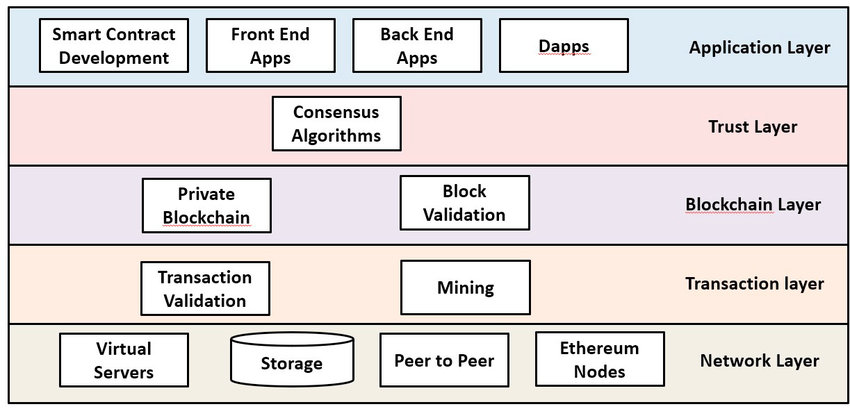
Application Layer
This is the topmost layer where users interact with blockchain applications.
Components:
Smart Contract Development: Writing and deploying self-executing contracts.
Front End Apps: User interfaces for interacting with the blockchain.
Back End Apps: Server-side logic for blockchain applications.
Dapps (Decentralized Applications): Full applications built on blockchain.
Trust Layer
Ensures all network participants agree on the state of the blockchain.
Key Component: Consensus Algorithms (e.g., Proof of Work, Proof of Stake)
Blockchain Layer
Manages the structure and validation of the blockchain itself.
Components:
Private Blockchain: Controlled, permissioned networks.
Block Validation: Verifying the integrity of new blocks.
Transaction Layer
Handles the processing and validation of individual transactions.
Components:
Transaction Validation: Ensuring transactions are legitimate.
Mining: The process of creating new blocks (in some blockchain systems).
Network Layer
The foundation that enables communication and data storage across the network.
Components:
Virtual Servers: Hosting blockchain nodes and services.
Storage: Distributed storage of blockchain data.
Peer to Peer: Direct communication between network participants.
Ethereum Nodes: Specific to Ethereum, these maintain and validate the blockchain.
Right now, we understand the layers of the Ethereum Blockchain and at the same time, every layer gets different kinds of vulnerabilities below we can see the possible smart contract vulnerabilities in the Ethereum blockchain.
Possible Smart Contract Vulnerabilities in Ethereum:
Reentrancy
Reentrancy via Modifier
Read-Only Reentrancy
Cross-Function Reentrancy
Cross-Contract Reentrancy
Front-Running
Front-Running - Unprotected withdraw
Front-Running - Sandwich attack
Front-Running - ERC20 approval
Front-Running - Signatures
Back-Running
Flash-Loan Governance Attack
Flash-Loan Price Attack
Denial Of Service (DOS) by complex fallback function
Denial Of Service (DOS) by gas limit
Denial Of Service (DOS) by non-existent address or malicious contract
Floating Point Arithmetic
ECDSA Signature malleability
ECDSA Signature replay
Replay Attack
DAO Attacks
Price Oracle Manipulation
Cross-Chain Bridge Manipulation
Initial Supply Mint Issue
Divide before multiply
Unchecked External Calls
Integer Underflow
Defi Slippage attack
Amplification Attack Double Spending
Malicious Honeypot
Unsafe Delegatecalls
Loops Gas Limit
Short Address/Parameter Attack
Phishing With Improper Authorization
Unexpected Ether With Forcibly Sending Ether
Block timestamp Manipulation
Unchecked return values
Insecure Randomness
Proxy Storage Collision
Strict equalities
Timestamp Dependence
Use of Deprecated Functions
Requirement Validation
Business logic
Absent modifiers
Force Feeding
Gas Limit Exhaustion
Rounding Down To Zero
Smart Contract Security Research and Its Importance
Smart contract security research is crucial because vulnerabilities in smart contracts can lead to significant financial losses and undermine trust in blockchain systems. Here's how it relates to each layer:
Application Layer
Importance: This is where most security vulnerabilities are introduced.
Focus Areas:
Secure coding practices for smart contracts.
Proper handling of user inputs in front-end and back-end apps.
Ensuring Dapps don't introduce vulnerabilities when interacting with smart contracts.
Trust Layer
Importance: Vulnerabilities here could compromise the entire blockchain's integrity.
Focus Areas:
Ensuring consensus algorithms are resistant to manipulation.
Protecting against 51% attacks or other consensus-related vulnerabilities.
Blockchain Layer
Importance: Vulnerabilities could allow tampering with the blockchain's structure.
Focus Areas:
Ensuring proper block validation to prevent invalid or malicious blocks.
Securing private blockchains against unauthorized access or modifications.
Transaction Layer
Importance: Vulnerabilities here could lead to financial theft or fraud.
Focus Areas:
Ensuring robust transaction validation to prevent double-spending or other fraudulent activities.
Securing the mining process against potential exploits.
Network Layer
Importance: Foundational security that affects all upper layers.
Focus Areas:
Protecting against network-level attacks like DDoS.
Ensuring secure peer-to-peer communications.
Safeguarding data storage to prevent unauthorized access or tampering.
Why Understanding These Layers is Crucial for Smart Contract Security
Holistic Security Approach: Vulnerabilities can exist at any layer. Understanding the entire stack helps in creating comprehensive security strategies.
Interdependence: Issues in lower layers can impact the security of smart contracts. For example, a network-layer attack could disrupt smart contract execution.
Proper Implementation: Knowledge of how each layer functions helps in implementing smart contracts that work securely within the blockchain ecosystem.
Vulnerability Assessment: Understanding the layers aids in identifying potential weak points and attack vectors in smart contract design and implementation.
Efficient Debugging: When issues arise, knowing the layers helps in quickly identifying where the problem might be originating.
Innovation in Security: Understanding the full stack can lead to innovative security solutions that leverage the strengths of different layers.
Risk Management: Proper knowledge allows for better risk assessment and mitigation strategies in smart contract development and deployment.
Conclusion
For beginners in blockchain and smart contract development, understanding these layers is foundational. It provides a comprehensive view of how blockchain systems operate and where potential vulnerabilities may arise.
If you like my works, kindly share your love and respect through:
Bitcoin - bc1q3qtpng345hup3q99a8qxdxn7ajfy730lxn56uz
Ethereum / Polygon / Arbitrum - 0xB6C784dB83538646C3AD67eA025A11bA49880c21
Solana - BMpE17BaauA8GUX5ym97cNam1k4PifW7oeJD9wPggnn7
Polkadot - 5H49N8uyrxz4rH4YjyENAoQ4HFT5CERUxhhFTWABjKAj7fmW
Subscribe to my newsletter
Read articles from Manojkumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
