Nmap: TryHackMe
 Jebitok
JebitokTable of contents

In this article, I’ll be covering the THM challenges and answers related to Nmap Overview, Nmap Switches, Scan Types from the Overview, TCP Connect Scans, SYN Scans, UDP Scans, NULL, FIN, and Xmas to ICMP Networking Scanning, NSE Scripts from the Overview, Working with the NSE to Searching for Scripts and Firewall.
Introduction to Nmap and PortScanning
Every computer has a total of 65535 available ports; however, many of these are registered as standard ports. For example, an HTTP web service can nearly always be found on port 80 of the server. A HTTPS Webservice can be found on port 443. Windows NetBIOS can be found on port 139 and SMB can be found on port 445. It is important to note; however, that especially in a CTF setting, it is not unheard of for even these standard ports to be altered, making it even more imperative that we perform appropriate enumeration on the target.
If we do not know which of these ports a server has open, then we do not have a hope of successfully attacking the target; thus, it is crucial that we begin any attack with a port scan. This can be accomplished in a variety of ways – usually using a tool called nmap, which is the focus of this room. Nmap can be used to perform many different kinds of portscan – the most common of these will be introduced in upcoming tasks; however, the basic theory is this: nmap will connect to each port of the target in turn. Depending on how the port responds, it can be determined as being open, closed, or filtered (usually by a firewall). Once we know which ports are open, we can then look at enumerating which services are running on each port – either manually, or more commonly using nmap.
So, why nmap? The short answer is that it's currently the industry standard for a reason: no other port scanning tool comes close to matching its functionality (although some newcomers are now matching it for speed). It is an extremely powerful tool – made even more powerful by its scripting engine which can be used to scan for vulnerabilities, and in some cases even perform the exploit directly! Once again, this will be covered more in upcoming tasks.
The THM Challenges
What networking constructs are used to direct traffic to the right application on a server?
PortsHow many of these are available on any network-enabled computer?
65535[Research] How many of these are considered "well-known"? (These are the "standard" numbers mentioned in the task)
1024Out of the total 65,535 available ports on a computer, the known or standard ports are typically divided into three main categories:
Well-known ports: Ports 0 to 1023
- These ports are reserved for common and widely used services (e.g., HTTP, FTP, DNS, SSH). They are officially assigned by the Internet Assigned Numbers Authority (IANA).
Registered ports: Ports 1024 to 49151
- These ports are registered by software developers for specific services or applications. They are not as universally standardized as well-known ports, but they are commonly used for specific purposes.
Dynamic or private ports: Ports 49152 to 65535
- These ports are not registered or assigned for any particular service and are often used dynamically for client-side communication or temporary services.
Thus, the well-known and registered ports range from 0 to 49151, meaning there are 49,152 known or standard ports in total.
Nmap To cover the next section from questions 4 to 19, we need to run nmap —help on our terminals. For this to be possible we need Nmap installed depending on our OS
// on MacOs
$ brew install nmap
// Debian/Ubuntu-based Distributions
$ sudo apt update
$ sudo apt install nmap
// Red Hat/CentOS/Fedora-based Distributions
$ sudo dnf install nmap
$ sudo yum install nmap
// Arch Linux-based Distributions
$ sudo pacman -S nmap
// OpenSUSE
$ sudo zypper install nmap
Run the command and use the result to solve the challenges in this category.
$ nmap --help
What is the first switch listed in the help menu for a 'Syn Scan' (more on this later!)?
-sS(this covers 4 - 5)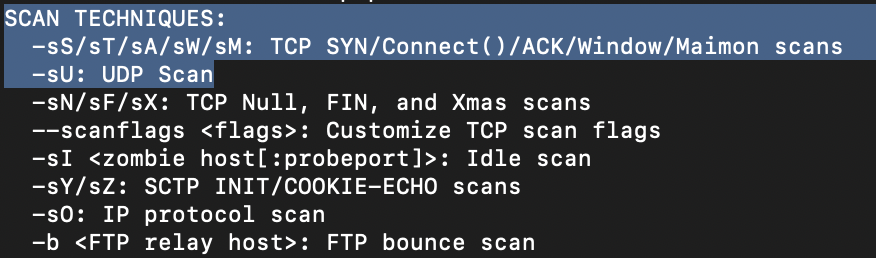
Which switch would you use for a "UDP scan"?
-sUIf you wanted to detect which operating system the target is running on, which switch would you use?
-O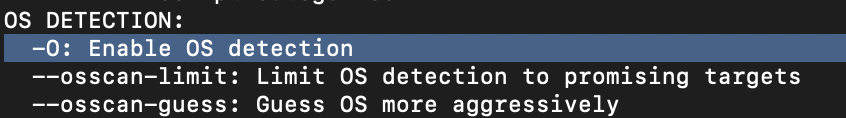
Nmap provides a switch to detect the version of the services running on the target. What is this switch?
-sV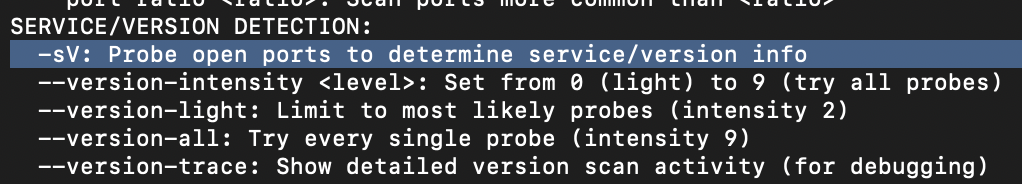
The default output provided by Nmap often does not provide enough information for a pentester. How would you increase the verbosity?
-v(The image below covers 8 - 9)
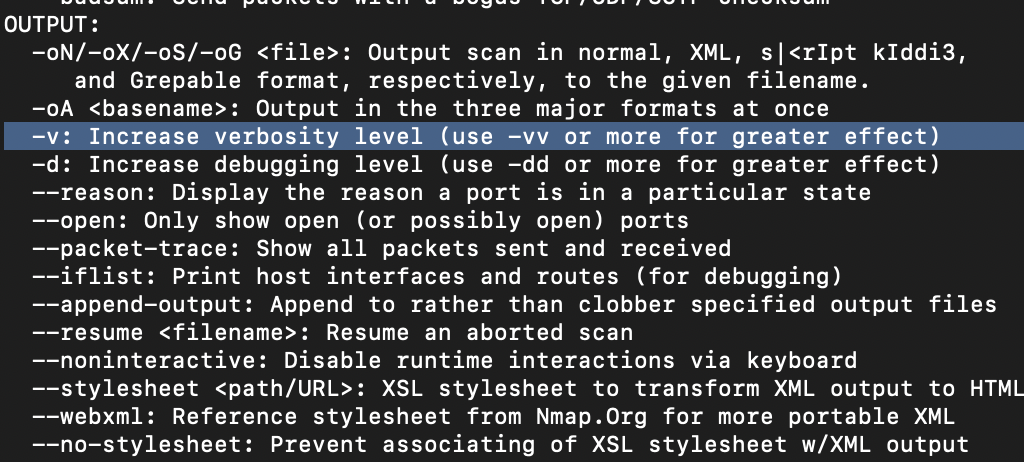
Verbosity level one is good, but verbosity level two is better! How would you set the verbosity level to two? (Note: it's highly advisable to always use at least this option)
-vvWe should always save the output of our scans -- this means that we only need to run the scan once (reducing network traffic and thus the chance of detection), and gives us a reference to use when writing reports for clients. What switch would you use to save the Nmap results in three major formats?
-oA(The image below covers questions 10 - 12)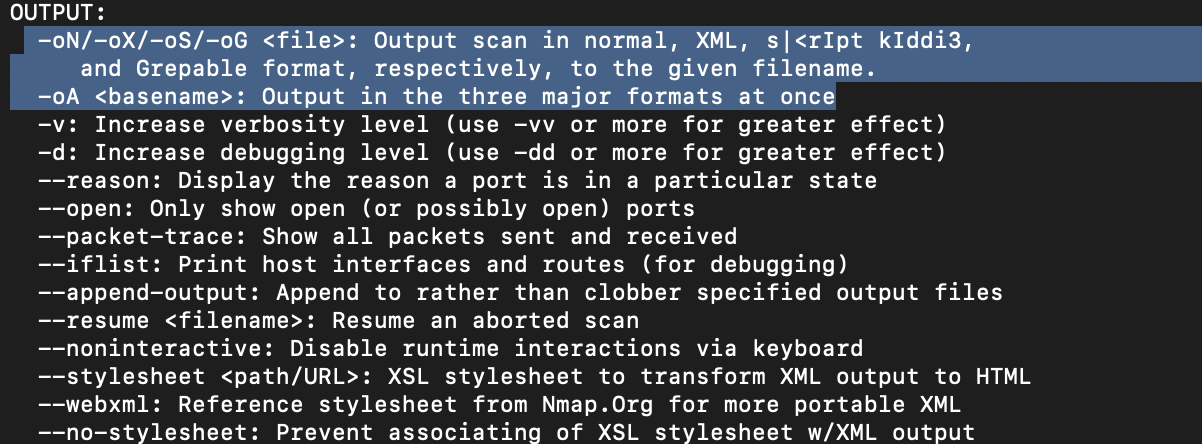
What switch would you use to save the Nmap results in a "normal" format?
-oNA very useful output format: how would you save results in a "grepable" format?
-oGSometimes the results we're getting just aren't enough. If we don't care about how loud we are, we can enable "aggressive" mode. This is a shorthand switch that activates service detection, operating system detection, a traceroute, and common script scanning. How would you activate this setting?
-A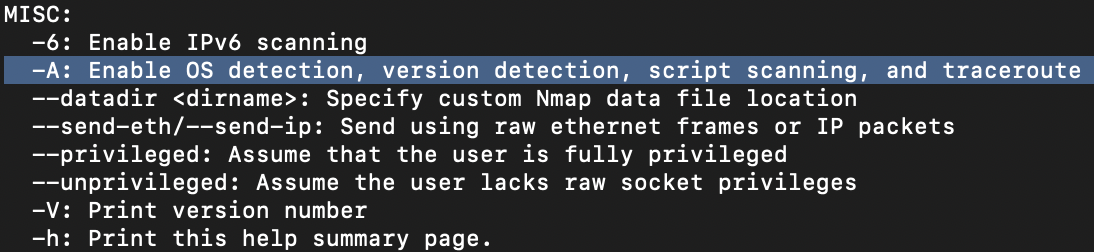
Nmap offers five levels of "timing" templates. These are essentially used to increase the speed of your scan runs. Be careful though: higher speeds are noisier, and can incur errors! How would you set the timing template to level 5?
-T5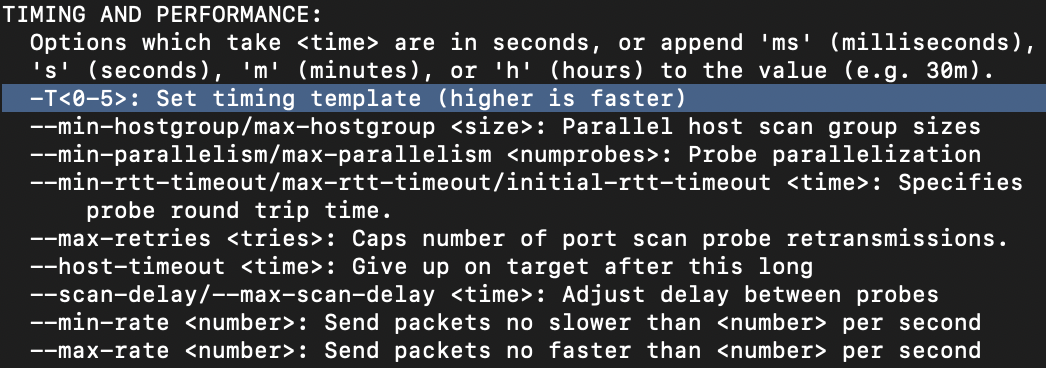
We can also choose which port(s) to scan. How would you tell Nmap to only scan port 80?
-p 80(the image below covers question 15 - 17)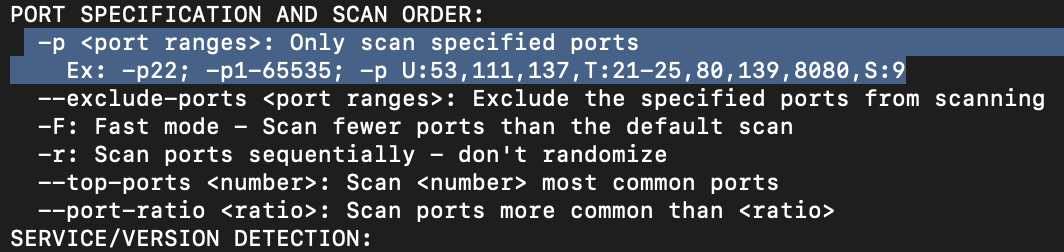
How would you tell Nmap to scan ports 1000-1500?
-p 1000-1500A very useful option that should not be ignored: How would you tell Nmap to scan all ports?
-p-How would you activate a script from the Nmap scripting library (lots more on this later!)?
--script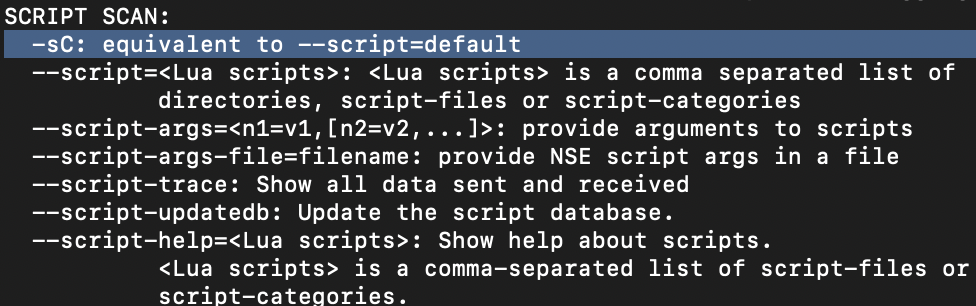
How would you activate all of the scripts in the "vuln" category?
--script=vuln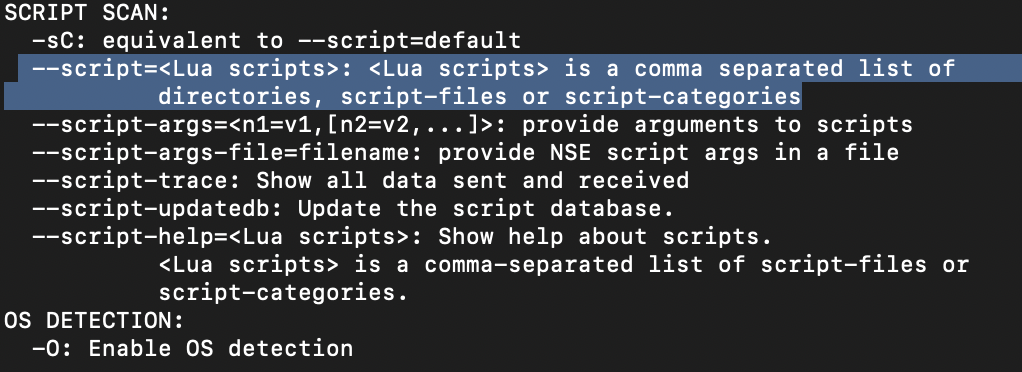
Which RFC defines the appropriate behavior for the TCP protocol?
RFC 9293If a port is closed, which flag should the server send back to indicate this?
RST(reset)
For example, if a port is closed, RFC 9293 states that: "... If the connection does not exist (CLOSED), then a reset is sent in response to any incoming segment except another reset. A SYN segment that does not match an existing connection is rejected by this means."
There are two other names for a SYN scan, what are they?
Half-Open, StealthCan Nmap use a SYN scan without Sudo permissions (Y/N)? N
SYN scans are the default scans used by Nmap if run with sudo permissions. If run without sudo permissions, Nmap defaults to the TCP Connect scan we saw in the previous task.
If a UDP port doesn't respond to an Nmap scan, what will it be marked as?
open|filteredWhen a UDP port is closed, by convention the target should send back a "port unreachable" message. Which protocol would it use to do so?
ICMPWhich of the three shown scan types uses the URG flag?
xmasWhy are NULL, FIN, and Xmas scans generally used?
Firewall EvasionWhich common OS may respond to a NULL, FIN or Xmas scan with a RST for every port?
Microsoft WindowsHow would you perform a ping sweep on the 172.16.x.x network (Netmask: 255.255.0.0) using Nmap? (CIDR notation)
nmap -sn 172.16.0.0/16
This command will ping all addresses in the 172.16.0.0 - 172.16.255.255 range using the-sn(ping scan) option without performing a port scan. This/16represents the subnet mask 255.255.0.0, covering a much larger range than/24. It helps in scanning an entire Class B network (65,536 IP addresses), whereas/24limits the scan to just 256 IP addresses.What language are NSE scripts written in?
LuaWhich category of scripts would be a very bad idea to run in a production environment?
intrusiveWhat optional argument can the
ftp-anon.nseDoes script take?maxlistThe `
ftp-anon.nse` script in Nmap, which checks for anonymous FTP access, can take an optional argument calledftp-anon.maxlist. This argument controls the maximum number of files that the script will attempt to list in each directory. If a directory contains more files than the limit, the script will stop listing.
Example usage:nmap --script=ftp-anon --script-args=ftp-anon.maxlist=50 <target>In this case, the script will attempt to list up to 50 files per directory on the FTP server. The default value is 1000, but you can adjust it depending on the size of the directories you're scanning.Search for "smb" scripts in the
/usr/share/nmap/scripts/directory using either of the demonstrated methods. What is the filename of the script which determines the underlying OS of the SMB server?smb-os-discovery.nse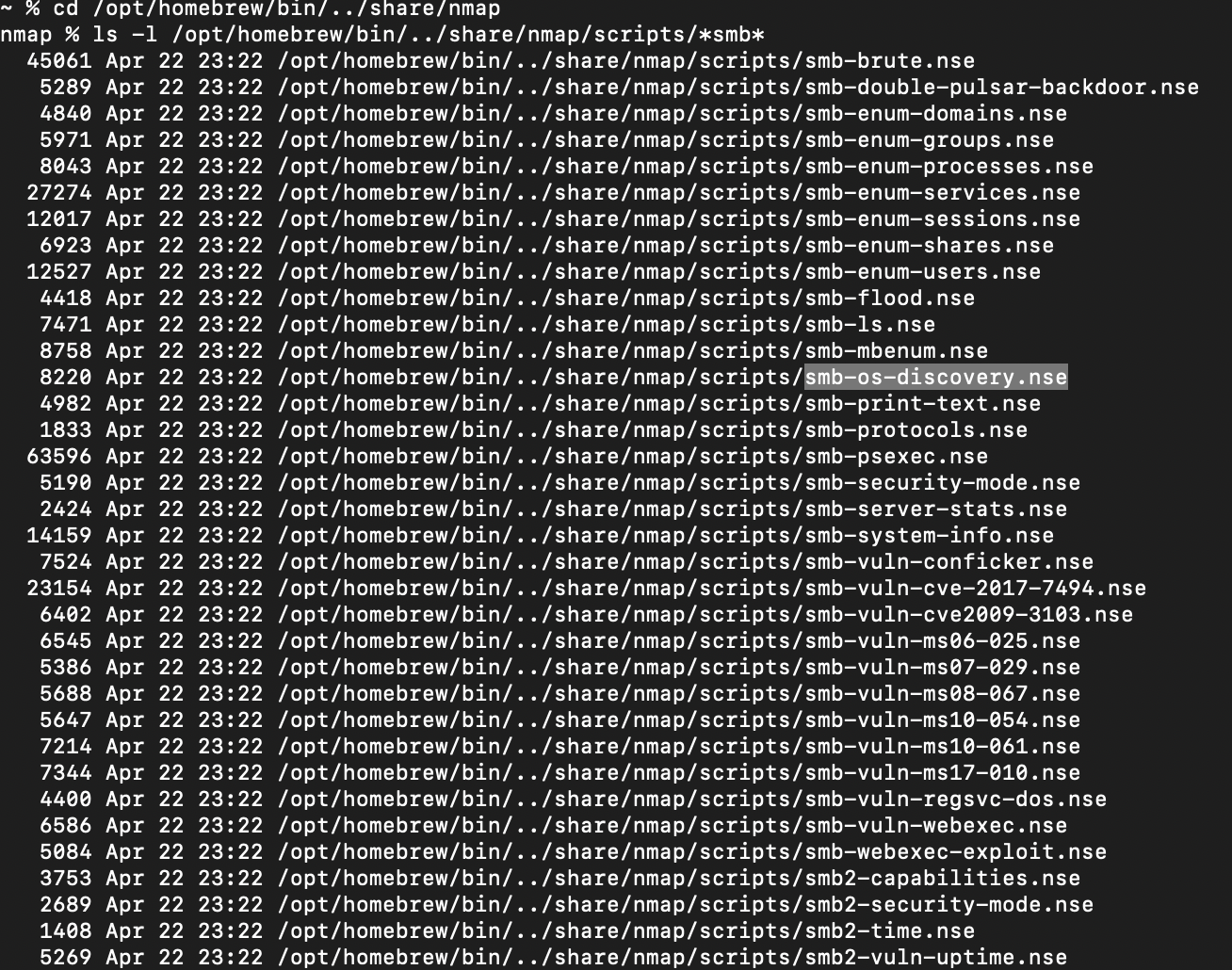
Read through this script. What does it depend on?
smb-bruteusing nano didn’t show the entire script.$ nano /opt/homebrew/bin/../share/nmap/scripts/smb-os-discovery.nseI checked on the Nmap Websites on the scripts section and scrolled up to out
smb-os-discovery.nseand I found this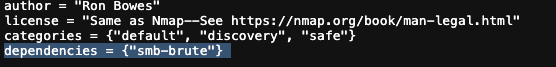
Which simple (and frequently relied upon) protocol is often blocked, requiring the use of the
-Pnswitch?ICMP[Research] Which Nmap switch allows you to append an arbitrary length of random data to the end of packets?
--data-lengthOn your terminal, you can run the commandNmap —helpthen check the firewall section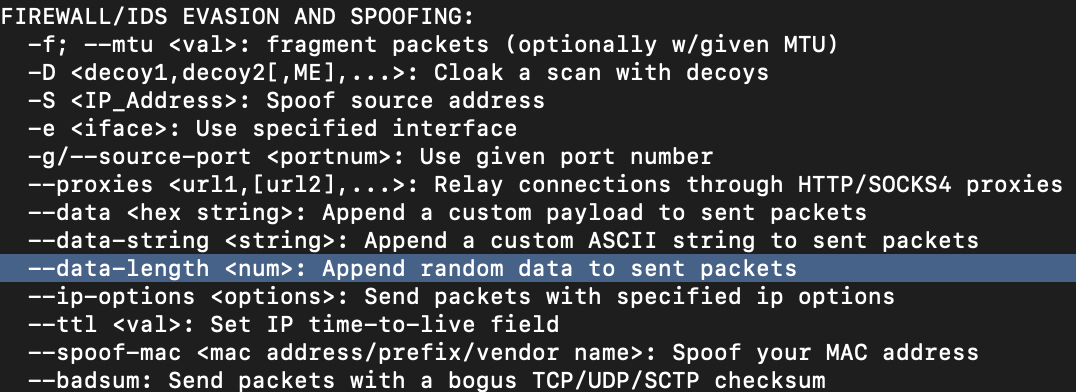
Does the target IP respond to ICMP echo (ping) requests (Y/N)?
Nthey’re blocked unless we use-PnPerform a Xmas scan on the first 999 ports of the target -- how many ports are shown to be open or filtered?
999We can use three commands to get the answers but because the next question is dependent on the outcome of this we use this one. The keyword isXmas ⇒ -sX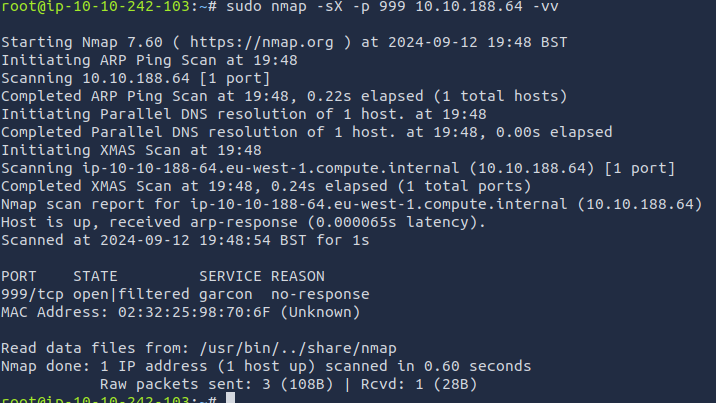
There is a reason given for this -- what is it? Note: The answer will be in your scan results. Think carefully about which switches to use -- and read the hint before asking for help!
No ResponsePerform a TCP SYN scan on the first 5000 ports of the target -- how many ports are shown to be open?
5(count the number of open ports)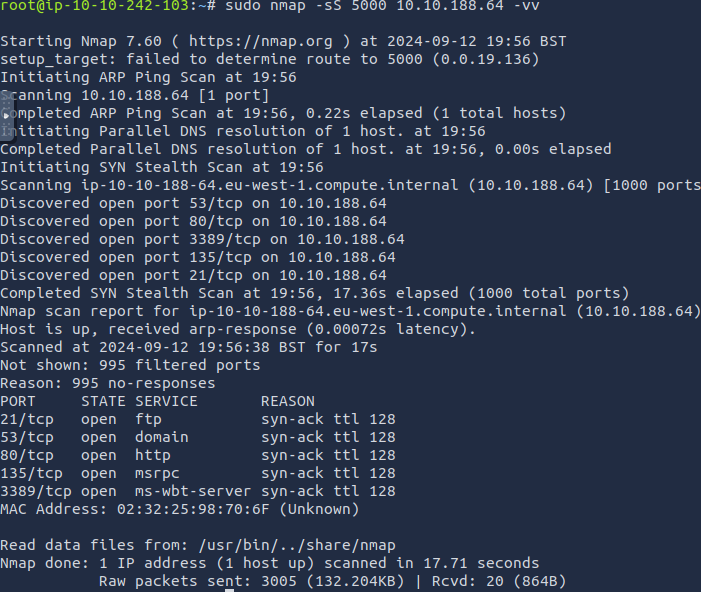
Open Wireshark (see Cryillic's Wireshark Room for instructions) and perform a TCP Connect scan against port 80 on the target, monitoring the results. Make sure you understand what's going on. Deploy the
ftp-anonscript against the box. Can Nmap login successfully to the FTP server on port 21? (Y/N)N
Thank you for reading through my article. You can leave any questions or comments on how I can improve my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.