Demystifying the OSI Model: A Layer-by-Layer Guide to Network Communication
 Ruchir Dixit
Ruchir DixitTable of contents
- Overview
- Why bother about learning OSI model?
- Why we need a communication model at all?
- Layer 7 : Application Layer
- Layer 6 : Presentation Layer
- Layer 5 : Session Layer
- Examples:
- Layer 4 : Transport Layer
- Layer 3 : Network Layer
- Layer 2 : Data Link Layer
- Layer 1 : Physical Layer
- Understanding the flow
- OSI Model vs. TCP/IP Model
- Conclusion
Overview
The OSI Model (Open Systems Interconnection) is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer serves a specific purpose, enabling various devices and applications to communicate over a network. By breaking down network communication into these layers, the OSI model simplifies complex interactions, making it easier to design, troubleshoot, and understand networking systems.
Why bother about learning OSI model?
In most of the cases, we just memorized the 7 layers of OSI model just for the sake of clearing the networking paper in our university and didn’t really bother to deep dive into what actually happens inside these layers. I did the same but just recently I was taking a fundamentals of networking for backend course by Hussein Nasser and was amazed at how important it is to understand how each layer is responsible for handling a different aspect of data transmission, starting from the physical transmission of signals to user-facing applications, and as a software engineer building backend systems, to make sure nothing after the request gets send is a black box to me!
Why we need a communication model at all?
Well without a standard model which is accepted worldwide, our applications would need to have knowledge of underlying network medium (that is the medium from/to which our request is coming from/going to). Just imagine, if you had to make different versions of your application so that it works on Wi-Fi, different version of your app to work on Ethernet, different version to work on LTE, different version to work on Fiber, etc. and two applications will not be able to understand each other if request is coming from two different mediums. That would be a disaster, right? But we don’t face this issue because we built a standard system that is used globally.
Ok, let’s start with the 7 layers…..
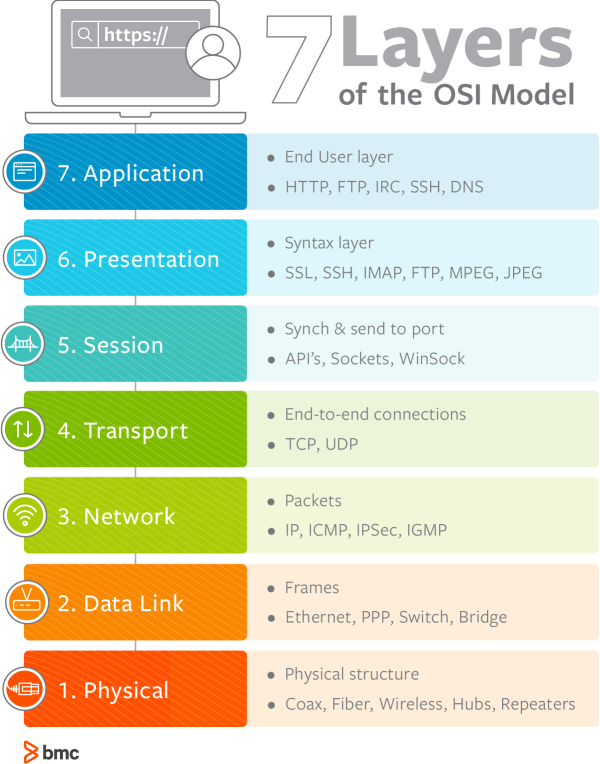
Image credits : BMC Software
Layer 7 : Application Layer
The Application Layer is the topmost layer of the OSI model, closest to the end user. It is responsible for providing network services directly to applications that require network communication. Unlike the other layers, which handle the technical details of data transmission, the application layer interfaces with software applications, enabling them to communicate over a network. It facilitates user interaction by providing services such as file transfers, email communication, and web browsing.
Examples:
Web browsers (HTTP/HTTPS): Applications like Chrome, Firefox, or Safari use HTTP/HTTPS to retrieve and display web pages from a server.
Email clients (SMTP/IMAP/POP3): Applications like Outlook or Gmail use protocols like SMTP (Simple Mail Transfer Protocol) to send emails and IMAP/POP3 for receiving them.
File transfer applications (FTP): Software like FileZilla that enables users to upload or download files from remote servers using FTP.
The application layer is the layer through which users interact with the network via applications, and it relies on other layers beneath it to deliver data reliably.
Layer 6 : Presentation Layer
The Presentation Layer acts as the translator between the network and the application layer. It formats and translates the data to ensure it is in a readable format for the application. It handles the encoding and decoding of data and manages data encryption and compression, ensuring secure and efficient transmission.
Examples:
SSL (Secure Socket Layer): Encrypts data for secure communication, like in HTTPS.
JPEG: Converts image files for efficient storage and transmission.
The Presentation Layer ensures data is formatted correctly, secure, and compressed for efficient transmission.
Layer 5 : Session Layer
The Session Layer is responsible for establishing, managing, and terminating connections between applications on different devices. It ensures that data is properly synchronized and organized during a communication session.
Some of the key concepts in this layer include:
Session Establishment:
- The Session Layer sets up a communication session between two devices or applications. This process involves negotiating parameters and ensuring that both parties are ready to exchange data.
Session Maintenance:
- Once a session is established, the Session Layer manages it to ensure that data is transmitted correctly and efficiently. It handles the flow of data, manages dialogues (e.g., half-duplex or full-duplex), and can manage the data exchange process to prevent issues such as data loss or duplication.
Session Termination:
- At the end of a communication session, the Session Layer is responsible for gracefully terminating the connection. This involves closing the session and ensuring that all data is properly handled and any resources are released.
Examples:
APIs (Application Programming Interfaces):
- APIs often rely on session management to maintain the state and context of interactions between applications. For instance, a web service might use session tokens to keep track of user interactions during a session.
Sockets:
- Sockets, which are endpoints for communication between devices, operate at the Session Layer to establish, maintain, and terminate connections. They provide a way for applications to send and receive data over a network.
The Session Layer ensures that communication sessions between applications are properly managed, providing a stable and reliable environment for data exchange.
Layer 4 : Transport Layer
The Transport Layer is responsible for ensuring the reliable transfer of data between devices. It manages error recovery, data flow control, and the segmentation of data into manageable units, ensuring that data sent from one application is correctly received by the other application. In this layer we deal with ports like 8080.
Protocols under this layer:
TCP (Transmission Control Protocol):
Characteristics: TCP is a connection-oriented protocol that ensures reliable and ordered delivery of data. It establishes a connection between sender and receiver before data transfer begins and manages the data transfer with error checking, acknowledgments, and flow control.
Features: Reliable, connection-oriented, provides error recovery, guarantees delivery, and manages data sequencing.
UDP (User Datagram Protocol):
Characteristics: UDP is a connectionless protocol that sends data without establishing a connection or guaranteeing delivery. It is used in scenarios where speed is more critical than reliability, and applications can handle error checking and correction on their own.
Features: Fast, connectionless, no error recovery, no guarantee of delivery, suitable for real-time applications like streaming and gaming.
Examples:
TCP: Used by applications where data integrity and order are critical, such as web browsing (HTTP/HTTPS), email (SMTP/IMAP/POP3), and file transfers (FTP).
UDP: Used by applications where speed is more important than reliability, such as video streaming (e.g., streaming services), online gaming, and VoIP (Voice over IP).
The Transport Layer plays a vital role in ensuring that data is transmitted reliably and efficiently between devices, providing necessary mechanisms for error recovery and flow control
Layer 3 : Network Layer
The Network Layer is responsible for routing data between devices across different networks. It manages logical addressing and determines the best path for data to travel from the source to the destination through various interconnected networks. In this layer we don’t know what ports are, we only know IP addresses.
Examples:
IP (Internet Protocol):
Description: A fundamental protocol used for addressing and routing data on the internet and other IP-based networks. IP defines the format of packets and the addressing scheme used to identify devices.
Versions:
IPv4: Uses 32-bit addresses, allowing for about 4.3 billion unique addresses.
IPv6: Uses 128-bit addresses, providing a vastly larger address space to accommodate the growing number of devices on the internet.
ICMP (Internet Control Message Protocol):
Description: A protocol used for network diagnostics and error reporting. ICMP helps in managing and controlling network operations by sending control messages.
Functions: Includes sending error messages (e.g., destination unreachable) and operational information (e.g., ping requests to test connectivity).
The Network Layer plays a crucial role in enabling data to be routed across different networks, providing logical addressing, and managing the path that data packets take from source to destination.
Layer 2 : Data Link Layer
The Data Link Layer is responsible for reliable node-to-node data transfer and error correction. It ensures data is properly packaged into frames and transmitted across a physical network. This layer also manages access to the physical medium and ensures that data arrives without errors.
A few key concepts in this layer :
MAC Addresses: Unique hardware addresses used to identify devices on the same network.
Switches: Devices that forward data based on MAC addresses.
Frames: Data packets at the Data Link Layer, containing headers, payload, and error detection.
Examples:
Ethernet: A protocol that defines how devices on a local network communicate.
PPP (Point-to-Point Protocol): A protocol used to establish a direct connection between two nodes, commonly used in internet connections.
The Data Link Layer ensures error-free, reliable transmission of data between directly connected devices on the same network.
Layer 1 : Physical Layer
The Physical Layer is the lowest layer of the OSI model and is responsible for the actual physical connection between devices. It handles the transmission of raw bits (binary data) over a communication medium, such as a cable or wireless signal. The physical layer ensures that data is transmitted as electrical, optical, or radio signals, depending on the transmission medium, without interpreting the content of the data.
A few key concepts in this layer :
Cables: Different types of cables such as copper (Ethernet) or fiber optic cables, which physically transmit data.
Network Adapters: Devices like NICs (Network Interface Cards) that interface with the physical medium.
Switches and Hubs: Devices that operate at the physical layer to forward electrical signals between devices.
Connectors: Plugs, jacks, and other hardware that connects devices to the network infrastructure.
Transmission Media: The medium through which the signals are transmitted, such as air (for wireless), copper wires, or optical fibers.
Examples:
Ethernet cables: Used to connect devices in a local area network (LAN), transmitting data in the form of electrical signals.
Fiber optic cables: Transmit data as light pulses, providing faster transmission speeds over longer distances.
Radio signals: Used for wireless communication, such as Wi-Fi, which transmits data using radio waves.
The physical layer is the foundation of network communication, providing the means for transmitting raw data across physical media, but it does not deal with the content of the data, only the method by which it is transmitted.
Understanding the flow
Alright…so now we know what each layer is responsible for, lets see what each layer does when an user sends an HTTPS POST request.
Sender’s flow :
First comes the Application Layer, which takes this POST request with JSON request body and sends it to HTTPS server.
Then comes the Presentation Layer, it takes your JSON and serializes it into flat byte strings because the network does not understand what JSON is, that is just what we use in our programming languages to be something that a human can read!
Next, the Session Layer, then checks if we need to establish a TCP connection?, do we need to establish TLS?
Then the Transport Layer, is the layer when we actual send a SYN request on basis of session layer to port 443 (because we are sending HTTPS request) and because this layer understands the ports. Remember, we have not yet sent the JSON data which we converted to bytes yet. Unless you establish a connection and receive a connection request to authenticate data does not get sent ahead!
Next, in the Network Layer, this SYN request is placed in an IP packet and adds the Source and Destination’s IP address in this packet. If you don’t know the IP address, then we have to do DNS to get the IP address.
In Data Link Layer, each packet goes into single frame and adds the Source and Destination’s MAC address to it.
At last in the Physical Layer, each frame from the data link layer becomes string of bits (i.e. converted to binary) which are then converted into radio signals (Wi-Fi), or electric signals (Ethernet), etc.
Receiver’s flow :
Now that we understood how the request gets send, we will see what happens at receivers end when it received this signals!
As we have a signal at receivers end, obviously we start with the Physical Layer! This layer now converts the radio signal, or electric signal into digital bits.
In Data Link Layer, all the bits from layer 1 (Physical layer) are assembled into frames.
Then in Network Layer, the frames from layer 2 (Data Link layer) are assembled into IP packets. As we have Destination IP in this packet, receiver checks if this request is intended for, if yes, it moves ahead.
The IP packets from layer 3 (Network layer) are assembled into TCP segments and deals with congestion control/flow control in case of TCP. If the request is just a SYN request (i.e. just looking to establish connection) it wont go any further into more layers as we are still processing the connection request!!
If otherwise, the go to Session layer to establish a connection.
Once we have a connection, in next request we will have our JSON data which in the Presentation layer, we will de-serialize the flat byte strings back to JSON for the application to consume. This de-serialization can be completely different from the way we serialized, like we would have serialized the JSON using Javascript but can de-serialize into Java.
At last, at the application layer, the application understands this JSON POST request and your Apache request event is triggers and does what it needs to do!
There is another popular model which is similar to OSI model that is TCP/IP Model.
OSI Model vs. TCP/IP Model
Comparison:
The OSI model has 7 layers, while the TCP/IP model has 4 layers (Application, Transport, Internet, and Network Access). Both models are designed to facilitate communication over a network, but the OSI model is more theoretical, serving as a general reference framework, whereas the TCP/IP model is practical and directly tied to the protocols used on the internet. In the TCP/IP model, certain OSI layers are combined (e.g., the OSI Application, Presentation, and Session layers are merged into the TCP/IP Application layer).
Why TCP/IP is Used More:
The TCP/IP model is more widely used because it was developed specifically for the internet and real-world networking. It is simpler and more adaptable to modern protocols, making it more practical for today's interconnected world. Additionally, the internet itself is built on TCP/IP, making it the de facto standard.
Conclusion
The OSI model breaks down the complex process of network communication into seven distinct layers, each with a specific role. From the Physical Layer managing raw data transmission, up to the Application Layer interacting with end-users, every layer contributes to ensuring reliable, organized, and secure data exchange across networks. Each layer’s functions are crucial for maintaining smooth communication between devices.
Final Thoughts:
Though modern networks often use the TCP/IP model, the OSI model remains highly relevant in understanding network protocols and structures. It offers a clear, modular approach to learning how different aspects of networking fit together, making it an essential tool for students and professionals alike.
Hopefully, you have got a better idea about OSI model and how it functions. And hopefully you now give this global standard the respect it deserved 😀
Please let me know in the comments if you enjoyed reading this article and learned something new. Also feedback if any is appreciated!
Subscribe to my newsletter to get notified about more such articles.
Follow me :
X (formerly twitter) : Ruchir Dixit
LinkedIn : Ruchir Dixit
Subscribe to my newsletter
Read articles from Ruchir Dixit directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ruchir Dixit
Ruchir Dixit
Hey 👋, Ruchir Dixit here! I am currently a Java backend developer at eQ Technologic, Pune, a product based company. I love learning new technologies and building projects while learning. About my Non tech side, I love travelling and trekking. An avid motorcycle enthusiast and Basketball sports player/fan. Lets Connect on LinkedIn, Instagram or GitHub to grow together.