Ransomware Resilience: DevSecOps Strategies for Preventing and Recovering from Cyber Extortion
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
Introduction: The Ransomware Threat
Ransomware attacks have evolved into one of the most significant threats to digital infrastructures worldwide. With high-profile incidents such as the Colonial Pipeline hack, the devastating consequences of ransomware have been made clear crippling operations, disrupting services, and leading to substantial financial and reputational damage.
In this post, we will explore how DevSecOps can help organizations build ransomware resilience. We’ll look at strategies such as automating incident response protocols, implementing immutable backups, and leveraging AI-powered ransomware detection within CI/CD pipelines to proactively prevent and mitigate ransomware attacks.
Understanding the Colonial Pipeline Incident
The Colonial Pipeline ransomware attack in 2021 was a wake-up call. The company’s fuel pipeline was brought to a standstill, causing fuel shortages across the U.S. eastern seaboard. The attack was carried out by the DarkSide group, demanding a ransom in cryptocurrency to restore operations. Despite the hefty ransom payment, the recovery was slow due to a lack of proper backup and incident response mechanisms, highlighting the critical need for more robust ransomware defense and recovery strategies.
Key DevSecOps Strategies for Ransomware Resilience
1. Automated Incident Response Protocols
Automated incident response can help limit the damage caused by a ransomware attack. By detecting ransomware activity early, your system can isolate infected nodes, revoke access privileges, and alert relevant stakeholders without manual intervention.
2. Immutable Backups
Having immutable backups means your data is safe from encryption or deletion by ransomware. These backups are stored in write-once-read-many (WORM) format, ensuring they cannot be altered once written. By incorporating automated backup systems into your CI/CD pipeline, you can create robust recovery points.
3. AI-Powered Ransomware Detection
Machine learning and AI models can spot suspicious behavior in your infrastructure, such as unauthorized file modifications, encryption patterns, and unusual network traffic. By integrating these models into your DevSecOps pipeline, you can enable real-time ransomware detection and response.
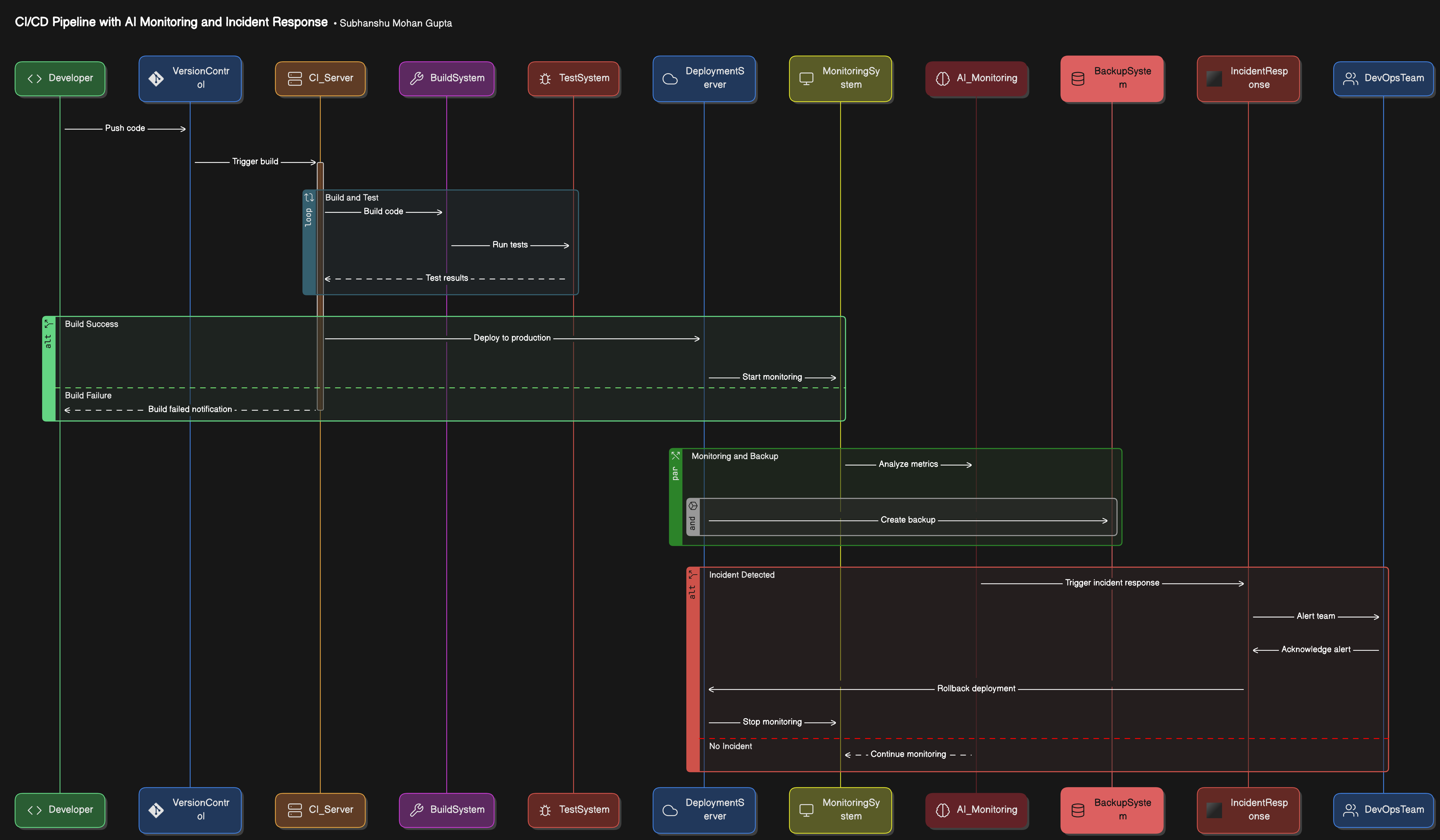
Architecting Ransomware Resilience in a DevSecOps Pipeline
In this architecture, we integrate automated incident response, immutable backups, and AI-powered ransomware detection directly into the CI/CD pipeline to ensure early detection and rapid recovery.
Architecture Overview:
CI/CD Pipeline with Integrated Security
Includes automated incident response triggers.
Ensures immutable backups at key stages.
Uses AI models to detect ransomware in real time.
Ransomware Detection Layer
AI-powered anomaly detection tools (like ElastAlert).
Monitors file system changes, encryption activity, and network behavior.
Immutable Backup Storage
- Leverages tools such as Amazon S3 Object Lock or Google Cloud Storage with versioning enabled to store immutable backups.
Automated Incident Response
- Uses Ansible or AWS Lambda for automated responses (isolation, alerting, and logging).
Testing Framework
- Caldera by MITRE for simulating ransomware attacks and validating the resilience of the pipeline.
Architecture Diagram
Step-by-Step Implementation Guide
Let's break down how you can implement this solution step by step, including the necessary code to integrate into your DevSecOps workflow.
1. Automated Incident Response Setup
By automating incident response, you ensure that when ransomware activity is detected, immediate action is taken. Here, we’ll use Ansible to automate container isolation and response.
Ansible Playbook for Automated Incident Response:
---
- hosts: all
become: true
tasks:
- name: Detect ransomware activity
shell: |
if [[ $(detect_ransomware_activity) ]]; then
echo "Ransomware detected, isolating container"
fi
- name: Isolate affected container
command: docker network disconnect my_app_network my_app_container
when: ransomware_detected
In the above playbook:
detect_ransomware_activity: This shell command detects ransomware behavior (you can integrate it with monitoring tools like Falco or a custom script).docker network disconnect: Automatically isolates the affected container from the network.
2. Implementing Immutable Backups
Immutable backups ensure that your critical data is safe from ransomware attacks. Using AWS S3 Object Lock or Google Cloud Storage with versioning provides robust, immutable backups. Below is a setup example for AWS S3.
AWS S3 Immutable Backup Setup:
# Enable S3 Object Lock on an existing bucket
aws s3api put-object-lock-configuration --bucket my-secure-bucket \
--object-lock-configuration '{
"ObjectLockEnabled": "Enabled",
"Rule": {
"DefaultRetention": {
"Mode": "COMPLIANCE",
"Days": 90
}
}
}'
This script ensures that backups saved in the my-secure-bucket are immutable for 90 days. You can automate this process by adding it as a post-deployment step in your CI/CD pipeline.
3. AI-Powered Ransomware Detection with ElastAlert
Using AI-powered monitoring tools like ElastAlert, you can build detection rules that look for abnormal file modifications or encryption behavior. Here’s how to set up a detection rule.
ElastAlert Rule for Detecting Suspicious File Activity:
# elastalert-rule.yaml
name: Detect Ransomware File Modifications
type: frequency
index: filebeat-logs-*
num_events: 10
timeframe: minutes: 5
filter:
- term:
event.action: "file_encryption"
alert:
- "email"
- "slack"
In this rule:
We’re tracking file encryption activity using logs captured by Filebeat.
The system alerts the security team via email and Slack if more than 10 encryption events occur within 5 minutes, suggesting possible ransomware activity.
4. Full Testing Using MITRE Caldera
To test the robustness of your DevSecOps pipeline, simulate ransomware attacks using MITRE Caldera. This allows you to ensure your automated responses and monitoring tools work as expected.
Simulating Ransomware Attack:
# Run Caldera to simulate a ransomware attack
python3 caldera.py --attack "simulate_ransomware"
After running this simulation, check your logs, alerts, and incident response triggers to validate that your pipeline is resilient against ransomware.
Real-World Scenario: End-to-End Recovery Workflow
Consider a scenario where a CI/CD pipeline is used to deploy an e-commerce application. During deployment, the system detects unusual file encryption activity. The automated response kicks in, isolating the affected container and notifying the DevSecOps team. Immutable backups stored on AWS S3 ensure that the most recent data is untouched, allowing for a rapid recovery without paying a ransom.
Key Outcomes:
Early detection through AI-powered monitoring ensures rapid containment of ransomware.
Immutable backups prevent data loss and allow for a smooth recovery.
Automated incident response ensures minimal downtime and operational impact.
Conclusion: The Power of DevSecOps in Ransomware Resilience
Building ransomware resilience into your DevSecOps pipeline is critical to safeguarding against modern cyber extortion attacks. Through the integration of automated incident response, immutable backups, and AI-powered ransomware detection, organizations can not only prevent ransomware but also ensure fast recovery.
The combination of automation, AI, and backup immutability enhances the security of your entire CI/CD lifecycle, fostering a proactive approach to cybersecurity. As ransomware continues to evolve, so must your strategies to detect, isolate, and recover.
Next Steps:
Start integrating immutable backups into your pipeline with AWS S3 Object Lock or Google Cloud Storage.
Use tools like ElastAlert to monitor your file systems for ransomware-like behavior.
Regularly test your incident response with tools like MITRE Caldera to ensure your defenses are ready for a real-world attack.
By following these strategies and incorporating the provided code examples, you’ll be well on your way to building a ransomware-resilient DevSecOps pipeline.
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.