Using Dive to analyze Docker Images
 Chukwudi Wowo
Chukwudi Wowo
This lab focuses on the review of docker images for extra or unneeded files to reduce attack surface using Dive. Dive is a layer-aware tool for exploring docker images, layer contents, and discovering ways to shrink the size of your Docker/OCI image.
(This lab is my solution to the part 1 of the container security course final project on INFOSEC Institue)
Lab Objective:
The challenge of this lab as was to:
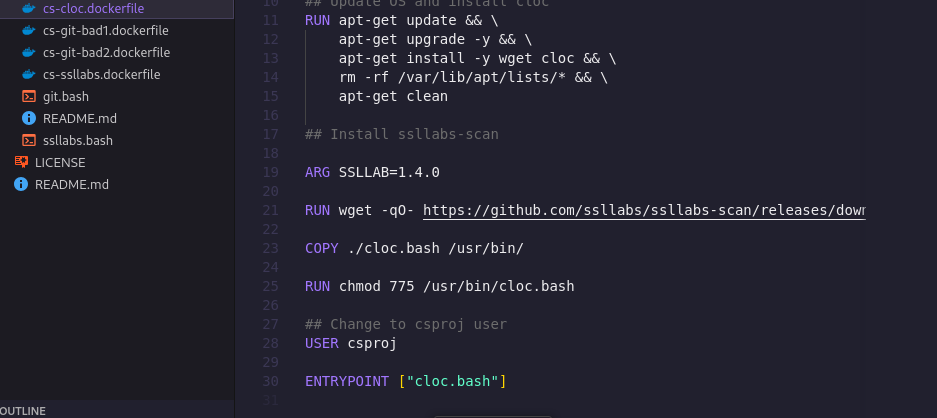
Review cs-cloc:latest to get the last file that was added
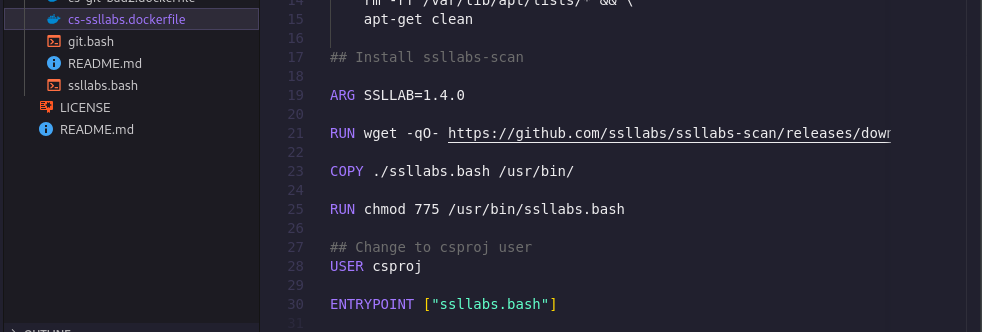
Review cs-ssllabs to get the last file that was modified
What I did:
Step 1: I pulled the images to be reviewed from docker.
Step 2: I installed the dive command line tool and verified the installation with dive --version command. Then, I took a dive into the images with command:
dive <image:tag>
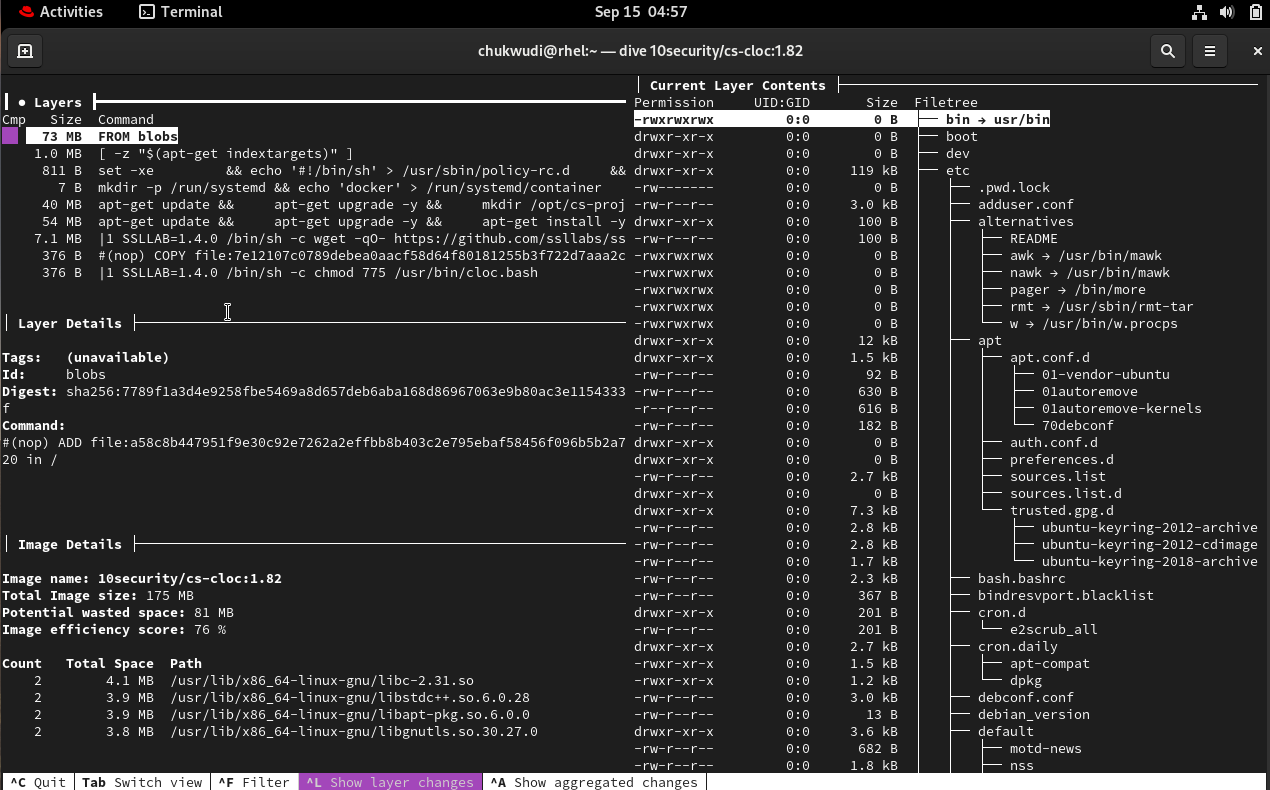
#Troubleshoot:
Using the dive <image:tag> command at first resulted in an error where the image config file wasn't found because dive was failing to fetch the local images. I debugged and solved this by upgrading from V0.9 to V0.12 (see here)
Step 3: Upon careful investigation of the images using available commands and filters available in Dive, I found the answers to the challenge to be cloc.bash and ssllabs.bash respectively.
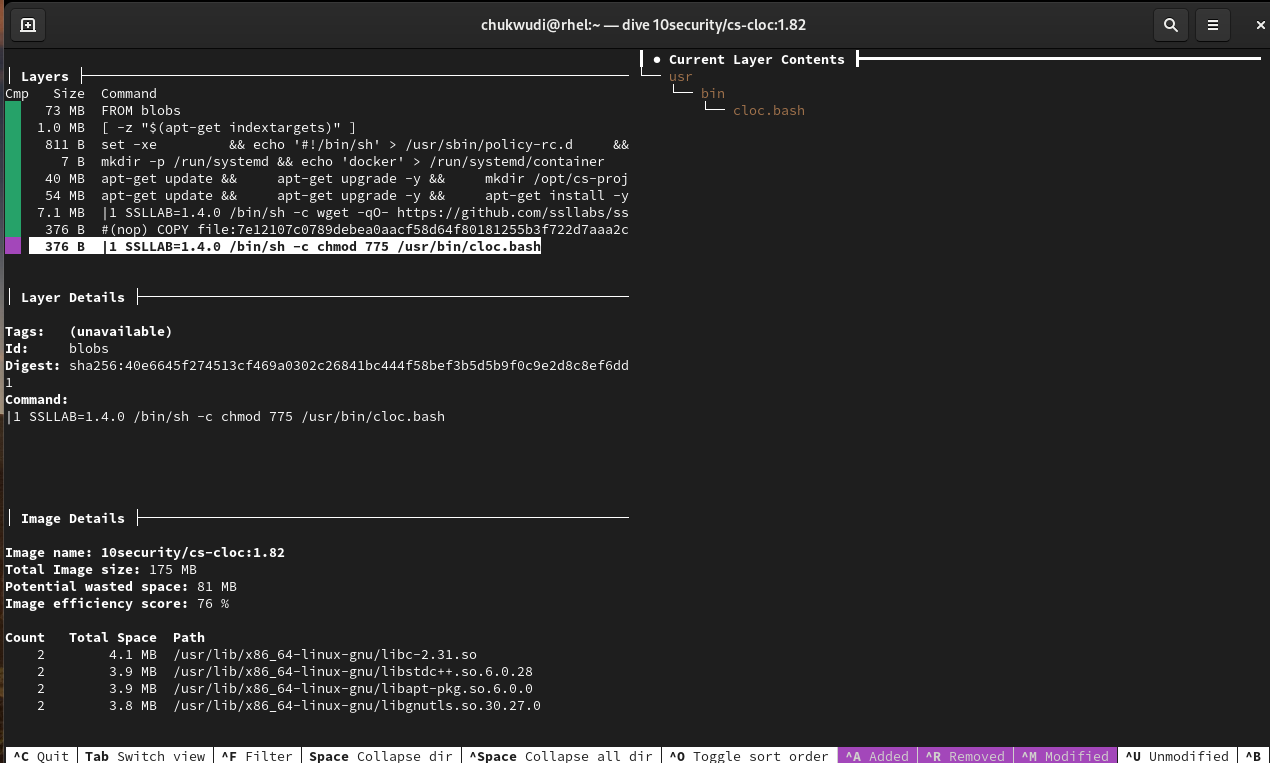
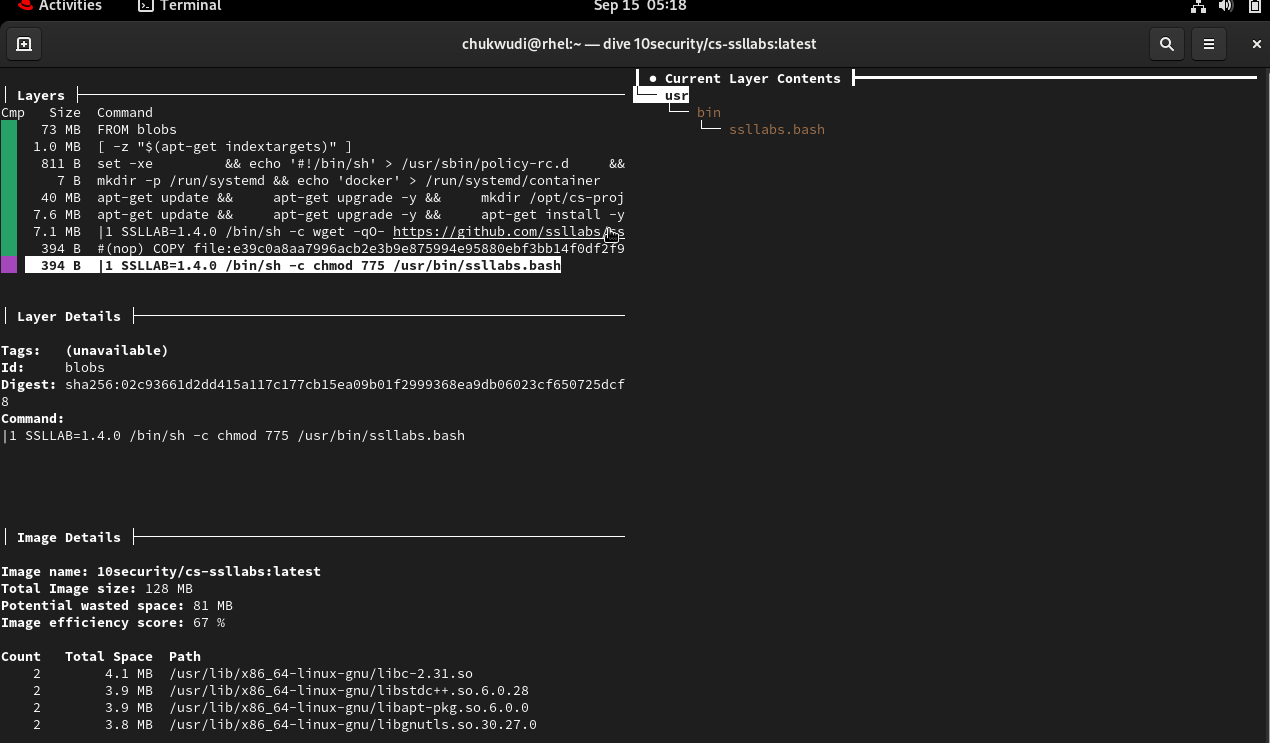
Step 4: I verified my answers by looking at the dockerfile of each image because docker files are the templates used to build images and it does so by building the images' layers in a chronological pattern where the first command/instruction of the template is the first image layer so I was able to verify my answers by looking at the last set of commands in the dockerfile.
Subscribe to my newsletter
Read articles from Chukwudi Wowo directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
