DevSecOps: Integrating Security in DevOps
 Deepak parashar
Deepak parashar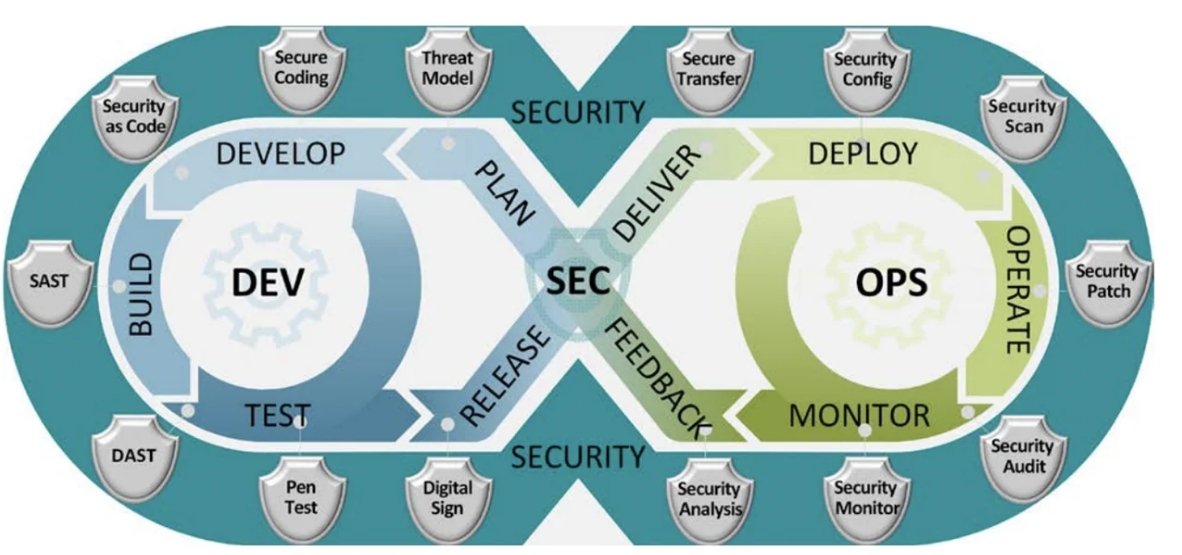
In today’s fast-paced software development world, security cannot be an afterthought. Enter DevSecOps, the practice of integrating security into every phase of the DevOps pipeline. It shifts security left, ensuring that vulnerabilities are caught early in development rather than after a breach has occurred. This blog post will take you through the core concepts of DevSecOps and how to implement it effectively.
If you’re a software engineer or a tech enthusiast looking to bring security and agility together in your workflow, this guide is for you. We'll walk through the steps to build a secure CI/CD pipeline and incorporate key security practices that blend seamlessly with your development and operations processes.
Step 1: Understanding DevSecOps
Before diving into the "how-to," let's first define DevSecOps and why it’s critical in modern software development.
DevSecOps is the integration of security practices into the DevOps process.
The goal is to build security into every part of the pipeline—development, testing, deployment—ensuring that security is no longer a bottleneck but a streamlined part of the lifecycle.
Why DevSecOps?
Shifts Security Left: Traditional security practices test applications once they’re built. DevSecOps pushes security testing earlier, right into the development process.
Automation: Like DevOps, DevSecOps thrives on automation. Automated tools scan for vulnerabilities and security misconfigurations, ensuring developers catch issues before they’re deployed.
Suggested Visual: Create an illustration of the DevSecOps lifecycle showing "Dev," "Ops," and "Security" as an integrated loop, rather than separate entities.
Step 2: Building a Secure CI/CD Pipeline
A secure CI/CD pipeline is at the core of DevSecOps. Let’s break down the process:
2.1 Configuring the CI/CD Pipeline
Your pipeline should include stages like build, test, scan, and deploy. Security should be present at every stage, starting from code quality checks to post-deployment monitoring.
Build Stage:
- In this stage, ensure that you're using secure dependencies by integrating tools like OWASP Dependency-Check or Snyk. These tools scan your libraries and dependencies for vulnerabilities.
Test Stage:
- Automated testing should cover security vulnerabilities alongside functional and unit tests. Integrate security testing tools like ZAP or OWASP Juice Shop to identify common vulnerabilities such as SQL Injection and XSS.
Scan Stage:
- After testing, scan your application and container images for vulnerabilities. Use tools like Clair for container security or Trivy to scan for vulnerable dependencies.
Deploy Stage:
- Ensure that your infrastructure as code (IaC) tools (like Terraform or Ansible) follow security best practices. Use InSpec to enforce compliance, and configure secret management tools (like Vault) to securely handle sensitive information.
Suggested Visual: A flowchart of a secure CI/CD pipeline showing the four stages (Build, Test, Scan, Deploy), with icons representing key security tools at each stage.
Step 3: Security Automation Tools for DevSecOps
One of the core principles of DevSecOps is automation. By automating security tests and scans, teams can move faster without compromising security.
3.1 Static Application Security Testing (SAST)
SAST tools analyze your code for vulnerabilities during the development process. They help catch vulnerabilities early, before your code is compiled or deployed.
Tools: SonarQube, Veracode
What it does: SAST scans your source code for patterns that may indicate security flaws, like insecure code or unvalidated input.
How to Use:
- Add SAST tools to your CI pipeline as part of the build or testing stage. Once integrated, it automatically scans your codebase on every commit.
Suggested Visual: Create a diagram showing the SAST process, with the tool analyzing code during the development phase before deployment.
3.2 Dynamic Application Security Testing (DAST)
Unlike SAST, which analyzes code, DAST tools test a running application for vulnerabilities by simulating attacks.
Tools: OWASP ZAP, Burp Suite
What it does: DAST interacts with your application in a live environment, testing for vulnerabilities like SQL Injection, Cross-Site Scripting (XSS), and more.
How to Use:
- DAST tools should be integrated into your staging or pre-production environment. They scan your application as it would be seen by a potential attacker.
Suggested Visual: Show a DAST tool interacting with a deployed application, testing for various vulnerabilities post-deployment.
3.3 Container Security
With the rise of containerization, ensuring the security of your Docker containers and Kubernetes environments is essential.
Tools: Aqua Security, Twistlock
What it does: These tools monitor your container images for vulnerabilities, misconfigurations, and enforce compliance rules.
How to Use:
- Integrate container security scanning tools into your build pipeline to automatically scan Docker images before they are deployed.
Suggested Visual: A tree diagram illustrating container security with nodes for image scanning, vulnerability detection, and compliance monitoring.
Step 4: Integrating Monitoring & Incident Response
Once your application is deployed, security monitoring and incident response should be a key part of your DevSecOps pipeline.
4.1 Security Monitoring
Real-time monitoring tools give you visibility into your system’s security state.
Tools: Prometheus, Datadog, AWS CloudWatch
What it does: These tools track system metrics like CPU usage, memory, and network traffic, which can help detect potential breaches.
How to Use:
- Set up alerts and dashboards to monitor key security metrics like unauthorized access attempts, abnormal spikes in traffic, or resource exhaustion.
Suggested Visual: A monitoring dashboard with real-time metrics, highlighting potential anomalies in network traffic or access attempts.
4.2 Incident Response
If a security incident occurs, you need a clear response plan in place. DevSecOps emphasizes automation here as well.
Tools: PagerDuty, Splunk
What it does: Incident response tools trigger automated alerts when a potential breach or vulnerability is detected.
How to Use:
- Integrate incident response tools with your monitoring system. Automatically trigger an alert to the security team if a potential issue is detected.
Suggested Visual: A workflow diagram showing an alert system where a detected security issue triggers an automatic alert to the incident response team.
Step 5: DevSecOps Best Practices
To implement DevSecOps effectively, follow these best practices:
Collaborate Early & Often:
- Involve security teams from the start of your project, ensuring that security isn't an afterthought.
Automate Everything:
- Wherever possible, automate security checks and vulnerability scanning. This ensures consistency and frees up developers to focus on building features.
Train Your Team:
- DevSecOps is a mindset. Ensure your team is trained not only in development and operations but also in security best practices.
Monitor Continuously:
- Continuous monitoring ensures that security vulnerabilities are detected and addressed as soon as they appear in production.
Suggested Visual: A best practices checklist with each item highlighted for emphasis.
Conclusion
Incorporating security into the DevOps pipeline is no longer optional—it's essential. DevSecOps ensures that security becomes a shared responsibility across development, operations, and security teams, fostering a culture of collaboration and automation. By following the steps outlined in this guide, you can build a robust DevSecOps pipeline that catches vulnerabilities early, automates security tasks, and ensures your applications are both fast and secure.
What challenges have you faced while implementing security in your development process? Leave a comment below—let’s discuss!
Meta Description:
Learn how to implement DevSecOps in your CI/CD pipeline. This guide covers automation tools, secure pipelines, monitoring, incident response, and best practices for integrating security into DevOps.
Subscribe to my newsletter
Read articles from Deepak parashar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
