Linux - Firewall Management
 Dinesh Kumar K
Dinesh Kumar K
Firewalls are crucial for maintaining the security of a Linux system. They act as barriers that filter incoming and outgoing network traffic based on predefined security rules. In Linux, there are several tools available to manage firewall rules, including ufw, firewalld, and iptables.
What is a Firewall?
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between trusted internal networks and untrusted external networks, such as the internet.
Firewalls are essential for:
Protecting against unauthorized access.
Preventing malicious attacks.
Controlling traffic flow based on security policies.
Comparative Summary
| Feature | ufw | firewalld | iptables |
| Overview | Simplified firewall management | Dynamic firewall management with zones and services | Advanced, detailed firewall control |
| Primary Use Case | Basic firewall management for beginners | Dynamic rule management, flexible and adaptable | Granular control over firewall rules |
| Ease of Use | Very user-friendly | Moderate; requires understanding of zones and services | Complex; steep learning curve |
| Installation | Pre-installed on Ubuntu; easy to install on other distros | Available on CentOS, Fedora, RHEL; easy to install | Usually pre-installed; manual configuration needed |
| Configuration | Simple command-line interface | Command-line and graphical tools available | Command-line only; detailed syntax |
| Rule Management | Simple rules (allow/deny services) | Zones and services with dynamic updates | Detailed rules and chains; requires knowledge of iptables syntax |
| Commands | ufw enable, ufw allow, ufw deny | firewall-cmd --add-service, firewall-cmd --zone | iptables -A INPUT -p tcp --dport 22 -j ACCEPT |
| Logging | Basic logging capabilities | More advanced logging options available | Detailed logging, but requires manual configuration |
| Dynamic Updates | Static; requires manual updates | Dynamic; supports runtime changes without reload | Static; changes require reloading rules |
| Zones Support | No zones | Supports zones for different network interfaces | No zone concept |
| Persistence | Configuration saved in /etc/ufw | Configuration saved in /etc/firewalld | Configuration typically managed with scripts |
| Default Policy | Deny all incoming, allow outgoing | Configurable; default is usually to allow all incoming unless specified otherwise | Requires manual setup; default is to allow all if not specified |
1. ufw (Uncomplicated Firewall)
ufw is designed to simplify firewall configuration. It’s commonly used on Debian-based distributions like Ubuntu and provides an easy-to-use command-line interface.
Key Features:
Ease of Use: Simple syntax for configuring firewall rules.
Status Overview: Easy to view current rules and status.
Profiles: Supports application profiles for common services.
Basic Commands:
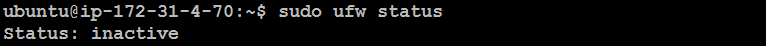
Check Firewall Status:
sudo ufw status
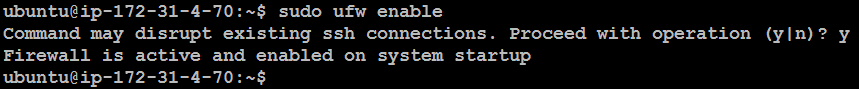
Enable Firewall:
sudo ufw enable
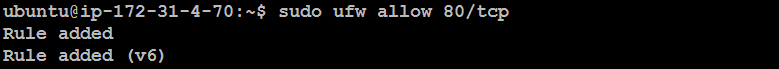
Allow a Port:
sudo ufw allow 80/tcp
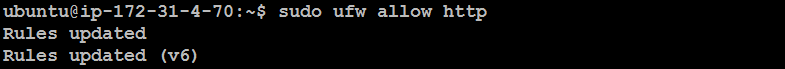
Allow a Service by Name:
sudo ufw allow http
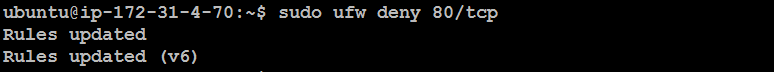
Deny a Port:
sudo ufw deny 80/tcp
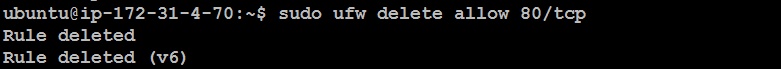
Delete a Rule:
sudo ufw delete allow 80/tcp
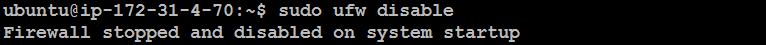
Disable Firewall:
sudo ufw disable
2. firewalld
firewalld is a dynamic firewall management tool that provides an easier way to manage firewall rules compared to iptables. It uses zones and services to simplify configuration.
firewalld is a dynamic firewall management tool available in many Linux distributions, including Fedora, CentOS, and RHEL. It provides a flexible way to manage firewall rules, utilizing zones and services.
Key Features:
Dynamic Configuration: Allows changes to the firewall rules without restarting the firewall service.
Zones: Different zones for different network interfaces, each with its own set of rules.
Rich Language: Supports rich language for complex rule definitions.
Integration: Works well with other tools like
NetworkManager.
Basic Commands:
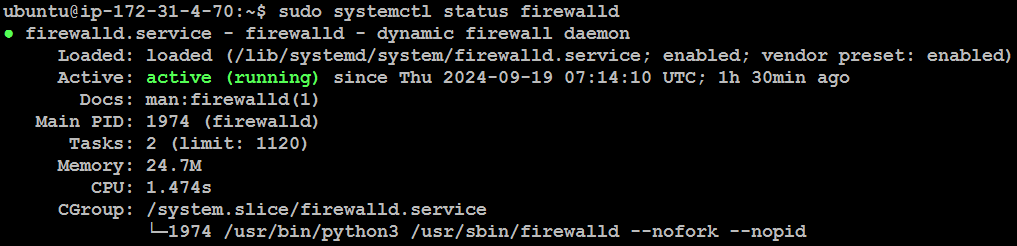
Check the status of the firewalld service to ensure it's running:
sudo systemctl status firewalld
List All Active firewalld Rules
To view the current firewall rules, use the following command:
sudo firewall-cmd --list-all
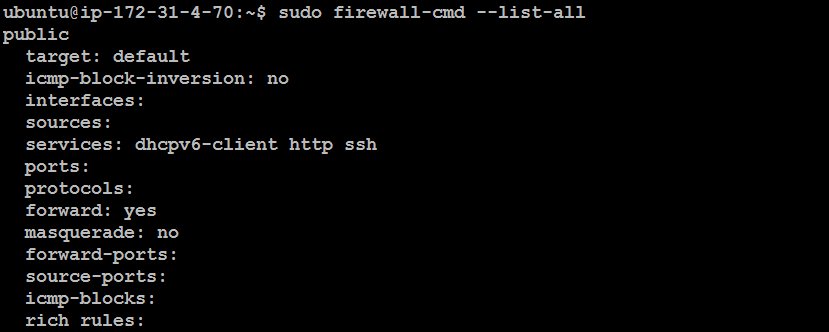
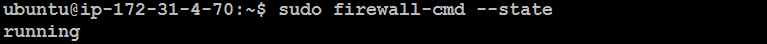
Check Firewall Status:
sudo firewall-cmd --state
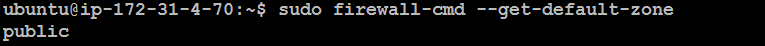
View the default zone:
sudo firewall-cmd --get-default-zone
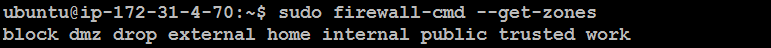
List Available Zones: To see all zones, run:
sudo firewall-cmd --get-zones
List All Active Zones:
sudo firewall-cmd --get-active-zones
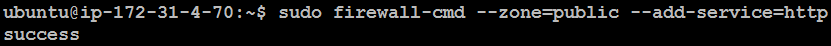
Add a Service to a Zone:
sudo firewall-cmd --zone=public --add-service=http
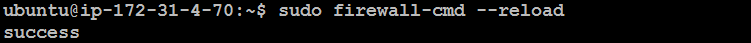
Reload Firewall:
sudo firewall-cmd --reload
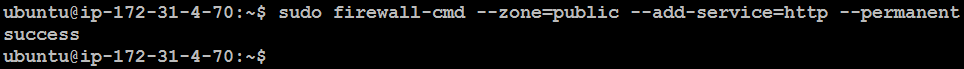
Permanent Changes:
sudo firewall-cmd --zone=public --add-service=http --permanent
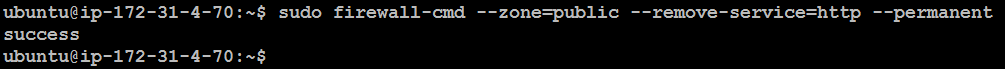
Remove a Service from a Zone:
sudo firewall-cmd --zone=public --remove-service=http --permanent
Adding a Specific Port (e.g., 8080) to the Firewall
To open a specific port like 8080 for TCP traffic in the permanent mode, use this command:
sudo firewall-cmd --permanent --zone=public --add-port=8080/tcp
Once added, reload the firewall to activate the rule:
sudo firewall-cmd --reload
Now, Check the port
sudo firewall-cmd --list-all
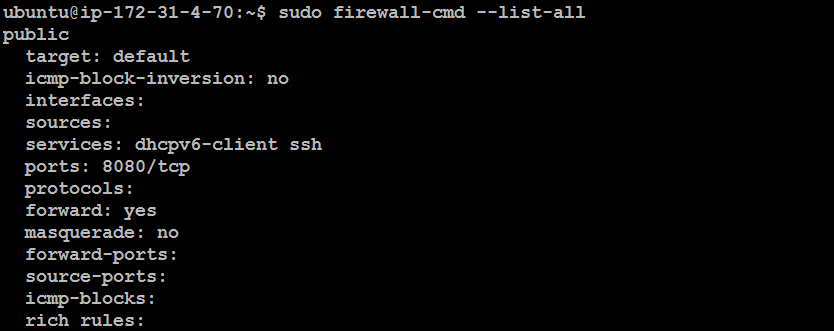
3. iptables
iptables is a traditional Linux firewall tool that provides a robust set of features for managing network traffic. It allows you to set up complex filtering rules, but its syntax can be complex.
Basic Commands:
List Rules:
sudo iptables -L
Allow a Port:
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT
Drop All Incoming Traffic:
sudo iptables -P INPUT DROP
Save Rules:
sudo iptables-save > /etc/iptables/rules.v4
Restore Rules:
sudo iptables-restore < /etc/iptables/rules.v4
Conclusion
Understanding and configuring Linux firewalls is essential for securing your systems. Whether you choose ufw, firewalld, or iptables, each tool has its strengths and use cases. ufw offers simplicity, firewalld provides flexibility, and iptables delivers detailed control. By choosing the right tool for your needs, you can ensure that your Linux system remains secure and well-managed.
Subscribe to my newsletter
Read articles from Dinesh Kumar K directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Dinesh Kumar K
Dinesh Kumar K
Hi there! I'm Dinesh, a passionate Cloud and DevOps enthusiast. I love to dive into the latest new technologies and sharing my journey through blog.