Satoshi Scoop Weekly, 20 Sep 2024
 Cryptape
CryptapeTable of contents
- Crypto Insights
- Pain Points in BTCFi L2/L1 Development? Why Enhance Contracts via Softfork?
- UTXO Stack Announces Transition to Lightning Network Staking Layer
- Exploring a New Fungible Token Protocol Using OP_CAT
- Enabling Native Tokens on Bitcoin via OP_CAT is not Ideal
- Known Attacks on the Nostr protocol
- You Probably Don't Need a Hardware Wallet
- New TMUL Primitive Unlocks More Efficient ZK Verification on Bitcoin
- Introducing Boundless: The Verifiable Compute Layer
- Top Reads on Blockchain and Beyond
Crypto Insights
Pain Points in BTCFi L2/L1 Development? Why Enhance Contracts via Softfork?
Pain points: No consensus on UTXO or the definition of Bitcoin L2s, along with divided opinions on whether changes or softforks are necessary or allowed for Bitcoin.
The moderate progressivism approach: Bitcoin should enhance contract capabilities via softforks to enable features like CSV-like assets and the Lightning Network.
UTXO Stack Announces Transition to Lightning Network Staking Layer
UTXO Stack is transitioning to a staking layer for the Lightning Network, with plans to introduce a token-based incentive mechanism.
This move aims to provide greater liquidity and a more attractive rewards model for the Lightning Network through decentralized staking, where users can stake CKB and BTC to enhance liquidity in state channels.
Exploring a New Fungible Token Protocol Using OP_CAT
One big challenge with protocols like Runes, BRC20 is that token validity depends on the entire prior state of the token (and sometimes on the entire chain). AMMs need the “swap” script to determine token quantities in an input/output.
OP_CAT enables the creation of a token protocol where validity and token amounts can be checked by a reasonably-sized script with a constant (or at least bounded) amount of data.
Enabling Native Tokens on Bitcoin via OP_CAT is not Ideal
OP_CAT-based token protocols are slow for trading, inefficient for maintaining token state, restrictive for writing smart contracts and recursive covenants, and expensive for transactions.
Known Attacks on the Nostr protocol
Ron Stoner is compiling a list of known attacks on the Nostr protocol.
You Probably Don't Need a Hardware Wallet
Some reasons you might consider:
The fiat value of the Bitcoin you're securing may not justify the hardware wallet cost.
DIY entropy generation (with cards, dice, etc.) can be more secure than relying on hardware.
Hardware wallets frequently change, and their software is centralized.
New TMUL Primitive Unlocks More Efficient ZK Verification on Bitcoin
TMUL (Tunable MUL) is an optimized and tunable field multiplication script for Bitcoin protocols that offers the smallest size MUL and the MUL with the least stack usage.
These optimizations reduce the SNARK verifier script used in BitVM by over 1.2 GB.
Introducing Boundless: The Verifiable Compute Layer
Boundless uses a zero-knowledge stack to make verifiable computing efficient and cost-effective across chains. It allows a single node’s execution to be verified cheaply by every other node in the network.
Top Reads on Blockchain and Beyond
Reclaiming the Bitcoin P2P Vision for a Web 5 Future
It explains:
Why is Ethereum’s decentralization seen as “pseudo-decentralization”?
How can PoW and the Programmable UTXO Model empower participation? How can the Lightning Network eliminate intermediaries? How to shift from token-oriented to service-oriented through Bitcoin-native stablecoins, to reclaim the peer-to-peer vision for a Web5 future?
Bitcoin Vaults and the Future of Bitcoin Custody
Bitcoin vaults are offline digital asset storage solutions offering enhanced protection against online threats though:
Cold storage: a security method that keeps Bitcoin offline or away from internet-connected devices
Multisig: when one key is compromised, the Bitcoin in the wallet cannot be transferred
Hardware Security Modules (HSMs): tamper-resistant and hardened devices that secure cryptographic processes
These technologies are critical for securing new Bitcoin financial products.
The 2024 Global Adoption Index
Central & Southern Asia and Oceania Region dominate in crypto adoption in 2024, with seven out of the top twenty countries, including India, Indonesia, Vietnam, the Philippines, Pakistan, Thailand, and Cambodia.
India is the top country, followed by Nigeria and Indonesia.
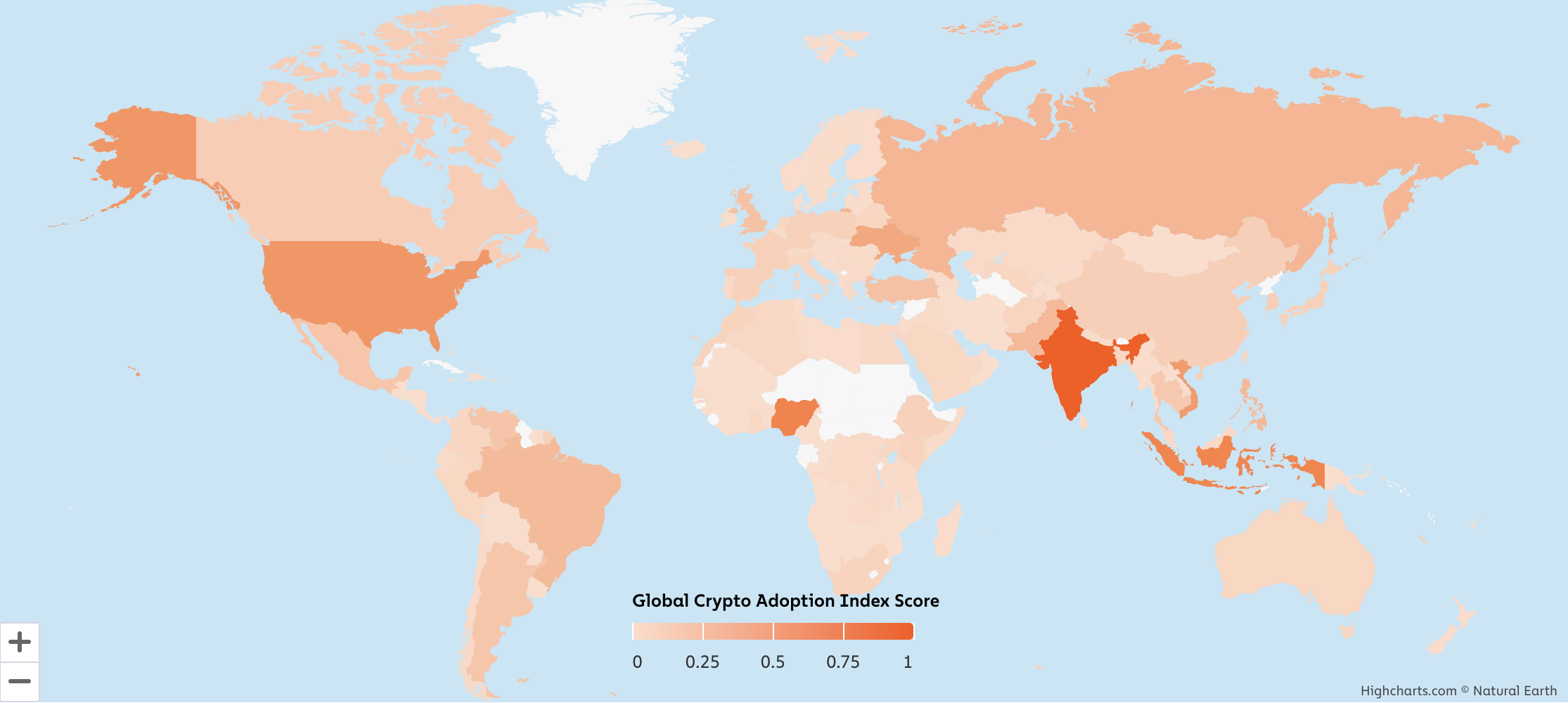
Image via: Chainalysis
Trusted Enclaves: Trusted Execution Environments (TEEs)
TEEs are secure spaces for highly valuable information stored in isolated environments that cannot be tampered with by third parties.
Onchain applications can tap on TEEs to fill gaps in computation power, privacy, improve UX and ensure that off-chain data are tamper proof. Examples include:
Flashbots: Ensuring privacy for incoming blocks while maintaining proof of authenticity
DePIN networks (e.g., Bagel): Verifying that the supply side isn't being manipulated
Wallets (e.g., Capsule and Clave): Using passkeys to enhance UX
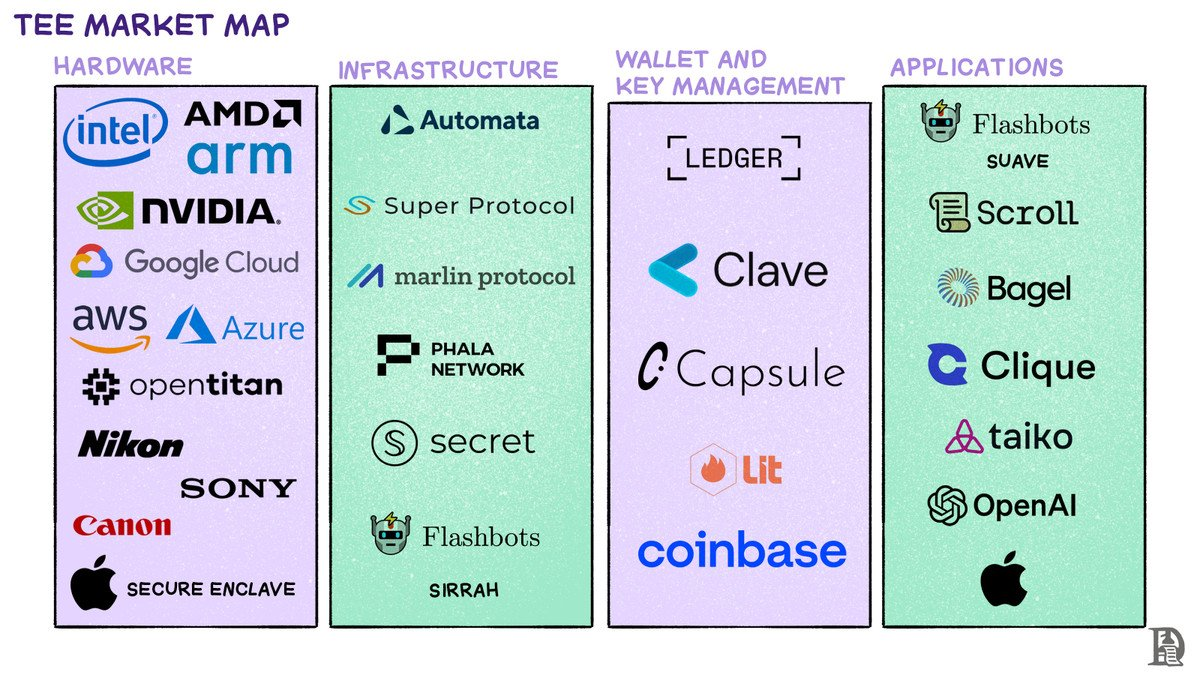
Image via: decentralised.co
Research Paper | Permissionless Verifiable Information Dispersal: Data Availability for Bitcoin Rollups
Rollups scale blockchains by processing transactions off-chain and posting updates to the main chain, cutting costs and boosting speed. They’re popular on Ethereum and now gaining interest for Bitcoin. This new system improves data availability for Bitcoin rollups, reducing communication costs by 1,000× and latency by 10×, while staying compatible with Bitcoin’s existing network.
Subscribe to my newsletter
Read articles from Cryptape directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
