Malware Analysis of Zeus Banking Trojan
 TATHAGATA ROY
TATHAGATA ROYTable of contents
- Introduction
- Setting Up the Environment for Malware Analysis
- Background Information on Zeus Trojan
- Exfiltration and delivery methods
- Zeus Trojan Crackdown: Gameover Zeus and the FBI’s Efforts
- The Global Impact of Zeus Trojan
- The Malware Analysis Process: Downloading Zeus Trojan
- Impact on End-User Machines and Financial Institutions
- Preventive Measures Against Zeus Trojan and Its Variants
- Conclusion
- Sources

The Zeus Banking Trojan has been one of the most persistent and dangerous pieces of malware to target financial institutions and end-user systems. This technical blog walks through a complete malware analysis of the Zeus Trojan using a secure, isolated environment. We will discuss its background, analyze its behavior using static and dynamic techniques, and explore how it exfiltrates data and infiltrates systems worldwide.
Introduction
Zeus Trojan (also known as Zbot) is one of the most infamous banking Trojans in cybersecurity history. First discovered in 2007, it made waves for its highly effective ability to steal sensitive financial information such as banking credentials and passwords. The malware operates through stealthy methods, adding infected systems to a peer-to-peer (P2P) botnet.
Malware analysis is crucial for understanding how these threats evolve. In this blog, we will perform a deep analysis of the Zeus Trojan by leveraging the Cuckoo Sandbox. We’ll analyze both static and dynamic behaviors of the malware, and provide key insights into how it exfiltrates data and propagates through systems.
Setting Up the Environment for Malware Analysis
When performing malware analysis, it's critical to work in a controlled and isolated environment to prevent accidental infection. For this analysis, we will use Cuckoo Sandbox (available at https://cuckoo.cert.ee/) and open it inside Firefox running within a Docker container for added isolation.
Here’s how you can set up the environment:
# Step 1: Clone the Docker environment repository
git clone https://github.com/roy9495/kde-in-docker
# Step 2: Build and run the container
docker run -p 8080:8080 -p 5900:5900 msjpq/firefox-vnc
This command will start a Docker container that runs Firefox in a VNC (Virtual Network Computing) environment, which allows you to safely browse and open the Cuckoo Sandbox without risking your host system. The sandbox will allow us to upload the Zeus malware sample and analyze its behavior securely.
Background Information on Zeus Trojan
The Zeus Trojan was first spotted in 2007 when it was caught stealing sensitive data from systems owned by the U.S. Department of Transportation. Its creator is believed to be Evgeniy Mikhailovich Bogachev, a Russian hacker, who remains one of the FBI's most wanted cybercriminals with a $3 million bounty on his head. Over the years, Zeus has evolved into a significant cybercrime tool, inspiring hundreds of additional variants and wreaking havoc across financial systems worldwide.
Some notable stats about Zeus from the Zeus Museum (https://zeusmuseum.com/):
573+ known versions of the Zeus Trojan
36 known families (only 1 active at present)
627 versions and, 98244 samples in total
Zero FOIA (Freedom of Information Act) disclosures related to Zeus.
In 2011, the source code for Zeus was leaked, allowing cybercriminals to modify and adapt the Trojan for various new purposes. As a result, many other forms of malware were born from Zeus’s codebase, making it one of the most influential malware strains to date.
Evolution of the Zeus Trojan
The leak of Zeus’s source code in 2011 was a turning point. It splintered into numerous new malware families, each using different parts of the code to target various systems, from financial networks to personal computers.
Gameover Zeus was one of the most notorious variants. Unlike earlier versions that relied on centralized servers, Gameover Zeus used a P2P architecture, making it far more resilient to law enforcement takedown attempts.
SpyEye was another variant, which rivaled Zeus but later combined elements from Zeus's codebase after its source code leak. The rivalry between SpyEye and Zeus pushed the development of more advanced malware variants that could bypass more robust cybersecurity defenses.
Citadel: Built on Zeus’s source code, Citadel expanded its focus from financial data to include corporate espionage. Citadel was widely used in targeted attacks against large corporations and government institutions.
ZeuSVM: An even more stealthy variant, ZeuSVM, introduced more sophisticated techniques for staying hidden on victim machines, such as improved rootkit features.
Exfiltration and delivery methods
Zeus's primary objective is to exfiltrate financial data from infected machines and add them to a globally distributed P2P botnet. Once a machine is infected, it can be remotely controlled by the attacker to perform a variety of malicious activities, including stealing login credentials, passwords, and more.
Credential theft: Zeus intercepts browser sessions to steal banking credentials.
Man-in-the-browser attacks: The malware modifies HTML and JavaScript within browsers to capture login details when users interact with banking websites.
Botnet activity: Infected machines are added to a P2P botnet that communicates with command-and-control servers controlled by attackers.
Drive-by Downloads: This method requires the victim to visit a compromised website that automatically downloads the malware onto the system. Modern browsers block most of these attacks by default, making this method mostly obsolete.
Phishing and Spam Campaigns: Currently, the most common method of spreading Zeus is through phishing emails. These emails contain malicious attachments or links that download the Trojan onto the system once clicked. Social engineering techniques are often used to make the emails appear legitimate.
Zeus Trojan Crackdown: Gameover Zeus and the FBI’s Efforts
One of the largest crackdowns on Zeus occurred in 2014 when the FBI launched a coordinated takedown of Gameover Zeus, one of the most sophisticated variants of Zeus. The operation targeted the malware's P2P infrastructure, which had infected over 1 million computers globally, with 25% of those infections in the United States.
- This operation was one of the largest in the FBI’s history and had significant repercussions for cybercriminals. Gameover Zeus alone caused an estimated $100+ million in financial damages.
The Global Impact of Zeus Trojan
Its flexibility and modular design allowed it to inspire numerous other variants, all of which contributed to substantial global financial losses. Zeus’s codebase remains foundational for many modern Trojans, extending its influence long after its original development.
The Malware Analysis Process: Downloading Zeus Trojan
To conduct a thorough malware analysis, it is essential to obtain a sample of the malware safely. In the case of Zeus Trojan, a sample is available on GitHub under the Zoo repository (the Zoo Repository).
Steps to Download
First, we have to download the malware from GitHub.
Important Note: When downloading malware samples, it's crucial to isolate them from any network connection and use a controlled environment. Here's a warning message you should always keep in mind when handling malware samples:
Warning: Do not download or execute malware samples on your main machine. Always use a virtual environment or sandbox to contain the malware and prevent accidental infectionWe have to go into https://github.com/ytisf/theZoo/tree/master/malware/Binaries/ZeusBankingVersion_26Nov2013 and download the raw zip file as it is more suitable for the analysis, and download it into Edge as Chrome would block it. After downloading it, we have to unzip the file and upload it into the sandbox. The password for unzipping is “infected”.
Uploading to Sandbox: Once extracted, upload the file to Cuckoo Sandbox for analysis (https://cuckoo.cert.ee/).
Fingerprint
- After uploading the file to the sandbox, it analyzes the file and after that gives a detailed report about this Trojan, which can be found at
https://cuckoo.cert.ee/analysis/5213360/summary/.
The sandbox gives it a score of 10 out of 10.
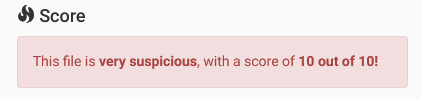
The hashes generated from the Zeus Trojan sample help us verify its integrity and detect whether the same file has been seen elsewhere in the malware community. These hashes include:
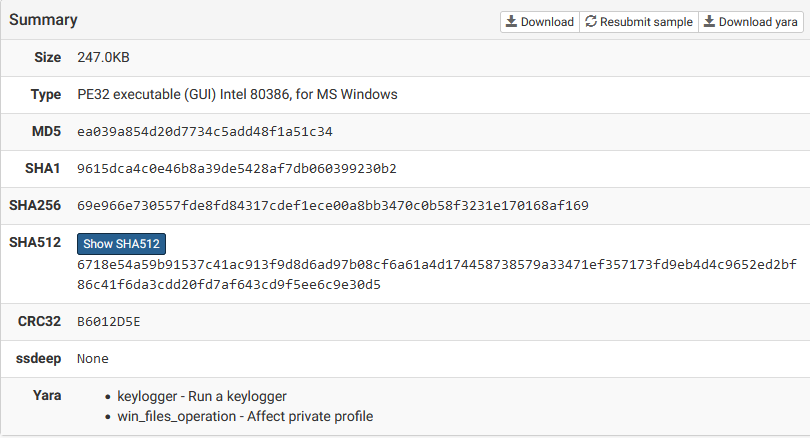
SHA256 : 69e966e730557fde8fd84317cdef1ece00a8bb3470c0b58f3231e170168af169
SHA1 : 9615dca4c0e46b8a39de5428af7db060399230b2
MD5 : ea039a854d20d7734c5add48f1a51c34
Filename : invoice_2318362983713_823931342io.pdf.exe
Yara rules help malware analysts identify malware based on patterns within the binary, such as strings, file sizes, and specific function calls. The sandbox also generates Yara rules to help identify Zeus in future analysis or investigations.
The file has been identified by 53 Antivirus engines on VirusTotal as malicious. These antivirus engines match the sample against their database of known malware, which helps identify Zeus and similar trojans.
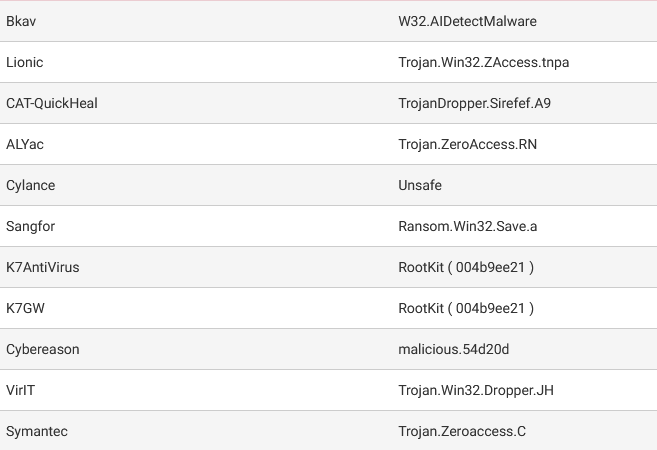
Basic Static Analysis
Once the Zeus sample has been uploaded into the sandbox, the first step in understanding its behavior is to conduct static analysis. This involves analyzing the binary without executing it. Static analysis gives us insight into the file’s structure, its dependencies, and embedded functions.
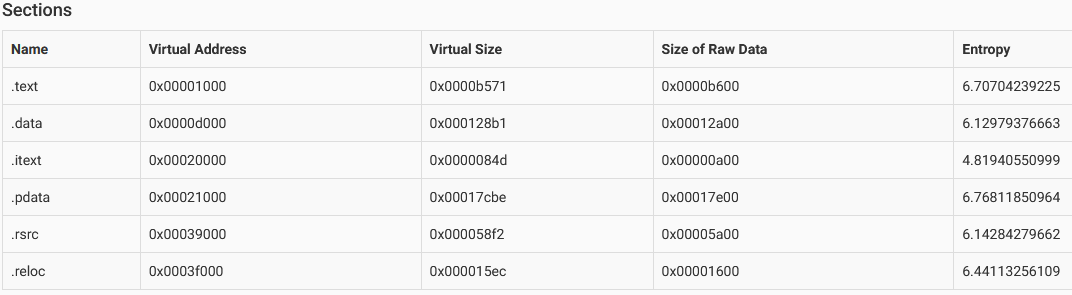
Size Comparison-Raw vs Virtual: In static analysis, one common method is to compare the raw size and virtual size of the file. This helps determine whether the file is packed or compressed.
Raw Size: The size of the file on disk.
Virtual Size: The size of the file when loaded into memory.
If these two sizes are significantly different, the file is likely packed. If they are similar, there’s no packing or compression present, and the malware is presented as-is.
In the strings part after the analysis, all API Calls are listed as below:
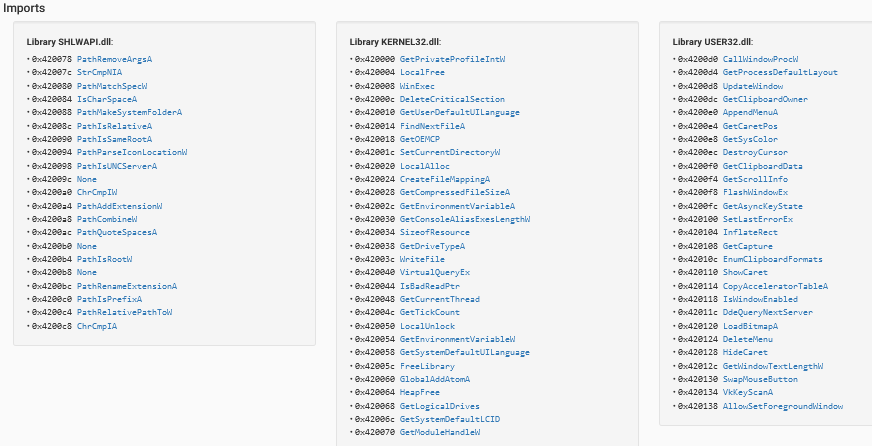
Strings can often reveal valuable information such as function calls, URLs, and embedded resources. The Zeus sample contains suspicious strings, particularly function calls related to critical Windows DLLs:
SHLWAPI.dll: This is a Shell Lightweight Utility Library that provides functions for handling strings, paths, and registry entries.
KERNEL32.dll: This is a critical part of the Windows kernel and provides core system functions such as memory management, input/output operations, and interrupts.
USER32.dll: It handles user interface components like windows, buttons, and input from keyboards and mice.
KERNEL32.MulDiv: A specific function in the KERNEL32.dll that performs combined multiplication and division in a single step for accurate calculations without intermediate overflow. Malware often leverages system-level DLLs like these to interact with the operating system in stealthy ways.
These files are essential for the functioning of Windows and are often involved in system-level processes.
Embedded URL- corect.com: Another suspicious indicator is the embedded corect.com URL within the binaries. When we examine this URL using VirusTotal, it shows no malicious flags. Further inspection of the website reveals that it’s a Romanian news website.
However, the inclusion of an embedded URL like this could point to Command and Control (C2) communication, or could serve as a decoy. While this specific URL is harmless, it's common for malware to hide C2 servers in plain sight, using legitimate-looking URLs as a cover for malicious activity.
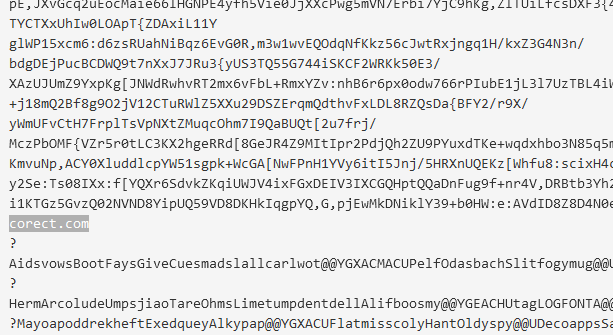
If we go into that website, we will see that it is a Romanian News website.
Dynamic Analysis
After completing static analysis, we move to dynamic analysis, where the malware is executed in a controlled environment to observe its real-time behavior. For this analysis, we also used Cuckoo Sandbox, which allows us to monitor system changes, file creation, network connections, and other behavioral indicators.
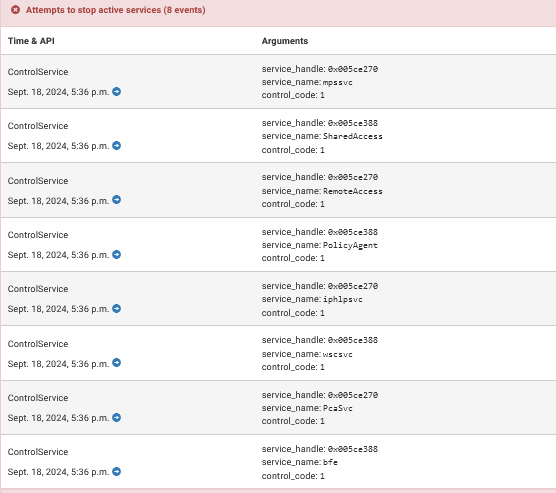
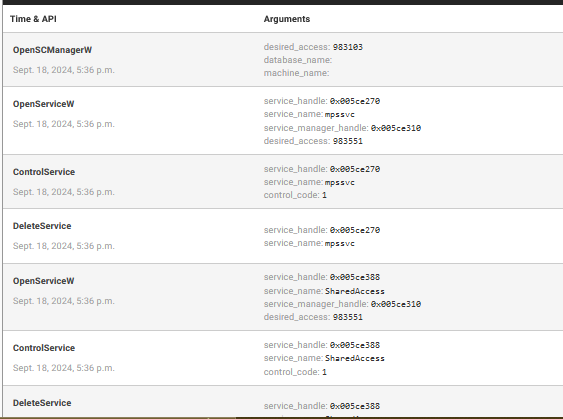
Attempts to stop active services
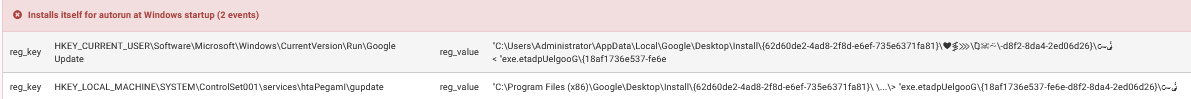
Installs itself for AutoRun at Windows startup: Zeus installs itself to AutoRun at system startup, ensuring persistence across reboots. This means that every time the computer is turned on, the malware will execute automatically. This persistence mechanism is crucial for attackers because it guarantees the malware stays active even after system restarts.
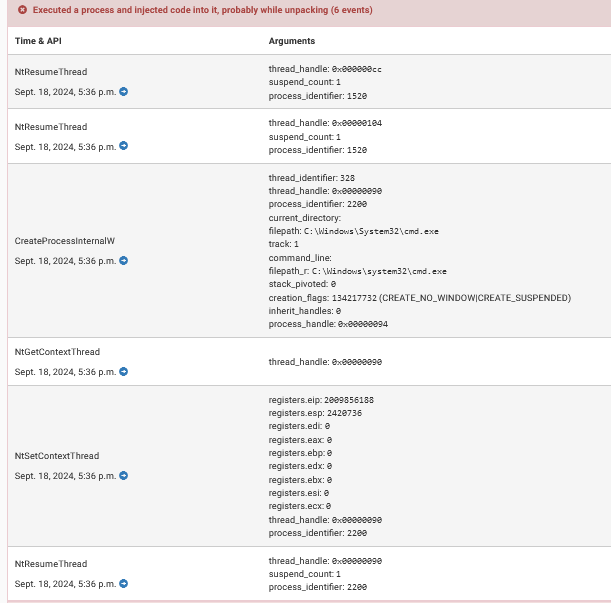
Process injections: Zeus uses process injection techniques to embed its malicious code into legitimate system processes, by doing so, it hides its activity under the guise of trusted system processes, making it harder for antivirus software and other monitoring tools to detect it.
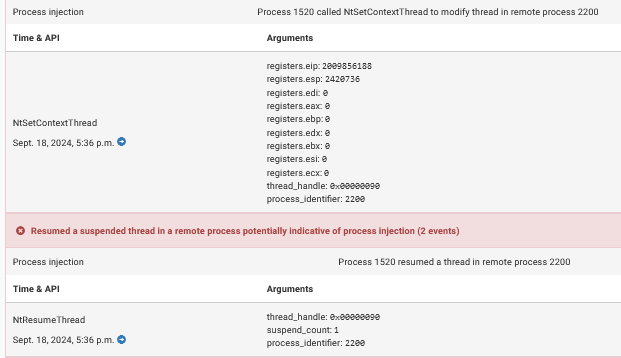
Stops Windows services: One of Zeus’s primary actions is to stop certain Windows services that may interfere with its execution. By terminating critical processes, Zeus attempts to weaken the system’s defense mechanisms.
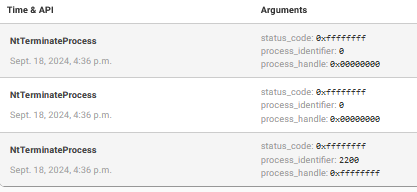
Executes processes and injects codes
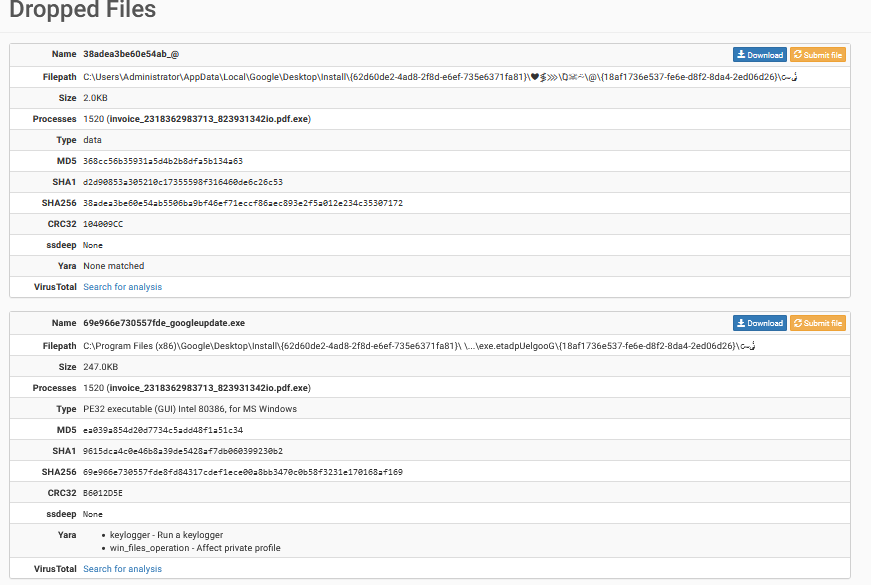
Dropped files: Zeus also drops additional files onto the infected system. These files are often used to help maintain persistence or communicate with external servers. In the case of our analysis, the following files were dropped:
invoice_2318362983713_823931342io.pdf.exe: This is the primary executable that contains the malicious code.
cmd.exe: Zeus injects code into the command prompt process to execute system-level commands.
These files are critical components of the Zeus infection process, helping it to evade detection and perform malicious activities, such as stealing credentials or exfiltrating data.
Some additional dropped files:
Services for
invoice_2318362983713_823931342io.pdf.exeprocess tree
8. Processes for cmd.exe process tree.
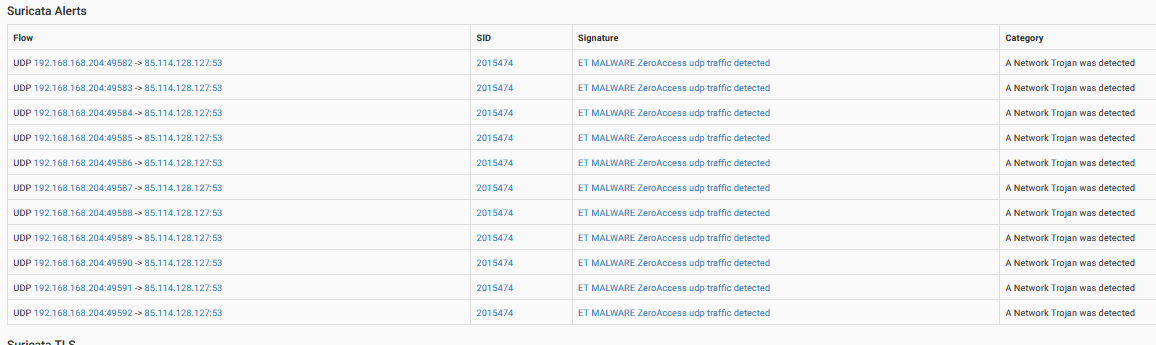
- Network analysis: Zeus uses a mix of HTTP, HTTPS, and custom protocols for communicating with its C2 infrastructure. These communications are usually encrypted or obfuscated to avoid detection by network monitoring tools. Cuckoo Sandbox revealed that Zeus attempted to communicate with several IP addresses and domains that were associated with known malicious activity.
Impact on End-User Machines and Financial Institutions
Zeus’s primary target is financial institutions, but its impact extends to personal devices, corporate networks, and government systems. The malware’s ability to steal login credentials, particularly banking details, has made it a preferred tool for cybercriminals seeking financial gain.
Impact on End-User Machines:
Once installed on a personal device, Zeus can perform a range of malicious actions:
Credential Theft: The malware is designed to capture sensitive login credentials, including usernames, passwords, and bank account information. It achieves this through man-in-the-browser (MitB) attacks, where it modifies the web browser to steal information as the user enters it.
System Degradation: Infected machines often experience significant performance slowdowns. This is due to Zeus’s constant monitoring and injection into various system processes, which increases CPU and memory usage.
Impact on Financial Institutions:
Zeus poses a massive threat to financial institutions. Its ability to target banking systems and online transaction platforms means that banks, payment processors, and even e-commerce platforms are at risk.
Credential Harvesting: Zeus’s MitB technique allows it to capture not only personal banking credentials but also two-factor authentication (2FA) codes, which are used to secure banking transactions.
Unauthorized Transactions: After capturing banking credentials, Zeus can initiate unauthorized transfers, draining victim accounts without their knowledge. This has resulted in millions of dollars in losses for both individuals and banks.
Preventive Measures Against Zeus Trojan and Its Variants
As Zeus continues to inspire new variants, the threat landscape for financial institutions and end-users evolves. However, several preventive measures can be employed to reduce the risk of infection.
1. User Education
Since phishing and social engineering remain the primary infection methods, educating users is the first line of defense. Employees of financial institutions and end-users should be trained to recognize phishing emails and avoid clicking on suspicious links or downloading untrusted attachments.
2. Email Filtering and Anti-Phishing Solutions
Implementing robust email filtering solutions that block phishing emails can help mitigate the risk of infection. Additionally, many anti-phishing tools can detect and block suspicious emails or malicious links before they reach the user’s inbox.
3. Network Segmentation
To prevent the spread of malware within an organization, network segmentation should be implemented. By isolating different parts of the network, an infection in one segment will not easily propagate to the rest of the network, reducing the overall impact.
4. Use of Sandboxing Solutions
Security teams should use sandboxing solutions like Cuckoo Sandbox to analyze suspicious files before they are allowed to enter the corporate network. By quarantining and analyzing these files, organizations can detect and block malware before it causes damage.
5. Regular Patching and Updates
Outdated software is often exploited by malware like Zeus to gain access to systems. Regularly updating software and applying security patches is critical to prevent Zeus from exploiting known vulnerabilities.
6. Advanced Threat Detection Solutions
Financial institutions should invest in advanced threat detection solutions that monitor for suspicious activities like process injections, auto-run modifications, and unusual network communications. By detecting these behaviors early, organizations can block malware like Zeus before it causes significant damage.
Conclusion
The Zeus Trojan is one of the most dangerous and financially devastating pieces of malware ever created. Its evolution into numerous variants, such as Gameover Zeus, has made it a formidable adversary for both cybersecurity professionals and financial institutions. Through both static and dynamic analysis, we’ve explored how Zeus operates, its exfiltration methods, and its impact on global cybercrime.
As malware continues to evolve, it’s vital to employ robust security practices, such as using sandbox environments, educating users, and leveraging advanced threat detection tools to stay ahead of these threats. The fight against malware like Zeus is ongoing, and continuous vigilance is necessary to protect systems and financial data from these sophisticated attacks.
FAQs:
What is Zeus Trojan?
- The Zeus Trojan is a type of banking malware designed to steal financial information and credentials. It also adds infected systems to a P2P botnet, making it a versatile tool for cybercriminals.
How can I protect my system from Zeus Trojan?
- To protect against Zeus, avoid opening suspicious emails, keep your software updated, and use antivirus solutions that can detect and block known Zeus variants.
Sources
Grant Collins : https://www.youtube.com/watch?v=USNOmFcebcU
Robert Simmons : https://www.youtube.com/watch?v=ZNxK4BvhAdI&t=1642s
Lauriewired Youtube:https://www.youtube.com/watch?v=JAfeGIMzsfw&t=172s
Zoo repository : https://github.com/ytisf/theZoo
Subscribe to my newsletter
Read articles from TATHAGATA ROY directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

TATHAGATA ROY
TATHAGATA ROY
Hello! I'm a passionate and dedicated cybersecurity enthusiast with a love for learning and sharing insights, my blog dives deep into cybersecurity threats, technical analysis, and best practices to safeguard digital assets.