OverTheWire's Bandit: A Hands-On Guide to Linux Commands and Security Fundamentals - Part 1 (Level 0–10)
 Collins Boit
Collins Boit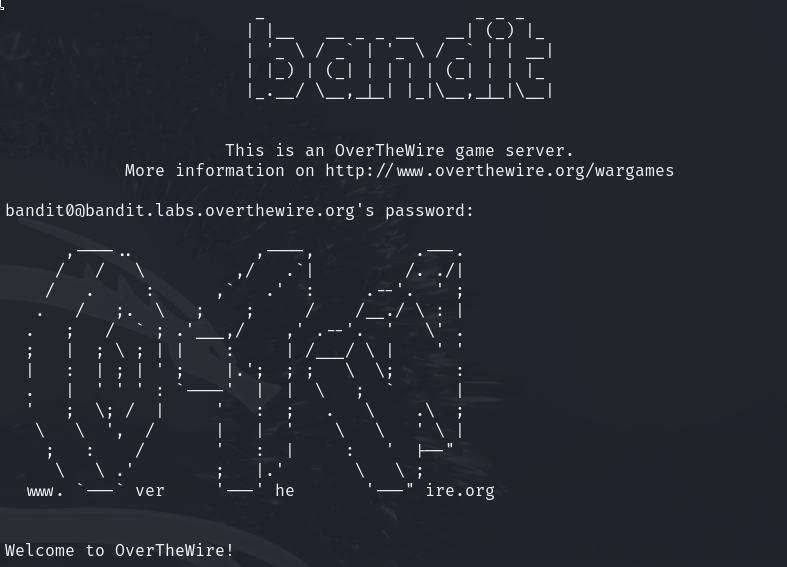
Introduction
Welcome to my walkthrough of the Bandit game from OverTheWire! If you’re like me, you’re probably on a quest to level up your Linux skills while having some fun in the process. Bandit is a fantastic starting point for anyone looking to get their hands dirty with command-line basics and security fundamentals.
Bandit Level 0
Level Goal
The goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org, on port 2220. The username is bandit0 and the password is bandit0. Once logged in, go to the Level 1 page to find out how to beat Level 1.
Secure Shell (SSH) protocol is a method for securely sending commands to a computer over an unsecured network. SSH uses cryptography to authenticate and encrypt connections between devices. SSH also allows for tunneling, or port forwarding, which is when data packets are able to cross networks that they would not otherwise be able to cross. SSH is often used for controlling servers remotely, for managing infrastructure, and for transferring files.
ssh bandit0@bandit.labs.overthewire.org -p 2220
bandit0@bandit.labs.overthewire.orgspecifies the username and host.-p 2220specifies the port number (2220 in this case, instead of the default 22).
Helpful Reading Material
Bandit Level 0 → Level 1
Level Goal
The password for the next level is stored in a file called readme located in the home directory. Use this password to log into bandit1 using SSH. Whenever you find a password for a level, use SSH (on port 2220) to log into that level and continue the game.
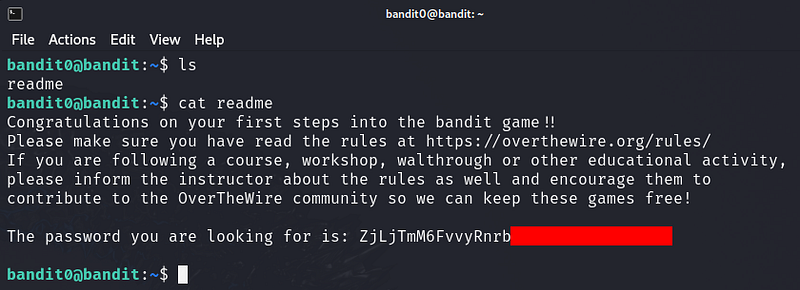
TIP: Create a file for notes and passwords on your local machine! Passwords for levels are not saved automatically. If you do not save them yourself, you will need to start over from bandit0.
Passwords also occassionally change. It is recommended to take notes on how to solve each challenge. As levels get more challenging, detailed notes are useful to return to where you left off, reference for later problems, or help others after you’ve completed the challenge.
Bandit Level 1 → Level 2
Level Goal
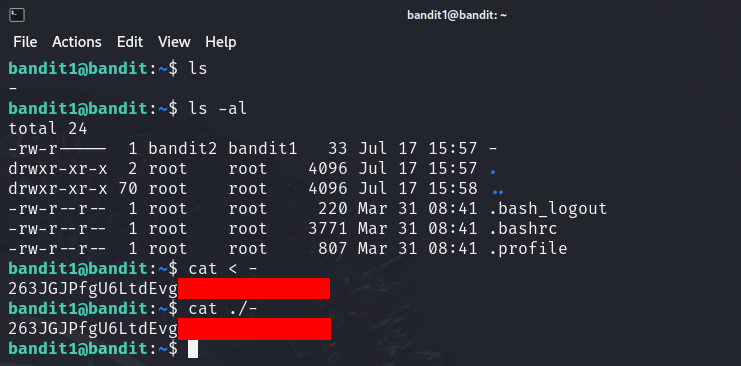
The password for the next level is stored in a file called — located in the home directory
Helpful Reading Material
Bandit Level 2 → Level 3
Level Goal
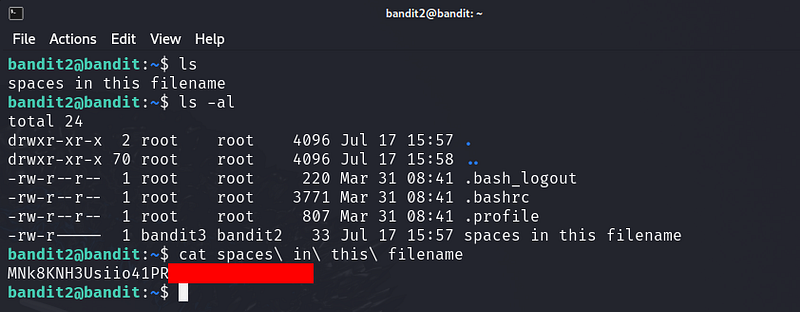
The password for the next level is stored in a file called spaces in this filename located in the home directory
Helpful Reading Material
Bandit Level 3 → Level 4
Level Goal
The password for the next level is stored in a hidden file in the inhere directory.
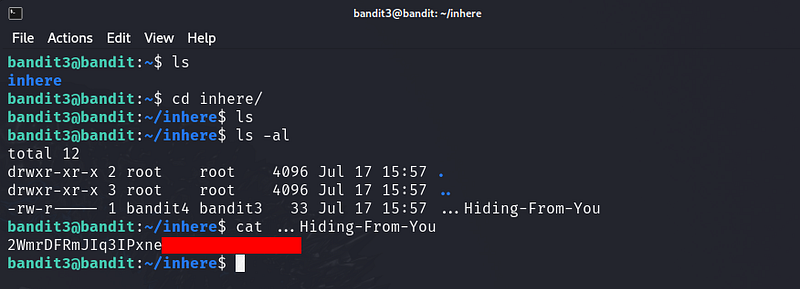
Bandit Level 4 → Level 5
Level Goal
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
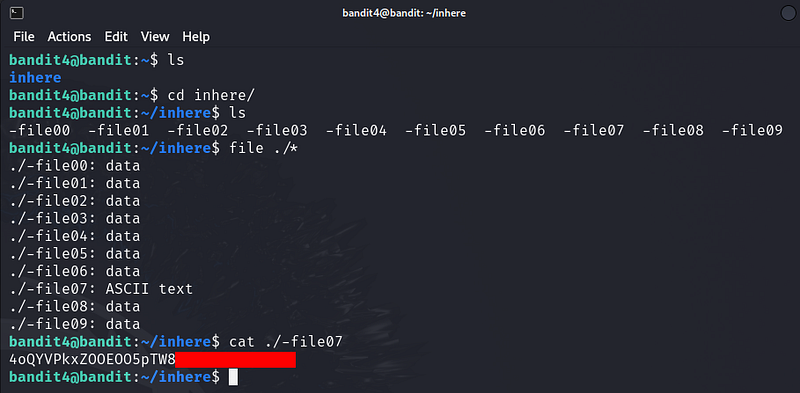
Bandit Level 5 → Level 6
Level Goal
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
human-readable
1033 bytes in size
not executable
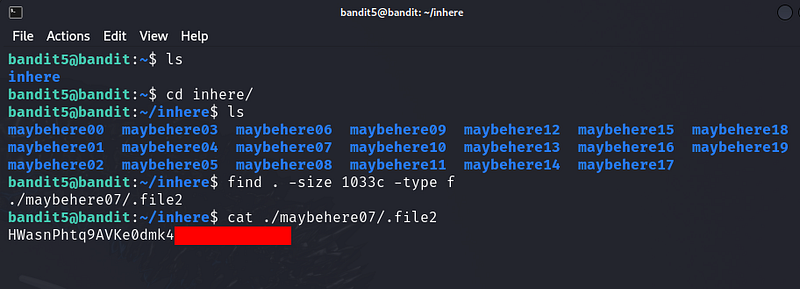
Explanation:
.indicates the current directory (inherein this case).-type flimits the search to files.-size 1033clooks for files that are exactly 1033 bytes (cstands for bytes).! -executableexcludes executable files.
Bandit Level 6 → Level 7
Level Goal
The password for the next level is stored somewhere on the server and has all of the following properties:
owned by user bandit7
owned by group bandit6
33 bytes in size
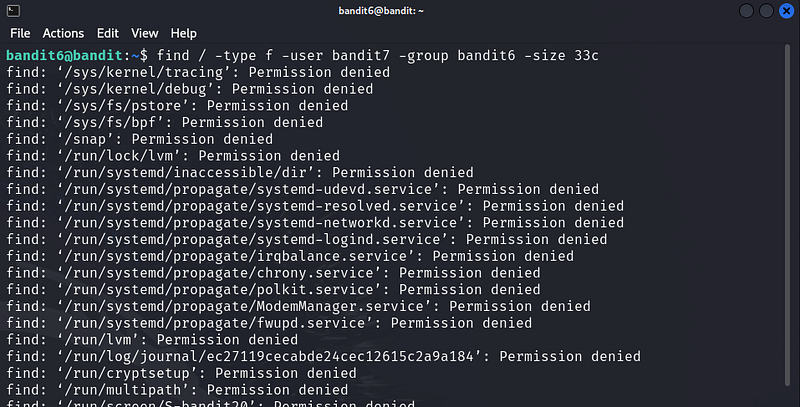
Explanation:
/starts the search from the root directory.-user bandit7limits the search to files owned by the userbandit7.-group bandit6limits the search to files owned by the groupbandit6.-size 33climits the search to files that are exactly 33 bytes (cstands for bytes).2>/dev/nullredirects error messages (like "Permission denied") to/dev/nullso they don't clutter your output.
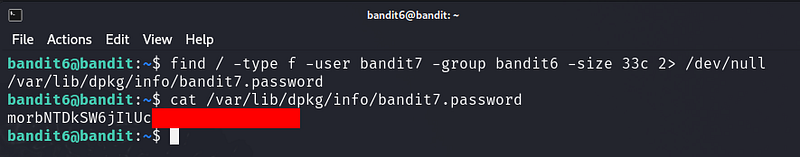
Bandit Level 7 → Level 8
Level Goal
The password for the next level is stored in the file data.txt next to the word millionth
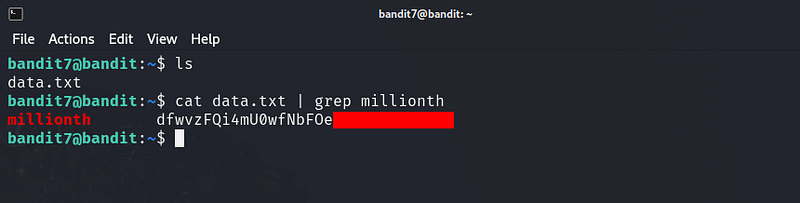
Bandit Level 8 → Level 9
Level Goal
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
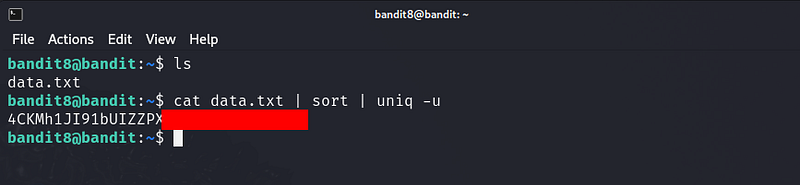
Helpful Reading Material
Bandit Level 9 → Level 10
Level Goal
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
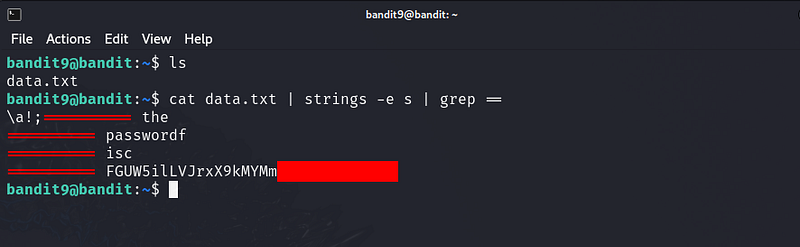
Bandit Level 10 → Level 11
Level Goal
The password for the next level is stored in the file data.txt, which contains base64 encoded data
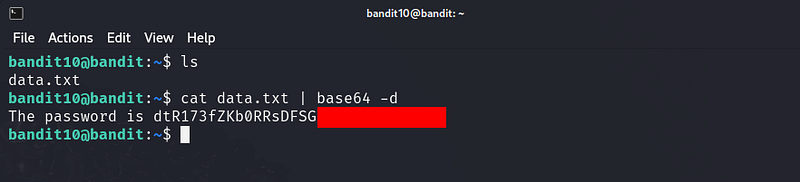
Helpful Reading Material
Commands you may need to solve this level
Here’s a breakdown of the commands used from Level 0 to Level 11 in OverTheWire’s Bandit game, along with examples on how to use them:
1. ssh (Secure Shell)
Usage: SSH is used to remotely log into the Bandit server.
Example: ssh bandit0@bandit.labs.overthewire.org -p 2220
bandit0@bandit.labs.overthewire.org: Username and host.-p 2220: Specifies the port (2220 instead of the default 22).
2. ls (List Directory Contents)
Usage: Lists files and directories in the current location.
Example:
ls: Lists all visible files in the directory.ls -a: Lists all files, including hidden ones (starting with.).ls -l: Provides detailed information such as file permissions, owner, and size.
3. cd (Change Directory)
Usage: Navigates between directories.
Example:
cd inhere: Moves into theinheredirectory.cd ..: Moves back to the parent directory.
4. cat (Concatenate and Display Files)
Usage: Displays the content of a file.
Example:
cat readme: Displays the contents of thereadmefile.cat -n filename: Displays the content with line numbers.
5. file (Determine File Type)
Usage: Describes the type of a file.
Example:
file readme: Identifies what type of data the filereadmecontains (e.g., text, binary).
6. du (Disk Usage)
Usage: Shows the disk usage of files and directories.
Example:
du -h: Shows the sizes in human-readable format (e.g., KB, MB).du -sh *: Displays a summary of the size of each file in the current directory.
7. find (Search for Files and Directories)
Usage: Locates files in a directory hierarchy.
Example:
find . -name readme: Searches for the file namedreadmein the current directory.find / -user bandit7 -group bandit6 -size 33c: Searches for a file based on specific properties like owner, group, and size.
8. grep (Search Inside Files)
Usage: Searches for patterns within files.
Example:
grep millionth data.txt: Finds the line containing "millionth" indata.txt.grep '^=' data.txt: Finds lines starting with the=character.
9. sort (Sort Lines of Text Files)
Usage: Sorts lines of a text file.
Example:
sort data.txt: Sorts the lines indata.txtalphabetically.sort -n data.txt: Sorts the file numerically.
10. uniq (Report or Omit Repeated Lines)
Usage: Removes or reports repeated lines in a file.
Example:
uniq data.txt: Removes adjacent duplicate lines.sort data.txt | uniq -u: Finds unique lines after sorting.
11. strings (Find Printable Strings in Binary Files)
Usage: Extracts printable text from binary files.
Example:
strings data.txt: Displays human-readable strings in thedata.txtfile.
12. base64 (Base64 Encoding/Decoding)
Usage: Encodes or decodes base64 data.
Example:
base64 -d data.txt: Decodes base64-encoded data indata.txt.echo "password" | base64: Encodes the word "password" in base64.
13. tr (Translate or Delete Characters)
Usage: Translates or deletes characters from input.
Example:
cat data.txt | tr 'a-z' 'A-Z': Converts lowercase letters to uppercase indata.txt.cat data.txt | tr -d '=': Deletes the=characters from the output.
14. tar (Tape Archive)
Usage: Archives multiple files into a single file and extracts them.
Example:
tar -xf archive.tar: Extracts the contents ofarchive.tar.tar -czf archive.tar.gz directory: Compresses a directory into a.tar.gzfile.
15. gzip (Compression Utility)
Usage: Compresses files using the GNU zip algorithm.
Example:
gzip file.txt: Compressesfile.txttofile.txt.gz.gzip -d file.txt.gz: Decompresses the file.
16. bzip2 (File Compression)
Usage: Compresses files using a higher compression ratio than gzip.
Example:
bzip2 file.txt: Compressesfile.txtintofile.txt.bz2.bzip2 -d file.txt.bz2: Decompresses the file.
17. xxd (Hex Dump Tool)
Usage: Creates a hex dump of a file.
Example:
xxd data.txt: Converts the filedata.txtto a hexadecimal representation.xxd -r data.hex: Converts the hex dump back into its original format.
Please check out https://github.com/l00pinfinity/blog-stories. It contains my blog posts online, do you have any suggestions? A correction, perhaps? Make a pull request on Github or open an issue.
Thanks for reading and stay tuned!!!
Subscribe to my newsletter
Read articles from Collins Boit directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Collins Boit
Collins Boit
Android and Backend Developer