The Most Severe DDoS Attacks and Mitigation Strategies
 SAMAN SARADRI
SAMAN SARADRI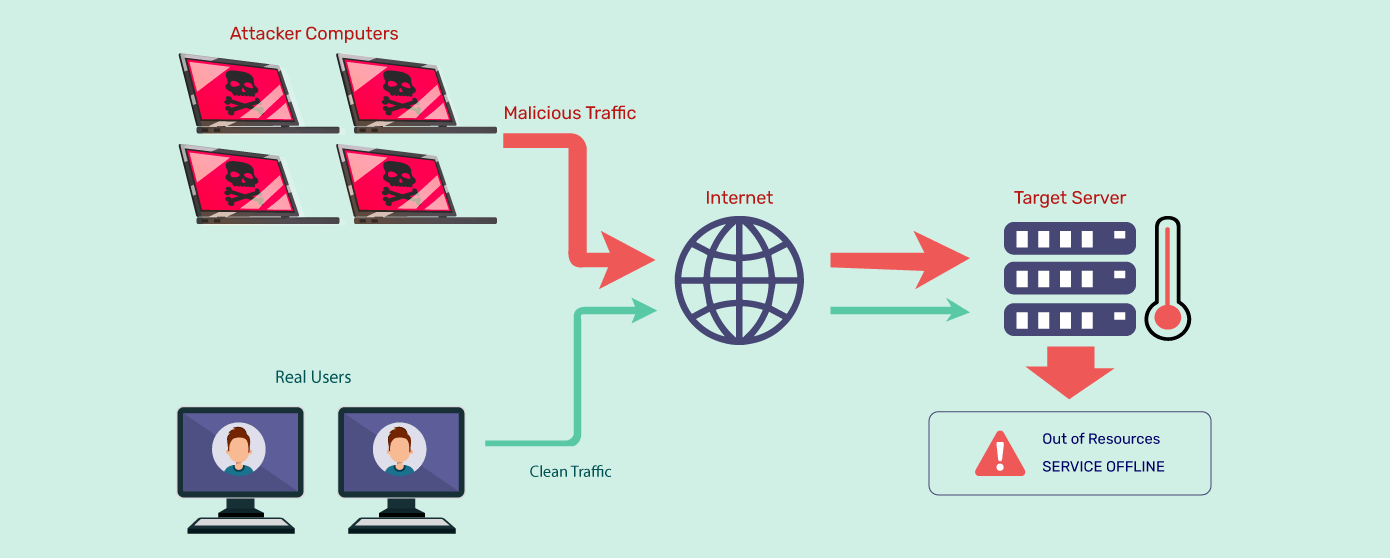
The Most Severe DDoS Attacks and Mitigation Strategies
Introduction
Distributed Denial of Service (DDoS) attacks are malicious attempts to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of Internet traffic. With the rise of the Internet of Things (IoT) and increasingly sophisticated cybercriminal tactics, DDoS attacks have become more frequent and severe. This article explores some of the most devastating DDoS attacks in history and offers effective mitigation strategies to help organizations defend against such threats.
Notable DDoS Attacks
The 2016 Dyn Attack
One of the most infamous DDoS attacks occurred in October 2016, targeting Dyn, a major DNS provider. The attack utilized the Mirai botnet, composed of thousands of compromised IoT devices, such as cameras and DVRs. The attack peaked at 1.2 Tbps (terabits per second) and caused widespread outages for major websites and services, including Twitter, Netflix, Reddit, and Spotify. The attack demonstrated the vulnerability of the DNS infrastructure and the potential for massive disruption through IoT exploitation.
GitHub Attack (2018)
In February 2018, GitHub experienced one of the largest DDoS attacks recorded at that time, peaking at 1.35 Tbps. The attack used a technique called Memcached amplification, where misconfigured Memcached servers were exploited to amplify the attack traffic significantly. The swift response from GitHub's engineering team and their collaboration with DDoS mitigation providers helped them to mitigate the attack within a short time frame.
Google Attack (2017)
In late 2017, Google reported that it had thwarted a massive DDoS attack that peaked at 2.54 Tbps, which is among the largest ever recorded. This attack targeted Google services using a combination of techniques, including SYN floods and other amplification methods. Google’s global infrastructure allowed them to absorb the attack effectively, showcasing the importance of having robust network architecture in place.
AWS Attack (2020)
Amazon Web Services (AWS) revealed in 2020 that they had mitigated a DDoS attack that peaked at 2.3 Tbps. The attack targeted an unnamed customer and employed multiple attack vectors, including UDP reflection attacks. AWS utilized its built-in DDoS protection capabilities to absorb and mitigate the attack, preventing any disruption to services.
Understanding DDoS Attack Techniques
DDoS attacks can be categorized into several types:
Volume-Based Attacks: These involve overwhelming the target with high volumes of traffic. Examples include ICMP floods and UDP floods.
Protocol Attacks: These attacks exploit weaknesses in network protocols to disrupt services. SYN floods and fragmented packet attacks fall under this category.
Application Layer Attacks: These are more sophisticated, targeting specific applications and services. HTTP floods and Slowloris attacks aim to exhaust server resources.
Understanding these attack types helps organizations design effective defenses.
Mitigation Strategies
Rate Limiting
Implementing rate limiting on servers can help control the amount of traffic accepted from a single source. By establishing thresholds for incoming requests, organizations can mitigate the impact of a DDoS attack.
Web Application Firewalls (WAFs)
WAFs can filter and monitor HTTP traffic to and from web applications. By analyzing traffic patterns, WAFs can detect and block malicious requests before they reach the server, providing an additional layer of defense.
DDoS Protection Services
Utilizing cloud-based DDoS protection services, such as those offered by Cloudflare or Akamai, allows organizations to absorb and mitigate attacks at scale. These services often employ advanced algorithms to distinguish between legitimate and malicious traffic.
Network Redundancy
Building redundancy into network infrastructure ensures that if one server or data center is overwhelmed, traffic can be rerouted to other resources. Load balancing and using multiple data centers geographically dispersed can significantly enhance resilience.
Incident Response Planning
Organizations should develop and regularly update an incident response plan tailored to DDoS attacks. This plan should include roles and responsibilities, communication strategies, and recovery procedures to minimize downtime and data loss.
Regular Security Audits
Conducting regular security audits and vulnerability assessments helps organizations identify and address weaknesses in their systems before they can be exploited by attackers.
Conclusion
DDoS attacks continue to pose a significant threat to organizations across various sectors. The severe impact of notable attacks such as those on Dyn, GitHub, Google, and AWS illustrates the need for proactive defense mechanisms. By understanding the types of DDoS attacks and implementing effective mitigation strategies, organizations can bolster their defenses and ensure greater resilience against these malicious activities. As cyber threats continue to evolve, staying informed and prepared is crucial for any organization looking to safeguard its digital assets.
Subscribe to my newsletter
Read articles from SAMAN SARADRI directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
