Understanding AWS IAM: Essential for Cloud Security
 Veda Kashid
Veda KashidAmazon Web Services (AWS) Identity and Access Management (IAM) is a powerful tool that helps organizations manage access to their cloud resources securely. As businesses increasingly move to the cloud, understanding and implementing IAM effectively is crucial for maintaining data security and compliance.
What is AWS IAM?
AWS IAM allows you to control access to AWS services and resources securely. It enables you to create and manage AWS users and groups, and define permissions to allow or deny access to resources. With IAM, you can ensure that only authorized users can access your AWS infrastructure.
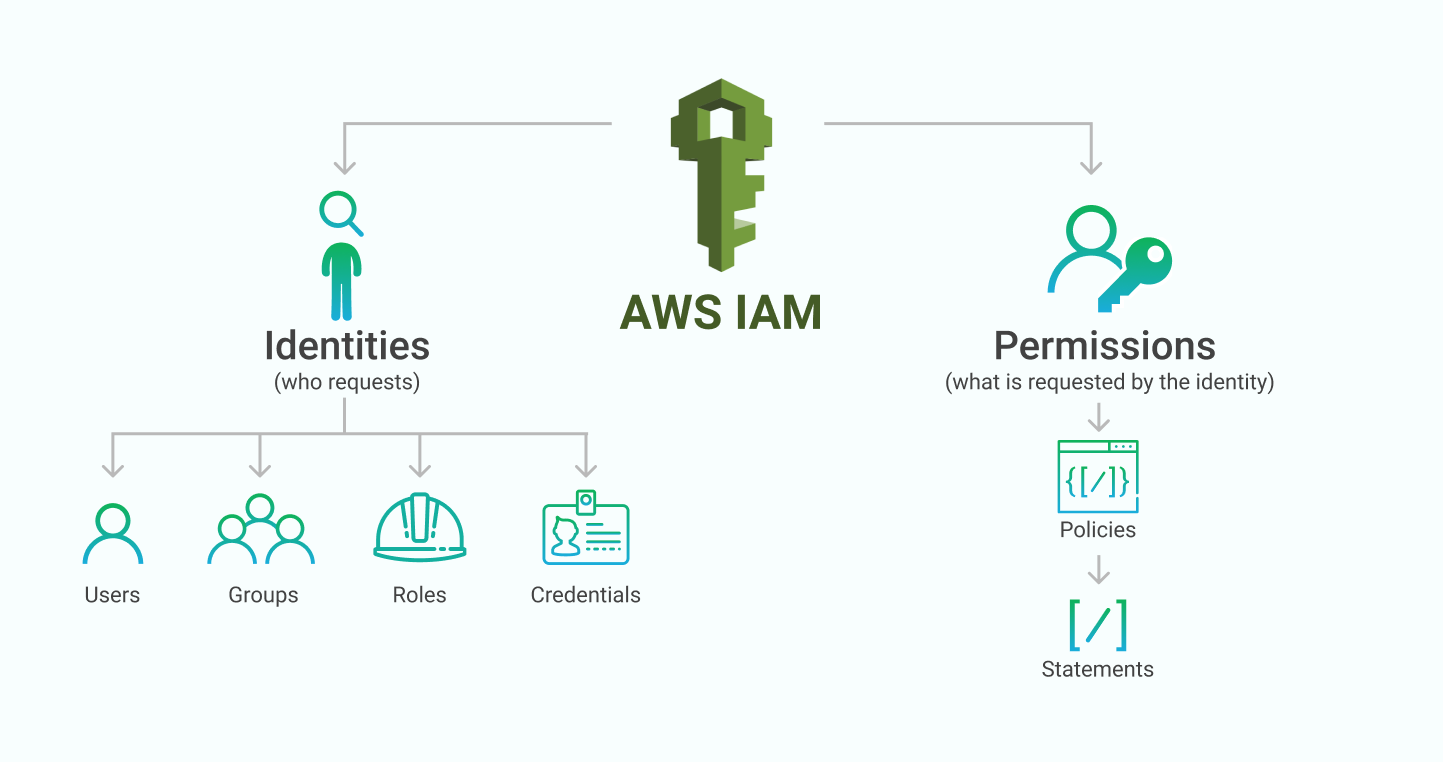
Key Features of AWS IAM
Granular Permissions: IAM allows you to set detailed permissions at the resource level, so you can specify who can do what with each resource.
User Management: You can create individual user accounts for team members, which helps in tracking activity and ensuring accountability.
Groups: Organize users into groups, applying permissions at the group level for easier management.
Roles: IAM roles are useful for granting temporary access to resources, such as when applications need to access AWS services.
Multi-Factor Authentication (MFA): Enhance security by requiring users to provide a second form of verification in addition to their password.
Policies: Define fine-grained access controls using JSON-based policies, which specify permissions based on conditions.
Integration with AWS Services: IAM seamlessly integrates with other AWS services, allowing for a cohesive security strategy across your cloud environment.
Best Practices for AWS IAM
Use Least Privilege Principle: Always grant users the minimum permissions they need to perform their job functions. This minimizes potential damage from compromised accounts.
Enable MFA: Add an extra layer of security by enabling MFA for all IAM users, especially those with high-level permissions.
Regularly Review Permissions: Periodically audit user permissions to ensure they still align with their current roles and responsibilities.
Use IAM Roles for Applications: Instead of hardcoding access keys in applications, use IAM roles to allow applications running on AWS services to access other AWS resources securely.
Implement Password Policies: Set strong password policies to enhance security, including complexity requirements and regular password changes.
Monitor and Log Activity: Use AWS CloudTrail to log and monitor IAM activity. This helps you detect any unauthorized access and ensures compliance with regulations.
Understanding AWS IAM: Users, Groups, Policies, and Roles
AWS Identity and Access Management (IAM) is a critical component of managing access to your AWS resources. Within IAM, there are several key concepts: users, groups, policies, and roles. Each plays a unique role in ensuring secure and efficient management of permissions. Let’s dive into each of these concepts in detail.
1. Users
Definition: An IAM user represents a single person or application that interacts with AWS resources. Each user has a unique identity and can be assigned specific permissions.
Key Features:
Unique Credentials: Each user has their own set of credentials, which can include a username and password, access keys, and MFA (Multi-Factor Authentication) settings.
Access Control: Permissions can be granted to users through policies, allowing them to perform specific actions on AWS resources.
Accountability: Since each user has unique credentials, it’s easier to track and audit activity in your AWS account.
Best Practices:
Create IAM users for individuals and applications that need access to AWS resources, rather than using root account credentials.
Enable MFA for all IAM users to enhance security.
2. Groups
Definition: A user group is a collection of IAM users. Groups help simplify permission management by allowing you to assign policies to multiple users at once.
Key Features:
Simplified Management: By creating groups, you can manage permissions for multiple users more easily. For example, you can create a “Developers” group and assign permissions needed for development tasks.
Inheritance of Permissions: Users within a group inherit the permissions assigned to that group, streamlining the process of assigning access.
Best Practices:
Use groups to organize users based on their roles (e.g., developers, administrators, etc.).
Regularly review group memberships and permissions to ensure they align with current organizational needs.
3. Policies
Definition: Policies are documents that define permissions and specify what actions are allowed or denied on specific resources. They are written in JSON format.
Key Features:
Fine-Grained Control: Policies can define permissions at a very granular level, specifying actions (like
s3:PutObject), resources (like specific S3 buckets), and conditions (like requiring MFA).Types of Policies:
Managed Policies: These are standalone policies that can be attached to multiple users, groups, or roles. AWS provides a set of predefined managed policies, and you can also create custom ones.
Inline Policies: These are policies that are directly embedded within a user, group, or role. They are tightly coupled and can’t be reused elsewhere.
Best Practices:
Follow the principle of least privilege by only granting permissions that are necessary for users to perform their job functions.
Regularly audit policies to ensure they are still relevant and secure.
4. Roles
Definition: An IAM role is similar to a user but is intended to be assumed by anyone (or any service) needing access to AWS resources. Roles are used for temporary access scenarios and do not have long-term credentials.
Key Features:
Temporary Credentials: When a role is assumed, temporary security credentials are provided. This is useful for applications running on AWS services (like EC2 or Lambda) that need access to other AWS resources.
Cross-Account Access: Roles can be used to allow access to resources in different AWS accounts, making it easier to manage multi-account environments.
Use Cases:
EC2 Instance Roles: You can assign a role to an EC2 instance, allowing applications running on that instance to access AWS services without needing to manage credentials.
Cross-Account Roles: Use roles to grant access to resources in another AWS account, facilitating collaboration between teams or organizations.
Best Practices:
Use roles instead of long-term access keys to enhance security for applications and services.
Regularly review and rotate roles to ensure they have the appropriate permissions.
Overall, AWS IAM is an essential service for managing access and permissions in the AWS ecosystem. Its strengths in granular control and security features make it a top choice for businesses prioritizing security. While the complexity and learning curve can be obstacles for some users, the benefits far outweigh the drawbacks for most organizations. Proper training and understanding of IAM principles can lead to a well-secured cloud environment that maximizes the benefits of AWS.
For those considering or currently using AWS, investing time in mastering IAM is well worth the effort for securing your cloud resources.
Subscribe to my newsletter
Read articles from Veda Kashid directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
