Solution to the InZiption Challenge from NCA CTF 2024
 Bimal Dhital
Bimal Dhital
Among the various challenges that were presented in the event, I had a lot of fun solving the forensic challenges.
Among them was the challenge called InZiPtion.
The initial challenge post was straightforward. We were provided with a zip file and upon opening it, we had a zip with nested zip files. I have seen such tactics many times in the CTF. Though I am not an avid CTF player and this one is probably my 3rd time playing, I always tend to read write-ups of the challenges when someone posts them on social media.
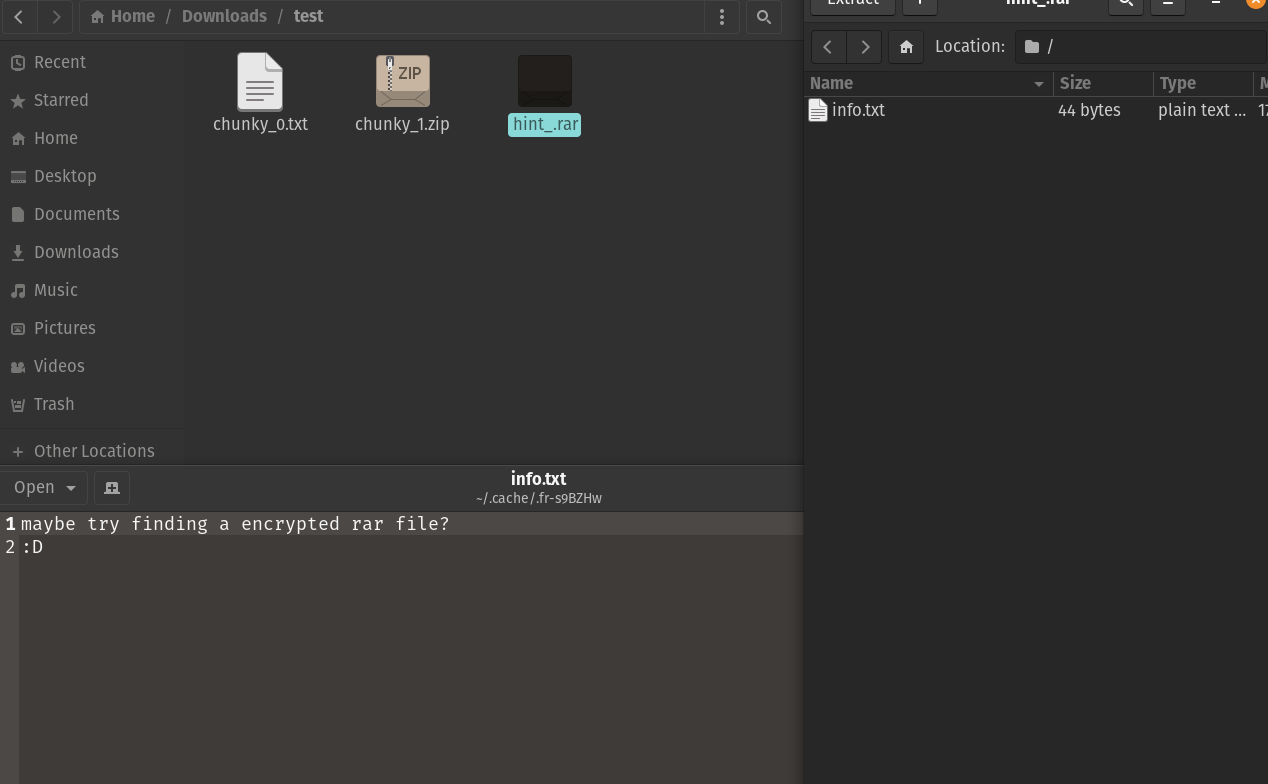
Along with the zip file, was a hint rar file where within it lay a text file that said as shown in the screenshot below.
Our first move was to automate the process of unnesting the nested zips using a simple bash script.
while [ "`find . -type f -name '*.zip' | wc -l`" -gt 0 ]; do find -type f -name "*.zip" -exec unzip -- '{}' \; -exec rm -- '{}' \;; done
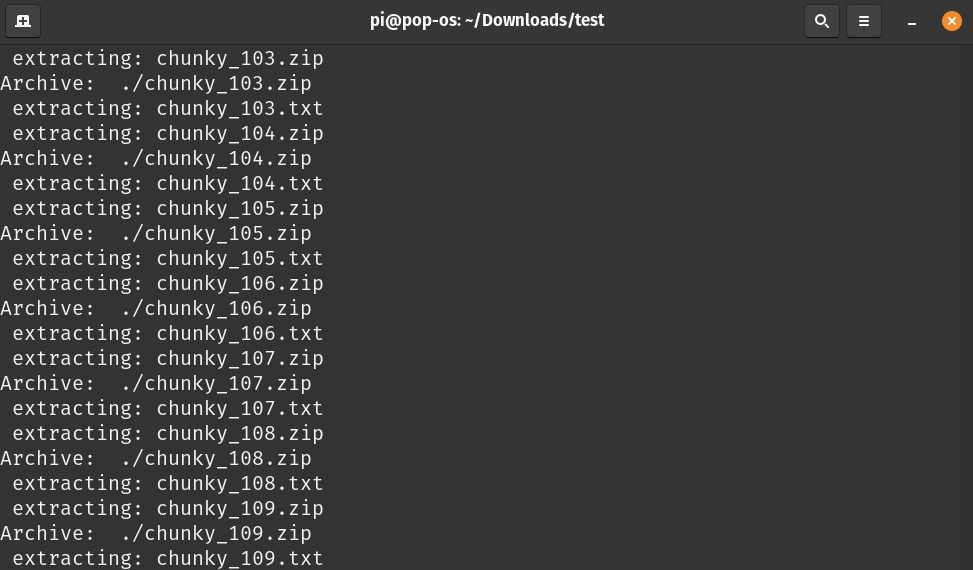
Now once we extracted every zip within the zip. We had a list of empty text files each with name chunky_numeric values.
Now we had that many text files we couldn’t just go and start opening every one of them manually. As all of them were empty, and our guess was one of the text files must have something. So we decided to automate this process using bash script. First, we open all txt files and only show the ones that have strings in it.
#!/bin/bash
# Loop through all .txt files
for file in *.txt; do
# Check if the file is not empty or only whitespace
if [ -s "$file" ] && [ "$(tr -d '[:space:]' < "$file")" ]; then
echo "Contents of $file:"
cat "$file"
echo ""
fi
done
Using this, we found that the text file named chunky_69.text had something in it as shown below.
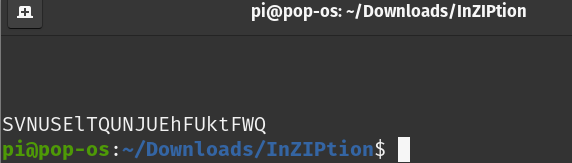
It’s a base64 encoded, upon decoding it we found this ISTHISACIPHERKEY
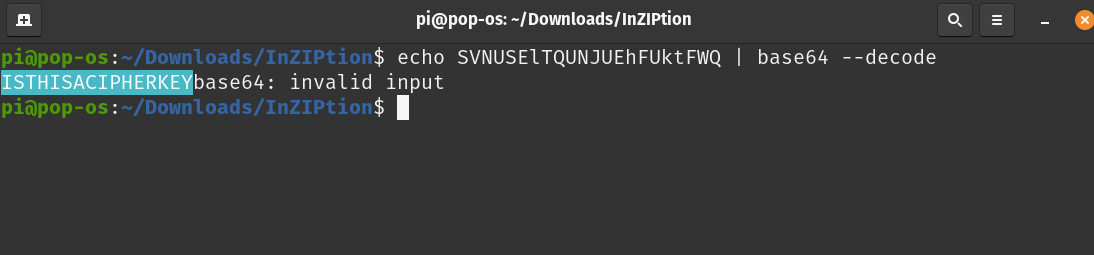
There was also a single rar file which was password protected. So as written in the starting hint text file, we have the encrypted rar file. But what now? We had no other clues and the only way to get that encrypted rar file opened was either using the password or just by brute-forcing. So my other teammate, Rabindra Man Bajracharya started brute-forcing it using John Ripper with the latest rockyou file.

While my other teammate was brute-forcing the rar file, I started looking for the clues. After moving around and going through the files multiple times, I discovered something strange. First of all, from the beginning, I was interested to know why they named the text files chunky each with ascending numeric values. I started reasoning that it must be on purpose and there must be something about it. In computer science terminology, chunky as in chunks can mean many things.
Another thing that I found interesting was each text file had a different number of newlines. So it was not empty after all, just empty new line spaces. The first chunky_0.txt had 52 new line spaces.
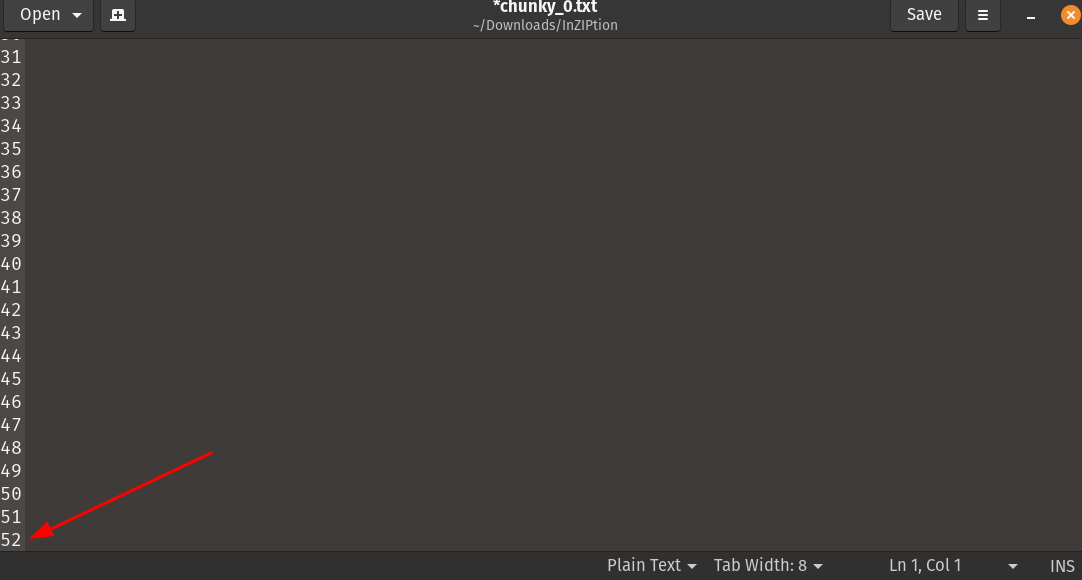
Also at the same time I was playing around with the encrypted rar file. I tried looking into it by opening it in a hex viewer thinking I might find something interesting, maybe a header info hidden in the rar.
Then it somehow clicked. The hex values I saw on the viewer and the number of new lines of each text file started looking like chunks of data. Our initial thought was to get the new line space count of all text files, convert those numeric values in hex, and make a rar file out of it. But it didn’t work out, so we tried converting the hex value into ASCII thinking there might be something interesting.
First, we used automation to get the new line counts of all the text files and store them on a text file in an ascending order following the numeric naming of the texts.
#!/bin/bash
# Output file
output_file="line_counts.txt"
# Clear the output file if it exists
> "$output_file"
# Loop through files, sort by numeric part of the filename
for file in $(ls chunky_*.txt | sort -t'_' -k2,2n); do
# Check if the file exists and is readable
if [[ -f "$file" ]]; then
# Count the number of lines in the file
line_count=$(wc -l < "$file")
# Output the file name and line count to the output file
echo "$line_count" >> "$output_file"
fi
done
echo "Line counts written to $output_file"
Then we converted each word count into hexadecimal values by automating it using bash script.
#!/bin/bash
# Input file with decimal line counts
input_file="line_counts.txt"
# Output file with hexadecimal line counts
output_file="line_counts_hex.txt"
# Clear the output file if it exists
> "$output_file"
# Read each line from the input file
while IFS= read -r line; do
# Extract the filename and line count (assuming format: "filename: count")
filename=$(echo "$line" | cut -d':' -f1)
line_count=$(echo "$line" | cut -d':' -f2 | xargs) # Remove any leading/trailing spaces
# Convert the line count to hexadecimal
hex_count=$(printf "%X\n" "$line_count")
# Write the filename and hexadecimal line count to the output file
echo "$hex_count" >> "$output_file"
done < "$input_file"
echo "Hexadecimal conversion complete. Output written to $output_file"
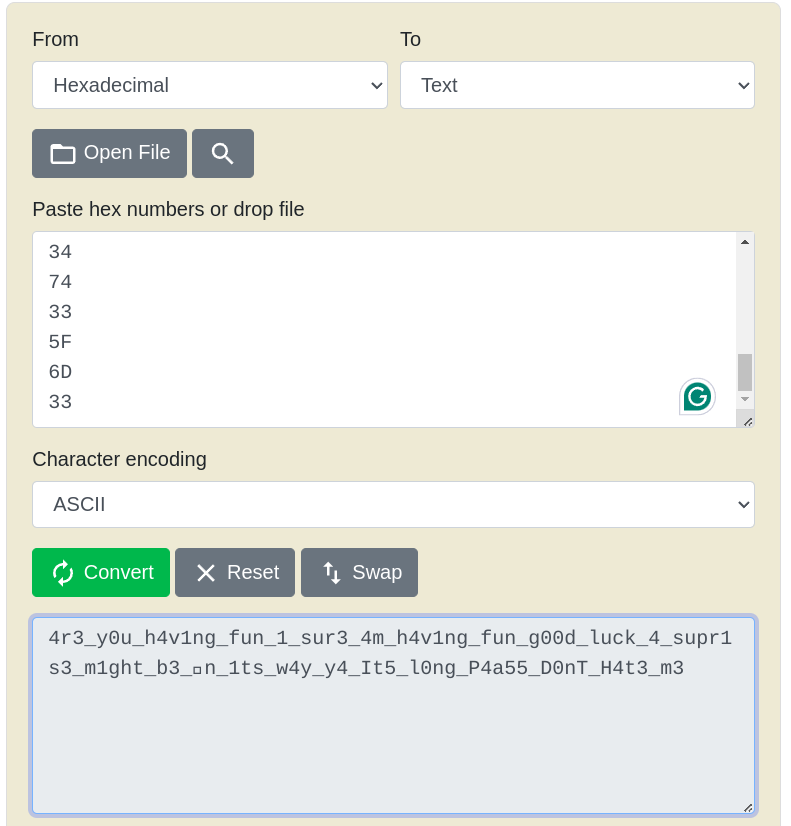
Now we had the hex values and the only thing left for us was to convert it into ASCII.
And there it was, our another clue to the flag.4r3_y0u_h4v1ng_fun_1_sur3_4m_h4v1ng_fun_g00d_luck_4_supr1s3_m1ght_b3_1n_1ts_w4y_y4_It5_l0ng_P4a55_D0nT_H4t3_m3
So, our first thought was it must be the password for the encrypted rar and we were correct. Upon unlocking the encrypted rar file we got a new text file that had what seemed like a flag and it also seemed like it was encrypted in some way. So, we immediately remembered the base64 cipher key we found on the chunky_69 text file.
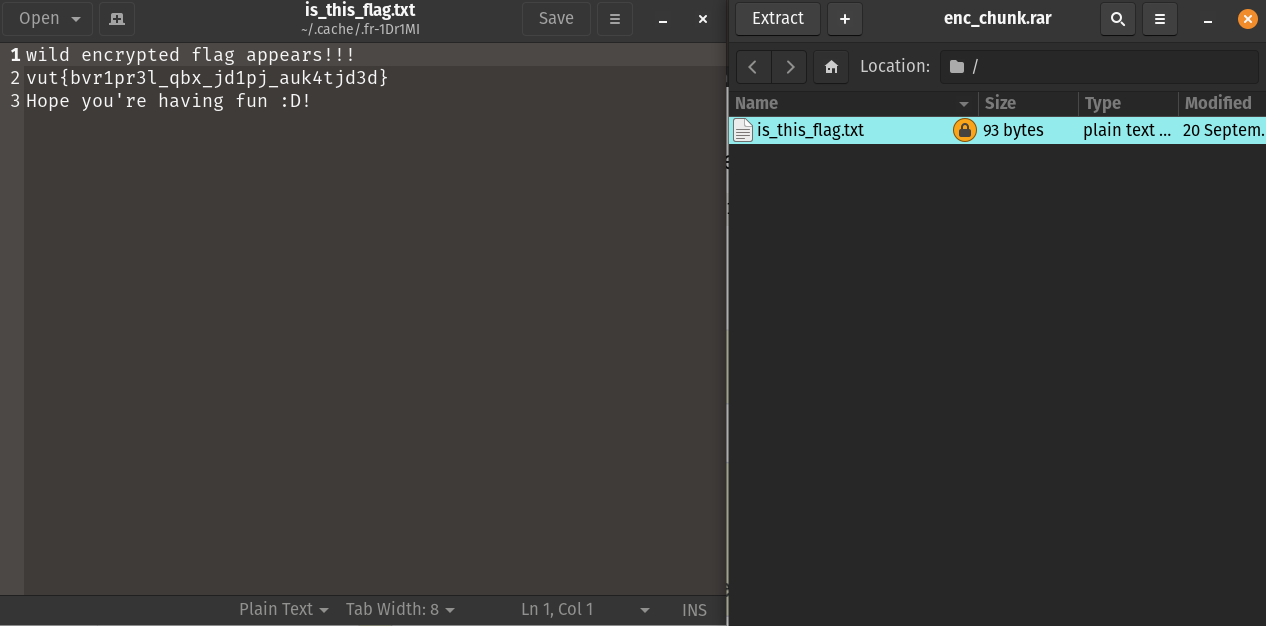
Now only thing left was to figure out what cipher was used to encrypt this. Surprisingly, with a simple prompt by giving the Cipher Key and the Cipher text in the ChatGPT, we were able to find out about the cipher name. It was Vigenère cipher.
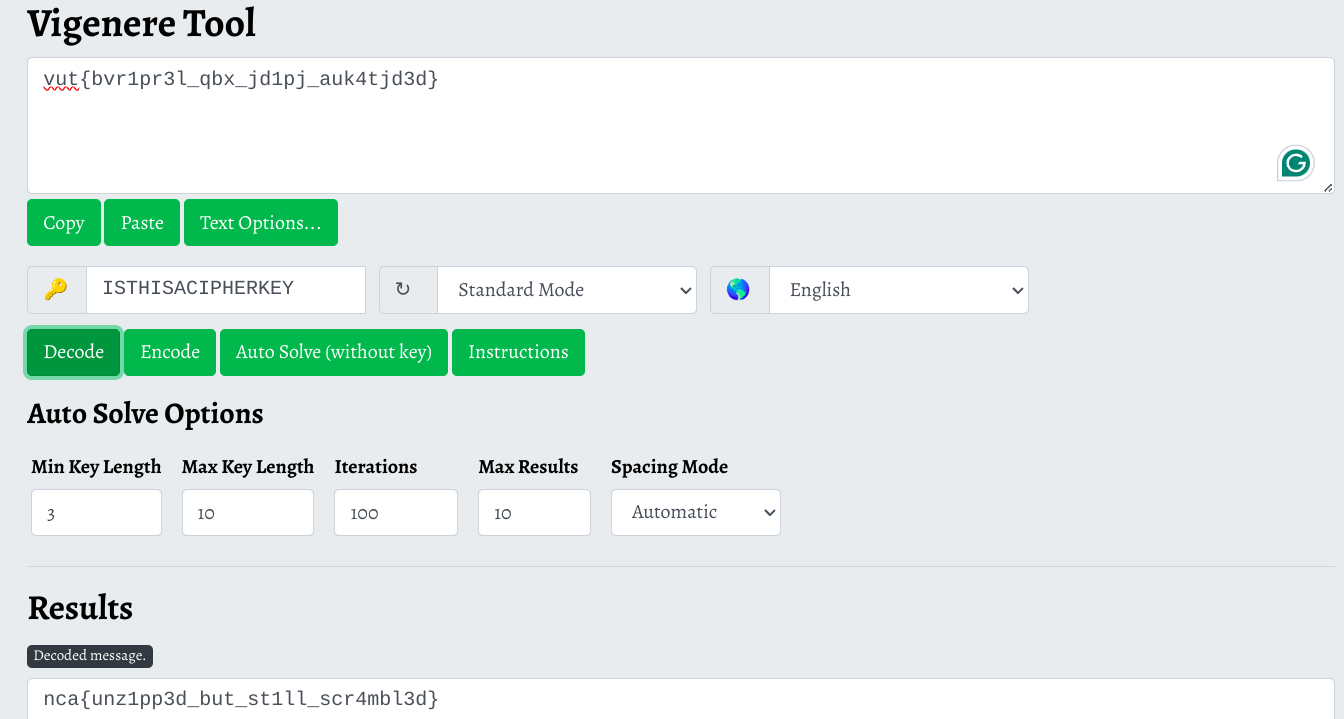
And there we have it. The flag was nca{unz1pp3d_but_st1ll_scr4mbl3d} .
A big thanks to the NCA Team for creating such fun challenges.
Subscribe to my newsletter
Read articles from Bimal Dhital directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Bimal Dhital
Bimal Dhital
A guy with a keen interest in computer networks, software development, web technologies, embedded systems, and programming. When I am bored you can find me bingeing anime series, reading novels, and tinkering with hardware and software.