Enhancing Linux DevSecOps with AI for Vulnerability Management and Compliance
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
Welcome to the second part of my Linux series, where we take a deep dive into AI-powered vulnerability management and compliance auditing. In the previous installment, we explored the fundamentals of securing Linux environments, but now it's time to tackle vulnerabilities head-on with cutting-edge AI.
In today’s fast-paced digital environment, Linux systems are foundational to DevSecOps workflows. Securing them requires a sophisticated, automated approach, leveraging AI to enhance vulnerability management and compliance auditing. AI-driven systems can continuously scan Linux environments, prioritize vulnerabilities based on risk, automate patching, and ensure compliance with regulations like GDPR, HIPAA, and PCI-DSS.
This article presents a step-by-step guide to implementing AI-powered vulnerability management and compliance auditing in your DevSecOps pipeline, with code examples and real-world integration.
Real-World Example: Financial Institution with Critical Linux Infrastructure
A major financial institution operates hundreds of Linux servers hosting critical applications. Managing vulnerabilities and ensuring compliance with GDPR is a significant challenge due to the complexity and scale of the environment. By deploying AI-powered Tenable.io and Wazuh, the institution automates vulnerability scanning, prioritizes patches based on risk, and ensures compliance through continuous audits. Incidents, like attempts to exploit kernel vulnerabilities, are detected in real-time, and compromised systems are isolated automatically — ensuring business continuity and regulatory compliance.
Architecture Overview
The AI-powered vulnerability management and compliance auditing system integrates directly into your CI/CD pipeline, continuously scanning Linux systems, auditing compliance, and responding to threats in real-time.
Below are the architectural diagrams and there breakdowns:
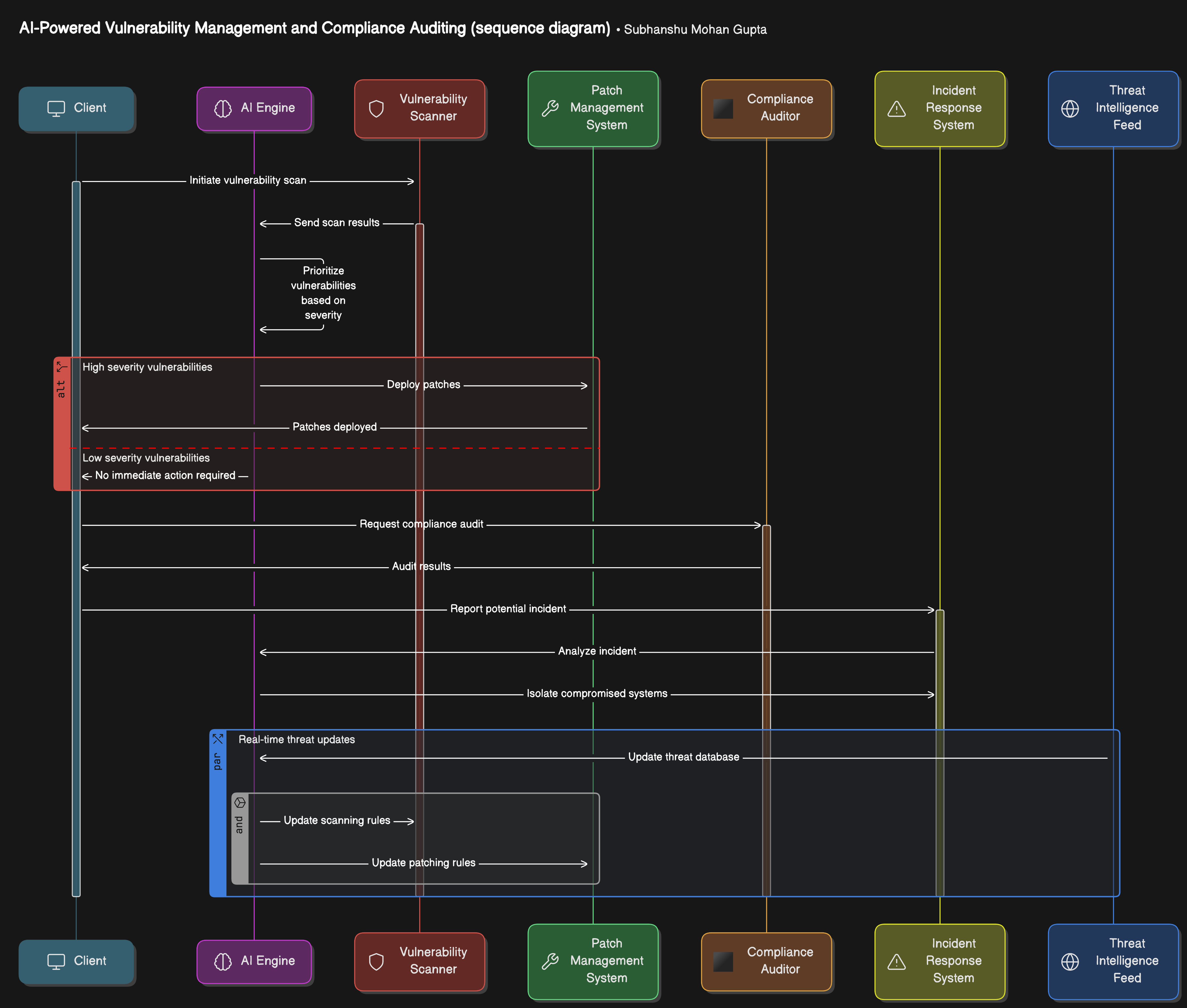
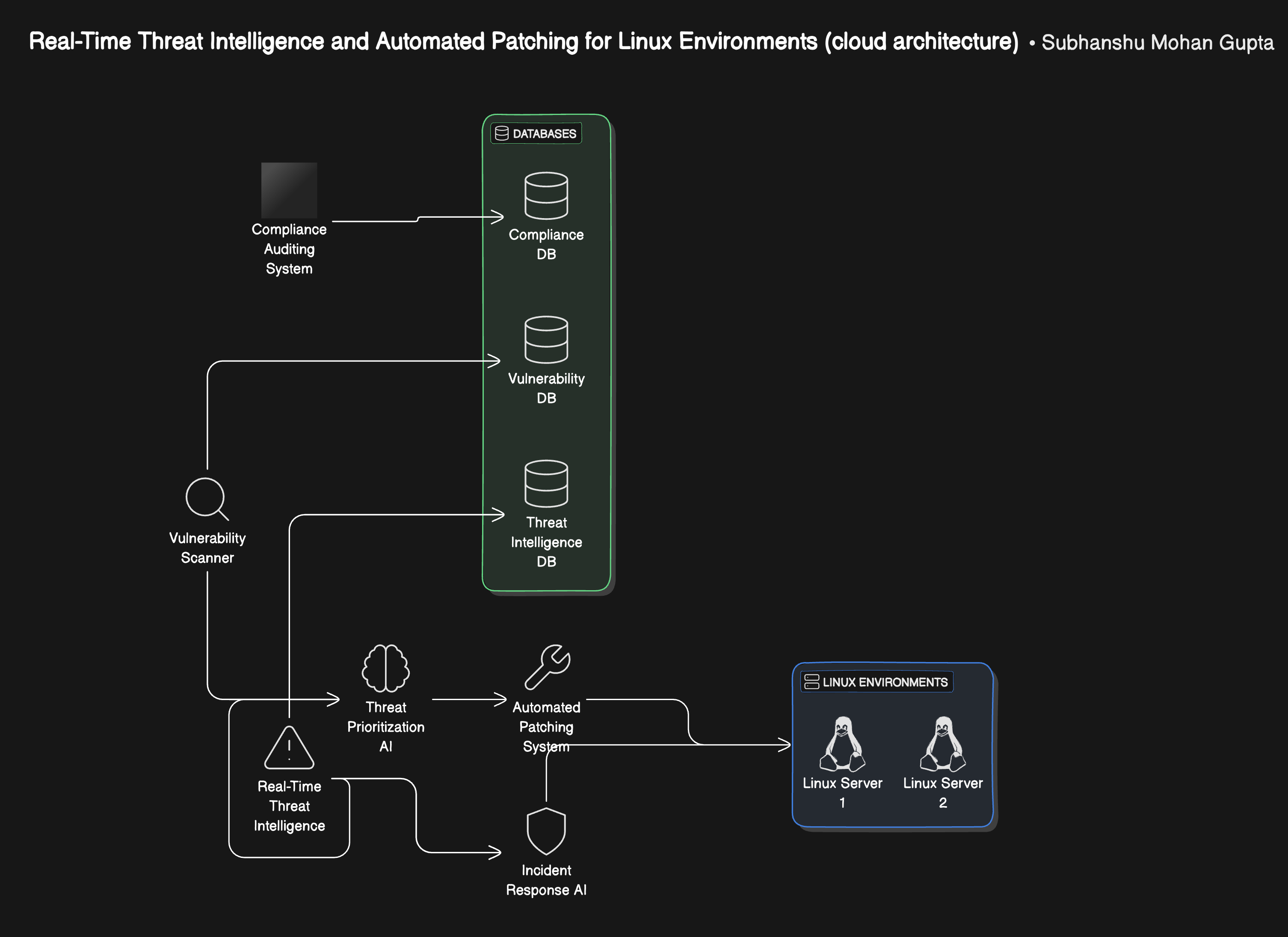
Vulnerability Scanning: Continuous scanning of Linux environments for vulnerabilities.
Threat Prioritization: AI prioritizes vulnerabilities based on severity.
Automated Patching: Automatically deploy patches to mitigate risks.
Compliance Auditing: Real-time auditing against compliance standards.
Incident Response: AI detects and isolates compromised systems in response to exploits.
Real-Time Threat Intelligence: Automated updates based on the latest threat feeds.
Step-by-Step Guide for Implementation
1. Setting Up the Environment
Start by setting up the necessary tools to scan and audit your Linux infrastructure. Here’s a sample setup using Docker and Tenable.io, an AI-powered vulnerability scanner, integrated with Wazuh for compliance auditing.
Tenable.io: Vulnerability scanning and management.
Wazuh: AI-powered monitoring, compliance, and incident response.
Step 1.1: Installing Docker and Docker Compose
Ensure your Linux system has Docker installed. If not, install Docker and Docker Compose:
# Install Docker
sudo apt-get update
sudo apt-get install -y docker.io
# Install Docker Compose
sudo apt-get install -y docker-compose
# Start and enable Docker
sudo systemctl start docker
sudo systemctl enable docker
2. Deploying Tenable.io for AI-Driven Vulnerability Scanning
Step 2.1: Configuring Tenable.io for Continuous Vulnerability Scanning
To scan for vulnerabilities, you’ll need to deploy a Tenable.io agent on your Linux environment. The agent continuously scans and sends data back to Tenable’s AI engine for threat prioritization.
# Install Tenable agent
wget https://downloads.nessus.org/nessusagent/downloads/tenable-agent.deb
sudo dpkg -i tenable-agent.deb
# Link Tenable agent to your Tenable.io account
sudo /opt/nessus_agent/sbin/nessuscli agent link --key=<YOUR_TENABLE_IO_ACTIVATION_KEY> \
--host=<TENABLE_IO_HOST> --port=443
# Start the agent
sudo systemctl start nessusagent
sudo systemctl enable nessusagent
Once deployed, the Tenable agent will continuously scan the Linux system for vulnerabilities and feed the information into the Tenable.io dashboard.
Step 2.2: Automating Vulnerability Scanning
Configure a continuous scan job in the Tenable.io interface. Ensure that Tenable.io updates with the latest threat intelligence feeds and runs scans regularly. Enable notifications for critical vulnerabilities.
3. Automated Patching with Ansible
AI-powered systems prioritize patches based on risk, and Ansible can automate the patching process.
Step 3.1: Installing Ansible
Install Ansible to automate patch deployments:
sudo apt update
sudo apt install ansible -y
Step 3.2: Creating an Ansible Playbook for Patching
Create a playbook that automatically applies patches to your Linux systems:
---
- hosts: all
become: true
tasks:
- name: Update all packages to the latest version
apt:
upgrade: dist
update_cache: yes
cache_valid_time: 3600
- name: Reboot the server if needed
reboot:
msg: "Rebooting to apply patches"
connect_timeout: 5
reboot_timeout: 600
Run this playbook whenever critical vulnerabilities are detected:
ansible-playbook patch-management.yml -i inventory
Step 3.3: Scheduling Automatic Patching
You can use cron jobs to run the playbook periodically:
crontab -e
# Add the following line to run the playbook every day at midnight
0 0 * * * ansible-playbook /path/to/patch-management.yml -i /path/to/inventory
4. Compliance Auditing with Wazuh
Wazuh provides real-time compliance auditing, monitoring your Linux systems for compliance with security standards (GDPR, HIPAA, PCI-DSS). It also helps with threat detection and incident response.
Step 4.1: Installing Wazuh
Install Wazuh for real-time monitoring and auditing:
# Download and install Wazuh
curl -s https://packages.wazuh.com/install | bash
Step 4.2: Configuring Compliance Auditing
Configure Wazuh to audit your system against specific compliance standards:
# Add compliance auditing to the Wazuh agent config
sudo nano /var/ossec/etc/ossec.conf
# Example config for PCI-DSS auditing
<rootcheck>
<compliance>
<enabled>yes</enabled>
<policy>PCI-DSS</policy>
</compliance>
</rootcheck>
Wazuh will now audit the Linux environment and report any non-compliance. Real-time alerts are generated, and remediation suggestions are provided automatically.
5. Automated Incident Response
Wazuh’s AI-powered engine can automatically detect suspicious activity, such as attempts to exploit vulnerabilities, and respond in real-time.
Step 5.1: Configuring Automated Incident Response
Enable automated incident response for Wazuh:
# Edit the Wazuh configuration file to enable automatic response
sudo nano /var/ossec/etc/ossec.conf
# Configure active response for isolating compromised systems
<active-response>
<command>disable-network</command>
<location>all</location>
</active-response>
In case of an exploit, the system will automatically quarantine the compromised machine by disabling its network access.
6. Integrating AI-Driven Vulnerability Management into DevSecOps Pipelines
To integrate AI-based vulnerability management and compliance auditing into your CI/CD pipeline, tools like Jenkins can trigger scans and compliance audits as part of the build process.
Step 6.1: Setting Up Jenkins Pipeline
Configure your Jenkins pipeline to run Tenable scans and Wazuh compliance checks after each deployment:
pipeline {
agent any
stages {
stage('Scan for Vulnerabilities') {
steps {
sh 'tenablecli scan start --target <SERVER_IP>'
}
}
stage('Run Compliance Audit') {
steps {
sh 'wazuh-agent-cli --check-compliance --standard PCI-DSS'
}
}
stage('Deploy Application') {
steps {
// Deploy your application
}
}
}
}
Conclusion
Implementing AI-powered vulnerability management and compliance auditing for Linux systems in DevSecOps provides enhanced security, automation, and real-time threat response. By integrating AI with existing tools like Tenable, Ansible, and Wazuh, organizations can significantly reduce their exposure to risks, automate compliance processes, and ensure the integrity of their Linux environments.
This approach not only strengthens security but also improves operational efficiency, freeing DevSecOps teams to focus on innovation.
Feel free to subscribe my newsletter and follow me on LinkedIn.
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.