Computer Networking Essentials for DevOps: A Simple Guide to Key Concepts, Protocols, and Layers
 Om Suple
Om SupleTable of contents
- What is a Computer Network?
- What is the World Wide Web?
- Network Architectures
- Why Do We Need Network Protocols?
- IP Addresses: Identifying Devices
- OSI and TCP/IP Models
- Network Topologies: How Devices are Connected
- HTTP Methods and Status Codes
- Cookies: How Websites Remember You
- How Email Works: SMTP, POP3, and IMAP
- DNS: Domain Name System
- Transport Layer: Moving Data Between Devices
- IPv6: The Future of IP Addresses
- Firewalls: Securing Your Network
- Network Address Translation (NAT)
- Data Link Layer: Sending Data Between Devices
- Conclusion: Networking Knowledge Essential for DevOps
- References
If you’re on the path to becoming a DevOps engineer, having a solid understanding of computer networking is crucial. This guide provides just the right amount of information you’ll need to understand the networking concepts required for a DevOps roadmap. From protocols to the OSI model and network architecture, you’ll have the necessary tools to navigate the world of networking confidently.
What is a Computer Network?
A computer network is a group of computers connected together to share data and resources. The best example is the internet, which connects millions of computers worldwide.
What is the World Wide Web?
The World Wide Web (WWW) is a collection of web pages stored on servers, which you can access through the internet. Every web page has a unique address called a URL (Uniform Resource Locator), and hyperlinks help you move from one page to another.
Network Architectures
1. Client-Server Architecture
In a client-server architecture, the server is the computer that provides services, like hosting a website, and the client is the computer (or user) that requests these services. For example, when you type a web address into your browser, your browser (the client) sends a request to the server that hosts the website, and the server sends the web page back to your browser.
2. Peer-to-Peer (P2P) Architecture
In a peer-to-peer (P2P) architecture, there’s no central server. Instead, every computer (or "peer") can share files directly with other computers. This system is common in file-sharing networks like torrenting.
Why Do We Need Network Protocols?
Protocols are like rules that computers follow to communicate with each other. Some important ones include:
TCP (Transmission Control Protocol): Ensures data is sent without errors.
UDP (User Datagram Protocol): Faster but doesn’t guarantee data will arrive without errors. Used for video calls or streaming where speed is more important.
HTTP (Hypertext Transfer Protocol): The protocol used for browsing websites.
FTP (File Transfer Protocol): For transferring files between computers.
SMTP (Simple Mail Transfer Protocol): Used for sending emails.
SSH (Secure Shell): Secure remote access to another computer.
IP Addresses: Identifying Devices
Every device on a network has a unique IP address, which acts like a home address for your device so other devices know where to send data. You can find your IP address using command [curl ifconfig.me] .
Your ISP (Internet Service Provider) gives your devices local IP addresses using DHCP (Dynamic Host Configuration Protocol).
OSI and TCP/IP Models
These are two ways of organizing how data travels through a network.
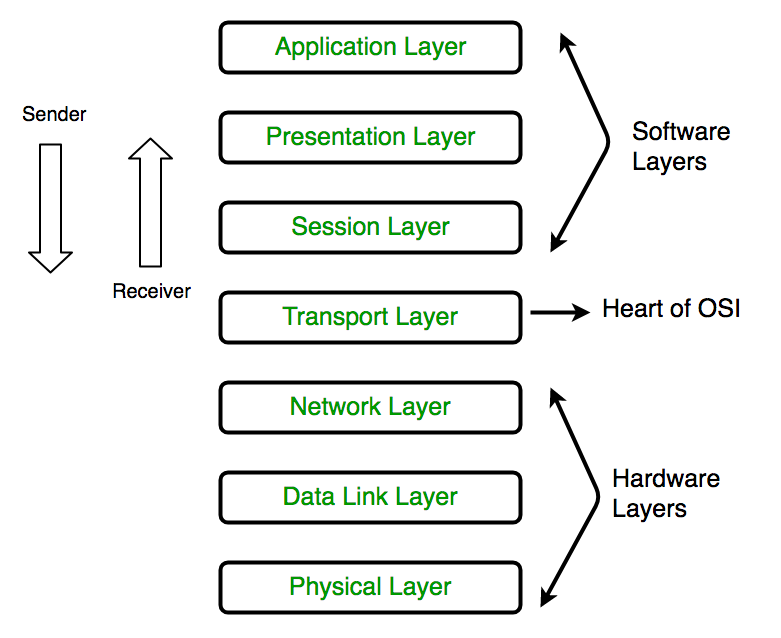
OSI Model
The OSI model has seven layers that explain how data moves from one device to another:
Application Layer: Handles apps like browsers.
Presentation Layer: Converts data into a readable format.
Session Layer: Manages communication between devices.
Transport Layer: Makes sure data gets sent correctly (using TCP or UDP).
Network Layer: Directs data between different networks.
Data Link Layer: Deals with data transfer between two devices on the same network.
Physical Layer: Deals with cables and hardware.
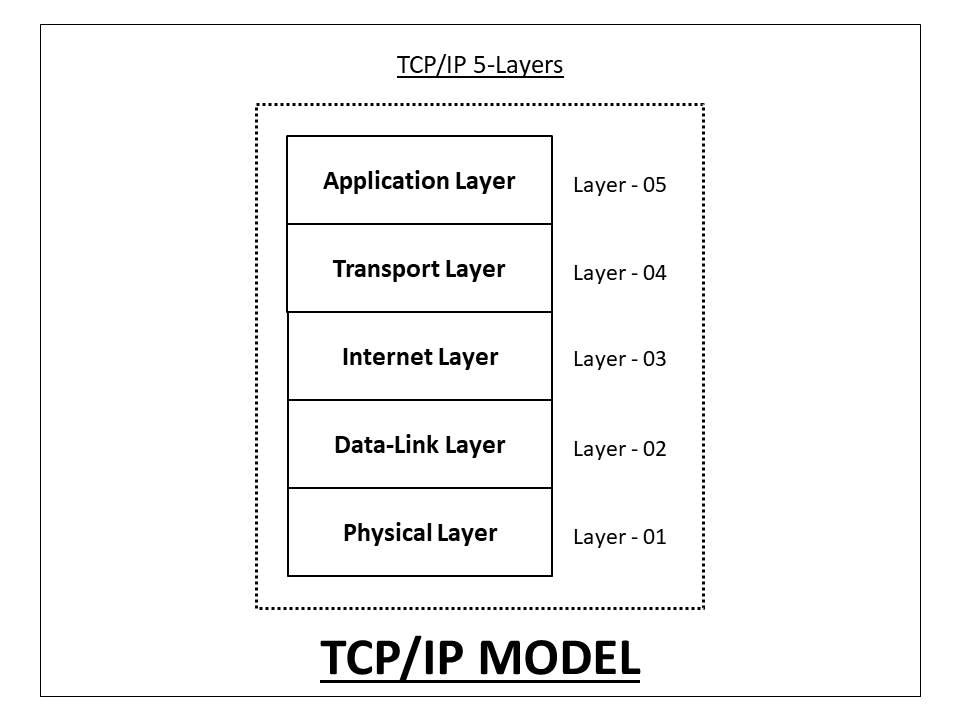
TCP/IP Model
The TCP/IP model is a simpler version of the OSI model. It has five layers:
Application Layer
Transport Layer
Network Layer
Data Link Layer
Physical Layer
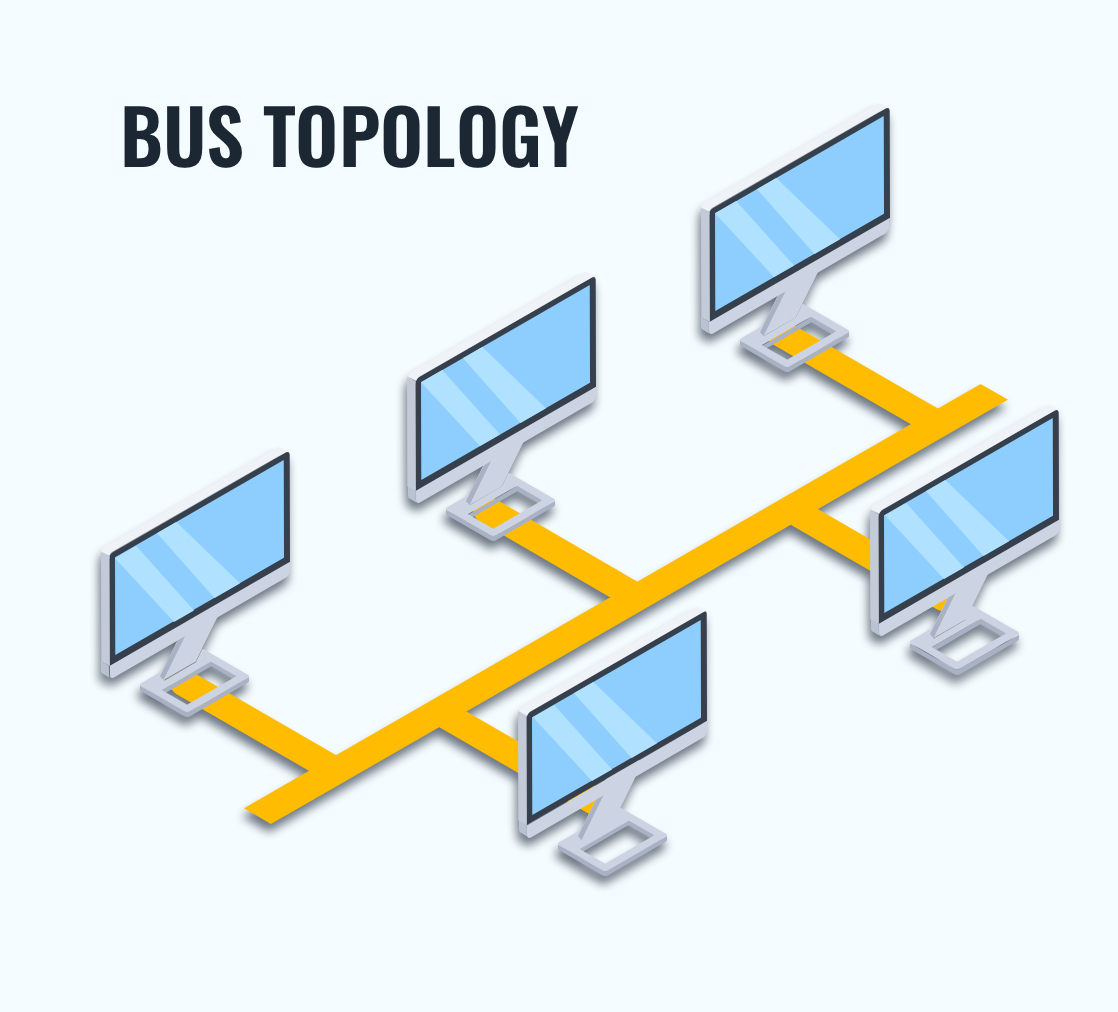
Network Topologies: How Devices are Connected
Network topology refers to the way devices are arranged in a network. Some common types include:
Bus Topology: All devices share the same communication line.
Ring Topology: Devices form a loop and data flows in one direction.

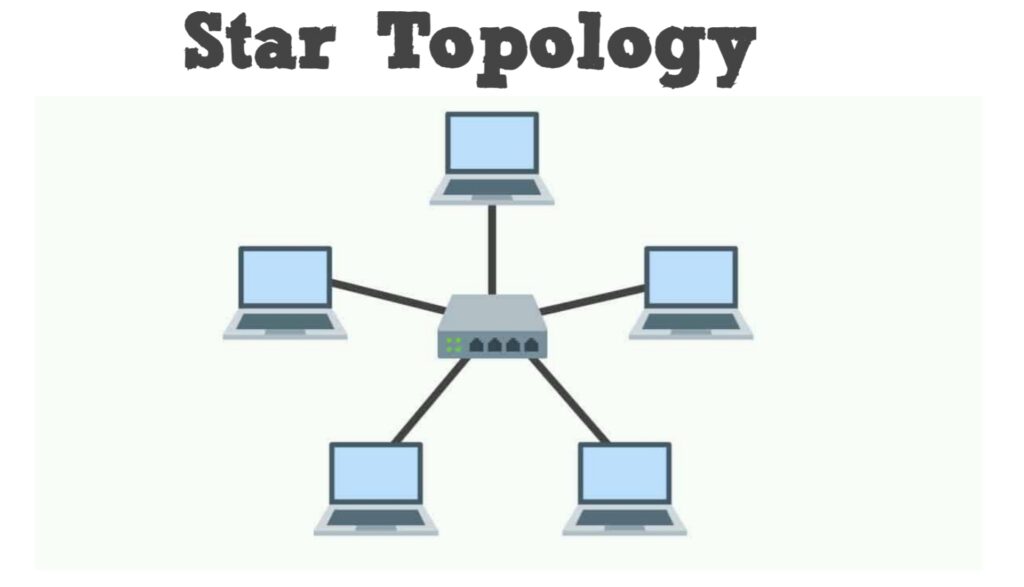
Star Topology: Devices connect to a central hub.
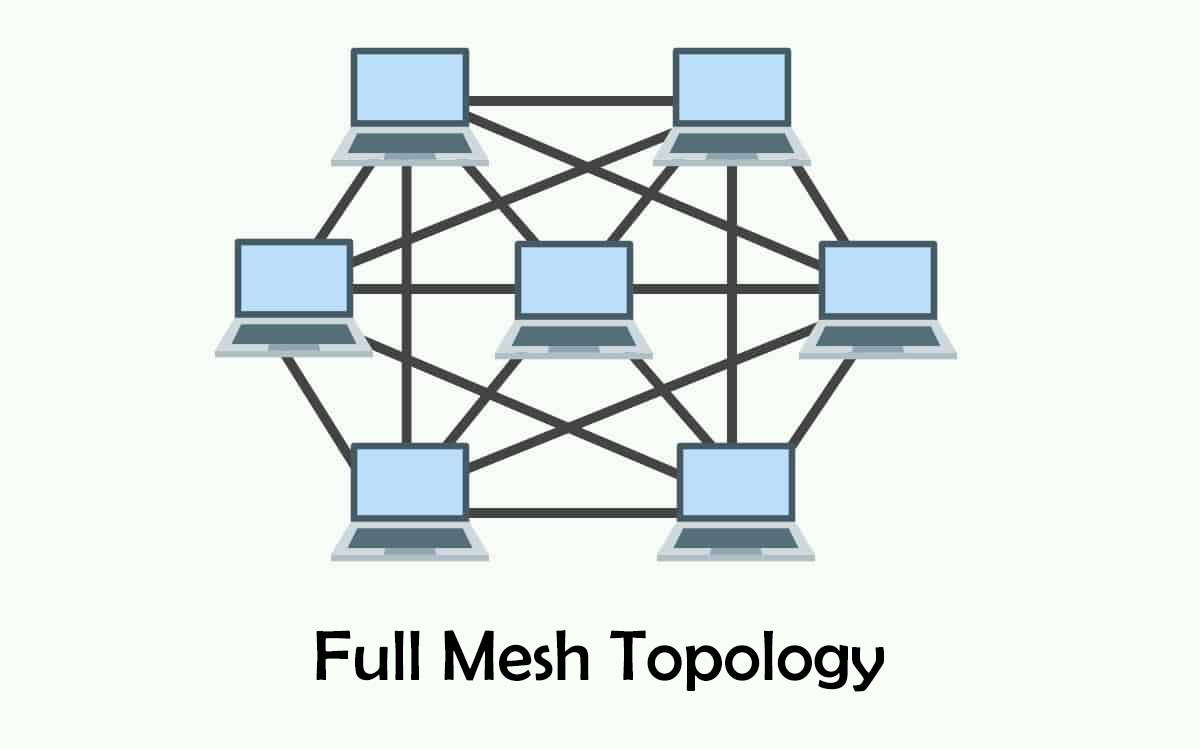
Mesh Topology: Every device is connected to every other device.
HTTP Methods and Status Codes
When you visit a website, you are making a request to the server. These requests follow HTTP methods:
GET: Request data from a server.
POST: Send data to the server (like filling out a form).
PUT: Update data on the server.
DELETE: Remove data from the server.
HTTP Status Codes tell you if your request worked or not:
200: Success.
404: Page not found.
400: Bad request.
500: Server error.
Cookies: How Websites Remember You
Cookies are small files stored on your browser to help websites remember your preferences or login details. Cookies are critical for login sessions and maintaining user preferences. There are:
First-party cookies: Set by the website you visit.
Third-party cookies: Set by other websites, usually for advertising.
How Email Works: SMTP, POP3, and IMAP
SMTP (Simple Mail Transfer Protocol): Sends emails.
POP3 (Post Office Protocol): Downloads emails from the server to your device and removes them from the server.
IMAP (Internet Message Access Protocol): Lets you access emails on multiple devices without deleting them from the server.
DNS: Domain Name System
The DNS (Domain Name System) converts easy-to-remember website addresses (like google.com) into IP addresses that computers use to find the website.
Transport Layer: Moving Data Between Devices
The Transport Layer is responsible for getting data from one device to another. It can:
Multiplex: Combine several data streams into one.
Demultiplex: Separate data into multiple streams.
It also handles flow control to make sure data doesn’t overwhelm the receiving device.
TCP vs. UDP
TCP: Reliable but slower, used for email or web browsing.
UDP: Faster but less reliable, used for video streaming or online games.
IPv6: The Future of IP Addresses
As the number of devices on the internet grows, we’re moving from IPv4 to IPv6. IPv4 uses 32-bit addresses, while IPv6 uses 128-bit addresses, allowing for many more devices to be connected.
Cons of IPv6:
Not compatible with older systems (requires new hardware).
Requires changes to the existing infrastructure.
Firewalls: Securing Your Network
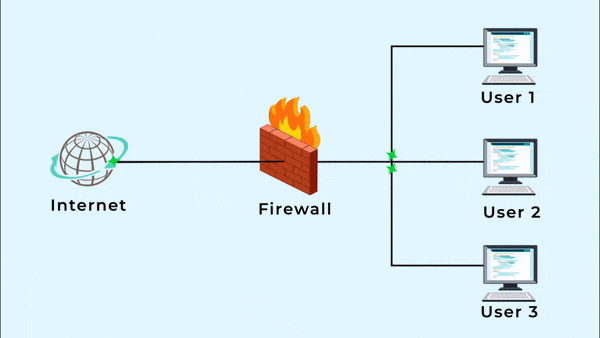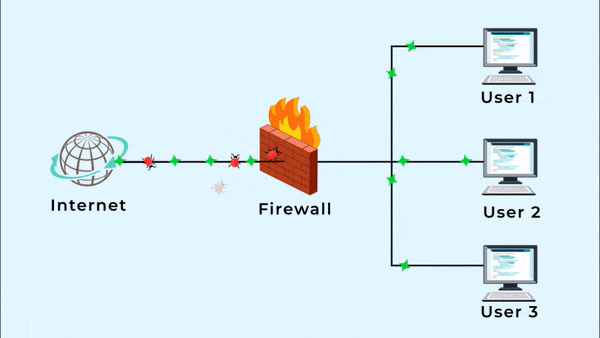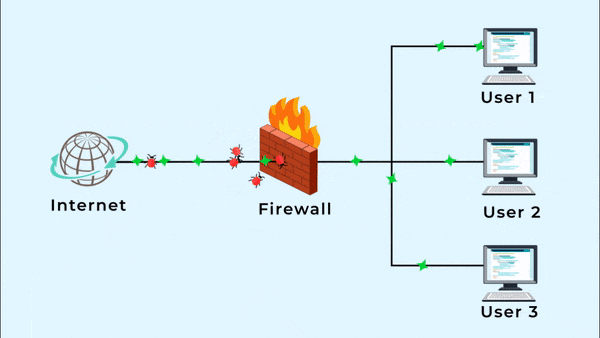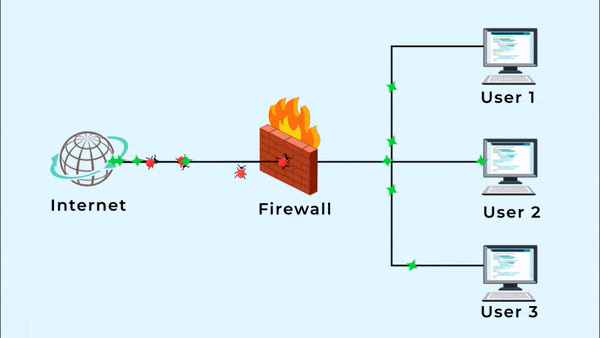
A firewall is a security tool that controls incoming and outgoing network traffic based on rules. Firewalls can block traffic based on:
IP addresses
Port numbers
Protocols
There are two types of firewalls:
Stateless: Checks each packet of data individually.
Stateful: Keeps track of ongoing connections and is more efficient.
Network Address Translation (NAT)

NAT (Network Address Translation) helps multiple devices on a local network share a single public IP address. It also adds a layer of security by hiding the internal network structure.
Data Link Layer: Sending Data Between Devices
The Data Link Layer is responsible for transferring data between devices on the same network. It uses MAC addresses (a unique hardware identifier) to make sure data gets to the right place.
Conclusion: Networking Knowledge Essential for DevOps
For anyone on the path to becoming a DevOps engineer, understanding these key networking concepts is both necessary and sufficient. From learning about how devices communicate to securing networks with firewalls, this foundational knowledge is essential for managing modern infrastructure.
Mastering these basics will help you confidently navigate network management, troubleshoot issues, and design scalable, reliable systems — skills that are vital in the DevOps world.
References
Much of the content in this article was inspired by the excellent YouTube video "Computer Networking Full Course - OSI Model Deep Dive with Real Life Examples" by Kunal Kushwaha. The video provides a deep dive into computer networking, explaining key concepts like the OSI model, TCP/IP protocols, and network architecture in a way that’s easy to understand. I highly recommend watching the full video here https://youtu.be/IPvYjXCsTg8?feature=shared.
Subscribe to my newsletter
Read articles from Om Suple directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Om Suple
Om Suple
I'm a budding DevOps engineer focused on cloud technologies and automation. I love diving into new tools and techniques to streamline cloud infrastructure and enhance system performance. Passionate about continuous learning, I enjoy writing about my experiences and connecting with fellow developers to share insights and grow in the ever-evolving tech landscape. Join me as I explore the world of DevOps and cloud engineering!