Introduction to Sealed Secrets in Kubernetes
 Anshu Kumar
Anshu Kumar
Need of Sealed Secrets
Kubernetes Secrets and the Problem
Kubernetes Secrets store sensitive data, but they use base64 encoding, not encryption. This leaves them vulnerable if stored in GitHub, making them easily decodable.
Why Encryption is Needed
To secure secrets in GitHub, encryption is necessary to prevent exposure. Tools like Sealed Secrets encrypt secrets, making them safe for version control and ensuring only the cluster can decrypt them.
Sealed Secrets and its Components
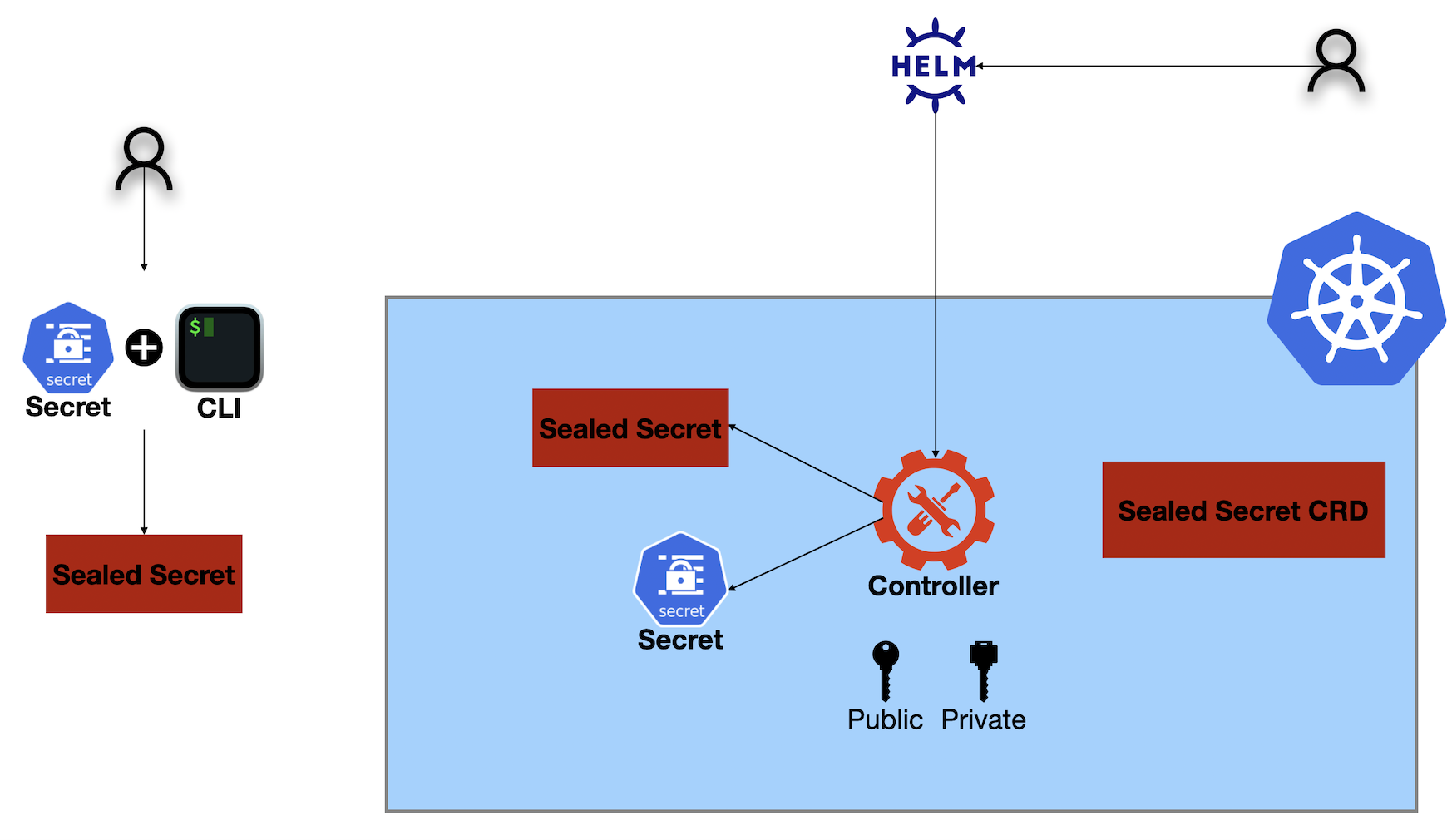
Sealed Secrets are encrypted Kubernetes Secrets that can be safely stored in Git. Only the Sealed Secrets Controller in the cluster can decrypt them, ensuring security during deployments.
Controller
Runs in the Kubernetes cluster, responsible for decrypting the Sealed Secrets and creating regular Kubernetes Secrets.
CLI
A command-line tool used to encrypt secrets into Sealed Secrets, which can then be safely stored in version control.
CRD
Defines a SealedSecret as a Kubernetes resource. This allows Kubernetes to treat Sealed Secrets as native objects, which the controller will decrypt into regular Secrets during deployment.
Working of Sealed Secrets
Deploying the Controller
First, Install the Sealed Secrets Controller in the Kubernetes cluster. It monitors SealedSecret resources and decrypts them into regular Kubernetes Secrets.
Custom Resource Definition
The SealedSecret is a custom Kubernetes resource defined by a CRD. This allows Kubernetes to recognize SealedSecret objects.
Concept of Keys
The controller uses a key pair (public and private) to handle encryption and decryption. The public key is used to encrypt secrets, and the private key (stored in the cluster) decrypts them.
Converting a Secret to a Sealed Secret
Use the Kubeseal CLI to encrypt a Kubernetes Secret into a SealedSecret. The SealedSecret can be safely stored in Git, as only the cluster can decrypt it.
Secrets in the Cluster
Once a SealedSecret is applied, the controller creates a regular Kubernetes Secret in Kubernetes cluster.
Demo
Prerequisites
Establishing Connection between Kubeseal and Kubernetes Cluster
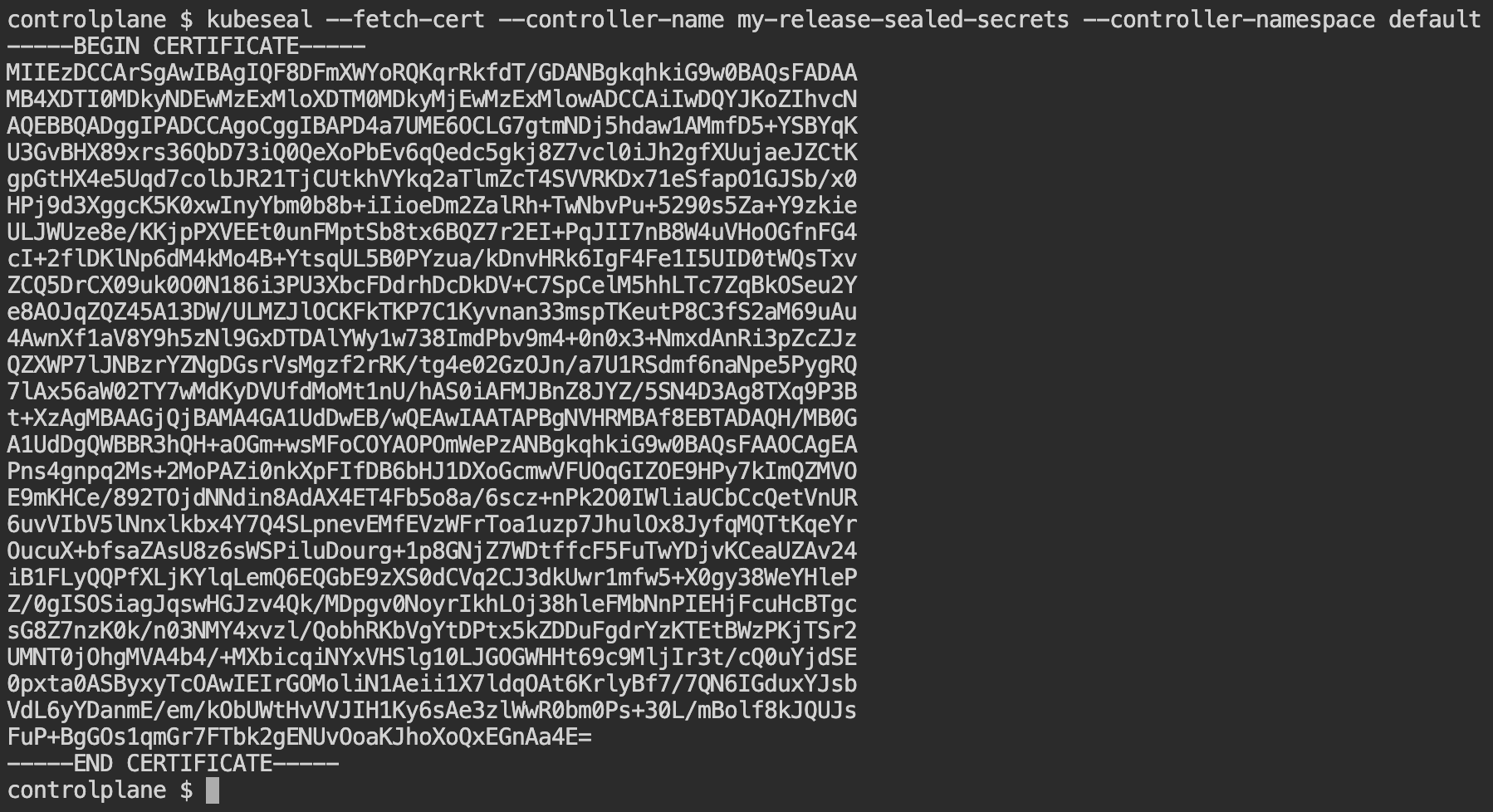
- Run this command to retrieve the public key from the Sealed Secrets Controller in your Kubernetes cluster.
kubeseal --fetch-cert --controller-name <XXX> --controller-namespace <YYY>
Replace XXX with the service name of controller deployed.
Replace YYY with Namespace where controller is deployed.
Create a Secret
- Create secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: my-secret
type: Opaque
data:
username: bXl1c2Vy # base64 encoded value of 'myuser'
password: bXlwYXNzd29yZA== # base64 encoded value of 'mypassword'
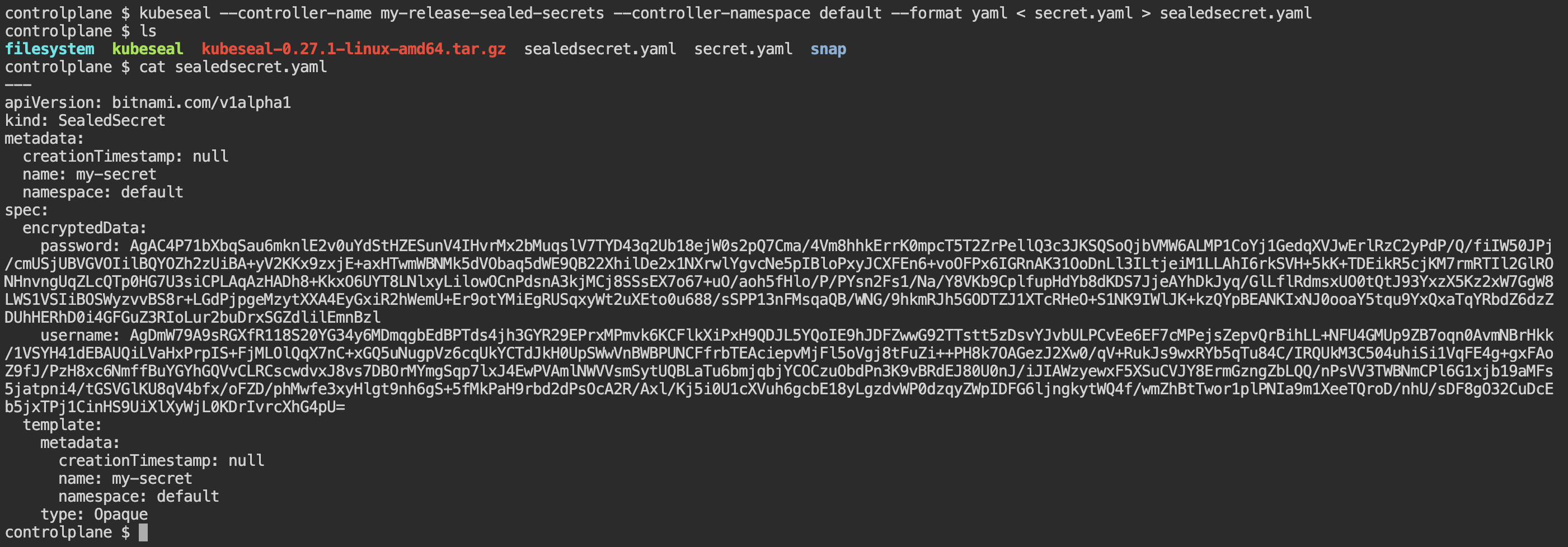
Encrypt the secret
kubeseal --controller-name <XXX> --controller-namespace <YYY> --format yaml < secret.yaml > sealedsecret.yaml
Apply the sealedsecret.yaml
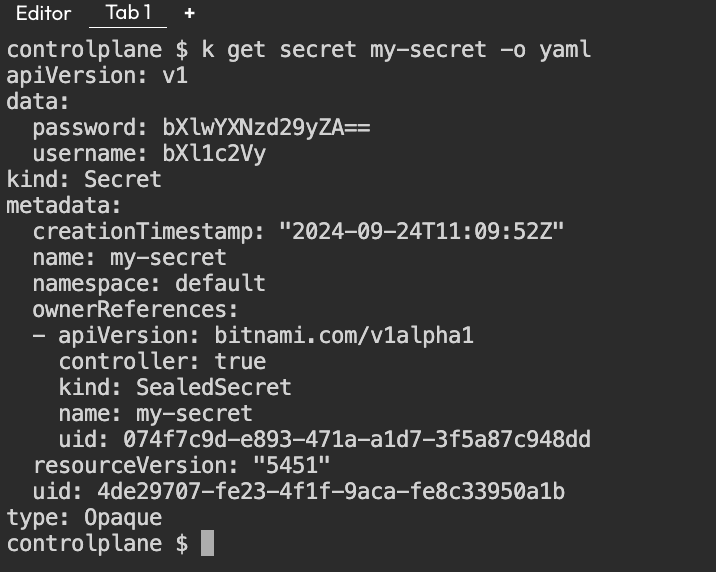
kubectl apply -f sealedsecret.yamlWe can see the regular Kubernetes Secret in Kubernetes cluster.
Subscribe to my newsletter
Read articles from Anshu Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
