Understanding the Difference Between Access Tokens and Refresh Tokens
 Samir Khanal
Samir Khanal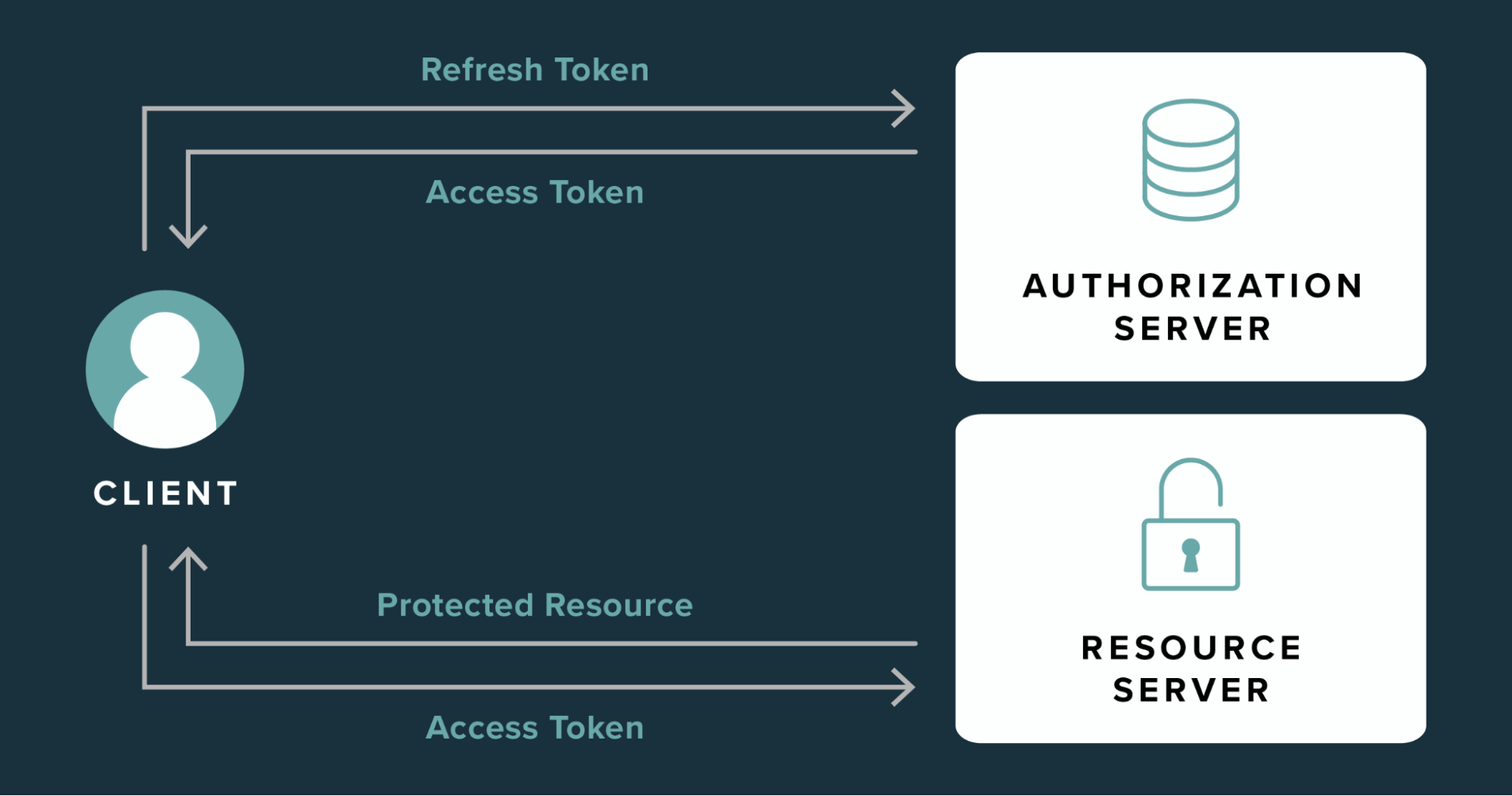
Introduction
Authentication plays a huge role in today’s modern web application. It makes sure that right user is accessing the secured resources which is crucial to prevent any harm to the user’s information. That’s where tokens come in play, mainly Access tokens and Refresh tokens.
In this blog, I’ll explain the differences between these two tokens, why they are needed, and how they work together to provide secure and user-friendly authentication.
What is an Access token?
Access token is short lived token which provides a client ( frontend or mobile apps) permission to access specific resources on behalf of the user. Access token are valid for limited time about 15 minutes or an hour to prevent any danger when the token is compromised. They are included in each request send to server mostly in authorization header as a bearer token. They are moslty in the form of JSON or JWT( JSON Web Token).
Why are they short lived?
Since Access token are ofter send alongside every request in the server, there may be a high risk of them getting stolen via malicious script or network attack. Hence, to prevent any potential damage caused by token theft, we tend to make their life span short.
What is a Refresh Token?
Refresh Tokens are the tokens responsible for generating new Access token after the previous Access token has expired. They usually have long lifespan about day or a week so that the server could generate a new access token without the need of client to frequently login to generate a new access token. They are stored securely mostly in a database entry and are securely sent through cookies by the server. They are not send with every request but only when absolutely necessary (e.g., when refreshing an access token).
Why a Long Lifespan?
A long lifespan allows for user convenience i.e. users won’t have to log in repeatedly, but security risks are minimized because the refresh token is rarely exposed to the client-side or API.
How Do Access and Refresh Tokens Work Together?
Here’s a step-by-step flow of how these tokens typically work:
User logs in:
The authentication server verifies the user’s credentials.
The server issues both an access token and a refresh token.
Access token is used:
The client (browser, mobile app, etc.) uses the access token to make authenticated requests to the API.
The token is passed in the headers with each request.
Access token expires:
- Once the access token expires, the client can no longer make authenticated requests with it.
Refresh token is used:
Instead of asking the user to log in again, the client sends the refresh token to the authentication server.
The server verifies the refresh token and issues a new access token.
Session continuation:
The client uses the new access token to continue making requests.
This process can repeat until the refresh token expires, at which point the user will need to log in again.
Conclusion
Access tokens and refresh tokens play a vital role in modern authentication systems, working together to balance security and user convenience.
Access tokens handle the day-to-day task of making API requests, but they expire quickly to limit any security risks if they’re compromised. On the other hand, refresh tokens act behind the scenes, allowing the system to silently issue new access tokens when the old ones expire, so users don’t have to keep logging in.
By using both, we get the best of both worlds: security through short-lived access tokens and a smoother user experience through longer-lived refresh tokens. Knowing how and when to use these tokens can help you build secure, user-friendly applications that people will appreciate.
Subscribe to my newsletter
Read articles from Samir Khanal directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Samir Khanal
Samir Khanal
My name is Samir Khanal. I am a web development enthusiast, mainly making exicting web apps in JavaScript environment.