Virtualization
 Vedant Singh Chauhan
Vedant Singh Chauhan
"Using virtualization, we can create a lab of multiple computers using a single computer."
The Pre-Virtualization Era
Before virtualization became widespread, organizations faced significant challenges in managing their computing resources:
Each server typically ran a single application or service
Inefficient resource utilization was common
Hardware costs were high
Power consumption was increased
Management and maintenance were complex
This approach, while ensuring isolation between different activities, often resulted in overestimated resource allocation and expensive infrastructure.
What is Virtualization?
Virtualization is a technology that allows you to create multiple simulated environments or dedicated resources from a single physical hardware system. It enables better utilization of hardware resources and provides flexibility in managing computing environments.
Key Components
Host OS: The operating system of the physical machine.
Guest OS: The operating system running inside a virtual machine.
Hypervisor: Software that creates and manages virtual machines.
Snapshot: A point-in-time image of a virtual machine's state.
Types of Hypervisors
Type 1 (Bare-metal): Runs directly on the hardware.
Type 2 (Hosted): Runs on top of a host operating system.
Setting Up Virtualization Manually in Windows
Prerequisites
Enable VT-x in BIOS
Disable default hypervisors in Windows services (e.g., Docker Desktop, Windows Hyper-V)
Steps
Install Oracle VirtualBox
Click "New" to create a virtual machine
Select the appropriate Linux distribution (Red Hat for CentOS, Ubuntu 64-bit for Ubuntu)
Allocate resources (storage, RAM, CPU)
Download the ISO image (CentOS Stream 9 or Ubuntu Server)
Configure VM settings:
Go to Settings > Storage
Add the ISO file
Set up network adapters (enable second one as bridged adapter)
Network Adapters Explained
Virtual machines can use different types of network adapters:
NAT: Allows VM to access the internet through the host's network connection.
Bridged: Connects VM directly to the physical network, assigning it a unique IP address.
Host-only: Creates a private network between the host and VMs.
VM Setup
Boot the VM
Set up installation destination and partition scheme
Enable SSH
Set hostname and password
Complete installation
Shut down VM and remove ISO file to prevent reinstallation on next boot
SSH into Virtual Machine
SSH (Secure Shell) is a protocol for securely accessing remote systems. To SSH into your VM:
Open a terminal or command prompt on your host machine
Use the command:
ssh username@vm_ip_address
You need a terminal for SSH because it's a text-based protocol. Direct connection isn't possible as the VM is a separate system with its own network identity.
Understanding Bash
Bash (Bourne Again Shell) is a command-line interface and scripting language commonly used in Unix-based systems, including most Linux distributions. Here's why Bash is important:
Command Execution: Bash allows us to run commands and programs on the system.
Scripting: We can write Bash scripts to automate tasks and manage our virtual environments.
System Interaction: Bash provides a way to interact with the operating system, manage files, and control processes.
The Role of SSH
SSH (Secure Shell) is a network protocol that provides a secure way to access a remote system. Key points about SSH:
Secure Communication: SSH encrypts all traffic between the client and server.
Remote Access: It allows us to log into and execute commands on a remote system as if we were sitting at its console.
Protocol, Not a Program: SSH is a protocol, not a program itself. We need programs that implement the SSH protocol to use it.
Why We Need Bash (or a Similar Shell) for SSH
When we SSH into a virtual machine:
Command-Line Interface: SSH provides a text-based connection to the remote system. We need a shell like Bash to interpret our commands and interact with the system.
Program Execution: Bash allows us to run the SSH client program (usually
sshon Unix-like systems) to initiate the connection.Remote Shell: Once connected via SSH, we're typically dropped into a Bash shell (or whatever the default shell is) on the remote system.
Automating VM Creation with Vagrant
Vagrant is an open-source tool for building and managing virtual machine environments. It simplifies the VM creation process and solves problems like:
Inconsistent development environments
Time-consuming setup processes
Difficulty in sharing exact configurations
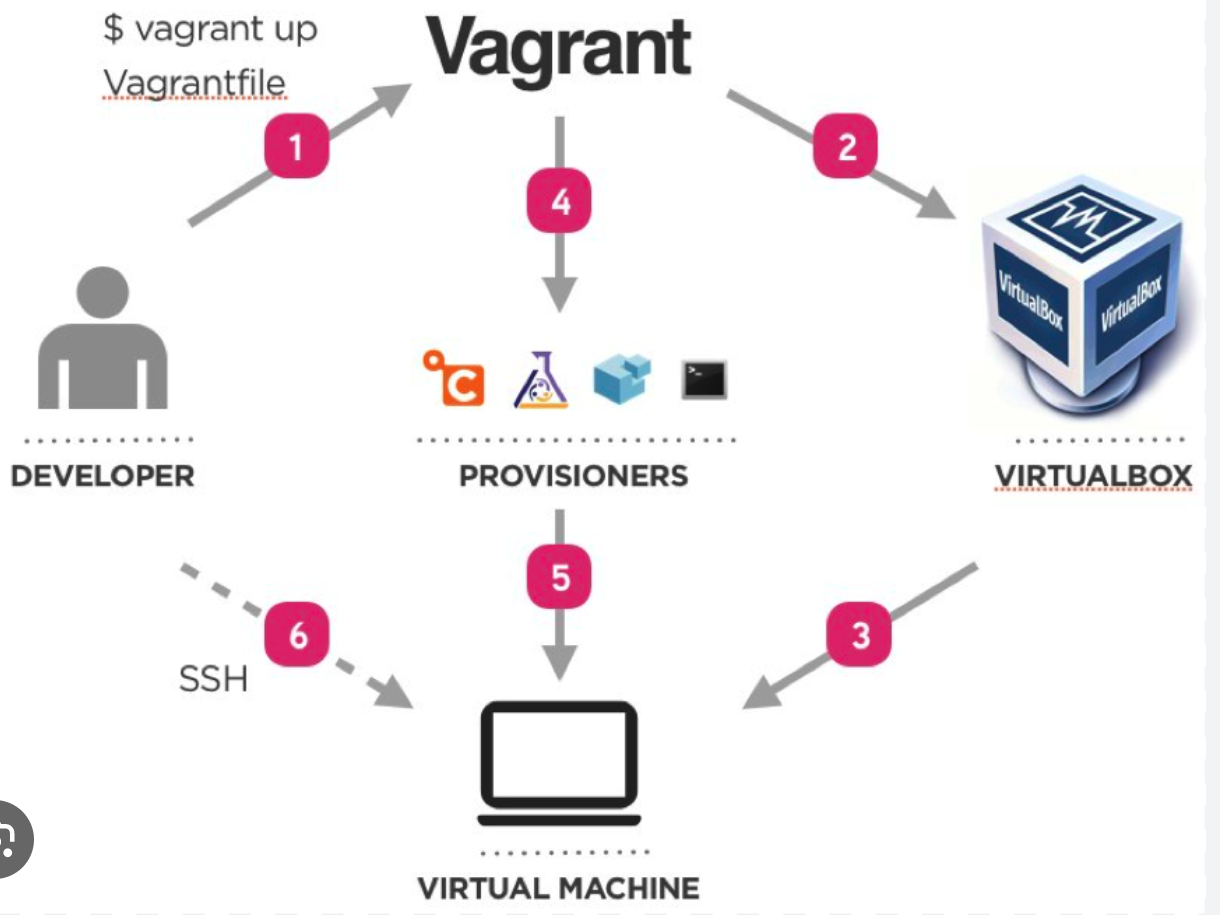
Vagrant Architecture
Vagrant uses a Vagrantfile to define VM configurations. When you run vagrant up, it:
Downloads the specified box (OS image) from the cloud
Creates a VM using the local hypervisor
Applies the configurations specified in the Vagrantfile
Basic Vagrant Commands
vagrant init: Initializes a new Vagrant environment.vagrant up: Starts and provisions the VM.vagrant ssh: Connects to the VM via SSH.vagrant halt: Stops the VM.vagrant destroy: Removes the VM.vagrant status: Shows the status of the VM in the current directory.vagrant global-status: Displays the status of all Vagrant environments on the system.
Example Vagrantfile
Vagrant.configure("2") do |config|
config.vm.box = "eurolinux-vagrant/centos-stream-9"
# or "ubuntu/jammy64" for Ubuntu
config.vm.network "private_network", type: "dhcp"
config.vm.provider "virtualbox" do |vb|
vb.memory = "1024"
vb.cpus = 2
end
end
This Vagrantfile sets up a CentOS Stream 9 VM with 1GB of RAM and 2 CPUs.
Conclusion
Virtualization has revolutionized how we manage computing resources, offering flexibility, efficiency, and cost savings. Whether you're setting up VMs manually or automating with tools like Vagrant, understanding these concepts is crucial for modern IT professionals.
By leveraging virtualization, organizations can optimize their infrastructure, reduce costs, and increase agility in their IT operations. As technology continues to evolve, virtualization remains a cornerstone of modern computing environments, enabling everything from local development environments to large-scale cloud deployments.
Subscribe to my newsletter
Read articles from Vedant Singh Chauhan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
