Securing Your APIs with Azure API Management: Internal and External VNet Options
 Jitendra Yadav
Jitendra YadavTable of contents
As businesses increasingly rely on APIs for connectivity and integration, securing these endpoints becomes paramount. Azure API Management (APIM) offers powerful features for managing and securing APIs, including the ability to deploy your API gateways within virtual networks (VNets). In this article, we’ll explore the security implications of using internal and external VNets with Azure API Management.
Without VNet Integration:
You can easily use the API manager though public load balancer [Ex. Front-door, App gateway etc] and just configure the public IP of apim in backend service
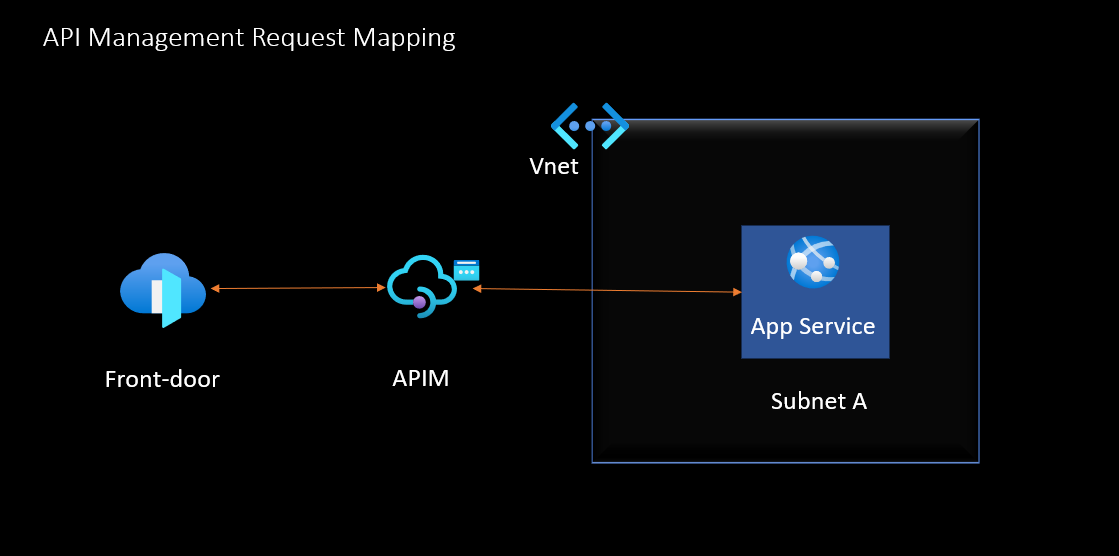
Understanding VNet Integration:
Virtual Networks (VNets) provide an isolated environment within Azure, allowing you to securely connect resources like Azure API Management to your existing on-premises infrastructure or other Azure services. There are two primary deployment options for APIM in relation to VNets:
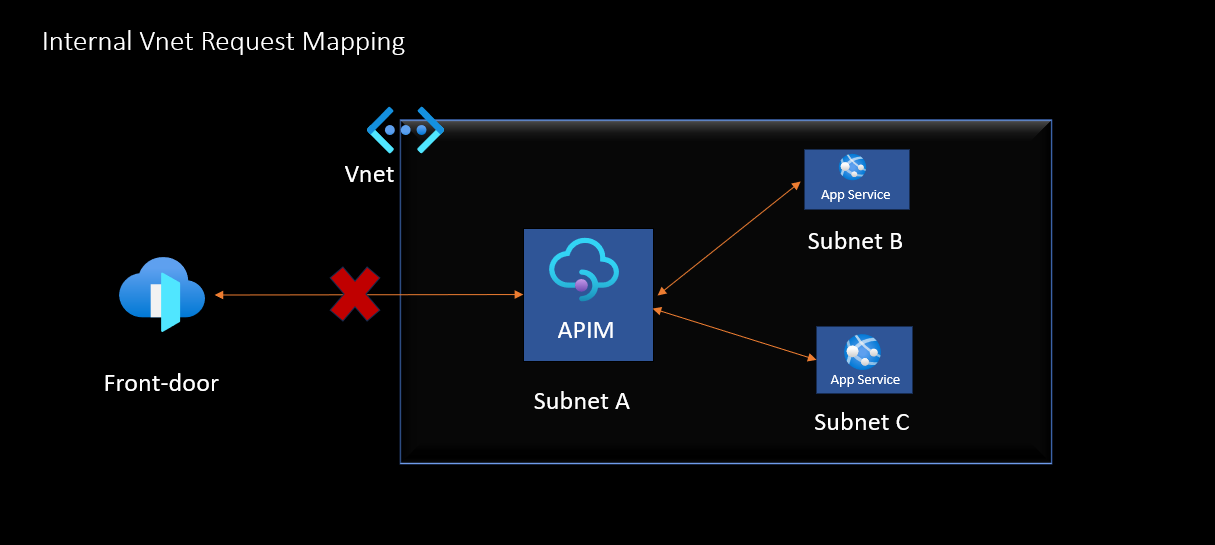
Internal VNet Deployment:
Description: When APIM is deployed in an internal VNet, it is accessible only from within that network. This setup restricts public access to your APIs, making them visible only to authorized users or applications within the same network.
Use Cases:
Ideal for organizations that need to keep their APIs private and limit exposure to the public internet.
Suitable for scenarios where APIs interact with sensitive data or critical internal services.
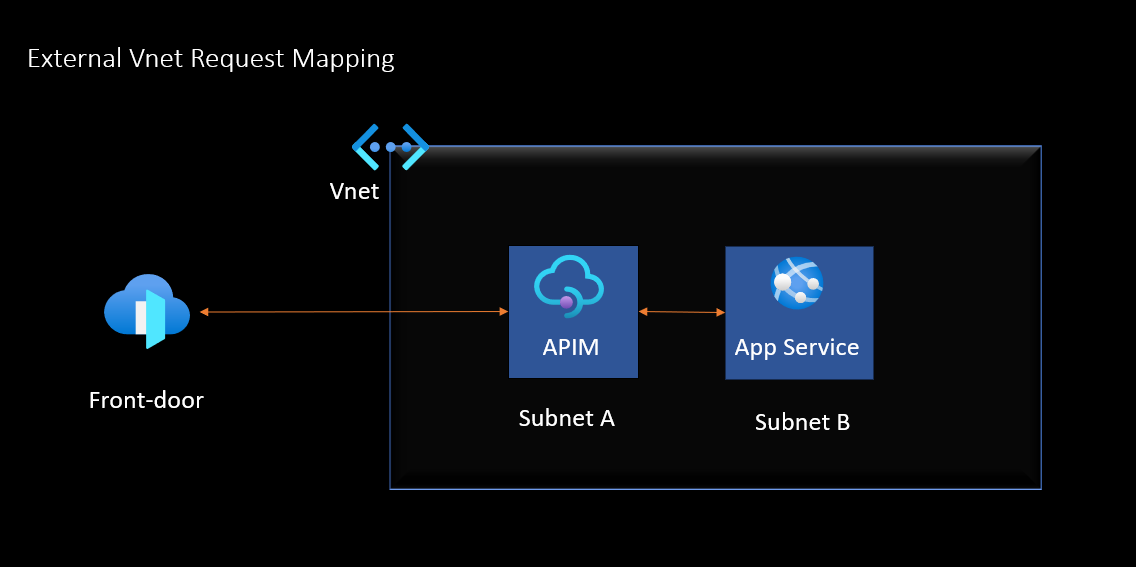
External VNet Deployment:
Description: In this setup, APIM is placed within an external VNet, allowing it to serve APIs that can be accessed from both internal and external clients. This means that while your APIs are secured, they can also be exposed to the internet when necessary.
Use Cases:
Useful for businesses that require a hybrid approach, needing to serve both internal applications and external partners or customers.
Ideal for APIs that need to be accessed from mobile apps, web clients, or third-party integrations.
Some Key deference:
| Feature | External VNet Integration | Internal VNet Integration |
| Accessibility | Accessible from both inside the VNet and the internet. | Accessible only from within the VNet or connected networks. |
| Public IP | Yes, the service has a public IP address. | No, the service only has a private IP address. |
| Use Case | Scenarios where both internal and external clients need access. | Scenarios requiring strict isolation from the public internet. |
| DNS Resolution | Public DNS resolves to a public IP. | Private DNS resolves to a private IP. |
| Security | External access can be restricted using NSGs, but the service is still publicly accessible. | Complete isolation, only accessible via private IP, enhancing security. |
Best Practices for Securing APIs with APIM
Use Managed Identities: Leverage Azure Active Directory (AAD) and managed identities to authenticate and authorize access to your APIs, reducing the need for hardcoded credentials.
Implement Rate Limiting and Throttling: Protect your APIs from abuse and ensure fair usage by configuring rate limits and throttling policies within APIM.
Monitor and Audit: Regularly monitor API usage and audit logs for unusual activity. Utilize Azure Monitor and Application Insights for real-time insights into API performance and security.
Secure API Gateway: Always configure HTTPS to encrypt data in transit and prevent interception by unauthorized users.
Conclusion
Securing your APIs is critical in today’s interconnected landscape, and Azure API Management provides robust options for doing so through VNet integration. Whether you choose an internal or external deployment, the ability to control access, enhance isolation, and leverage Azure's security features will help you protect your sensitive data and maintain the integrity of your API services.
By thoughtfully implementing these strategies, you can create a secure environment for your APIs, ensuring they serve their purpose without compromising on security.
Subscribe to my newsletter
Read articles from Jitendra Yadav directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jitendra Yadav
Jitendra Yadav
As a DevOps Engineer, I specialize in managing release cycles and Azure infrastructure using Terraform. I automate deployments through YAML code and handle various automation requirements using PowerShell and Python. My responsibilities include managing app services, storage containers, and Kubernetes, providing solutions for software needs like backup and disaster recovery, and overseeing Azure policies. With strong end-to-end debugging skills, I excel at log analysis and code inspection to identify and resolve issues effectively.