Mastering AWS IAM: A Beginner's Guide to Secure Access Management
 Hema Sundharam Kolla
Hema Sundharam Kolla
1 . What is IAM?
2 . What is Authentication?
3 . What is authorization?
4 . How does IAM work?
what is IAM?
Let's take a real-world scenario of a bank. Let's say a bank has a service desk, an employee desk, and sensitive information. First, if a person needs to enter the bank, they must have an account in that bank. Only then can the person enter the bank, and this is known as authentication. Let's say that person has different access levels. Based on that, they will be allowed to go to the employee desk and perform their tasks there. The employee has no access to the service desk and sensitive information. This is known as authorization. In short, we can say that the work or policy of a person is known as authorization.
Now let's compare this with the scenario of AWS. Let's say you are a DevOps engineer at xyz.com and you have access to the root account of AWS. If a new employee or an existing employee requests permission to create a server, you can't give them the root credentials. If you give the root credentials to all employees, they might accidentally delete the database, causing all data to be lost. To prevent this, AWS introduced IAM. Let's say an employee's role is a backend engineer, and you need to create an IAM user and attach a policy that allows them to only create a database. This way, the employee can access only database-related tasks, solving the problem.
How does IAM work in AWS?
IAM consists of:
Let’s break down IAM User, Policy, Group, and Roles with a real-world analogy:
1. IAM User (Identity and Access Management User)
What it is:
An IAM user is a person or application that interacts with AWS resources and services. Each user has a set of credentials (username/password or access keys) and permissions that define what they can and cannot do.
Real-World Scenario:
Imagine you run a company, and you have multiple employees (like Bob, Alice, and John). Each of these employees needs access to certain parts of the company’s infrastructure. In this case, Bob needs access to the servers, Alice needs access to the database, and John needs access to both the servers and databases. Each employee gets a unique ID card (which represents an IAM user), allowing them to access only the areas they need.
2. IAM Policy
What it is:
A policy is a set of permissions that defines what actions are allowed or denied for a user, group, or role. Policies are written in JSON format and attached to users, groups, or roles to enforce these permissions.
Real-World Scenario:
In the company analogy, let’s say Alice works in the HR department, and she should only have access to the employee records database. Bob is in IT and should only access the servers but not the databases. So, the company assigns specific rules to their ID cards that allow or restrict access to certain parts of the office. These rules represent the IAM policies.
Bob's Policy: Access to the server room but not the HR database.
Alice's Policy: Access to the HR database but not the server room.
3. IAM Group
What it is:
An IAM group is a collection of users with the same set of permissions. Instead of assigning policies to individual users, you can group users together and assign policies to the group. All members of the group inherit the group’s permissions.
Real-World Scenario:
In the company, you have multiple employees in different departments. For example, all HR staff (Alice, Mary) need access to the employee records, and all IT staff (Bob, John) need access to the servers. Instead of giving each HR or IT member their own policy, you create groups:
HR Group with access to the employee database.
IT Group with access to the server room.
Now, when a new HR or IT employee joins, you can simply add them to the right group, and they will automatically have the appropriate permissions.
4. IAM Role
What it is:
A role is like a set of permissions that you can temporarily assign to a user or service. Roles are typically used to grant access without the need for long-term credentials. They are useful for services or users that need temporary or restricted access to resources.
Real-World Scenario:
Let’s say Alice from HR needs to help the IT team for a day, so she temporarily needs access to the servers. Instead of creating a new user or adding her to the IT group permanently, you can give her a special “IT Support Role”. This role allows her to access the servers only while she is performing her temporary duties. Once the job is done, the role expires, and she goes back to her HR-only access.
Putting It All Together (Full Scenario):
Your company (AWS account) has employees (IAM users).
Each employee has an ID card with permissions (IAM policy) that allows them to access specific areas like the database or server room.
The company organizes employees into departments (IAM groups), like IT or HR, where members of the group have similar access needs.
When someone from another department temporarily needs access to another part of the company, they are given a special badge (IAM role) for a limited time to perform their task.
This structure ensures security, as employees (users) only have access to what they need, and it’s easy to manage permissions by grouping users and applying roles as needed.
Let's dive into the execution part :
Let's create an IAM user :
Open the AWS console, search for "IAM user" in the search bar, and click on it.
Go to the IAM user console, navigate to the Users tab, and click on Create User.
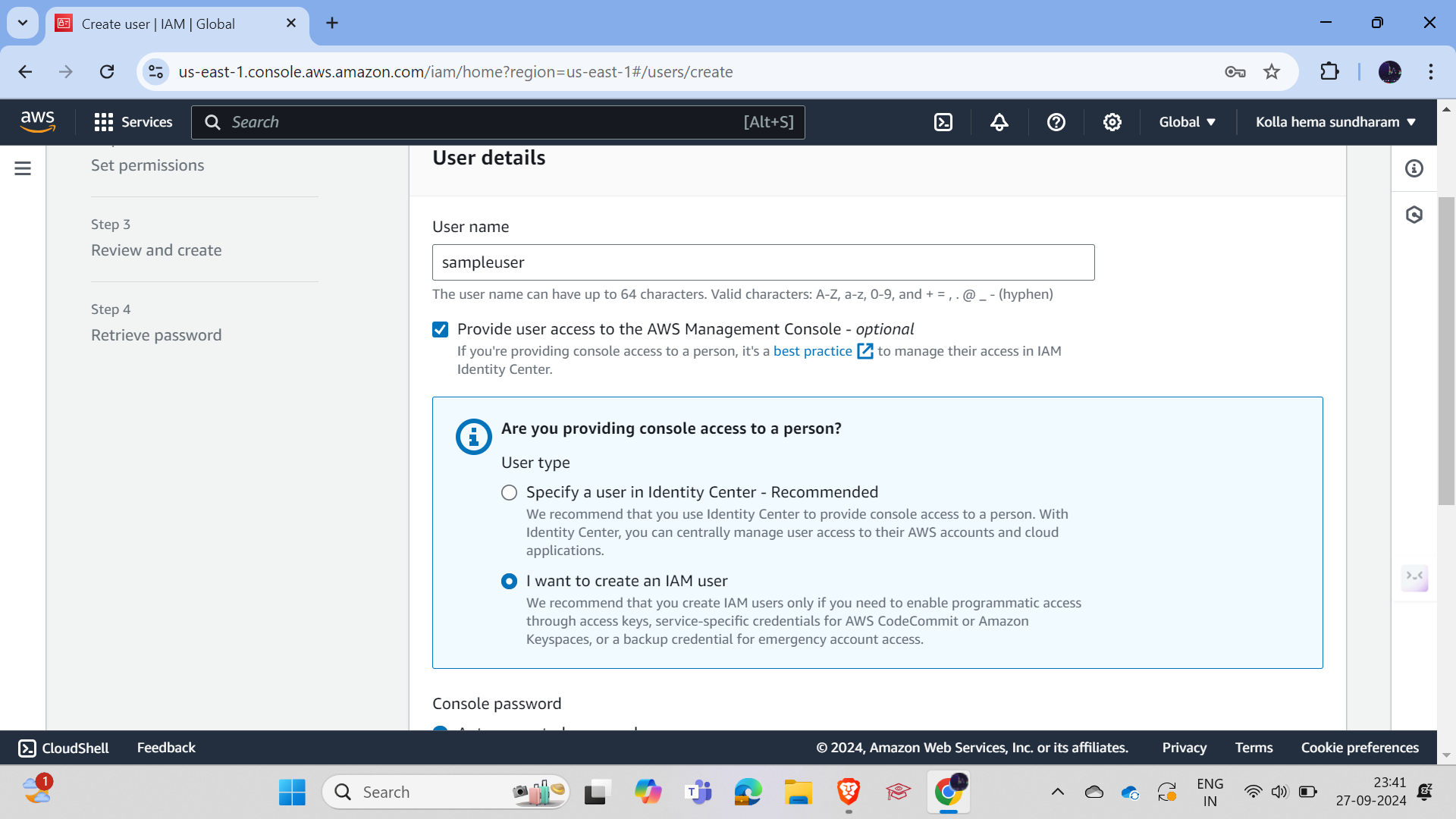
and simply add the name as per your requirement and specify i want to create an IAM user
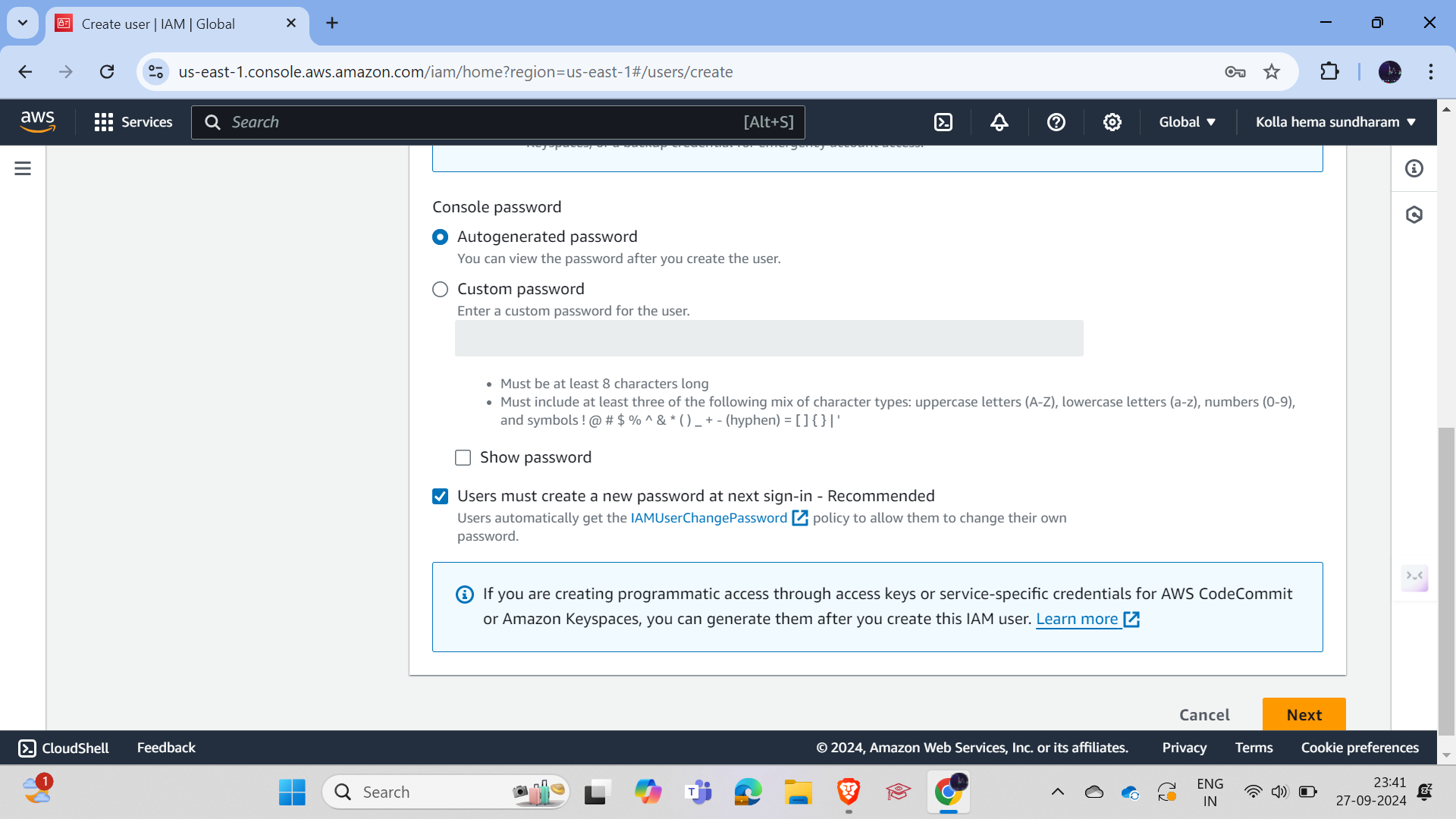
And simply click on the auto-generated password option and select "Users must change the password at next sign-in" so that the user can set the password according to their requirement.
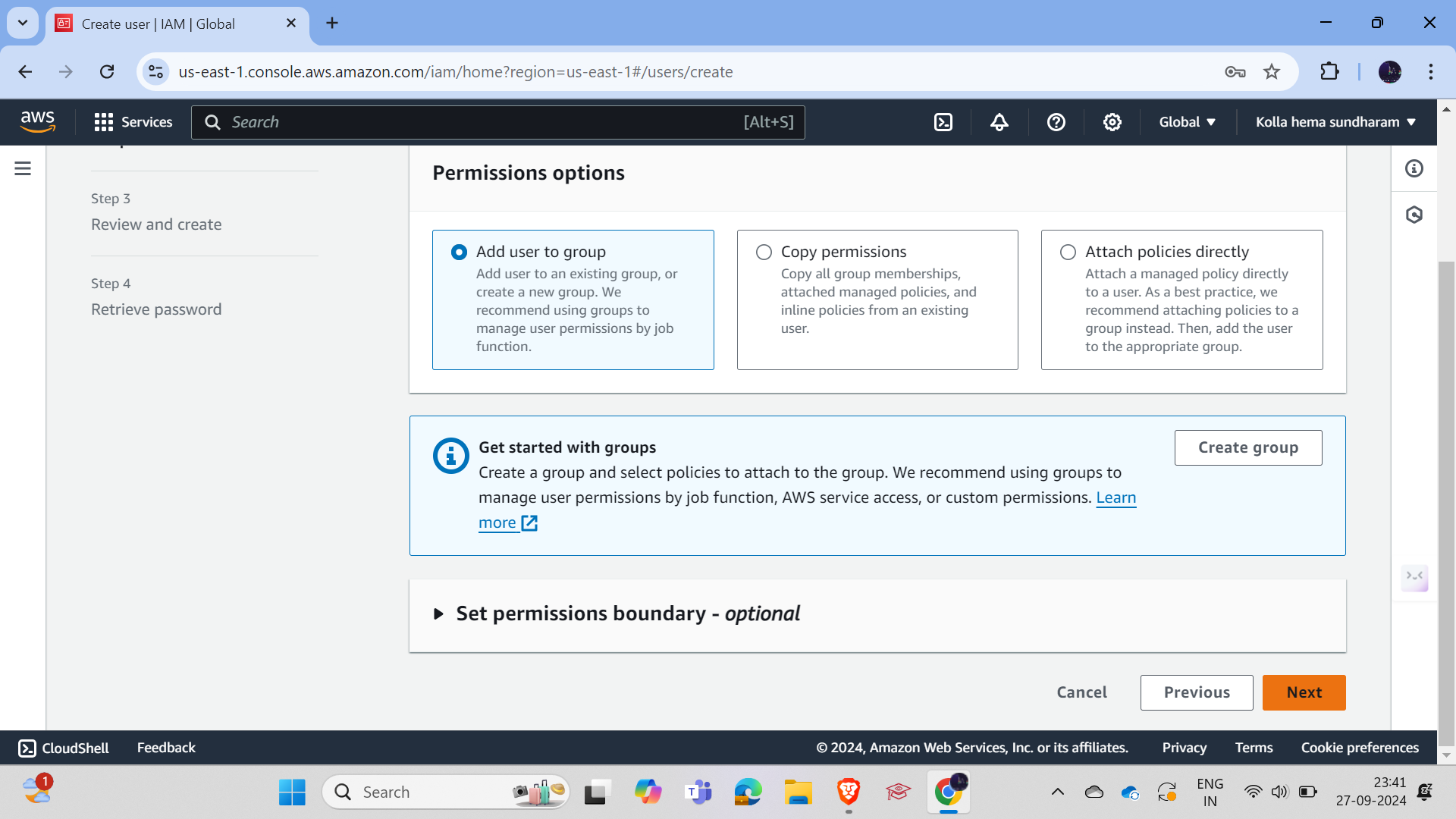
And in the next tabs, leave the settings as they are and click on Next. If you need to attach policies, you can add them, but at this point, we will just create a user with no permissions so that we can edit or add the policies later.
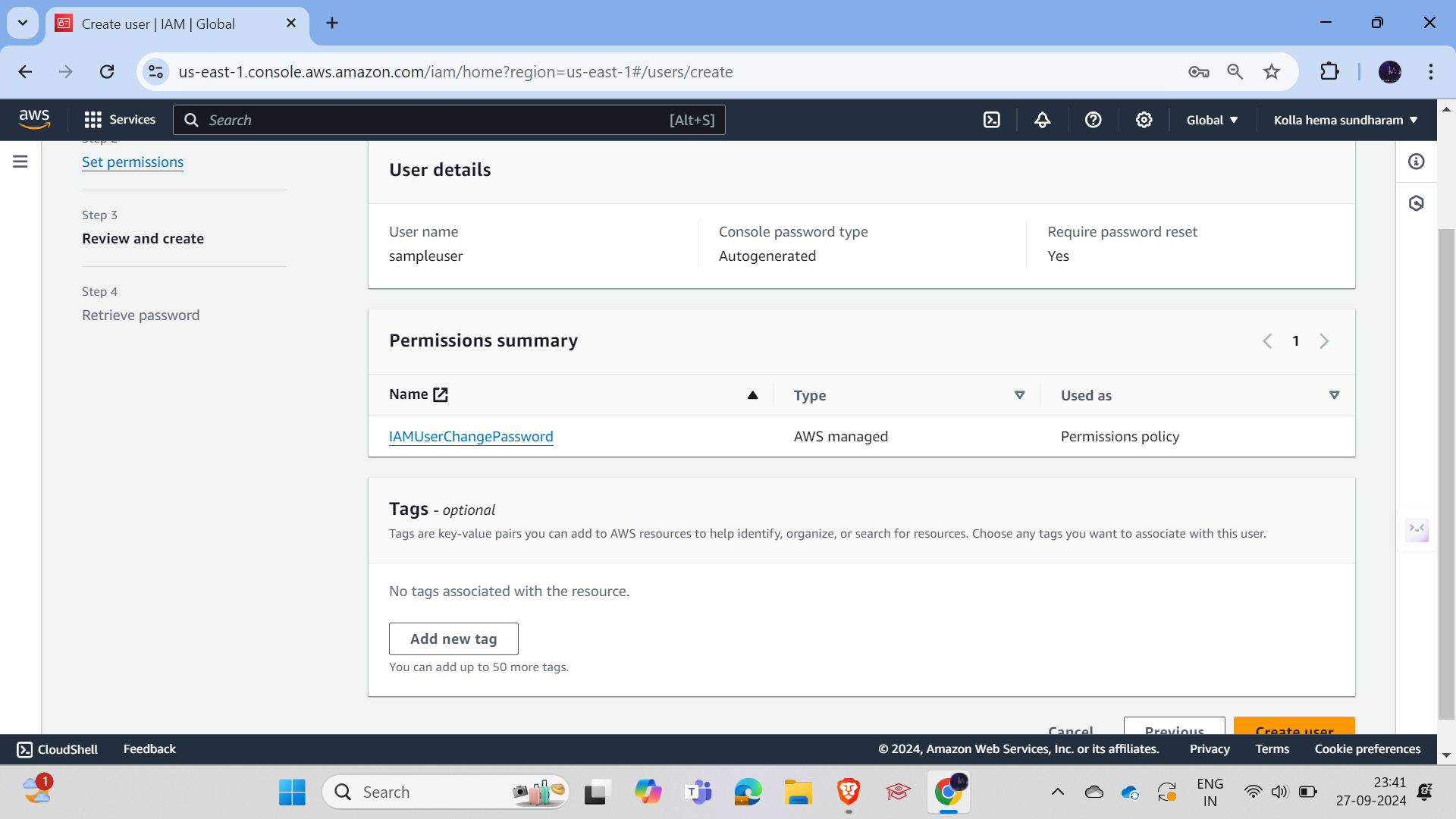
After validating everything, just click on Create User.
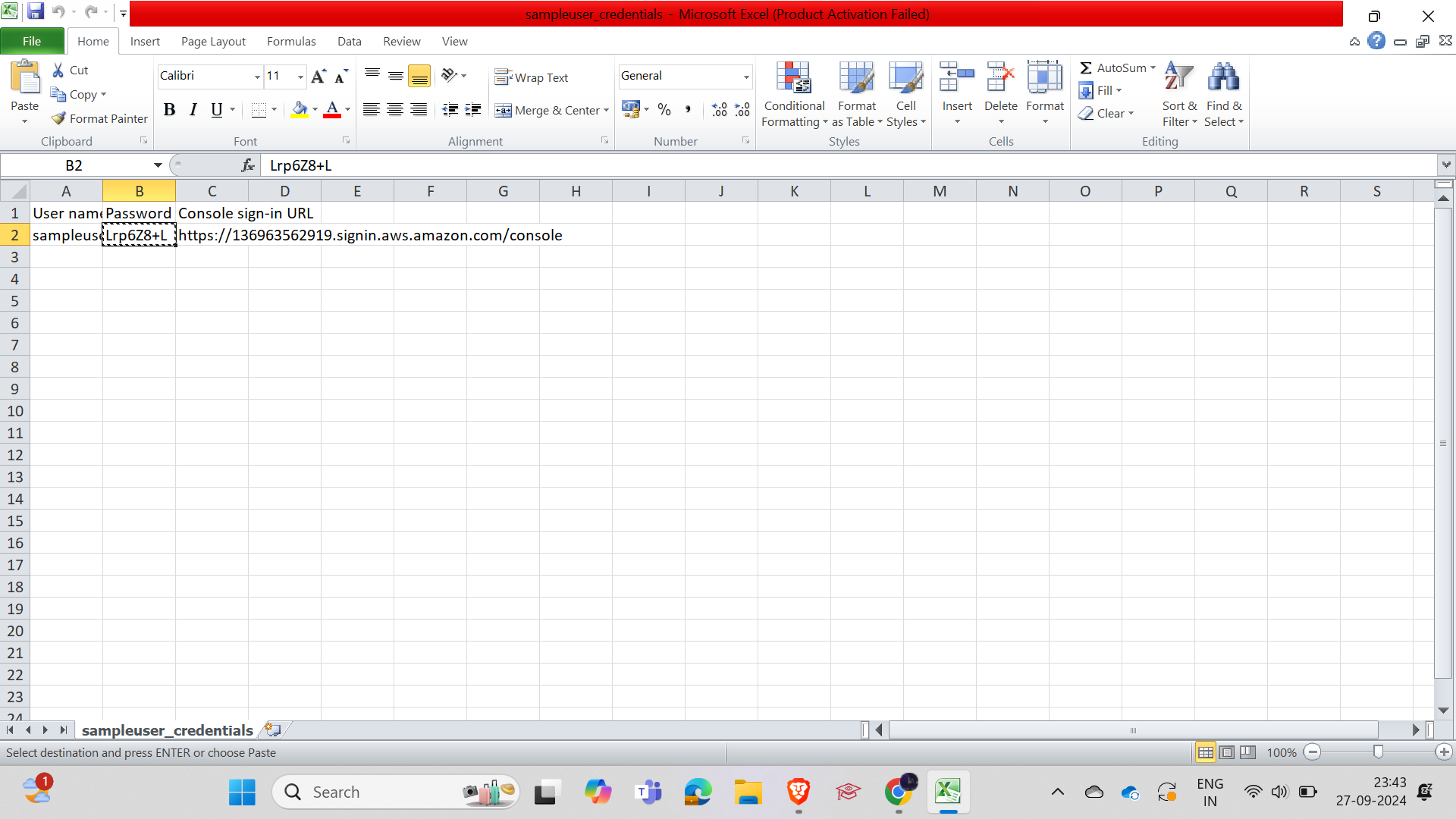
and just download the CSV file that contains the credentials of the user and send it to the employee.
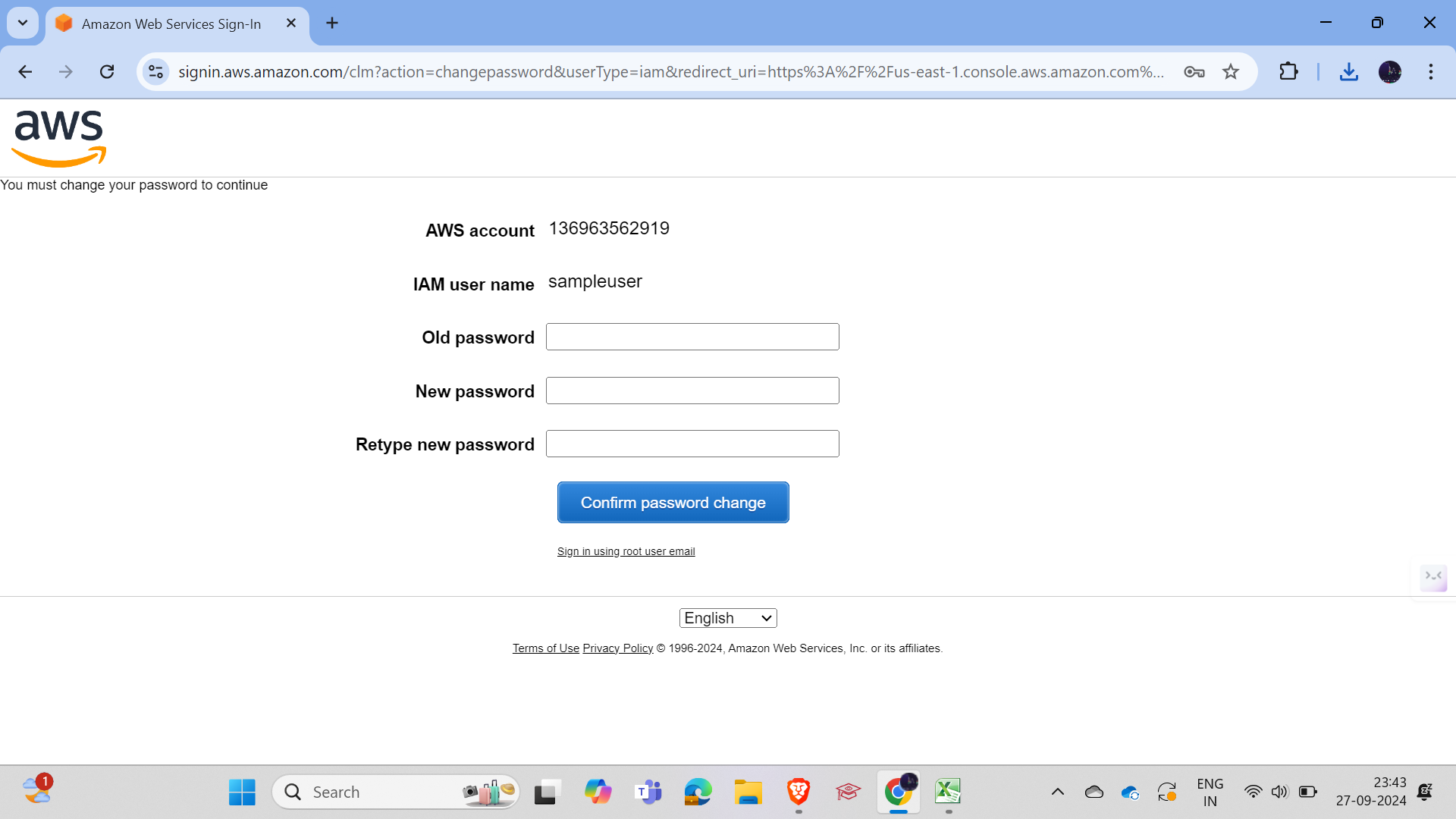
We enforced a policy requiring users to change their password after the first login.
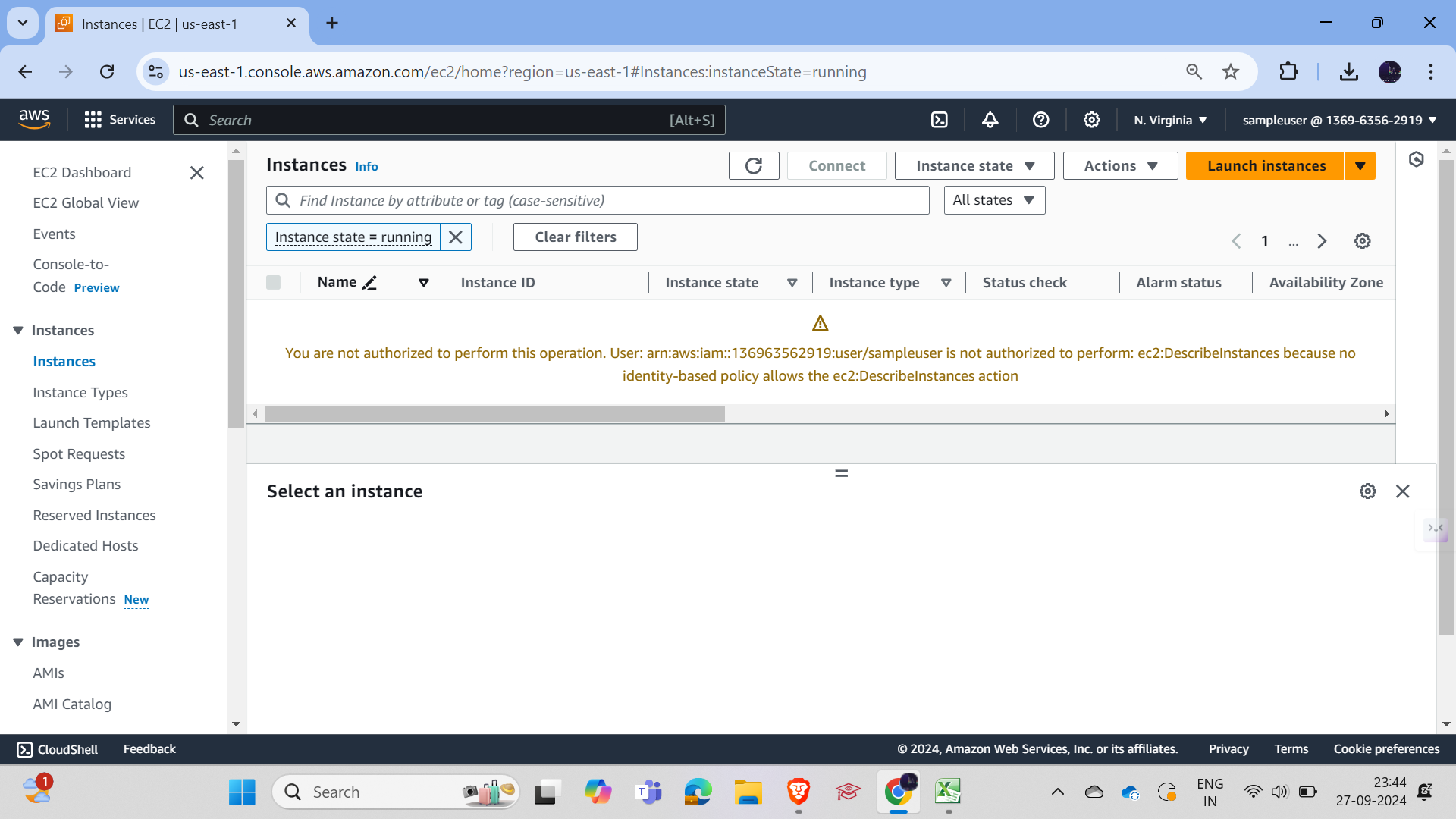
Let's search for any EC2 creation. We had no access for creation at first because, while creating the user, you had not given the permissions for creating. So, here we can't access anything. Let's give access and check what happens.
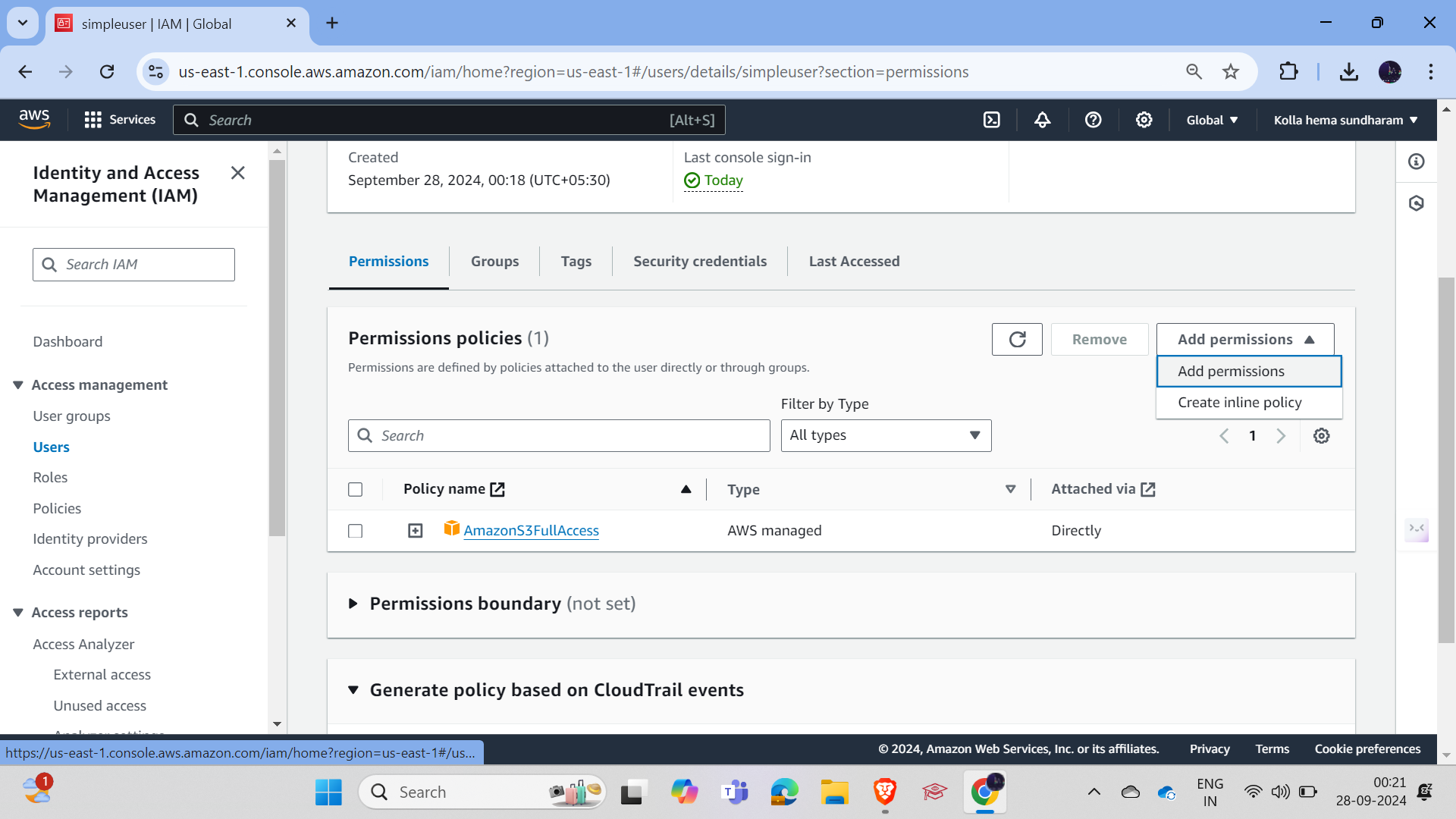
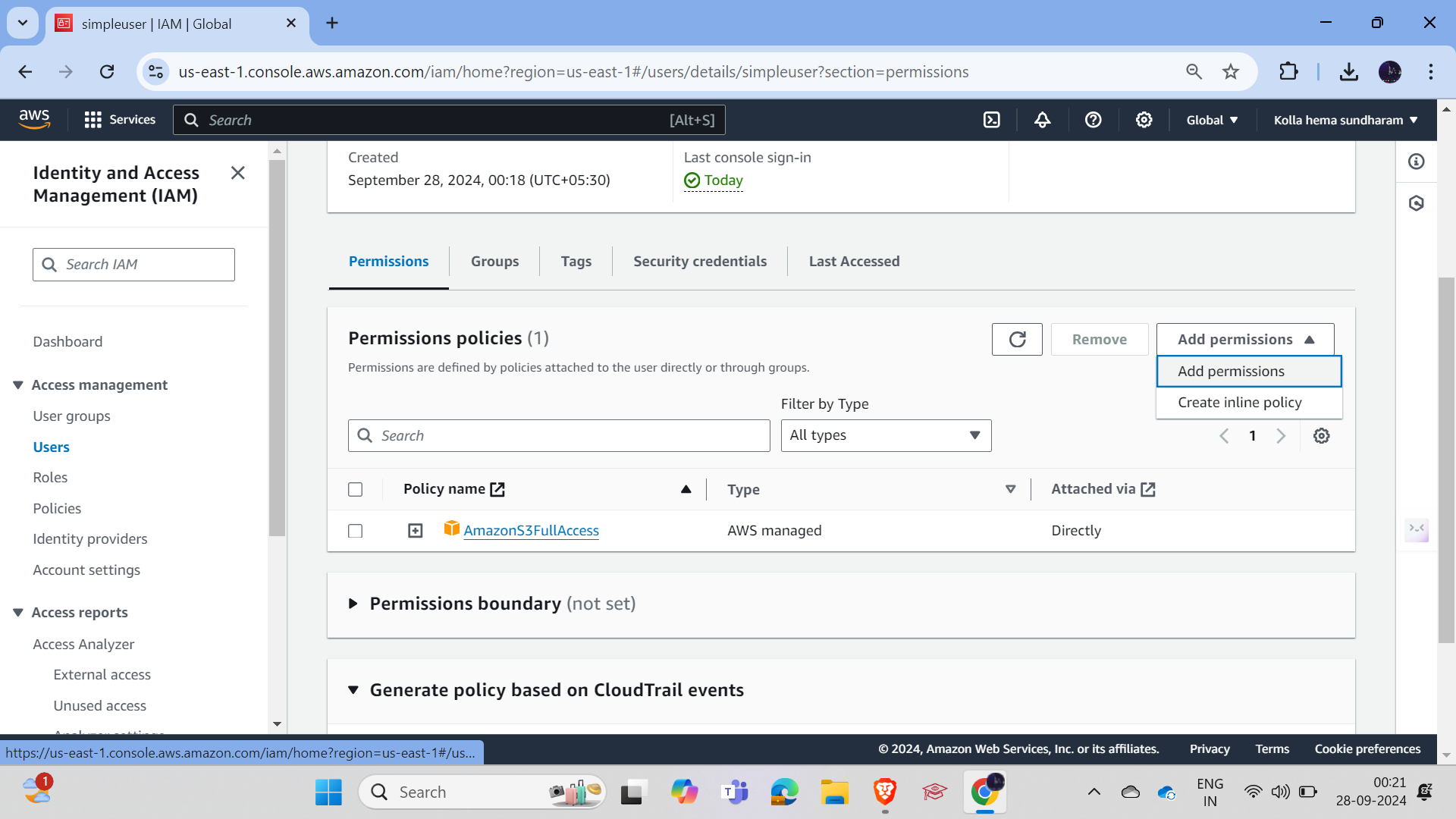
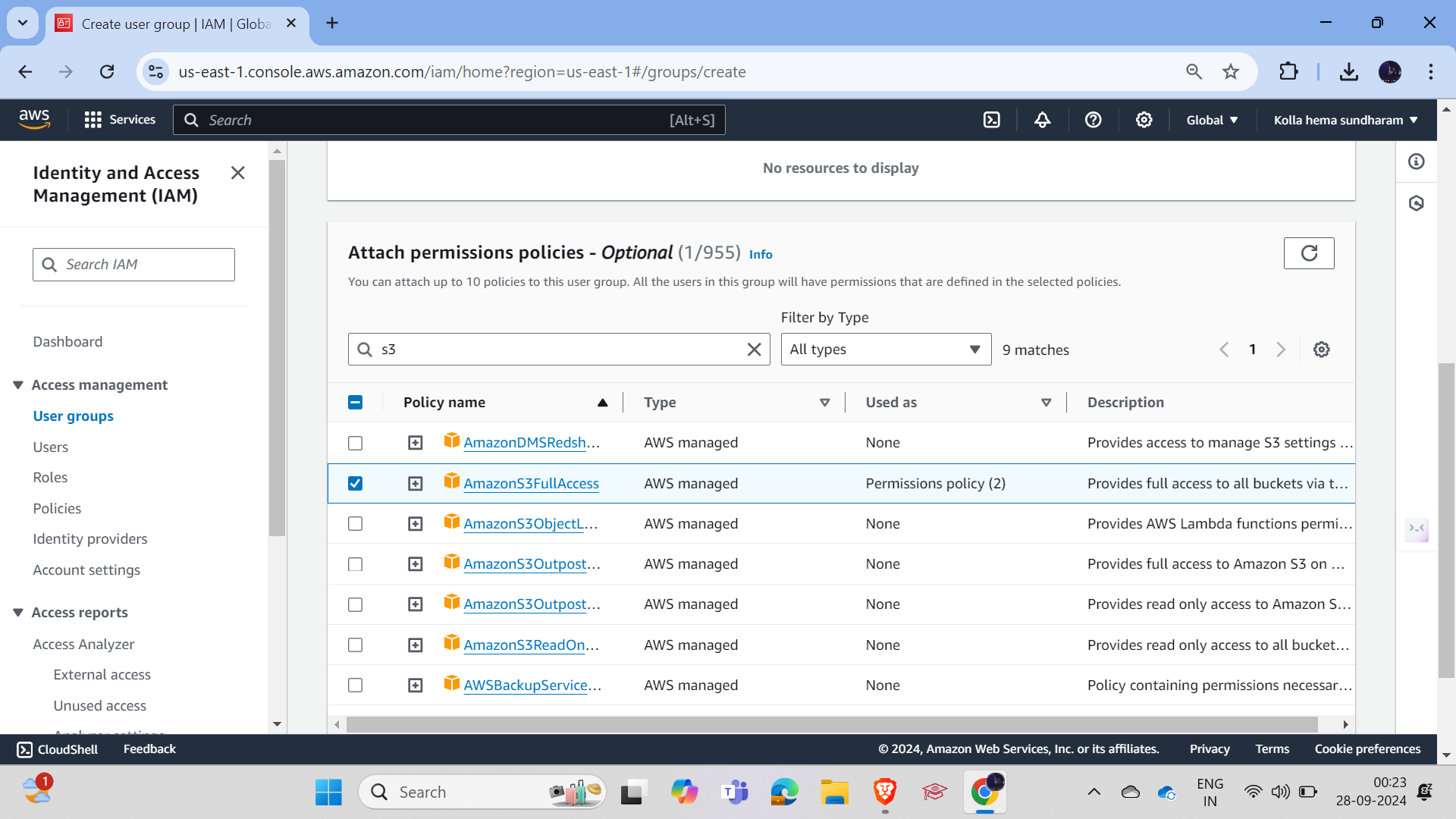
Let's enter into that, click on Add Permissions, then select S3FullAccess and click on it. Save, and you can select as per your requirements. There are lots of policies, and there are also user-defined policies. You can manage them as per your requirement.
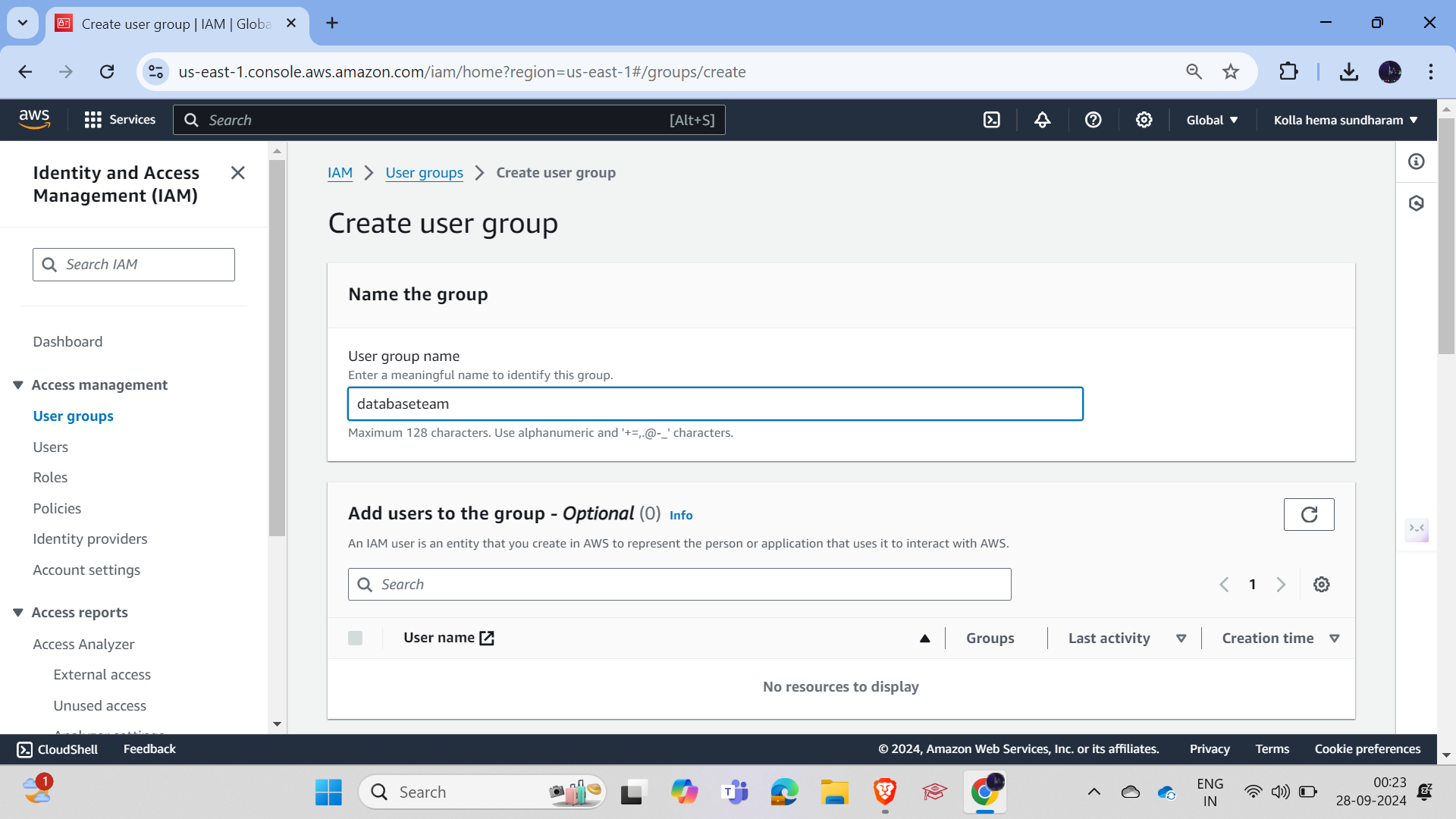
Let's say there are lots of employees who join and leave the company frequently. The DevOps engineer had to create users repeatedly. Instead of that, we can create a group and attach the policies. When a new employee comes and asks for a login, simply create a new user and add them to that group. That's it. This way, we can gain efficiency and save time.
Let's see the images of creating a group and adding the user to the group. Let's check if the user has received the policies that we attached to the group.
Creating a group
Attach the permissions to the group.
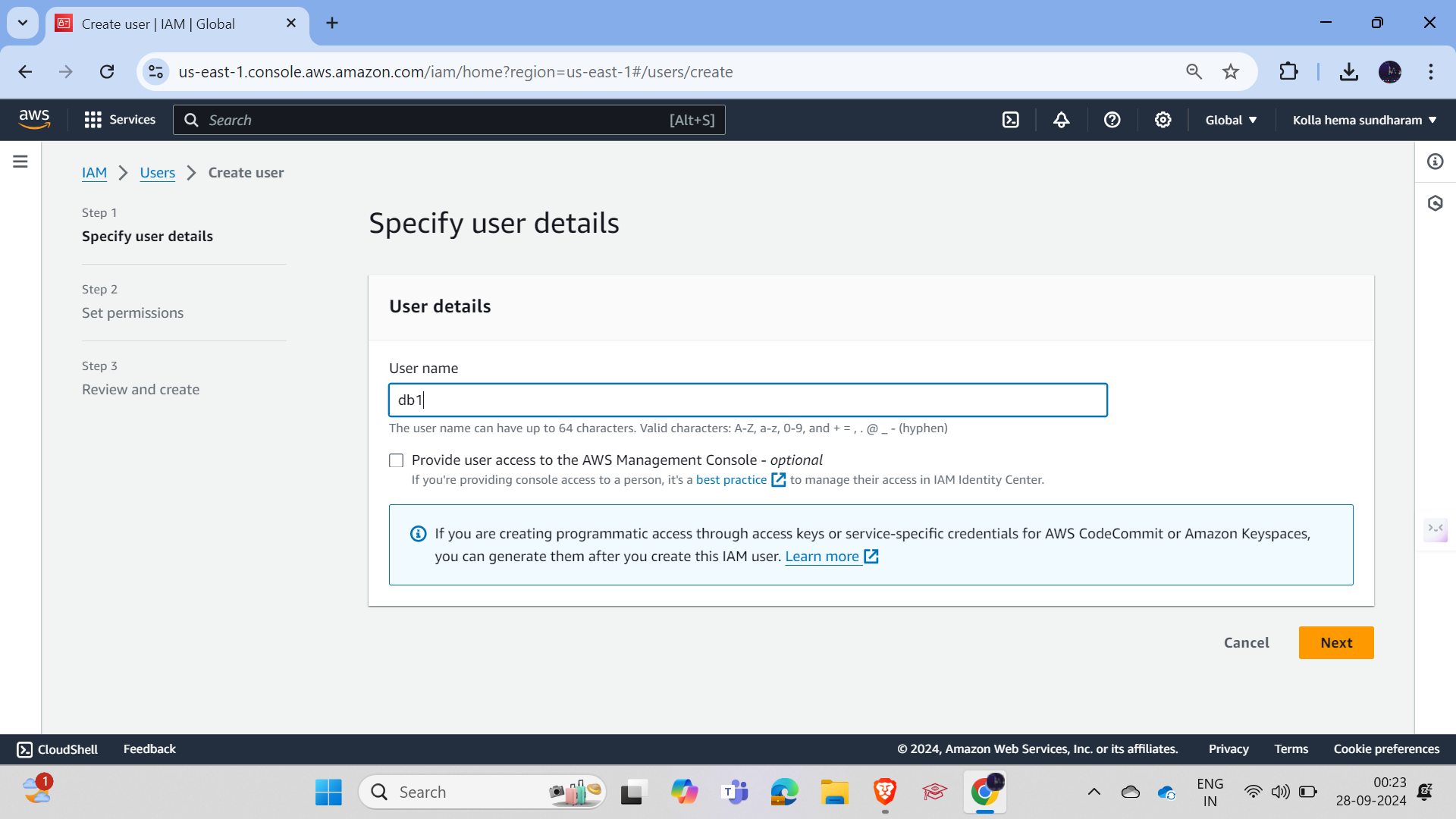
creation of two users and adding them to the group
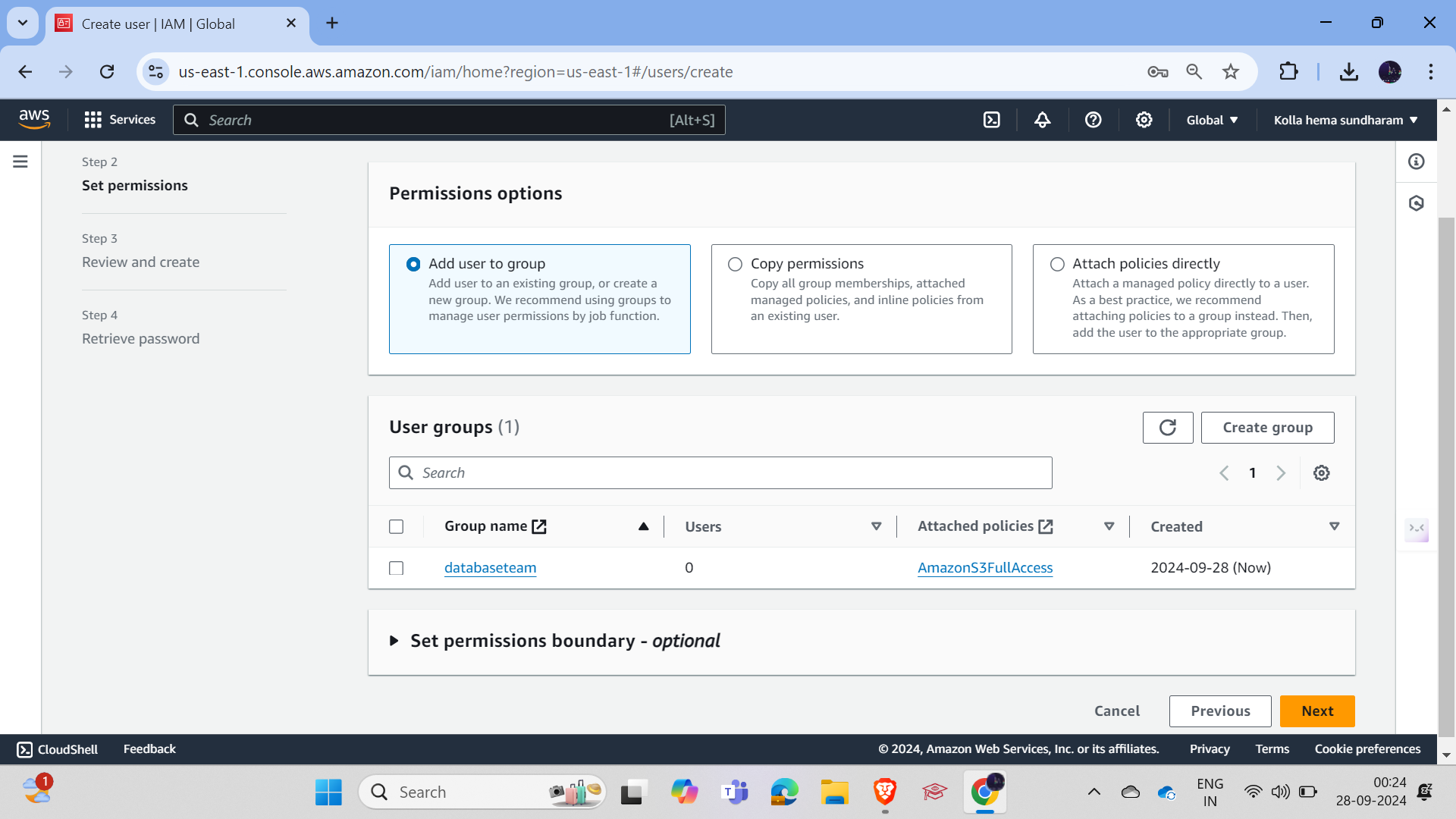
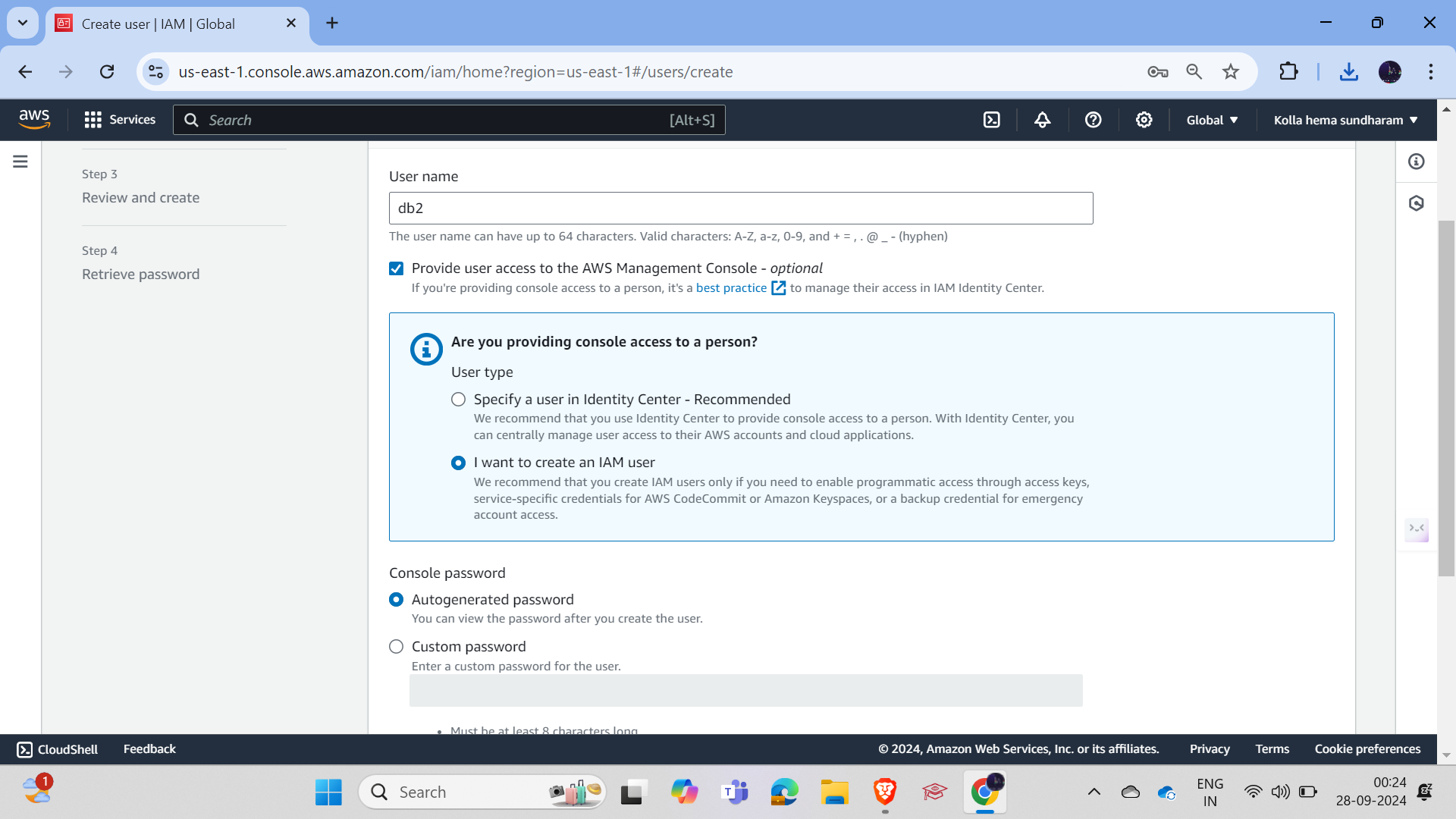
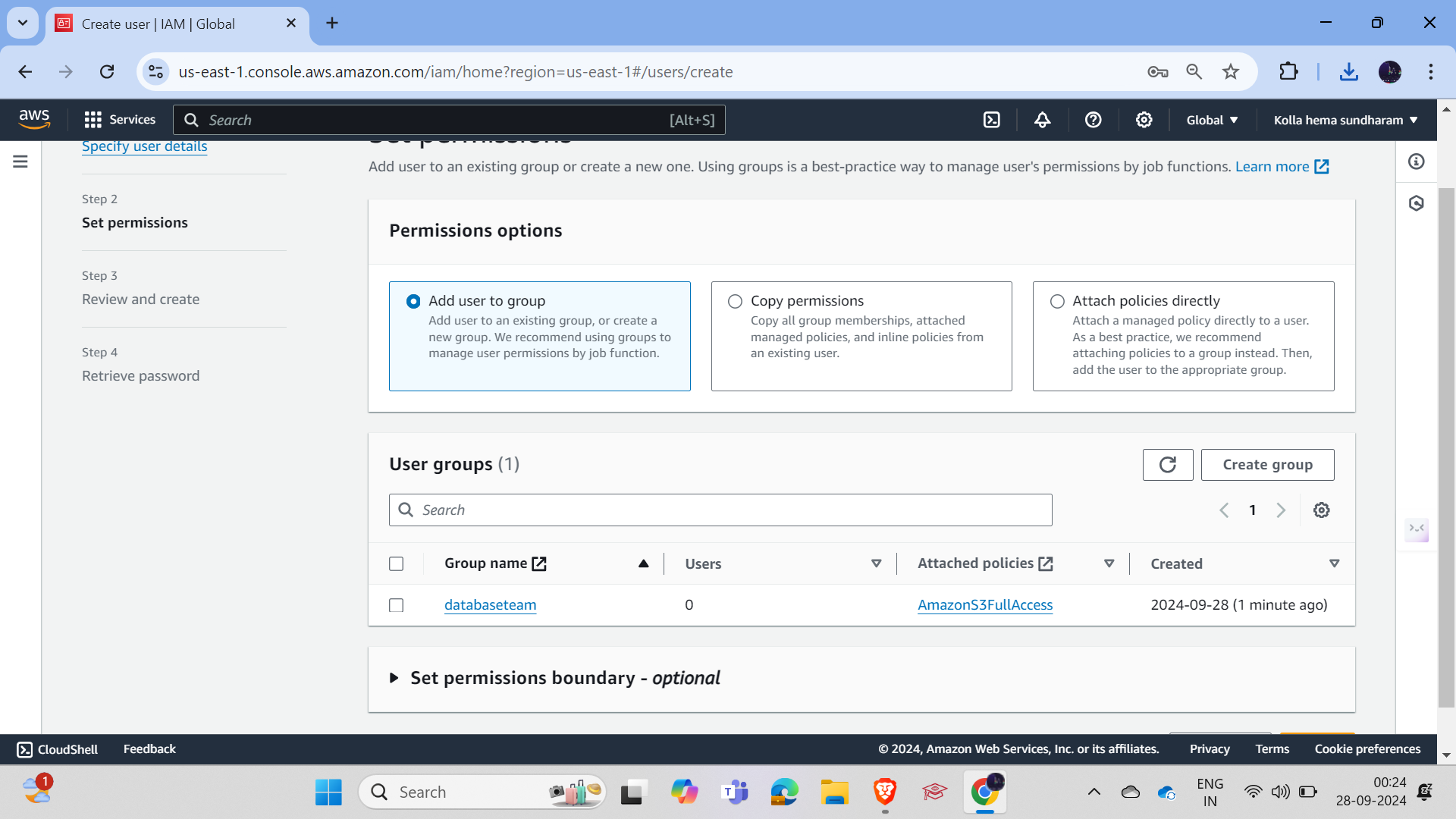
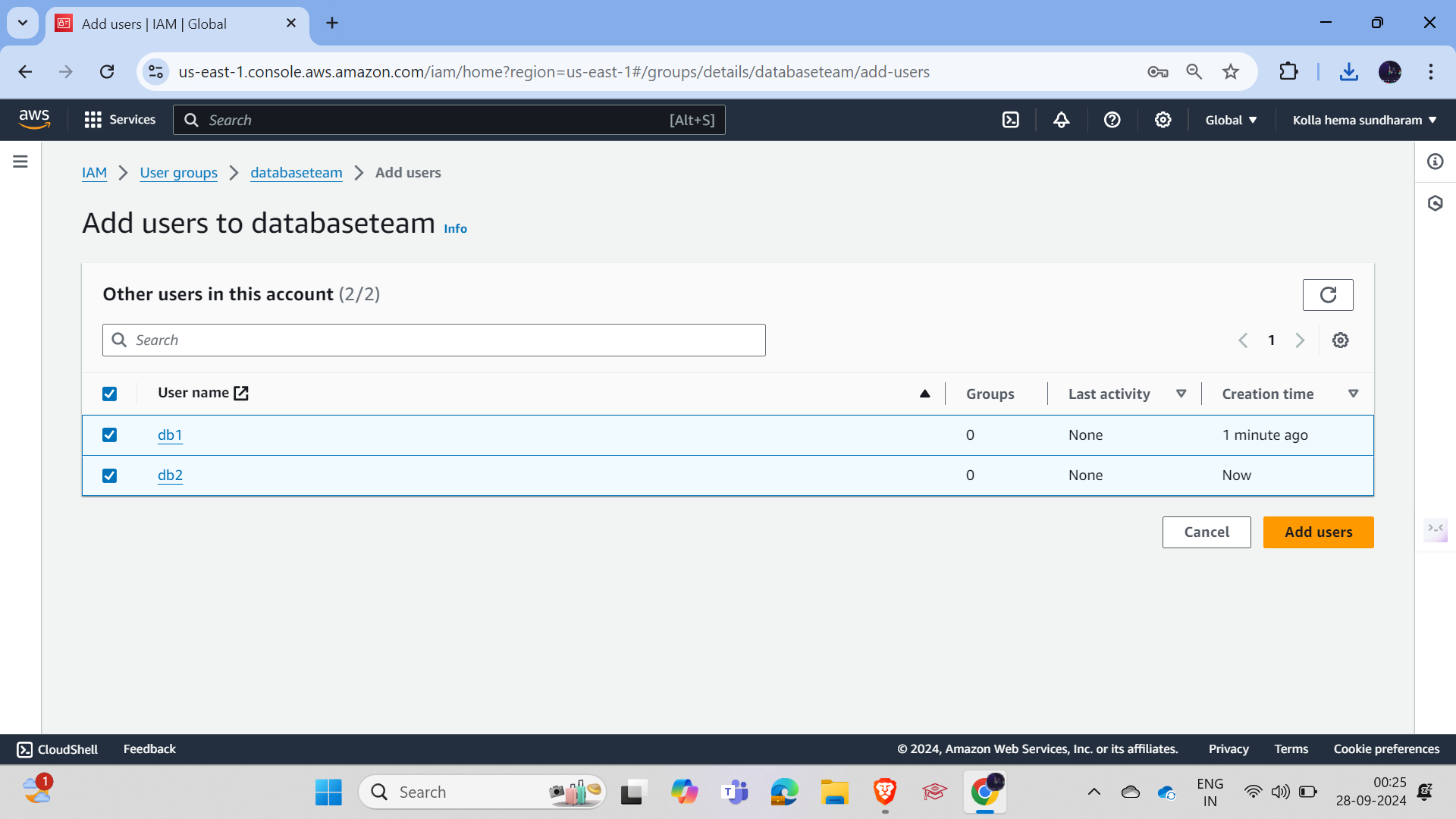
Now add both users to the group by going to the group, clicking on "Add Users," and adding the users.
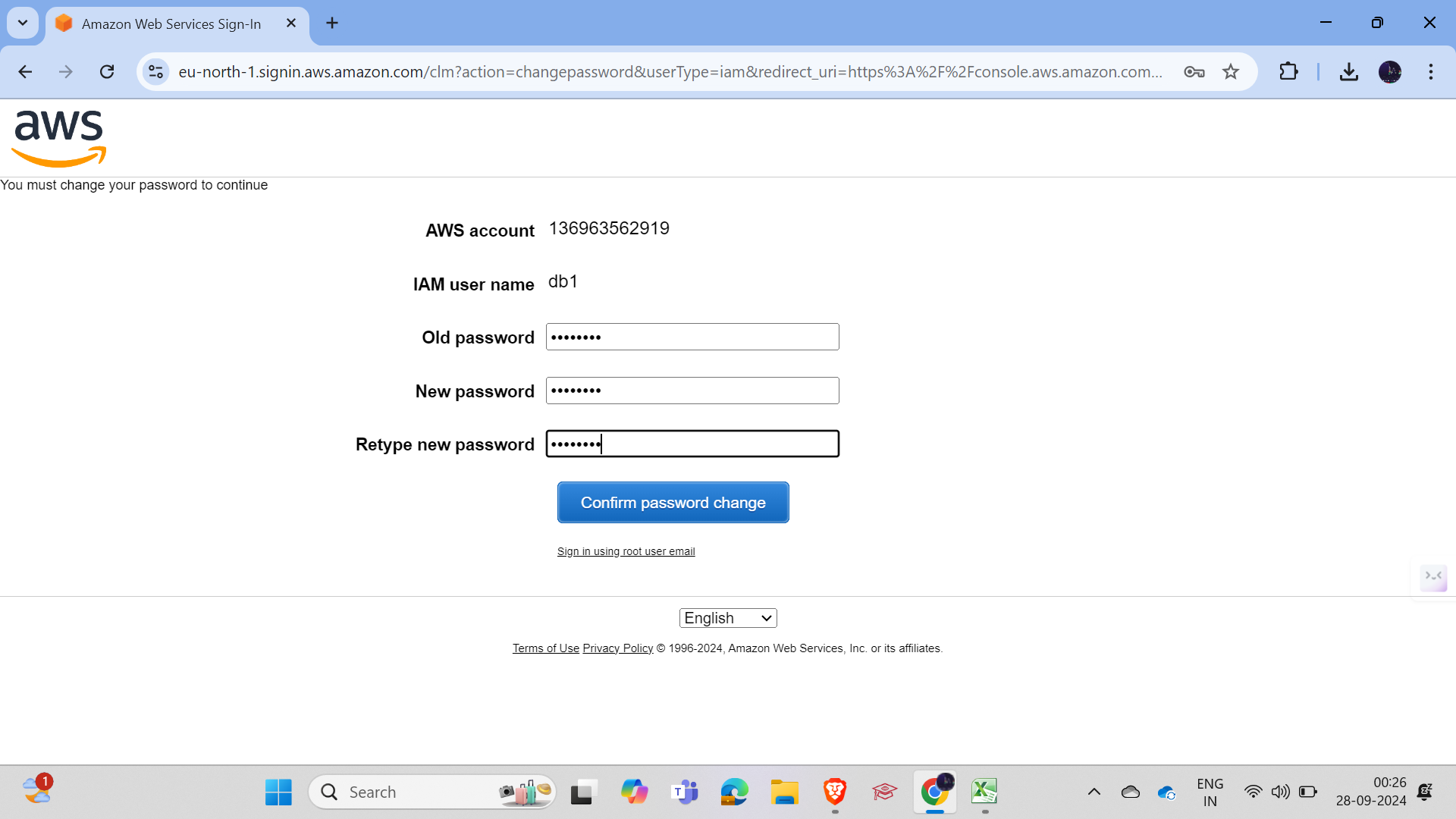
Let's log in to both users and see if they got the permissions.
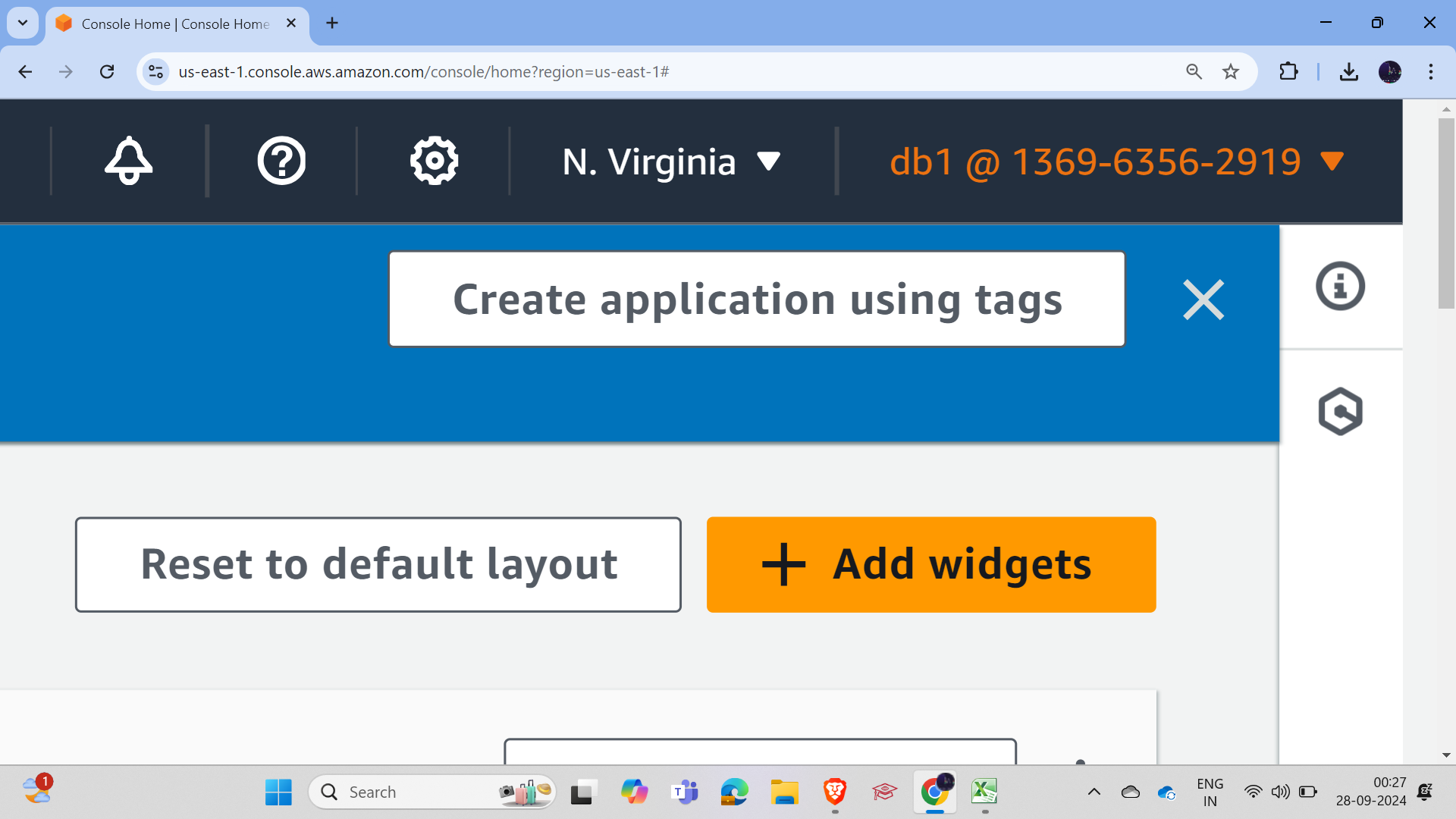
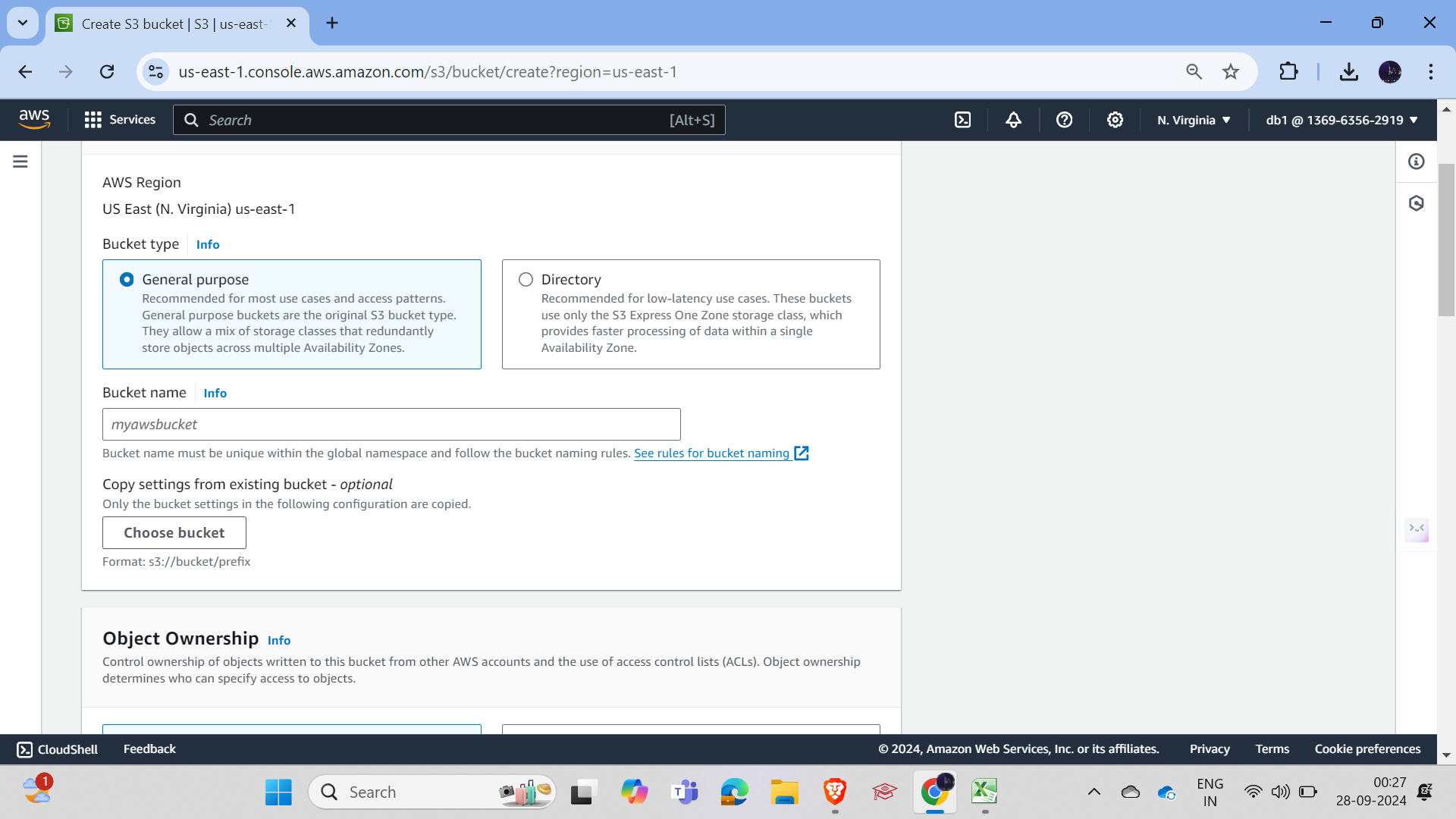
User 1 now has access to create the bucket; let's check for User 2.
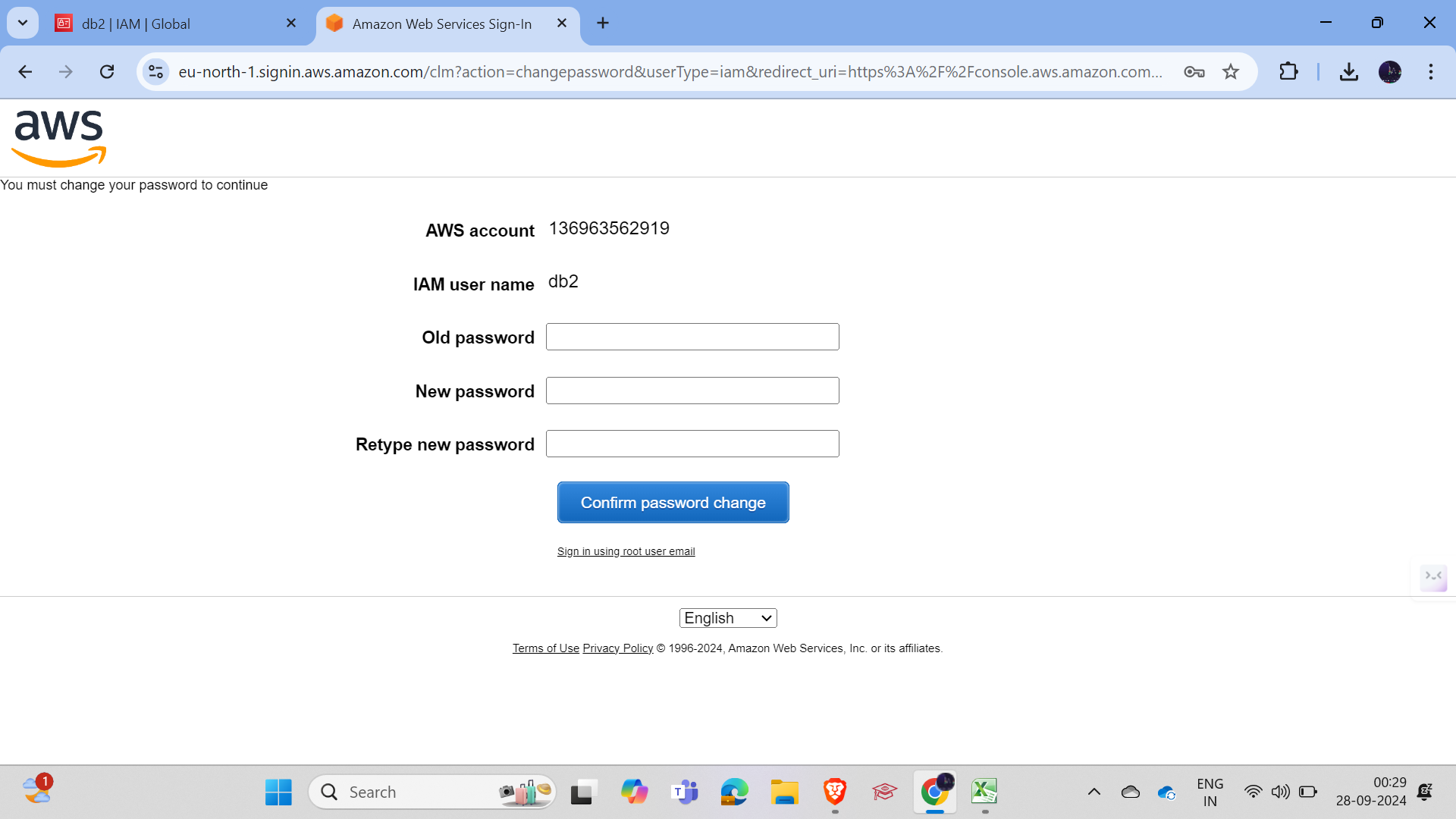
User 2 now has access to create the bucket.
Note: At the end, delete all the resources to avoid costs.
Conclusion :
In conclusion, mastering AWS IAM is crucial for ensuring secure access management within your AWS environment. By understanding the core components—IAM users, policies, groups, and roles—you can effectively manage permissions and access controls, minimizing the risk of unauthorized actions. Implementing IAM best practices not only enhances security but also streamlines the process of managing user access, making it easier to scale and adapt to changing organizational needs. Whether you are a beginner or looking to refine your IAM strategy, this guide provides a solid foundation to help you navigate and leverage AWS IAM for robust access management.
Subscribe to my newsletter
Read articles from Hema Sundharam Kolla directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Hema Sundharam Kolla
Hema Sundharam Kolla
I'm a passionate Computer Science student specializing in DevOps, cloud technologies, and powerlifting. I've completed several certifications, including AWS Cloud Practitioner and Google’s Generative AI badge, and I'm currently exploring both AWS and Azure to build scalable, efficient CI/CD pipelines. Through my blog posts, I share insights on cloud computing, DevOps best practices, and my learning journey in the tech space. I enjoy solving real-world problems with emerging technologies and am developing a platform to offer career advice to students. Outside of tech, I'm a competitive powerlifter, constantly striving to improve and inspire others in fitness. Always eager to connect with like-minded individuals and collaborate on projects that bridge technology and personal growth.