Threat detection🕵️♂️ With Flaws.cloud CloudTrail Logs using ELK Stack
 Goodycyb
GoodycybThis project demonstrates the deployment of the ELK Stack on an AWS EC2 instance and the ingestion of Flaws.cloud CloudTrail logs into the ELK Stack for threat detection.
Step 1: Setting up ELK Stack On AWS EC2
This step provides detailed instructions on deploying the ELK Stack on an AWS EC2 instance running Ubuntu 20.04 LTS, using a t2.medium instance type."
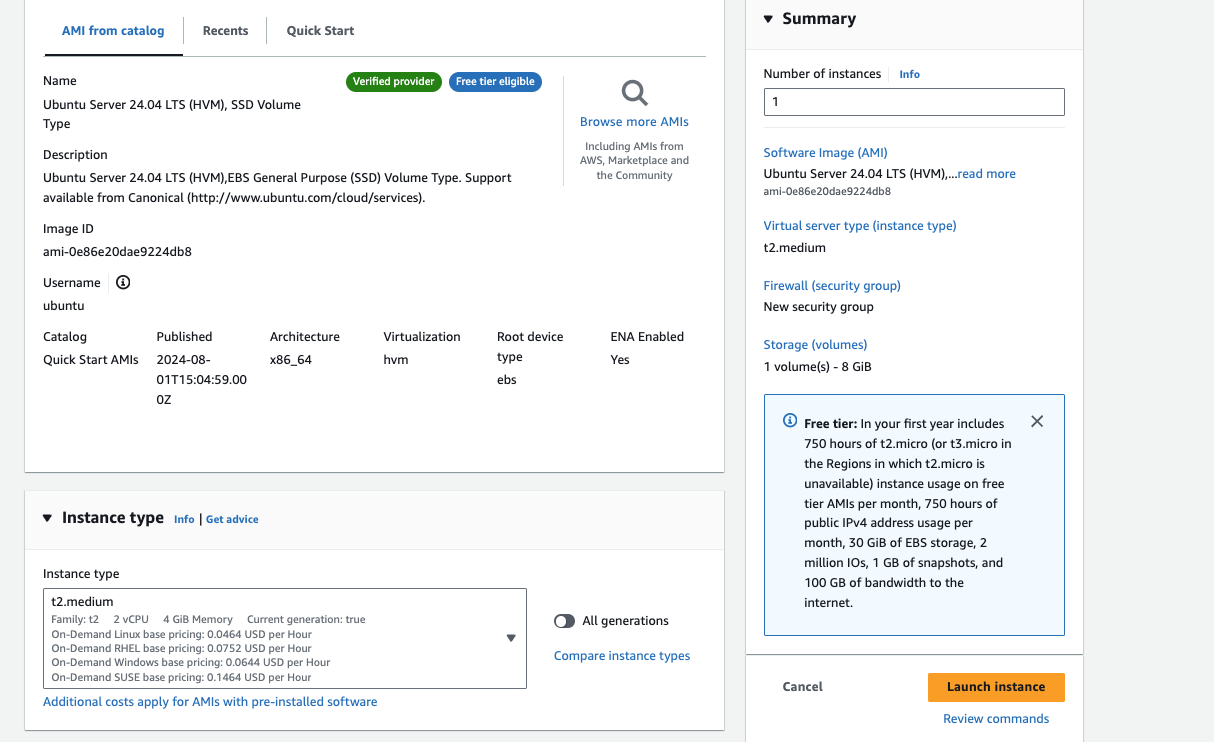
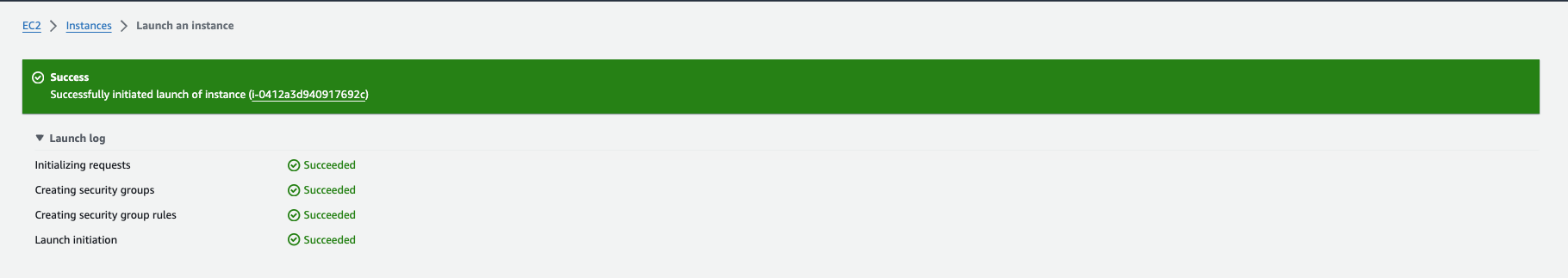
Step 2: Initial Configuration for ELK Setup
This step demonstrates detailed instructions on deploying the ELK (Elasticsearch, Logstash, and Kibana) login page for security purposes.
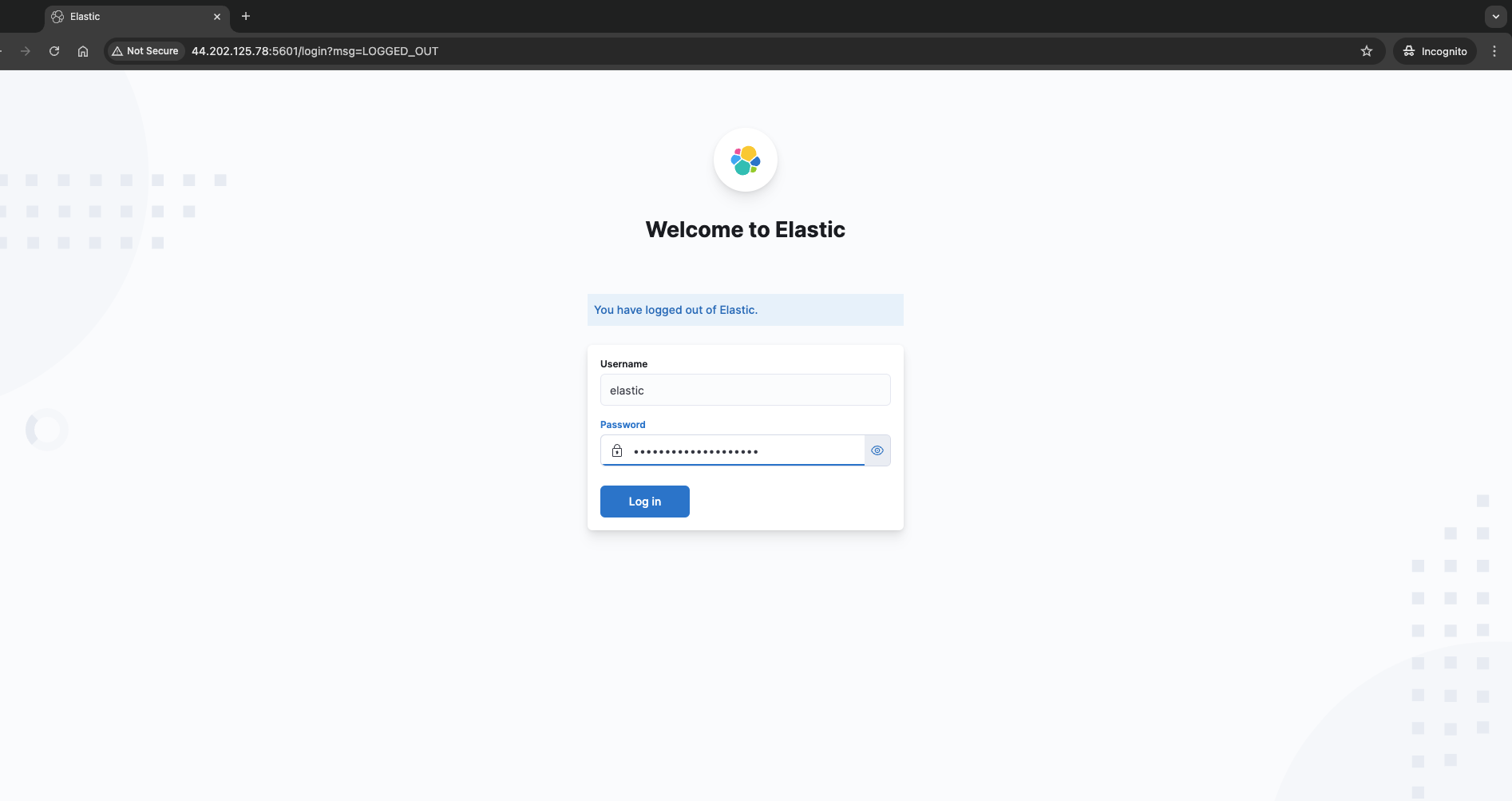
Step 3: Ingesting Flaws.cloud CloudTrail Logs to ELK - Guide
The Logs ingested to ELK are the flaws.cloud AWS CloudTrail dataset to identify unusual patterns and detect potential security threats.
CloudTrail Log Dataset Summary
The Log Dataset used in this lab is the Public dataset of Cloudtrail logs from flaws.cloud which can be accessed Here.
You can Read through the blog post Here. md5: 4f0481c6be700ffc7610dbbf8cee5578 Size: ~240MB of log data
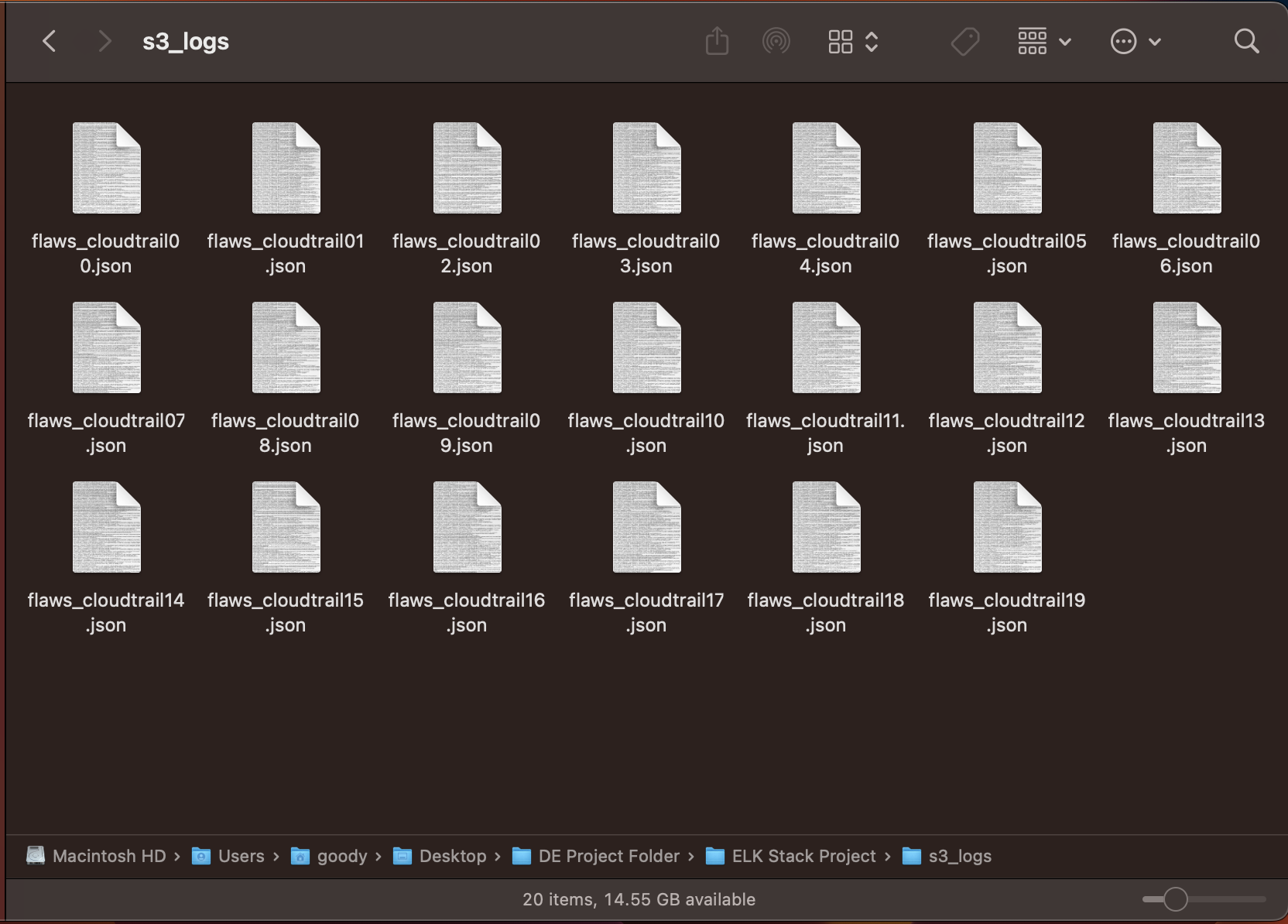
Flaws.cloud cloud-trail dataset cleaning
🔥 Python Code to Convert Multiple CloudTrail Json files to a single Json File. - Helper Script aws-cloudtrail2sof-elk.py from the SOF-ELK repository.
🔥 Python Code to Split a Single JSON File into chunks of JSON files of 50MB - Split_json.py
The Pyhton Scripts can be access via my GitHub page.
Ingesting 50MB chunks of CloudTrail Log Files to ELK
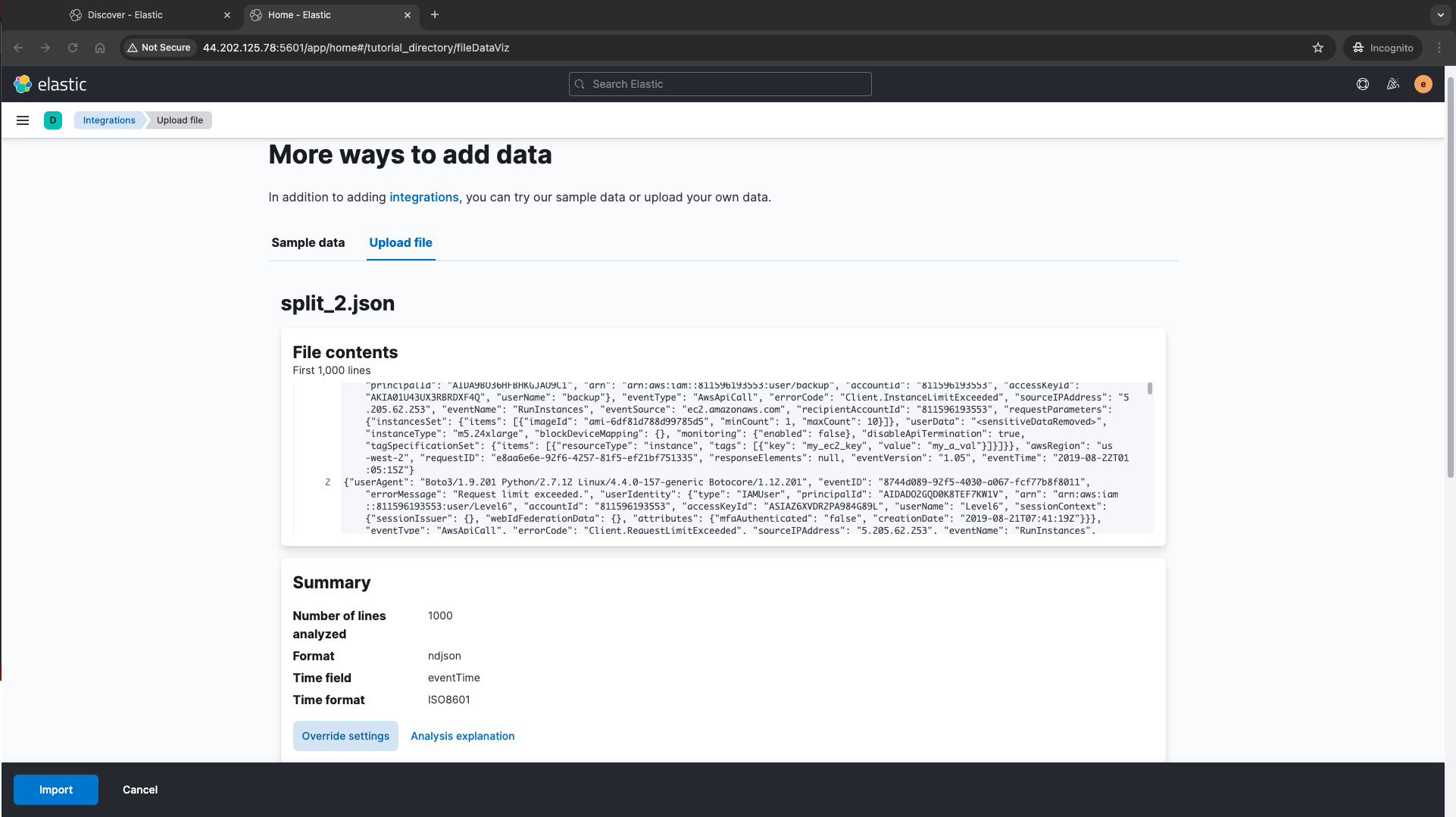
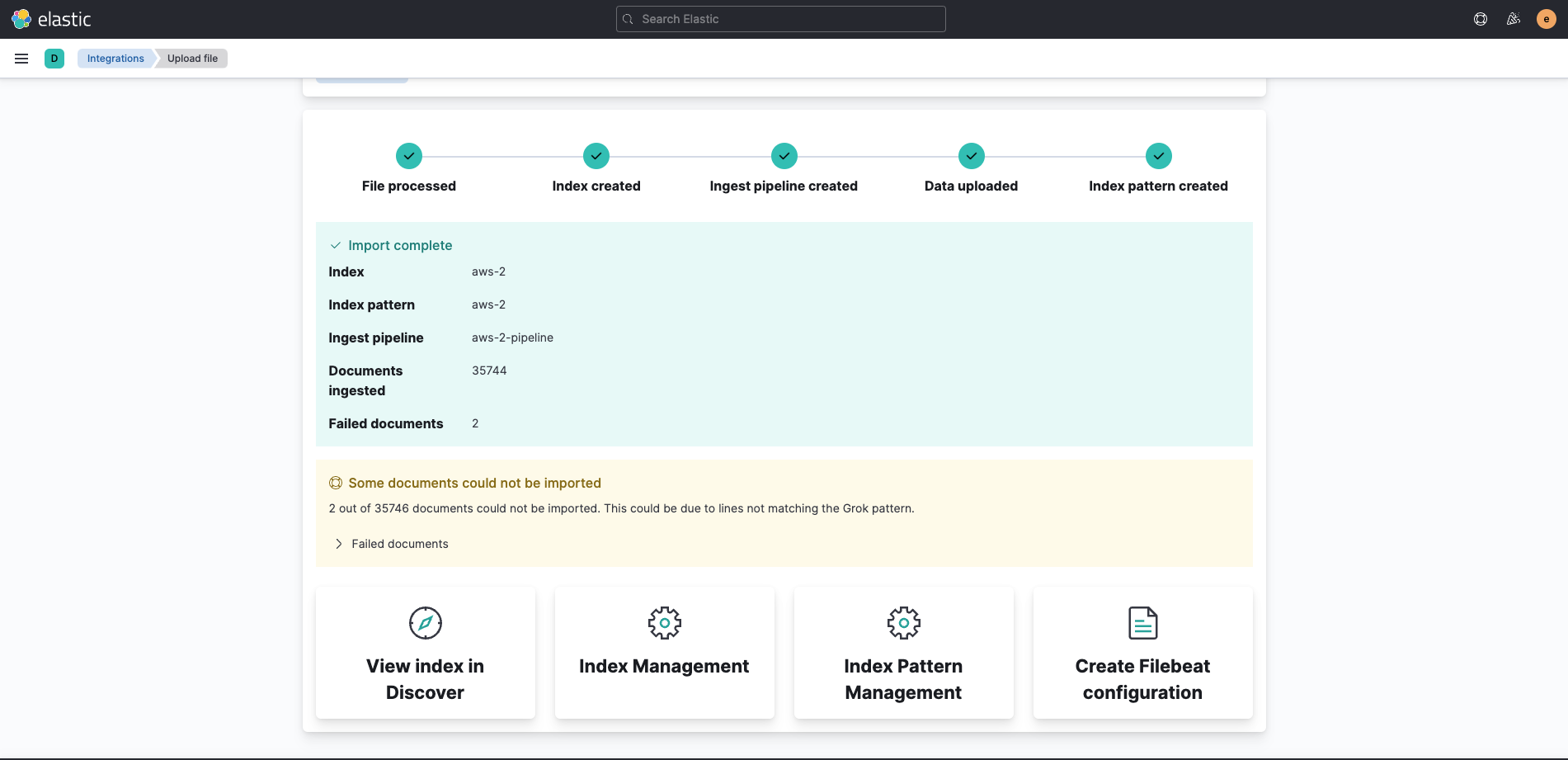
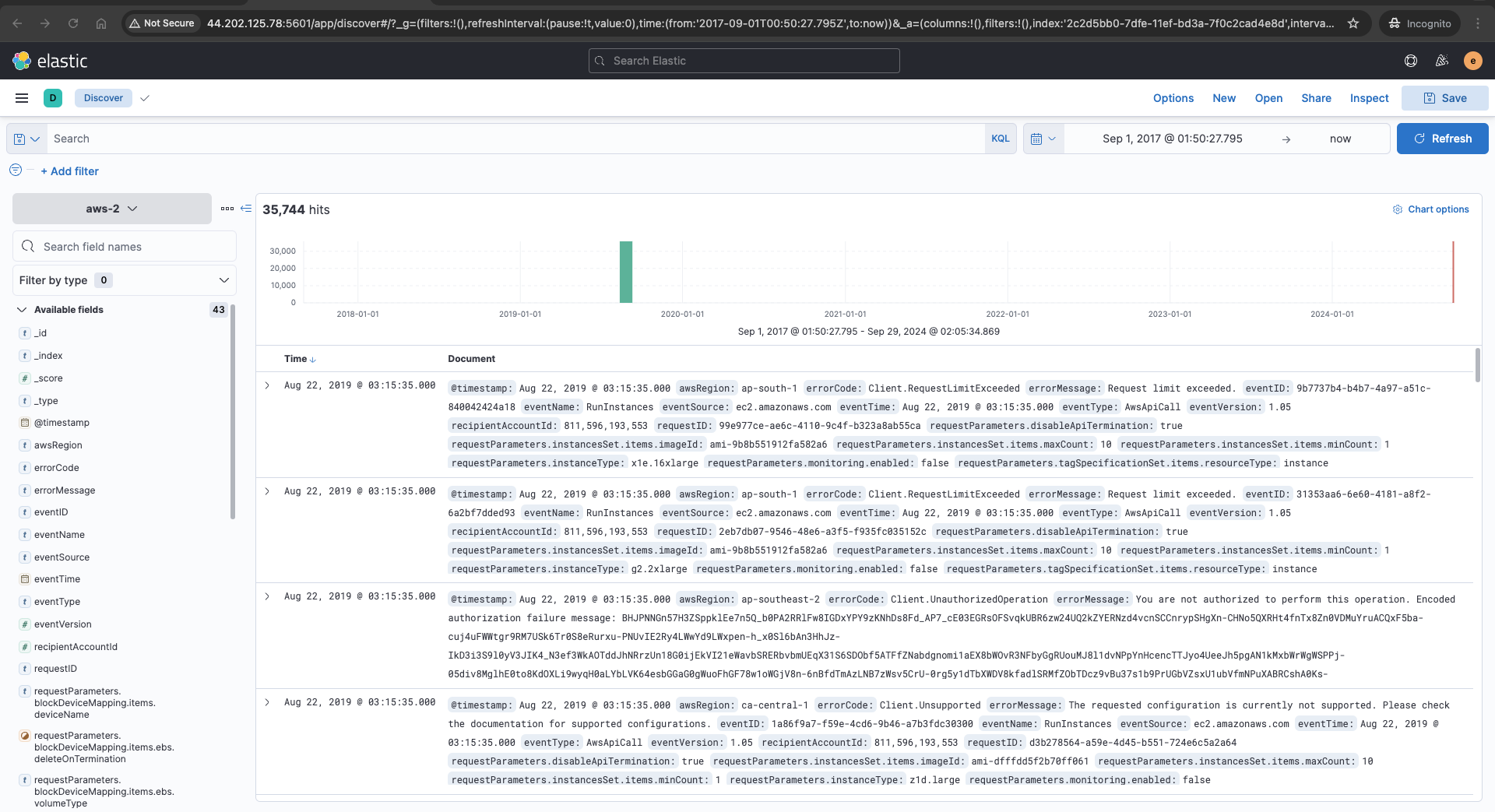
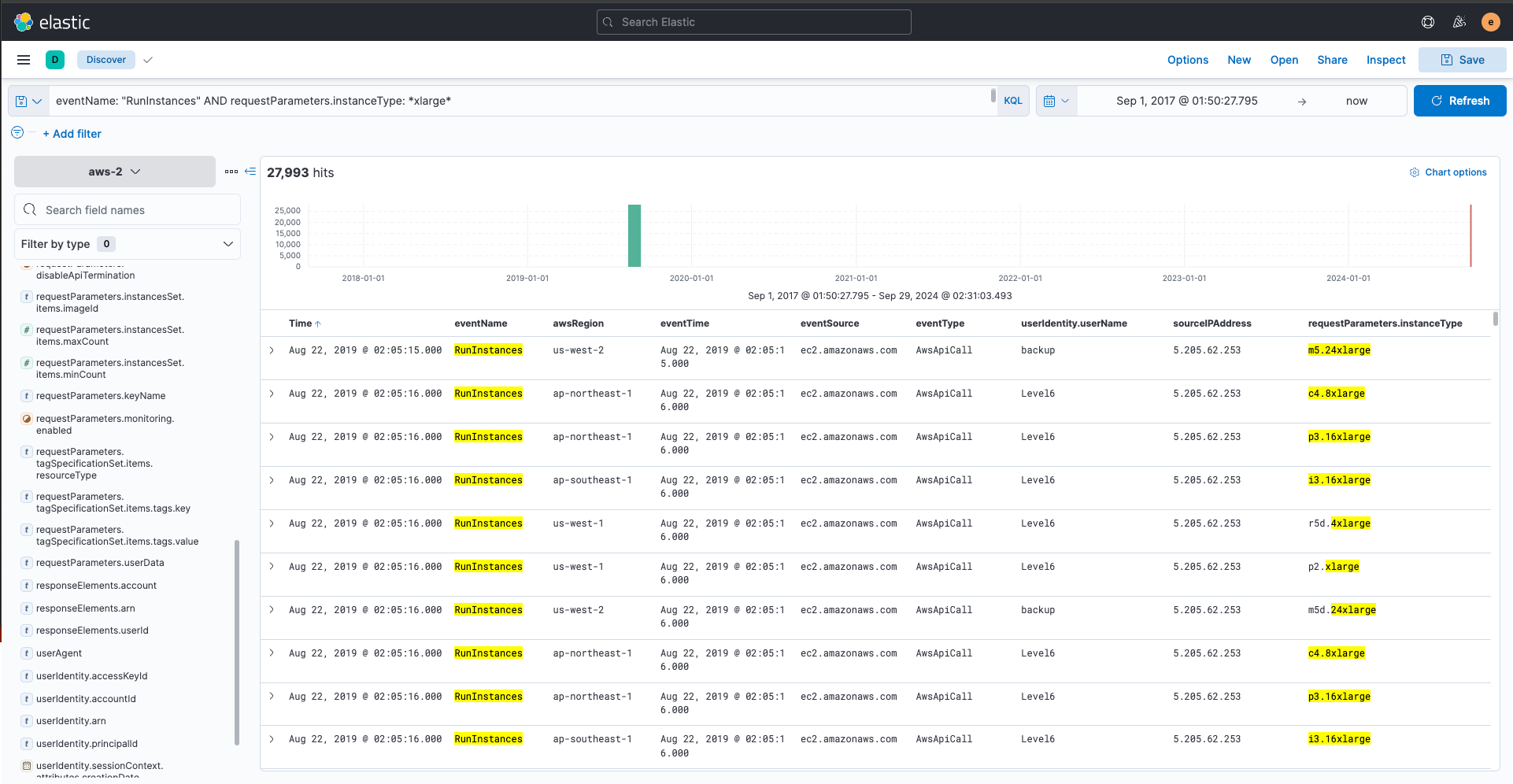
Step 4: Access the Logs and investigate cloud threats
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.