Taints and Tolerations simplified
 Syed Mahmood Ali
Syed Mahmood Ali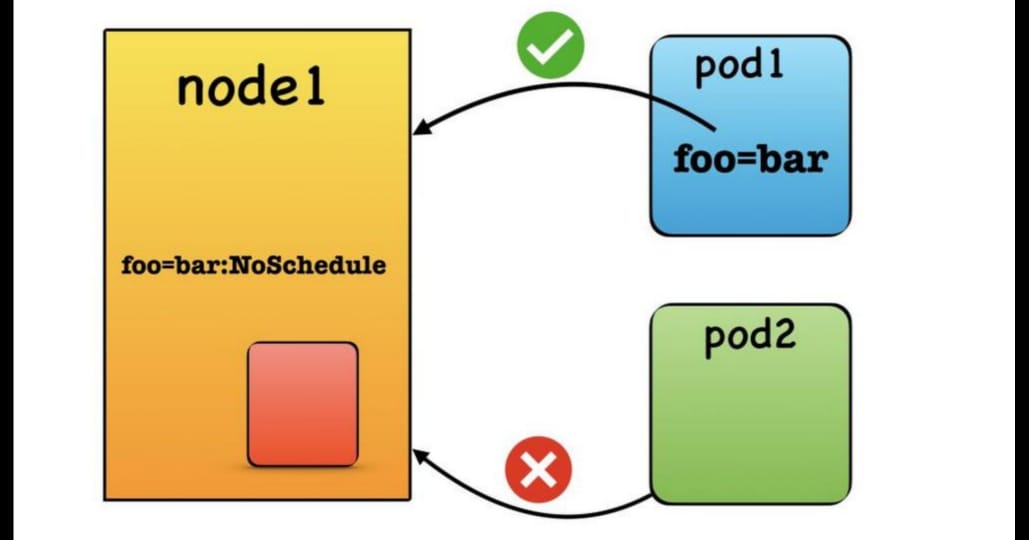
Imagine Kubernetes is like a city of houses, where the houses are computers (nodes), and the people living in them are the applications (pods). Kubernetes decides which person (pod) lives in which house (node). But, sometimes, certain houses are special, and you don’t want just anyone (pod) to move into them.
To handle this, Kubernetes uses taints and tolerations to control who can stay where.
Taints (Making a House Less Welcoming)
A taint is like a sign you put on a house saying, "No one can live here unless you can tolerate this condition."
When you put a taint on a node, you're telling Kubernetes:
"Hey, don’t let just any pod come to this node. Only let the pods in that are okay with this condition. Only the pods who can tolerate this taint."
Example:
- Imagine a house with a taint that says, “This house is very noisy.” Now, only people (pods) who are okay with noise (have a toleration) will be allowed to live there.
Tolerations (Allowing Certain People (pods) to Enter)
A toleration is like a special badge that a person (pod) carries that says, “I’m okay with noisy places,” so they can move into houses (nodes) with that taint.
Example:
- A pod might have a toleration that says, “I can tolerate noise.” So, if there’s a noisy house (taint), this pod will be allowed to live there.
How Taints and Tolerations Work Together
Taints on Nodes: You put a taint on a node when you want to keep most pods away. For example:
Taint: “Noisy house! Only people okay with noise can live here.”
Effect: Only pods with the right toleration can live in that node.
Tolerations on Pods: A toleration is applied to a pod when it’s okay with certain conditions. For example:
Toleration: “I’m okay with noise.”
Result: This pod can move into any node that has the “Noisy house” taint.
Use Cases for Taints and Tolerations
Special Workloads: Let’s say you have a special node for testing or for high-priority work. You could taint that node so only specific pods with tolerations can run there. This ensures normal pods don’t accidentally get scheduled there.
Node Maintenance: If you’re planning to work on a node and don’t want any new pods to go there, you can taint it. Only pods with a specific toleration will be allowed to stay or move in.
Some Points to Remember
Taints: They repel pods from nodes, like a "Do Not Enter" sign unless they meet certain criteria.
Tolerations: They allow pods to enter nodes with specific taints if the pod can tolerate the node's condition.
Example in Real Kubernetes
Applying a Taint to a Node using Imperative method:
kubectl taint nodes node1 key=value:NoScheduleThis command says: "Don’t schedule pods on node1 unless they have the right toleration."
Adding a Toleration to a Pod: In the pod’s configuration file (YAML):
tolerations: - key: "key" operator: "Equal" value: "value" effect: "NoSchedule"This tells the pod: "I can tolerate this condition and am allowed to run on nodes with this specific taint."
Real-World Analogy
Taint: Like a "Keep Out" or "Restricted Entry" sign on a house.
Toleration: Like a VIP pass that allows certain people (pods) to enter even if there’s a restriction (taint).
Summary
In Kubernetes, taints are applied to nodes to restrict which pods can be scheduled on them, acting like a "Keep Out" sign. Only pods with matching tolerations are allowed to run on these tainted nodes. Taints help manage workloads by preventing most pods from running on specific nodes unless they can tolerate certain conditions, while tolerations allow pods to bypass these restrictions. This mechanism ensures that special workloads go to designated nodes, improving resource management and cluster efficiency.
So, taints help keep certain pods away from nodes unless they have a toleration saying they’re okay with the condition. This helps Kubernetes manage where workloads run more efficiently.
Subscribe to my newsletter
Read articles from Syed Mahmood Ali directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
